kali linux之msf信息收集
nmap扫描

Auxiliary 扫描模块
目前有557个扫描方式
use auxiliary/scanner/smb/smb_version(smb版本扫描)
use auxiliary/scanner/smb/pipe_auditor(扫描命名管道,判断smb服务类型,帐号,密码)
use auxiliary/scanner/smb/pipe_dcerpc_auditor(扫描通过smb管道可以访问的RCERPC服务)
use auxiliary/scanner/smb/smb_enumshares(smb共享枚举---帐号,密码)
use auxiliary/scanner/smb/smb_enumusers(smb用户枚举----帐号密码)
use auxiliary/scanner/smb/smb_lookupsid(sid枚举--帐号,密码)
use auxiliary/scanner/ssh/ssh_version(ssh版本扫描)
use auxiliary/scanner/ssh/ssh_login (ssh密码爆破)
use auxiliary/scanner/ssh/ssh_login_pubkey(ssh公钥登录---set KEY_FILE id_rsa set USERNAME root)
use post/windows/gather/enum_patches(基于已经获取了session进行检测windows缺少的补丁)
use auxiliary/scanner/mssql/mssql_ping(mssql端口扫描)
use auxiliary/scanner/mssql/mssql_login(爆破mssql密码)
use auxiliary/admin/mssql/mssql_exec(远程执行代码--set CMD net user user pass /ADD)
use auxiliary/scanner/ftp/ftp_version(FTP版本扫描)
use auxiliary/scanner/ftp/anonymous(FTP匿名登录)
use auxiliary/scanner/ftp/ftp_login(FTP暴力破解)
use auxiliary/scanner/vnc/vnc_login(vnc密码破解)
use auxiliary/scanner/vnc/vnc_none_auth(vnc无密码访问---supported:None, free access!)
use auxiliary/scanner/rdp/ms12_020_check(RDP远程桌面漏洞---检查会不会造成DoS攻击)
use auxiliary/scanner/ssh/juniper_backdoor(设备后门)
use auxiliary/scanner/ssh/fortinet_backdoor(设备后门)
use auxiliary/scanner/vmware/vmauthd_login(VMWare ESXi密码破解)
use auxiliary/scanner/vmware/vmware_enum_vms(VMWare ESXi密码破解)
use auxiliary/admin/vmware/poweron_vm(利用web api远程开启虚拟机)
HTTP 弱点扫描
use auxiliary/scanner/http/cert(过期证书扫描)
use auxiliary/scanner/http/dir_listing(显示目录及文件)
use auxiliary/scanner/http/files_dir显示目录及文件)
use auxiliary/scanner/http/dir_webdav_unicode_bypass(WebDAV Unicode 编码身份验证绕过)
use auxiliary/scanner/http/tomcat_mgr_login(Tomcat 管理登录页面)
use auxiliary/scanner/http/verb_auth_bypass(基于HTTP方法的身份验证绕过)
use auxiliary/scanner/http/wordpress_login_enum(Wordpress 密码爆破--- set URI /wordpress/wp-login.php)
WEB应用扫描器
wmap
load wmap
wmap_sites -a http://x.x.x.x
wmap_targets -t http://x.x.x.x/xxx/xx.php
wmap_run -t
wmap_run -e
wmap_vulns -l
vulns
Openvas
load openvas(需要配置,使用繁琐,导入nbe格式扫描日志,db_import xxx.nbe)
Nessus
load nessus
nessus_help
nessus_connect nessus@nessus 192.168.1.12(连接nessus服务器)
nessus_policy_list
nessus_scan_new
nessus_report_list
arp扫描 set INTERFACE RHOSTS THREADS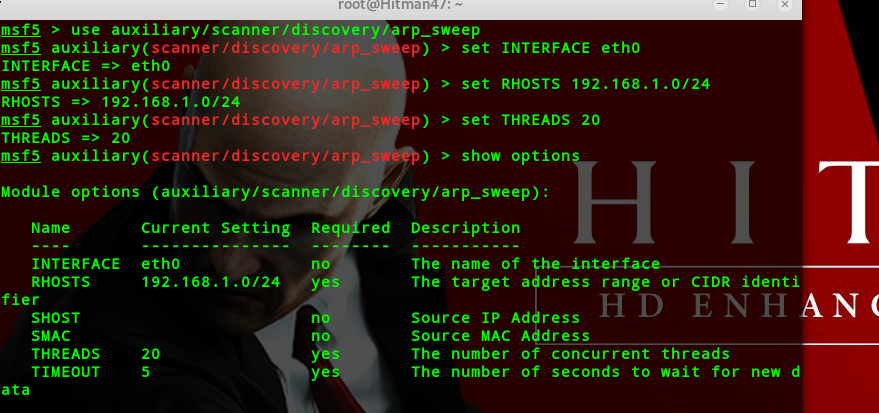
扫描结果
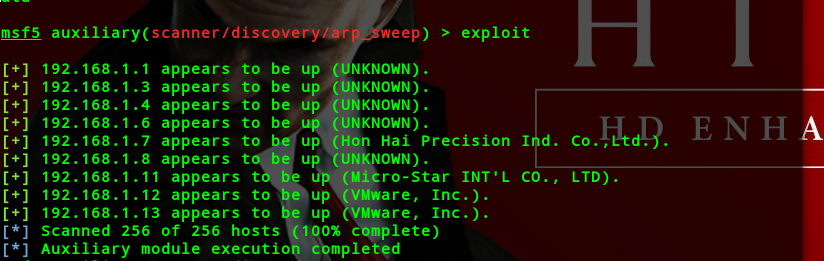
syn扫描
set RHOSTS PORTS THREADS
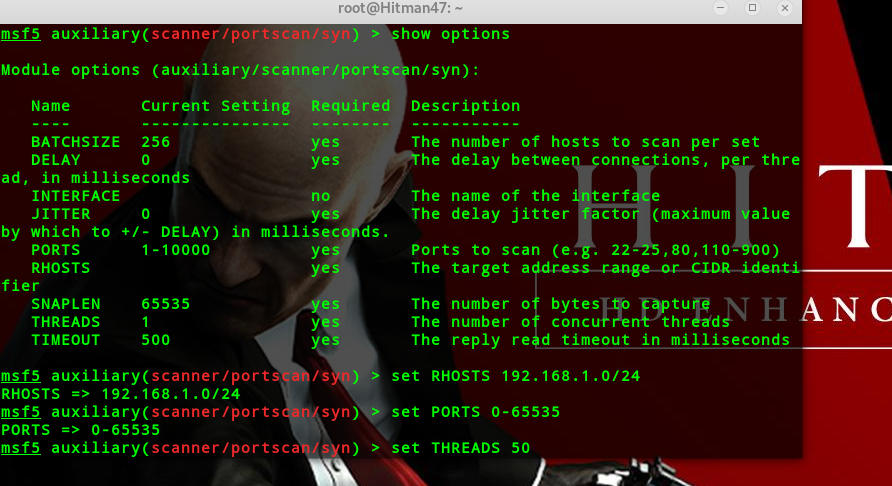
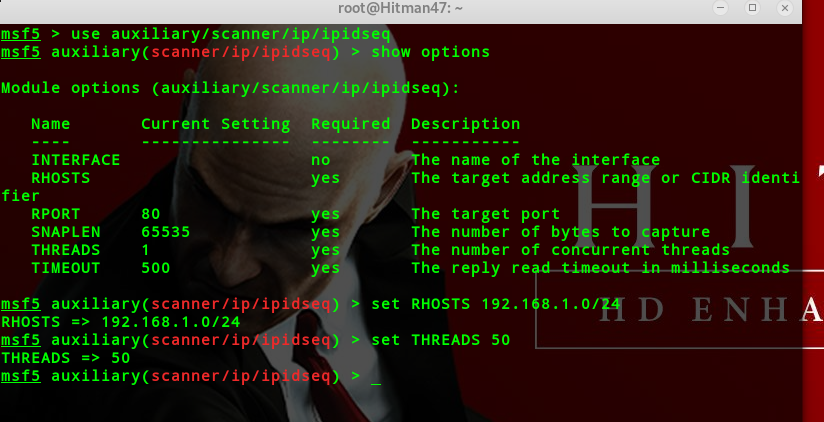
IPID IdIe扫描
查找ipidseq主机
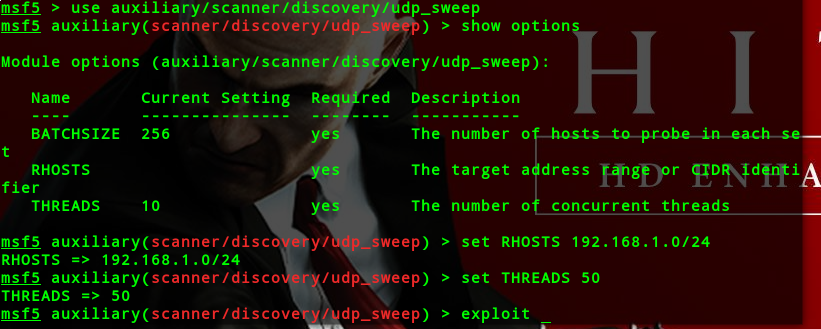
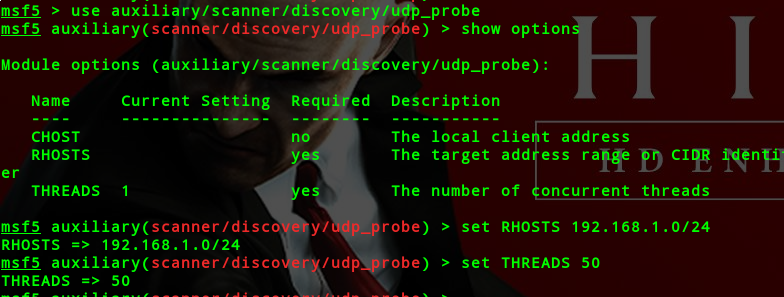
udp扫描
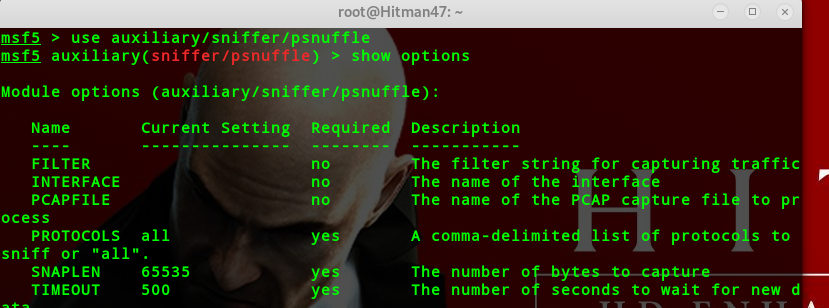
密码嗅探
msf5 > use auxiliary/sniffer/psnuffle
支持从pcap抓包文件中提取密码
功能类似于dsniff
目前只支持pop3,imap,ftp,http get协议
set 接口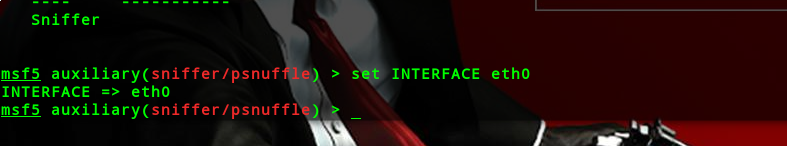
snmp扫描
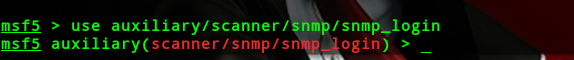
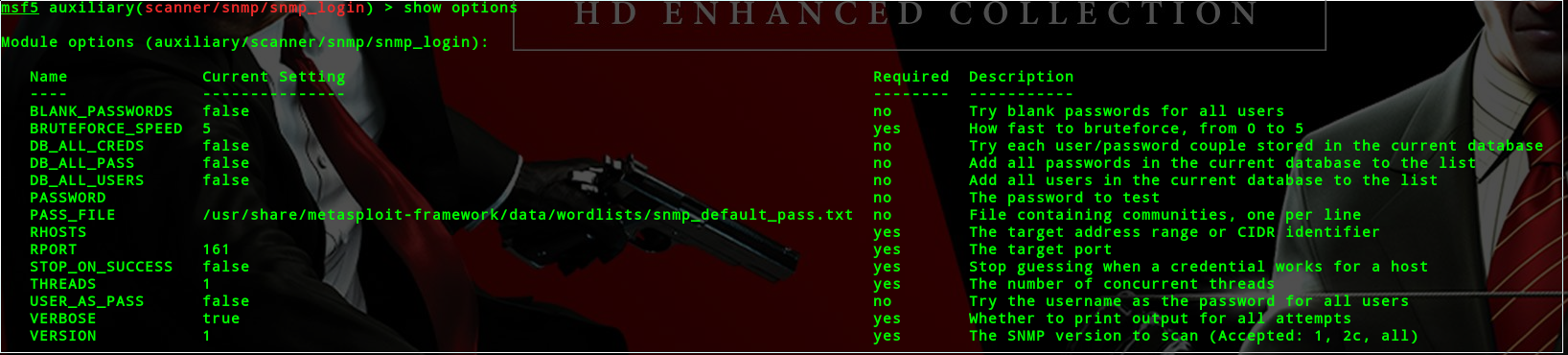
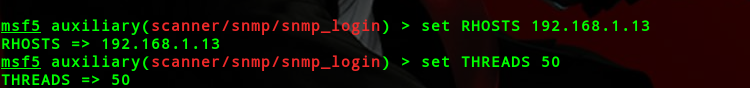
auxiliary/scanner/snmp/snmp_login
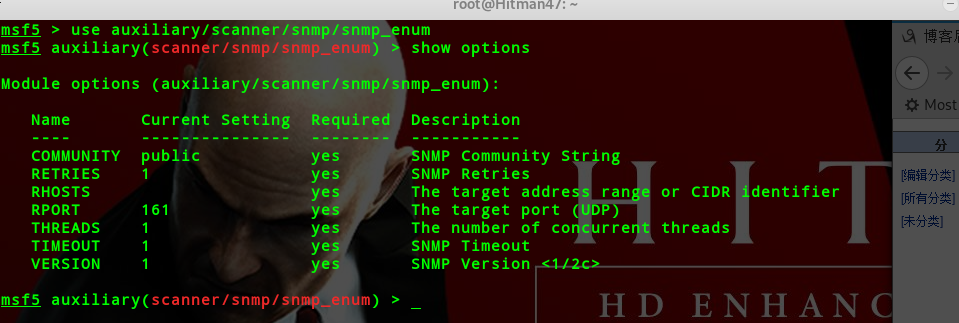
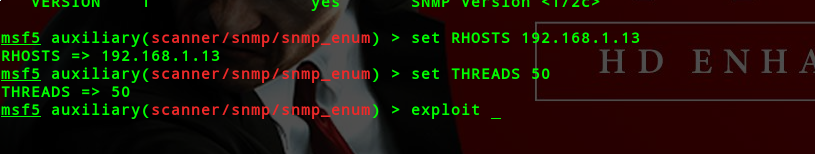
auxiliary/scanner/snmp/snmp_enum
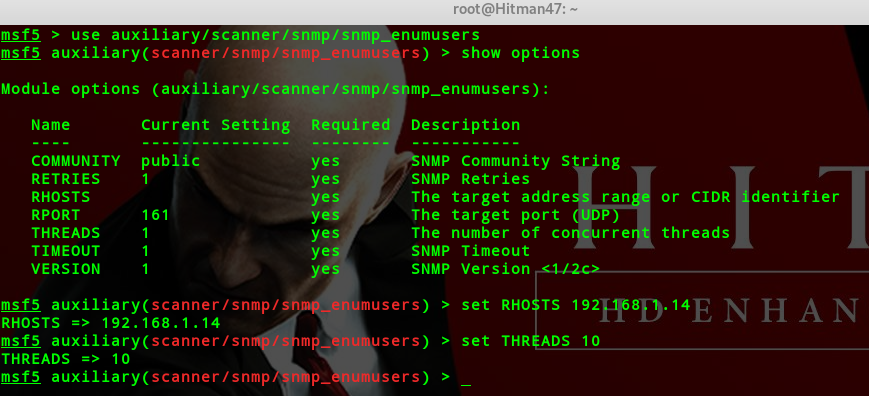
auxiliary/scanner/snmp/snmp_enumusers(windows)
auxiliary/scanner/snmp/snmp_enumshares(windows) 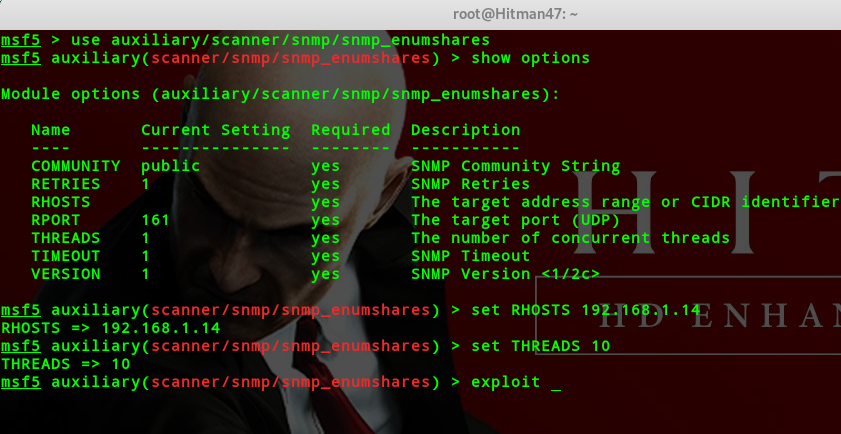
友情链接 http://www.cnblogs.com/klionsec
http://www.cnblogs.com/l0cm
http://www.cnblogs.com/Anonyaptxxx
http://www.feiyusafe.cn




 浙公网安备 33010602011771号
浙公网安备 33010602011771号