千靶日记-0002
day-2
Ahiz靶机复盘
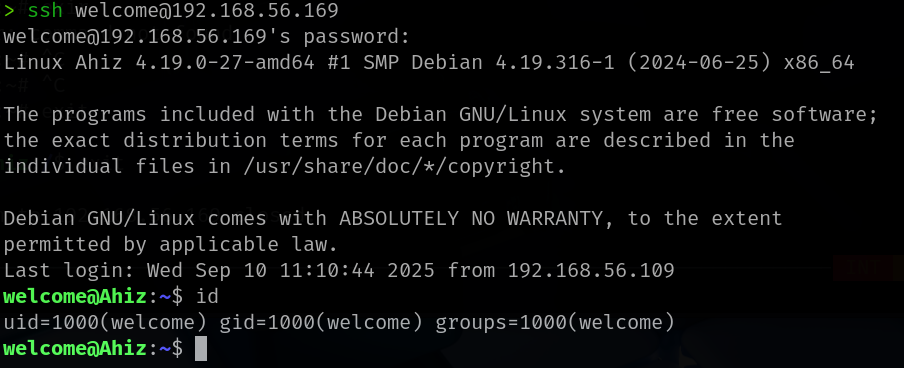
ssh
只开启了80端口,扫描目录发现许多php文件,php文件有4个字符,可能是base64编码的字符
手写一个小脚本
import requests
a = ""
for i in range(1,100):
url = f'http://192.168.56.169/{i}.php'
r = requests.get(url)
s = r.text
if r.status_code == 404:
break
a += s
print(a)
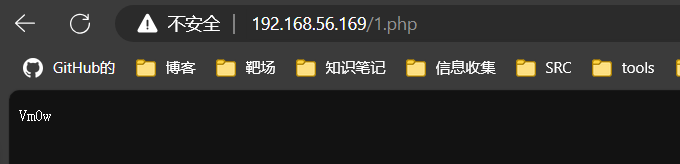
//Vm0weGQxSXhWWGhTV0d4VFYwZG9WVll3WkRSWFJteDBaVVYwVjJKR2JETlpWVlpQWVVaS2MxZHVhRmRTTTJoUVZtMXplRll4WkhWaVJtUnBWMGRvZVZaclVrZFpWMDE0Vkc1T1dHSkdjSEJXYTFwaFpWWmFjVk5xVWxwV01VcElWbTAxVjJGc1NuVlJiVGxhVjBoQ1dGUlhlR0ZqYkd0NllVWk9UbUY2VmpWV1JscFhWakpHU0ZadVJsSldSM001
然后拿到字符串,在厨子那里加工一下
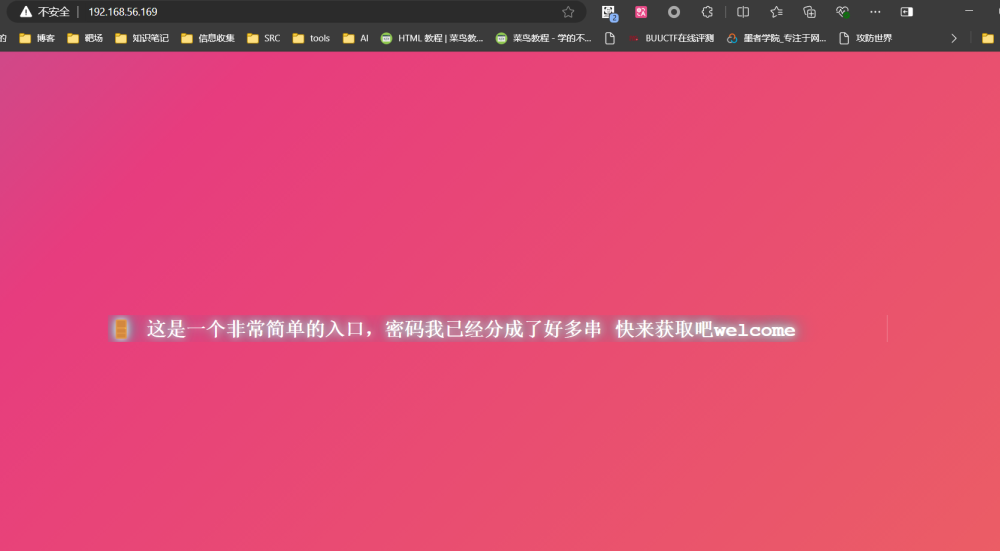
应该是ssh登录的密码,用户名应该是主页暗示的welcome
成功登录
补充:welcome下面有一个可执行程序1
welcome@Ahiz:~$ ./1 "$(python3 -c "print('1'* 1000)")"
✅ Good job! Here is your flag:
user_FLAG{this_is_a_safe_demo_flag}
提权root
这边正常的收集没看到有用信息,需要看到/opt目录(许多靶机的入口都在opt里面以后需要注意)
dns_data.pcap
这边把数据包拿到本地
分析一下
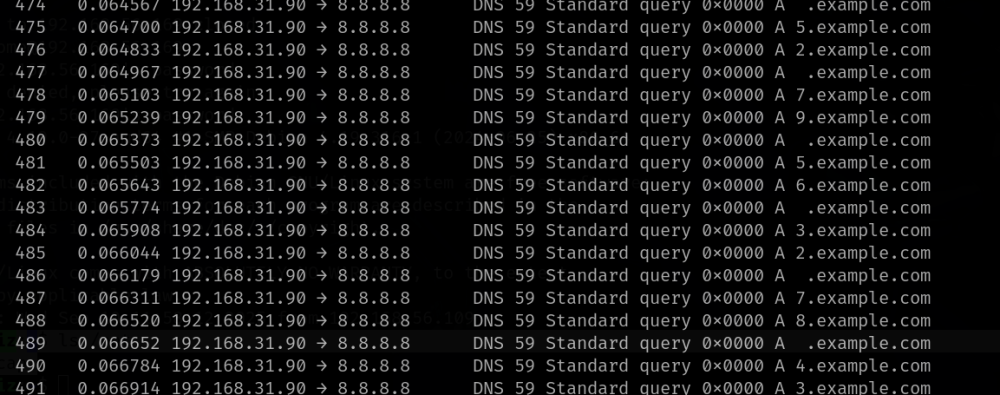
tshark -r dns_data.pcap
发现数据包的网址前缀有东西
用perl提取一下
> tshark -r dns_data.pcap | perl -ne 'print "$1" if /A (\w+)\.example\.com/'
Running as user "root" and group "root". This could be dangerous.
** (tshark:102019) 12:07:34.353844 [Main WARNING] ./ui/filter_files.c:245 -- read_filter_list(): '/usr/share/wireshark/cfilters' line 1 doesn't have a quoted filter name.
** (tshark:102019) 12:07:34.353964 [Main WARNING] ./ui/filter_files.c:245 -- read_filter_list(): '/usr/share/wireshark/cfilters' line 2 doesn't have a quoted filter name.
566d30786431497856586853574778545630646f565659775a445258526d78305a55563056324a4762444e5a56565a5059555a4b63316475614664534d326851566d317a654659785a485669526d52705630646f65565a72556b645a563031345647354f57474a476346685556455a4c5a565a6b56316473576d78534d4456365632746f54324673536e5652626b4a61596b5a4b655670586547465762475279563278435632457763465257565670535a444643556c42554d44303d#
然后厨子先16进制解码一下再base64解码得到root密码
(截图不贴了睡觉了)




 浙公网安备 33010602011771号
浙公网安备 33010602011771号