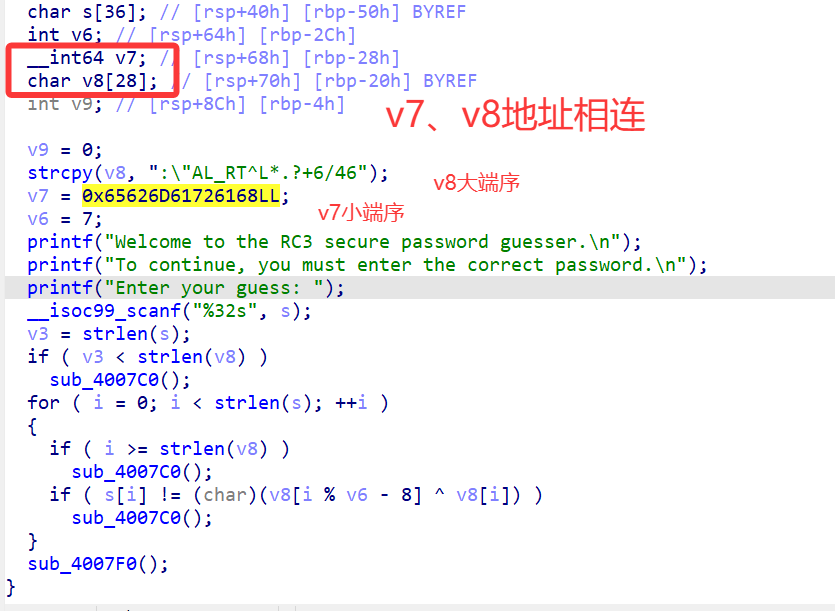
用鼠标点v7的数值,然后按R,将十六进制数转为对应ASCII码字符
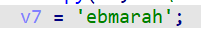
用HEX视图看是大端序还是小端序
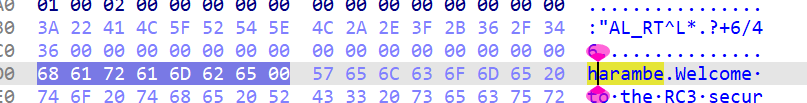
认真阅读代码后,编写以下代码反解出flag
def crack_rc3_password():
# 1. 校验模板v8的ASCII值(索引0-16)
v8_ascii = [
0x3A, 0x22, 0x41, 0x4C, 0x5F, 0x52, 0x54, 0x5E, 0x4C,
0x2A, 0x2E, 0x3F, 0x2B, 0x36, 0x2F, 0x34, 0x36
]
# 2. 密钥字节(v7的小端存储,循环使用):h(0x68),a(0x61),r(0x72),a(0x61),m(0x6D),b(0x62),e(0x65)
key_bytes = [0x68, 0x61, 0x72, 0x61, 0x6D, 0x62, 0x65]
# 3. 逐字符计算密码
password = []
for i in range(17): # 输入长度必须为17
key_idx = i % 7# 循环取密钥字节
s_char_ascii = key_bytes[key_idx] ^ v8_ascii[i]
password.append(chr(s_char_ascii))
return ''.join(password)
# 执行破解
flag = crack_rc3_password()
print(f"RC3正确密码(flag):{flag}")
解得flag为:RC3-2016-XORISGUD






 浙公网安备 33010602011771号
浙公网安备 33010602011771号