re-upx
根据提示可知是upx加壳,脱壳后用IDA打开,惯例先按shift+F12,
得到:

可知需要输入验证,双击可执行文件也可验证猜想,双击“please input your flag: ”
跳转反汇编界面:
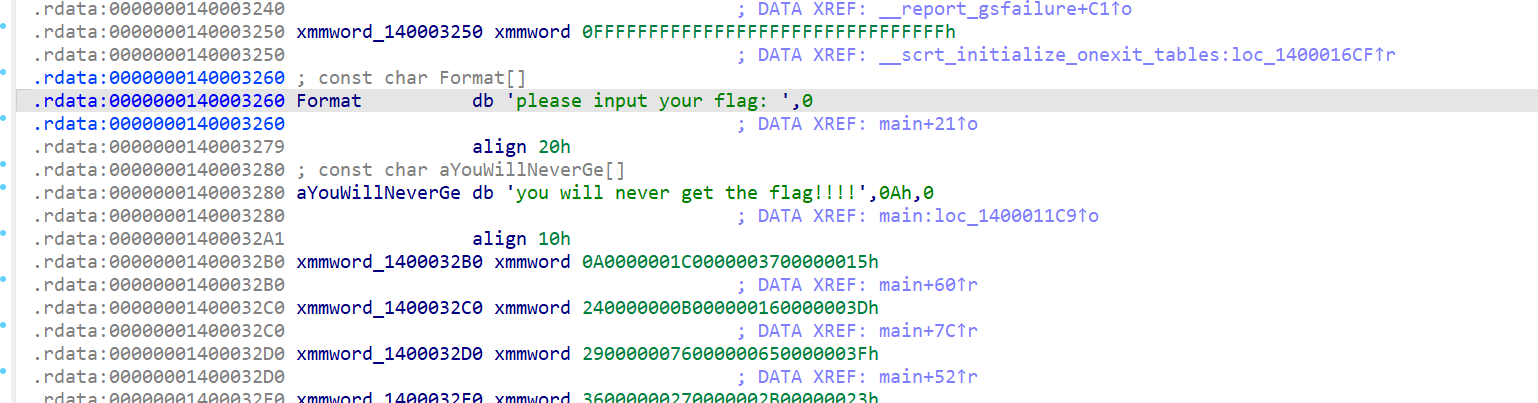
查看汇编代码和流程:

之后F5查看伪代码,

根据代码逻辑,我们可以逆推解密,v10的35个字符:

接下来逆推解密:
0x23, 0x2B, 0x27, 0x36, 0x33, 0x3C, 0x3, 0x48, 0x64, 0xB, 0x1D, 0x76, 0x7B, 0x10, 0xB, 0x3A, 0x3F, 0x65, 0x76, 0x29,
0x15, 0x37, 0x1C, 0xA, 0x8, 0x21, 0x3E, 0x3C, 0x3D, 0x16, 0xB, 0x24, 0x29, 0x24, 0x56,0xa
0x29, 0x24, 0x56,0xa分别是41,36,86,\n.
最后的结果:moectf{Y0u_c4n_unp4ck_It_vvith_upx}
代码:
#include <iostream>
#include <vector>
int main() {
std::vector<unsigned char> v10_bytes = {
0x23, 0x2B, 0x27, 0x36, 0x33, 0x3C, 0x3, 0x48, 0x64, 0xB, 0x1D, 0x76, 0x7B, 0x10, 0xB, 0x3A, 0x3F, 0x65, 0x76, 0x29,
0x15, 0x37, 0x1C, 0xA, 0x8, 0x21, 0x3E, 0x3C, 0x3D, 0x16, 0xB, 0x24, 0x29, 0x24, 0x56, 0xa
};
std::vector<unsigned char> flag(v10_bytes.begin(), v10_bytes.end());
for (int i = 35; i > 0; i--) {
flag[i - 1] = flag[i - 1] ^ 0x21 ^ flag[i];
}
for (auto c : flag) {
std::cout << c;
}
std::cout << std::endl;
return 0;
}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号