目标:AR1和AR2之间为广域网域。二者配置GRE,完成后确保两个区域的终端能互通。
网络图:
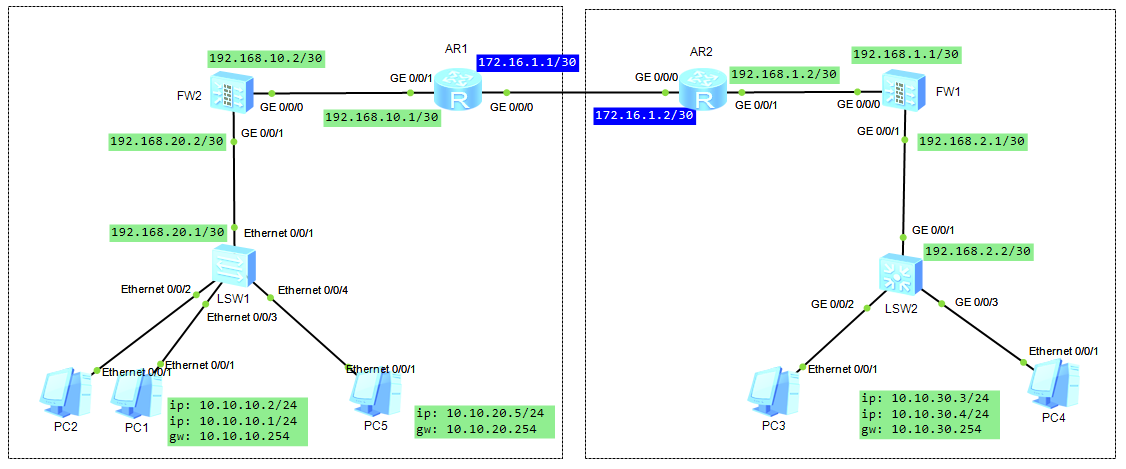
配置说明:
(1)配置各设备接口ip
(2)配置各设备静态路由
(3)配置防火墙上接口加入区域,及开通区域间流量inbound和outbound的permit
(4)配置AR上的gre,即创建tunnel接口,配置tunnel接口的协议为gre,配置source和destination为公网的本和对端ip
配置命令:
LSW1:
#
sysname LSW1
#
vlan batch 10 20 1000
#
interface Vlanif1
#
interface Vlanif10
ip address 10.10.10.254 255.255.255.0
#
interface Vlanif20
ip address 10.10.20.254 255.255.255.0
#
interface Vlanif1000
ip address 192.168.20.1 255.255.255.252
#
interface MEth0/0/1
#
interface Ethernet0/0/1
port link-type access
port default vlan 1000
#
interface Ethernet0/0/2
port link-type access
port default vlan 10
#
interface Ethernet0/0/3
port link-type access
port default vlan 10
#
interface Ethernet0/0/4
port link-type access
port default vlan 20
#
interface NULL0
#
ip route-static 10.10.30.0 255.255.255.0 192.168.20.2
#
FW2:
<FW2>dis cur
22:50:42 2022/04/01
#
stp region-configuration
region-name f0eee215704f
active region-configuration
#
interface GigabitEthernet0/0/0
alias GE0/MGMT
ip address 192.168.10.2 255.255.255.252
#
interface GigabitEthernet0/0/1
ip address 192.168.20.2 255.255.255.252
#
interface NULL0
alias NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface GigabitEthernet0/0/0
#
firewall zone untrust
set priority 5
#
firewall zone dmz
set priority 50
add interface GigabitEthernet0/0/1
#
ip route-static 10.10.10.0 255.255.255.0 192.168.20.1
ip route-static 10.10.20.0 255.255.255.0 192.168.20.1
ip route-static 10.10.30.0 255.255.255.0 192.168.10.1
#
firewall packet-filter default permit interzone local trust direction inbound
firewall packet-filter default permit interzone local trust direction outbound
firewall packet-filter default permit interzone local untrust direction outbound
firewall packet-filter default permit interzone local dmz direction outbound
firewall packet-filter default permit interzone trust dmz direction inbound ////custom config
firewall packet-filter default permit interzone trust dmz direction outbound ////custom config
#
AR1:
interface GigabitEthernet0/0/0
ip address 172.16.1.1 255.255.255.252
#
interface GigabitEthernet0/0/1
ip address 192.168.10.1 255.255.255.252
#
interface NULL0
#
interface Tunnel0/0/1
ip address 1.1.1.1 255.255.255.255
tunnel-protocol gre
source 172.16.1.1
destination 172.16.1.2
#
ip route-static 10.10.10.0 255.255.255.0 192.168.10.2
ip route-static 10.10.20.0 255.255.255.0 192.168.10.2
ip route-static 10.10.30.0 255.255.255.0 Tunnel0/0/1
ip route-static 10.10.xx.0 255.255.255.0 Tunnel0/0/1 //静态路由好多啊。能用ospf吗?
ip route-static 10.10.cc.0 255.255.255.0 Tunnel0/0/1
ip route-static 10.10.dd.0 255.255.255.0 Tunnel0/0/1
ip route-static 10.10.xx.0 255.255.255.0 Tunnel0/0/1
....
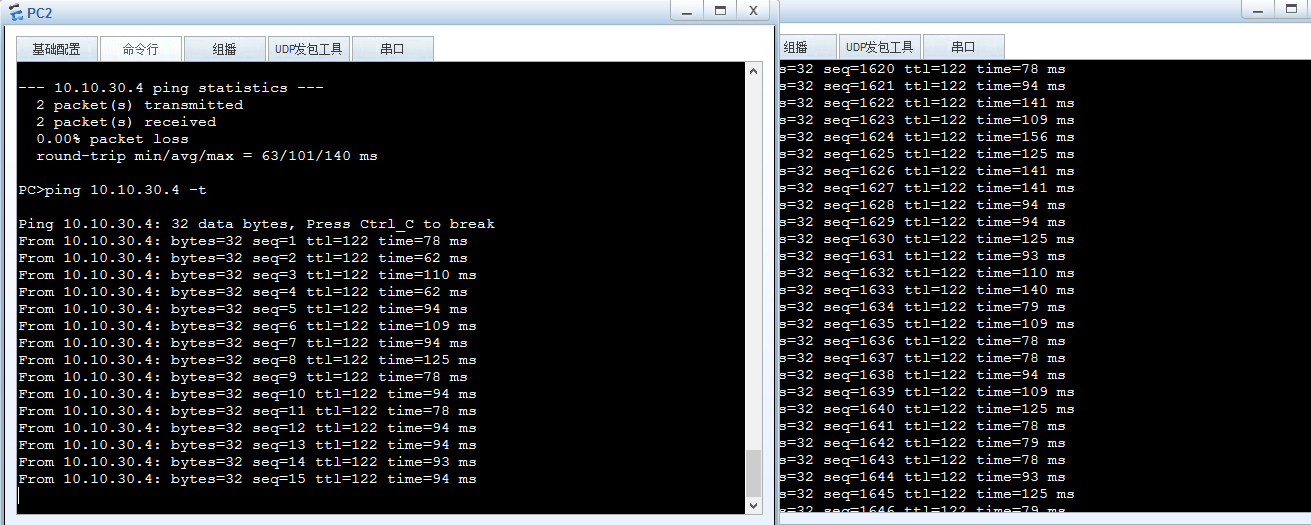
抓包验证(红圈为抓包点):
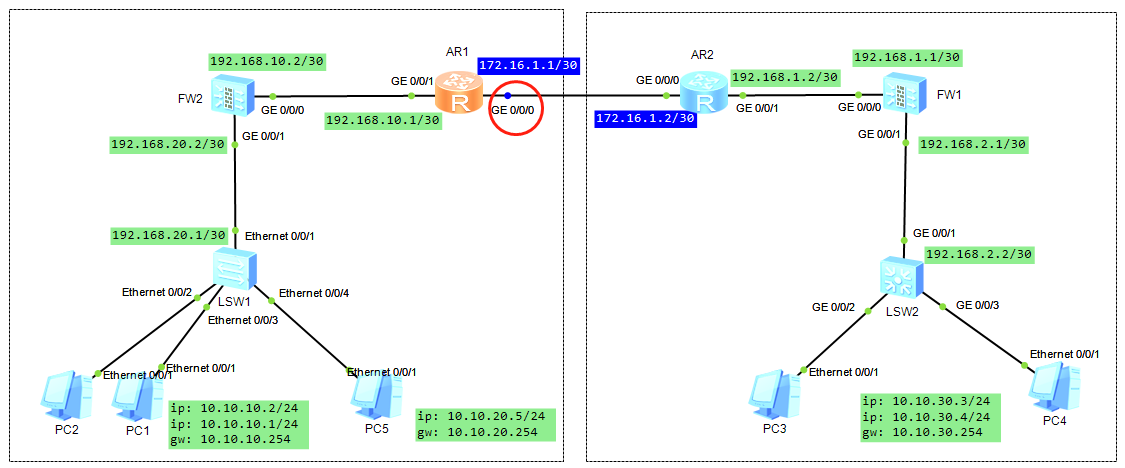
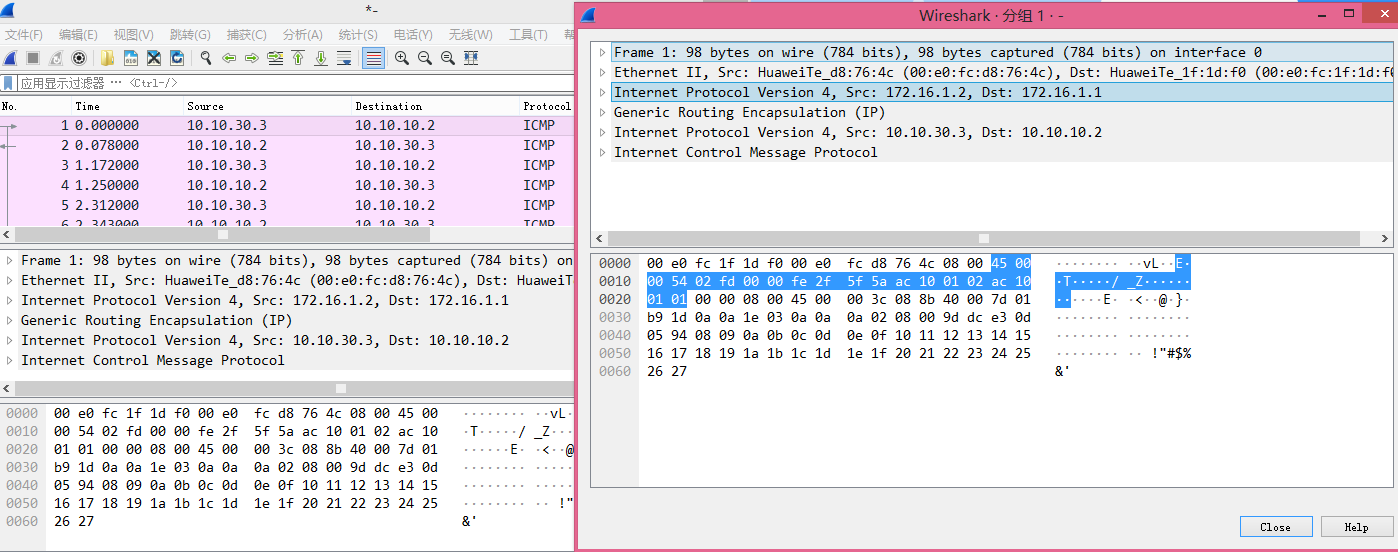
笔记:
仅配置ip后,LSW与防火墙虽然同网段,但相互之间不通。即,从fw ping与它的接口连接的对端的设备ip不通,反之也不通。这就涉及local区与其他区通信的问题
firewall zone local ///local区不能用命令加入任何接口
set priority 100
#
firewall zone trust
set priority 85
#
firewall zone untrust
set priority 5
#
firewall zone dmz
set priority 50
#
若将某接口if1加入了zone trust,if2加入了untrust,if3加入了dmz。并且有以下包过滤配置
#
firewall packet-filter default permit interzone local trust direction inbound
firewall packet-filter default permit interzone local trust direction outbound
firewall packet-filter default permit interzone local untrust direction outbound
firewall packet-filter default permit interzone local dmz direction outbound
则从fw可以ping通与if1连接的对着端设备接口ip
从与if1连接的对着端设备可以ping通if1
从fw可以ping通与if2连接的对着端设备接口ip,反之不行
从fw可以ping通与if3连接的对着端设备接口ip,反之不行
注:
inbound: 低优先级到高优先级
outbound: 高优先级到低优先级


 浙公网安备 33010602011771号
浙公网安备 33010602011771号