OWASP ModSecurity Core Rule Set (CRS)的基本使用
Preface
前述文章开源WAF工具ModSecurity,介绍了ModSecurity作为Nginx的动态加载模块的基本安装和使用。
本篇简单介绍ModSecurity CRS规则集的使用。
# nginx -v # nginx版本 nginx version: nginx/1.17.6 # which nginx # nginx可执行文件路径 /usr/sbin/nginx # find / -name nginx.conf # nginx配置文件路径 /etc/nginx/nginx.conf
# ls /etc/nginx/modules/ # modsecurity模块位置
ngx_http_modsecurity_module.so
# ls /etc/nginx/modsec/*.conf # modsecurity配置文件路径
/etc/nginx/modsec/main.conf /etc/nginx/modsec/modsecurity.conf
如果参照前面给出的链接,除了版本上可能会有差异外(由于更新),其它的是一样的。
OWASP CRS
下载OWASP规则并生成配置文件
# cd /etc/nginx/modsec/ # 切换到我们设置的modsecurity配置文件路径 # git clone https://github.com/SpiderLabs/owasp-modsecurity-crs.git # 下载CRS规则文件 # cd owasp-modsecurity-crs # cp crs-setup.conf.example crs-setup.conf # 使用默认配置
# git branch
* v3.3/dev # 目前在最新的3.3分支
配置OWASP规则
编辑crs-setup.conf文件(使用命令)。
# sed -ie 's/SecDefaultAction "phase:1,log,auditlog,pass"/#SecDefaultAction "phase:1,log,auditlog,pass"/g' crs-setup.conf # sed -ie 's/SecDefaultAction "phase:2,log,auditlog,pass"/#SecDefaultAction "phase:2,log,auditlog,pass"/g' crs-setup.conf # sed -ie 's/#.*SecDefaultAction "phase:1,log,auditlog,deny,status:403"/SecDefaultAction "phase:1,log,auditlog,deny,status:403"/g' crs-setup.conf # sed -ie 's/# SecDefaultAction "phase:2,log,auditlog,deny,status:403"/SecDefaultAction "phase:2,log,auditlog,deny,status:403"/g' crs-setup.conf
生成例外排除请求的配置文件
# pwd # 当前已在这个路径 /etc/nginx/modsec/owasp-modsecurity-crs # cp rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf # 例外排除请求 # cp rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf.example rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf # 例外排除请求 $ cp rules/*.data .. # data文件拷贝至modsecurity配置文件路径,即/etc/nginx/modsec
# cd /etc/nginx/modsec/ # ls # /etc/nginx/modsec路径下的内容是这样 crawlers-user-agents.data java-errors.data owasp-modsecurity-crs php-function-names-933151.data scanners-headers.data sql-errors.data iis-errors.data lfi-os-files.data php-config-directives.data php-variables.data scanners-urls.data unicode.mapping java-classes.data main.conf php-errors.data restricted-files.data scanners-user-agents.data unix-shell.data java-code-leakages.data modsecurity.conf php-function-names-933150.data restricted-upload.data scripting-user-agents.data windows-powershell-commands.data
其中:
- modsecurity.conf为modsecurity的配置文件;
- main.conf为我们自己添加的主配置文件,规则都可添加到这里,方便进行管理;
添加规则
在main.conf配置文件中添加我们想要的规则:
# vim main.conf # 以下是main.conf中的内容 # Include the recommended configuration include modsecurity.conf include owasp-modsecurity-crs/crs-setup.conf include owasp-modsecurity-crs/rules/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf include owasp-modsecurity-crs/rules/REQUEST-901-INITIALIZATION.conf Include owasp-modsecurity-crs/rules/REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf include owasp-modsecurity-crs/rules/REQUEST-905-COMMON-EXCEPTIONS.conf include owasp-modsecurity-crs/rules/REQUEST-910-IP-REPUTATION.conf include owasp-modsecurity-crs/rules/REQUEST-911-METHOD-ENFORCEMENT.conf include owasp-modsecurity-crs/rules/REQUEST-912-DOS-PROTECTION.conf include owasp-modsecurity-crs/rules/REQUEST-913-SCANNER-DETECTION.conf include owasp-modsecurity-crs/rules/REQUEST-920-PROTOCOL-ENFORCEMENT.conf include owasp-modsecurity-crs/rules/REQUEST-921-PROTOCOL-ATTACK.conf include owasp-modsecurity-crs/rules/REQUEST-930-APPLICATION-ATTACK-LFI.conf include owasp-modsecurity-crs/rules/REQUEST-931-APPLICATION-ATTACK-RFI.conf include owasp-modsecurity-crs/rules/REQUEST-932-APPLICATION-ATTACK-RCE.conf include owasp-modsecurity-crs/rules/REQUEST-933-APPLICATION-ATTACK-PHP.conf include owasp-modsecurity-crs/rules/REQUEST-941-APPLICATION-ATTACK-XSS.conf include owasp-modsecurity-crs/rules/REQUEST-942-APPLICATION-ATTACK-SQLI.conf include owasp-modsecurity-crs/rules/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf include owasp-modsecurity-crs/rules/REQUEST-949-BLOCKING-EVALUATION.conf include owasp-modsecurity-crs/rules/RESPONSE-950-DATA-LEAKAGES.conf include owasp-modsecurity-crs/rules/RESPONSE-951-DATA-LEAKAGES-SQL.conf include owasp-modsecurity-crs/rules/RESPONSE-952-DATA-LEAKAGES-JAVA.conf include owasp-modsecurity-crs/rules/RESPONSE-953-DATA-LEAKAGES-PHP.conf include owasp-modsecurity-crs/rules/RESPONSE-954-DATA-LEAKAGES-IIS.conf include owasp-modsecurity-crs/rules/RESPONSE-959-BLOCKING-EVALUATION.conf include owasp-modsecurity-crs/rules/RESPONSE-980-CORRELATION.conf include owasp-modsecurity-crs/rules/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf # A test rule SecRule ARGS:testparam "@contains test" "id:1234,deny,log,status:403"
【注】考虑到可能对主机性能上的损耗,可以根据实际需求加入对应的漏洞的防护规则即可。
测试
# nginx -s reload # 重载配置 # nginx -t # 测试 nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful # curl -D - http://localhost/?id=1 # 正常访问 HTTP/1.1 200 OK Server: nginx/1.17.6 Date: Tue, 26 Nov 2019 08:09:01 GMT Content-Type: text/plain Content-Length: 32 Connection: keep-alive Thank you for requesting /?id=1
# curl -D - http://localhost/?id='1 and 1=1' # 测试是否存在SQL注入 HTTP/1.1 403 Forbidden <<== 会被拦截 Server: nginx/1.17.6 Date: Tue, 26 Nov 2019 08:09:02 GMT Content-Type: text/html Content-Length: 153 Connection: keep-alive <html> <head><title>403 Forbidden</title></head> <body> <center><h1>403 Forbidden</h1></center> <hr><center>nginx/1.17.6</center> </body> </html> # curl -D - http://localhost/?input='<script>alert(/xss/)</script>' # 测试XSS HTTP/1.1 403 Forbidden <<== 同样会被拦截 Server: nginx/1.17.6 Date: Tue, 26 Nov 2019 08:09:40 GMT Content-Type: text/html Content-Length: 153 Connection: keep-alive <html> <head><title>403 Forbidden</title></head> <body> <center><h1>403 Forbidden</h1></center> <hr><center>nginx/1.17.6</center> </body> </html>
查看日志文件
modsecurity日志文件:/var/log/modsec_audit.log
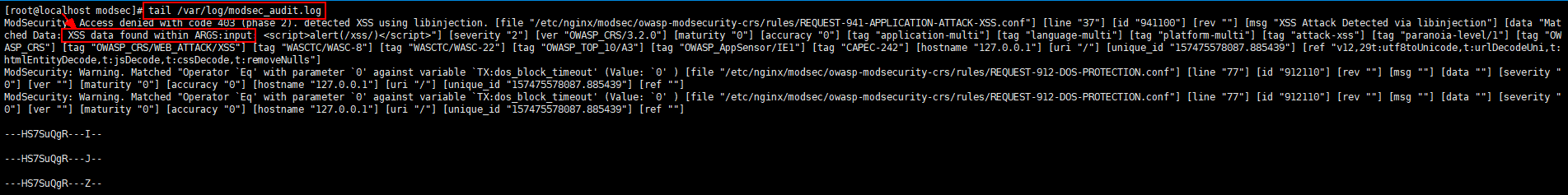
可以清楚的看到日志中记录了XSS的攻击记录。
ModSecurity CRS规则集的基本使用就是这样,最主要的是要知道CRS规则集中的内容,规则的编写,才能编写出符合自己要求的规则。
参考
-------------------------------------------
个性签名:如果世上的事都按你说的道理走 世界就不是现在这样了!
如果觉得这篇文章对你有小小的帮助的话,记得在右下角点个“推荐”哦,博主在此感谢!



 浙公网安备 33010602011771号
浙公网安备 33010602011771号