CompTIA_Security+_2.1_Compare and contrast common threat actors and motivations.
2.1 对比分析常见攻击者及其动机
摘要
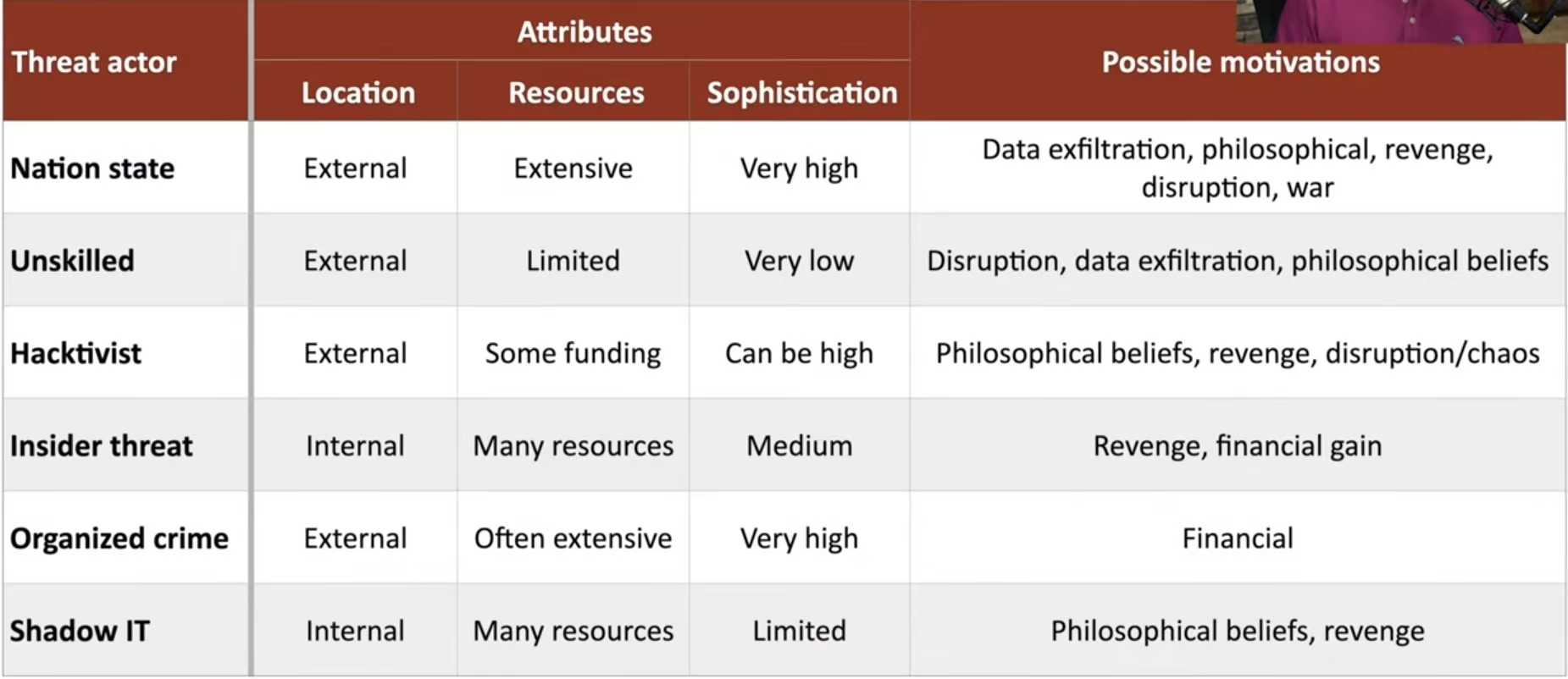
- 2.1.1 Threat actors(攻击者)
- Nation-state(国家行为体)
- Unskilled attacker(脚本小子)
- Hacktivist(黑客行动主义者)
- Insider threat(内部威胁)
- Organized crime(集团犯罪)
- Shadow IT(非授权IT)
- 2.1.2 Attributes of actors(行为体特征)
- Internal/external(内部/外部)
- Resources/funding(资源/资金)
- Level of sophistication/capability(复杂程度/能力)
- 2.1.3 Motivations(动机)
- Data exfiltration(数据窃取)
- Espionage(间谍活动)
- Service disruption(服务中断)
- Blackmail(勒索)
- Financial gain(经济利益)
- Philosophical/political beliefs(意识形态与政治信仰)
- Ethical(符合道德准则与职业操守的)
- Revenge(报复)
- Disruption/chaos(破坏与制造混乱)
- War(战争)
2.1.1 Threat actors(攻击者)
The entity(实体)responsible for an event that has an impact on the safety of another entity
- Also called a malicious(恶意)actor
Threat actor attributes(特性)
- Describes characteristics of the attacker
Useful(有助于)to categorize(分类)the motivation
- Why is this attack happening?
- Is this directed(有目的的)or random?
2.1.2 Attributes of threat actors
Internal/external
- The attacker in inside the house
- They're outside and trying to get in
Resources/funding(资金)
- No money
- Extensive funding(大量资金投入)
Level of sophistication(复杂程度)/capability(能力水平)
- Blindly(盲目地)runs scripts or automated vulnerability scans
- Can write their own attack malware(恶意软件)and scripts(脚本)
2.1.3 Motivations of threat actors
What makes them tick?(是什么让他们如此行事?)
- There's a purpose to this attack
Motivations include
- Data exfiltration(泄露)
- Espionage(间谍活动)
- Service disruption(中断)
- Blackmail(敲诈勒索)
- Finance gain
- Philosophical(哲学)/political beliefs(政治信仰)
- Ethical(道德)
- Revenge(复仇)
- Disruption(混乱)/chaos(动荡)
- War(战争)
Nation states(民族国家)
External entity
- Government and national security
Many possible motivations
- Data exfiltration, philosophical, revenge, disruption, war
Constant(持续不断的)attacks, massive(大量的)resources
- Commonly(通常)an Advanced Persistent Threat (APT)(高级持续性威胁)
Highest sophistication(复杂性)
- Military(军事)control, utilities(公用事业), financial control
- United States and Israel(以色列)destoryed 1,000 nuclear(核)centrifuges(离心机)with Stuxnet worm(震网病毒)
Unskilled attackers
Runs pre-made scripts without any knowledge of what's really happening
- Anyone can do this
Motivated by the hunt(狩猎)
- Disruption, data exfiltration, sometimes philosophical
Can be internal or external
- But usually external
Not very sophisticated(精明)
- Limited resources, if any(如果有的话)
No formal(正式的)funding(资助)
- Looking for low hanging fruit(容易实现的目标)
Hacktivist
A hacker with a purpose
- Motivated by phillosophy, revenge, disruption, etc.
Often an external entity
- Could potentially infiltrate(渗透)to also be an insider threat
Can be remarkably(非常地)sophisticated(复杂)
- Very specific hacks
- DoS, web site defacing(篡改), private document release(泄露)
Funding may be limited
- Some organications have fundraising(筹款)options
Insider threat
More than just passwords on sticky notes(便签纸)
- Motivated by revenge, finance gain
Extensive resources
- Using the organization's resources against themselves
An internal entity
- Eating away from the inside(从内部侵蚀破坏)
Medium(中等)level of sophistication
- The insider has institutional(专业的)knowledge
- Attacks can be directed(针对)at vulnerable(易受攻击的)systems
- The insider knows what to hit(打击)
Organized crime
Professional criminals
- Motivated by money
- Almost(几乎)always an external entity
Very sophisticated
- Best hacking money can buy
Crime that's organized
- One person hacks, one person manages the exploits(处理漏洞), another person sells the data, another handles customer support
Lots of capital(资金)to fund(资助)hacking efforts
Shadow IT
Going rogue(违反规则)
- Working around the internal IT organization
- Builds their own infrastructure(基础设施)
Information Technology can put up(设置)roadblocks(障碍)
- Shadow IT is unencumbered(不受影响)
- Use the cloud
- Might also be able to innovate(创新)
Limited resources
- Company budget(预算)
Medium sophistication
- May not have IT training or knowledge
Threat actors



 浙公网安备 33010602011771号
浙公网安备 33010602011771号