小白学逆向六月份第三周笔记
题目描述:猜个数字然后找到flag.
下载文件,是一个jar文件,解压后得到class文件
用jadclipse反编译后,得到源代码如下
import java.io.PrintStream; import java.math.BigInteger; public class guess { public guess() { } static String XOR(String _str_one, String _str_two) { BigInteger i1 = new BigInteger(_str_one, 16); BigInteger i2 = new BigInteger(_str_two, 16); BigInteger res = i1.xor(i2); String result = res.toString(16); return result; } public static void main(String args[]) { int guess_number = 0; int my_num = 0x14d8f707; int my_number = 0x5c214f6c; int flag = 0x149b861a; if(args.length > 0) { try//获得flag { guess_number = Integer.parseInt(args[0]); if(my_number / 5 == guess_number)//可以求得guess_number为309137378 { String str_one = "4b64ca12ace755516c178f72d05d7061"; String str_two = "ecd44646cfe5994ebeb35bf922e25dba"; my_num += flag; String answer = XOR(str_one, str_two); System.out.println((new StringBuilder("your flag is: ")).append(answer).toString()); } else { System.err.println("wrong guess!"); System.exit(1); } } catch(NumberFormatException e) { System.err.println("please enter an integer \nexample: java -jar guess 12"); System.exit(1); } } else { System.err.println("wrong guess!"); int num = 0xf4240; num++; System.exit(1); } } }
运行后可得 your flag is: a7b08c546302cc1fd2a4d48bf2bf2ddb
题目:easyre
拖进IDA64,shift+f12,直接得到flag
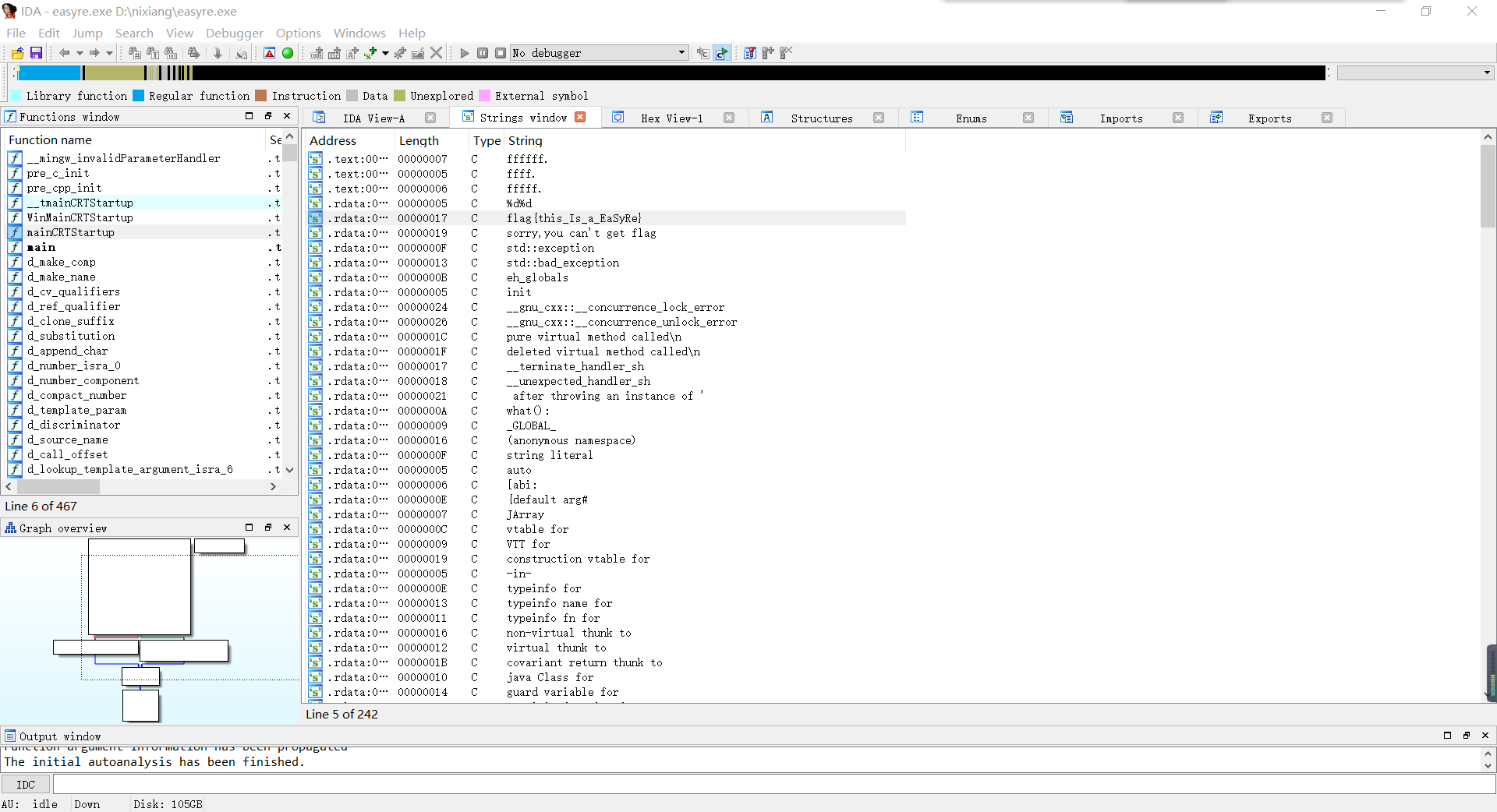
flag{this_Is_a_EaSyRe}
下载附件后放入IDA查看字符串
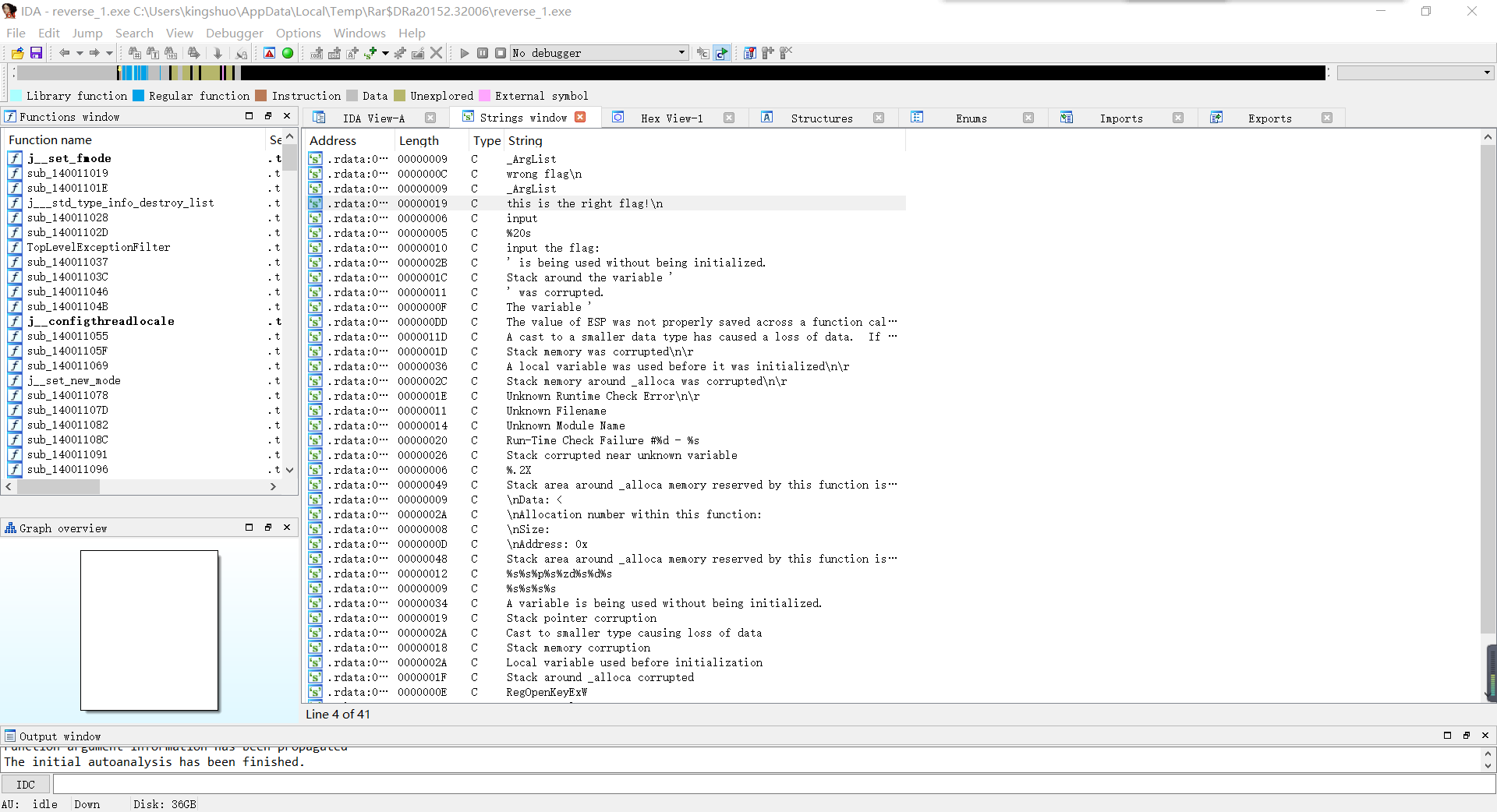
发现.this is the right flag!\n,双击跟进,查看伪代码
找到函数
__int64 sub_1400118C0() { char *v0; // rdi signed __int64 i; // rcx size_t v2; // rax size_t v3; // rax char v5; // [rsp+0h] [rbp-20h] int j; // [rsp+24h] [rbp+4h] char Str1; // [rsp+48h] [rbp+28h] unsigned __int64 v8; // [rsp+128h] [rbp+108h] v0 = &v5; for ( i = 82i64; i; --i ) { *(_DWORD *)v0 = -858993460; v0 += 4; } for ( j = 0; ; ++j ) { v8 = j; v2 = j_strlen(Str2); if ( v8 > v2 ) break; if ( Str2[j] == 111 ) Str2[j] = 48;//将111变为48,Char("111") o,Char("48") 0,则将o变为0 } sub_1400111D1("input the flag:"); sub_14001128F("%20s", &Str1); v3 = j_strlen(Str2); if ( !strncmp(&Str1, Str2, v3) ) sub_1400111D1("this is the right flag!\n"); else sub_1400111D1("wrong flag\n"); sub_14001113B(&v5, &unk_140019D00); return 0i64; }
而str2[]的内容为
4001C000 Str2 db '{hello_world}',0 ; DATA XREF: sub_1400118C0+4B↑o .data:000000014001C000 ; sub_1400118C0+67↑o ...
则flag为{hell0_w0rld}
题目reverse2
使用IDA64打开
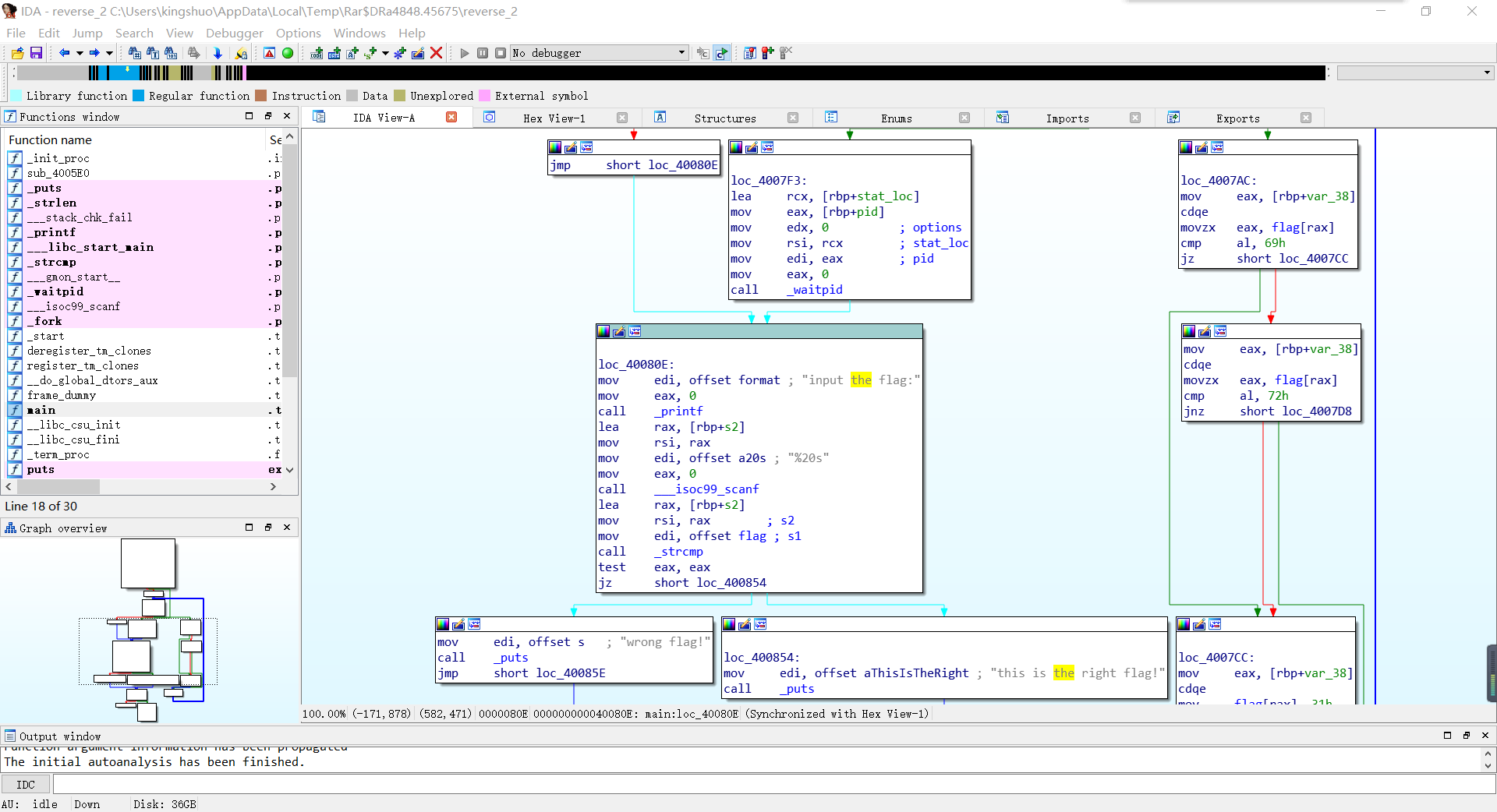
显然,左边在验证flag,右边在对flag进行变换
进入flag后看到
.data:0000000000601080 flag db 7Bh ; DATA XREF: main+34↑r .data:0000000000601080 ; main+44↑r ... .data:0000000000601081 aHackingForFun db 'hacking_for_fun}',0 .data:0000000000601081 _data ends
显然是对{hacking_for_fun}进行变换
f5反编译为伪代码
int __cdecl main(int argc, const char **argv, const char **envp) { int result; // eax int stat_loc; // [rsp+4h] [rbp-3Ch] int i; // [rsp+8h] [rbp-38h] __pid_t pid; // [rsp+Ch] [rbp-34h] char s2; // [rsp+10h] [rbp-30h] unsigned __int64 v8; // [rsp+28h] [rbp-18h] v8 = __readfsqword(0x28u); pid = fork(); if ( pid ) { argv = (const char **)&stat_loc; waitpid(pid, &stat_loc, 0); } else { for ( i = 0; i <= strlen(&flag); ++i ) { if ( *(&flag + i) == 105 || *(&flag + i) == 114 ) *(&flag + i) = 49;//将'i'和‘r’字符替换为1 } } printf("input the flag:", argv); __isoc99_scanf("%20s", &s2); if ( !strcmp(&flag, &s2) ) result = puts("this is the right flag!"); else result = puts("wrong flag!"); return result; }
则flag{hack1ng_fo1_fun}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号