二:注重K8S安全 RKE2方式部署K8S高可用集群 (harbor仓库搭建连接)
harbor非安全镜像仓库[略]-实际生产中我们都需要安全的harbor镜像仓库;
vim /etc/hosts
192.168.109.140 k8s-harbor www.myharbor.com
192.168.109.141 k8s-master01
192.168.109.142 k8s-worker01
192.168.109.143 k8s-worker02
一.证书的创建:自签证书: 域名以www.myharbor.com

1.创建证书存放路径: mkdir -pv /apprun/ssl cd /apprun/ssl 2.创建ca.key密钥 openssl genrsa -out ca.key 4096 3.创建ca.crt openssl req -x509 -new -nodes -sha512 -days 3650 -subj "/C=CN/ST=hangzhou/L=hangzhou/O=example/OU=Personal/CN=www.myharbor.com" -key ca.key -out ca.crt 4.创建给harbor服务使用的密钥 www.myharbor.com.key openssl genrsa -out www.myharbor.com.key 4096 5.创建给harbor服务使用的证书签名请求文件 www.myharbor.com.csr openssl req -sha512 -new -subj "/C=CN/ST=hangzhou/L=hangzhou/O=example/OU=Personal/CN=www.myharbor.com.com" -key www.myharbor.com.key -out www.myharbor.com.csr 6.构建用于域名配置的v3.ext文件 cat > v3.ext <<-EOF authorityKeyIdentifier=keyid,issuer basicConstraints=CA:FALSE keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment extendedKeyUsage = serverAuth subjectAltName = @alt_names [alt_names] DNS.1=www.myharbor.com EOF 7.生成www.myharbor.com数字证书 www.myharbor.com.crt openssl x509 -req -sha512 -days 3650 -extfile v3.ext -CA ca.crt -CAkey ca.key -CAcreateserial -in www.myharbor.com.csr -out www.myharbor.com.crt
二.安装docker-ce:
yum install -y yum-utils
yum-config-manager --add-repo http://mirrors.aliyun.com/docker-ce/linux/centos/docker-ce.repo
yum install -y docker-ce docker-ce-cli containerd.io
systemctl enable --now dokcer
docker version
mkdir -pv /etc/docker
tee /etc/docker/daemon.json <<-'EOF'
{
"registry-mirrors": ["https://docker.m.daocloud.io"]
}
EOF
注意:
大部分的开源加速器已停止服务
https://esvjlqjx.mirror.aliyuncs.com 阿里云镜像加速器(https://blog.csdn.net/weixin_38125348/article/details/141922575)
https://docker.m.daocloud.io (2024-10-14起,阿里云镜像加速器 仅限在阿里云产品上使用。所以本地虚拟机也不行了)(https://blog.csdn.net/m0_62097957/article/details/144065748)
systemctl daemon-reload
systemctl restart docker
docker run -d -p 80:80 nginx:latest
docker ps
docker stop 容器id && docker rm 容器id
docker ps
三.安装harbor [离线安装包,github.com选择想要安装的版本]
cd /apprun/
wget https://github.com/goharbor/harbor/releases/download/v2.11.2/harbor-offline-installer-v2.11.2.tgz
tar -zxf harbor-offline-installer-v2.11.2.tgz
cd harbor/
cp harbor.yml.tmpl harbor.yml
vim harbor.yml
harbor在这里我们是仅以https安全认证模式运行的,而我们的证书是私有CA签发 或 自签的,这时我们docker登录harbor会报错:
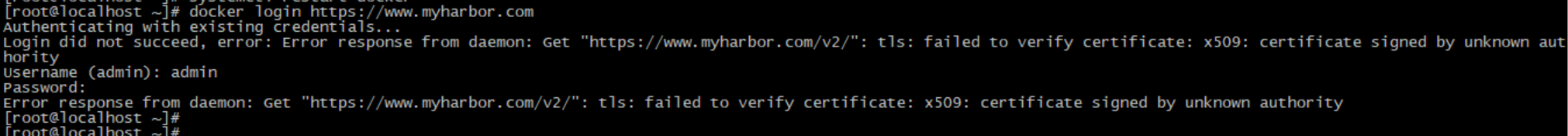
tls: failed to verify certificate: x509: certificate signed by unknown authority 【tls:无法验证证书:x509:由未知机构签名的证书】
curl -i https://www.myharbor.com 验证证书也报错;curl -i -k https://www.myharbor.com 跳过证书验证
此时docker登录harbor报错,我们处理方式有2种:
第一种:就是我们常用的非安全模式中处理的,编辑/etc/docker/daemon.json 添加:"insecure-registries": ["https://www.myharbor.com"],重启docker,信任我们的harbor仓库,这时登录就ok了,但curl证书(curl未能验证服务器的合法性)
第二种:为liunx机器设置证书授信;就是将CA根证书(ca.crt)添加/etc/pki/ca-trust/source/anchors/目录,然后更新证书列表:sudo update-ca-trust;此时登录与curl均正常
windows系统页面登录验证:https://www.myharbor.com 同样由于证书是私有CA签名的浏览器会认为不可信;
1.window机器首先添加内部域名映射(www.myharbor.com)域名解析成功;
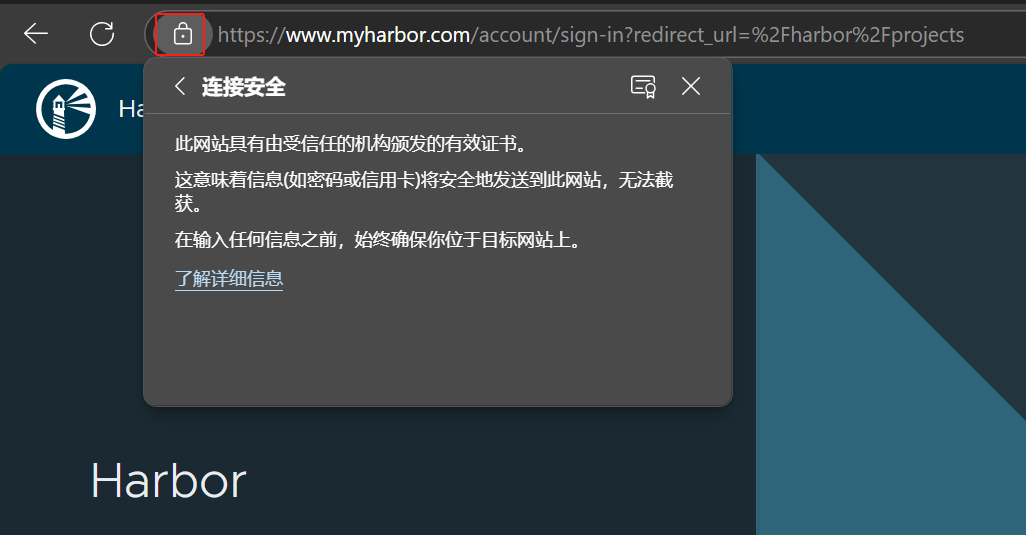
2.亦可将ca.crt 添加到浏览器可信任证书中(浏览器设置-隐私搜索和服务-安全性[管理证书])导入成功后[测试后certmgr.msc 中可以查到添加的证书,但浏览器看不到,也没起作用
win+r运行mmc,如下操作
https://zhidao.baidu.com/question/337205625542867085.html
浏览器可见添加的证书,www.myharbor.com验证成功
三.对接RKE2
1.RKE2机器创建证书存放路径:mkdir -pv /etc/rancher/rke2/www.myharbor.com/
2.传送ca.crt,www.myharbor.com.crt,www.myharbor.com.key这三个文件到RKE2的证书存放路径下
3.编辑RKE2的私有镜像仓库配置文件 vim /etc/rancher/rke2/registries.yaml

mirrors: www.myharbor.com: endpoint: - "https://www.myharbor.com" configs: "https://www.myharbor.com": auth: username: admin password: 12345 tls: cert_file: /etc/rancher/rke2/www.myharbor.com/www.myharbor.com.crt key_file: /etc/rancher/rke2/www.myharbor.com/www.myharbor.com.key ca_file: /etc/rancher/rke2/www.myharbor.com/ca.crt #insecure_skip_verify: true
重启前后查看cat /var/lib/rancher/rke2/agent/etc/containerd/config.toml
注:私有CA签名的证书和自签证书由于证书不可信 ;需要为liunx机器设置证书授信;就是将CA根证书(ca.crt)添加/etc/pki/ca-trust/source/anchors/目录,然后更新证书列表:sudo update-ca-trust;如果不添加拉取镜像失败报
tls: failed to verify certificate: x509: certificate signed by unknown authority 【tls:无法验证证书:x509:由未知机构签名的证书】
systemctl restart rke2-server
重启前后查看cat /var/lib/rancher/rke2/agent/etc/containerd/config.toml
cd /apprun
创建一个

--- apiVersion: apps/v1 kind: Deployment metadata: name: nginxweb spec: selector: matchLabels: app: nginxweb1 replicas: 3 template: metadata: labels: app: nginxweb1 spec: containers: - name: nginxwebc image: www.myharbor.com/library/nginx:latest imagePullPolicy: IfNotPresent ports: - containerPort: 80 --- apiVersion: v1 kind: Service metadata: name: nginxweb-service spec: externalTrafficPolicy: Cluster selector: app: nginxweb1 ports: - protocol: TCP port: 80 targetPort: 80 nodePort: 30080 type: NodePort
kubectl apply -f nginx.yaml
kubectl delete -f nginx.yaml
kubectl get pods
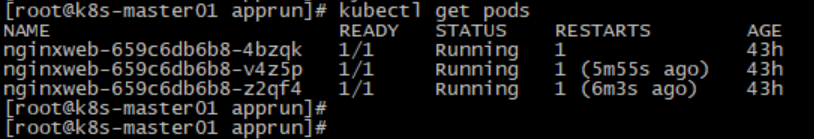
[root@k8s-master01 apprun]# kubectl describe pod nginxweb-659c6db6b8-4bzqk





 浙公网安备 33010602011771号
浙公网安备 33010602011771号