bWAPP——20201111
html injection-reflected(GET)
初级
function htmli($data)
{
switch($_COOKIE["security_level"])
{
case "0" :
$data = no_check($data);
break;
case "1" :
$data = xss_check_1($data);
break;
case "2" :
$data = xss_check_3($data);
break;
default :
$data = no_check($data);
break;
}
此处根据选择难度来给定函数,没有过滤可直接输入xss代码
中级
中级对应xss_check_1函数
function xss_check_1($data)
{
// Converts only "<" and ">" to HTLM entities
$input = str_replace("<", "<", $data);
$input = str_replace(">", ">", $input);
// Failure is an option
// Bypasses double encoding attacks
// <script>alert(0)</script>
// %3Cscript%3Ealert%280%29%3C%2Fscript%3E
// %253Cscript%253Ealert%25280%2529%253C%252Fscript%253E
$input = urldecode($input);
return $input;
}
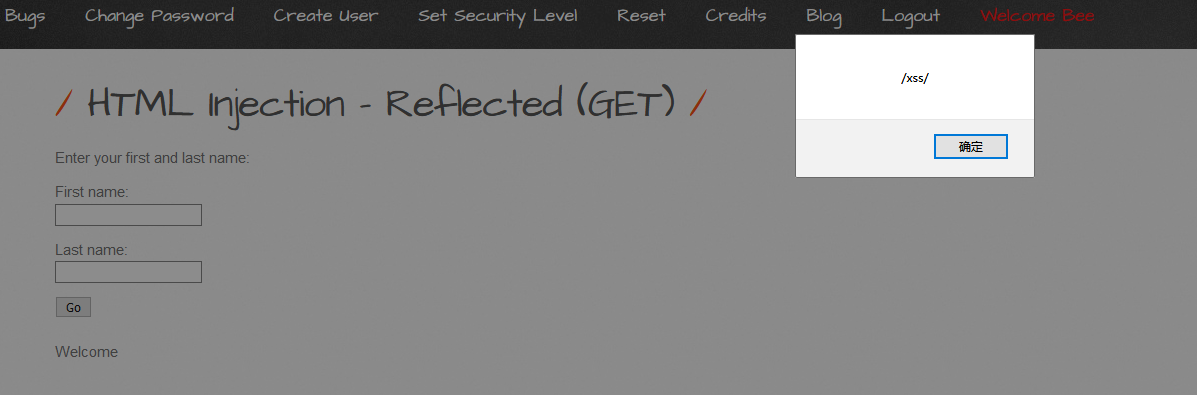
分析源码,这里是进行了url编码,把刚才的xss语句url编码后再提交%3c%73%63%72%69%70%74%3e%61%6c%65%72%74%28%2f%78%73%73%2f%29%3c%2f%73%63%72%69%70%74%3e弹窗成功
高级
这里把我们的符号都设置成实体了,所以这是安全的
function xss_check_3($data, $encoding = "UTF-8")
{
// htmlspecialchars - converts special characters to HTML entities
// '&' (ampersand) becomes '&'
// '"' (double quote) becomes '"' when ENT_NOQUOTES is not set
// "'" (single quote) becomes ''' (or ') only when ENT_QUOTES is set
// '<' (less than) becomes '<'
// '>' (greater than) becomes '>'
return htmlspecialchars($data, ENT_QUOTES, $encoding);
}
html injection-reflected(POST)
操作与get型相同
html injection-reflected(url)
低级
核心代码
<div id="main">
<h1>HTML Injection - Reflected (URL)</h1>
<?php echo "<p align=\"left\">Your current URL: <i>" . $url . "</i></p>";?>
</div>
防护代码
$url= "";
switch($_COOKIE["security_level"])
{
case "0" :
// $url = "http://" . $_SERVER["HTTP_HOST"] . urldecode($_SERVER["REQUEST_URI"]);
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"]; //$url= ''接受的参数来自请求头HOST和URL
break;
case "1" :
$url = "<script>document.write(document.URL)</script>";
break;
case "2" :
$url = "http://" . $_SERVER["HTTP_HOST"] . xss_check_3($_SERVER["REQUEST_URI"]);
break;
default :
// $url = "http://" . $_SERVER["HTTP_HOST"] . urldecode($_SERVER["REQUEST_URI"]);
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"];
break;
}
<select name="security_level">
<option value="0">low</option>
<option value="1">medium</option>
<option value="2">high</option>
</select>
查看源码
switch($_COOKIE["security_level"])
{
case "0" :
// $url = "http://" . $_SERVER["HTTP_HOST"] . urldecode($_SERVER["REQUEST_URI"]);
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"];
break;
case "1" :
$url = "<script>document.write(document.URL)</script>";
break;
case "2" :
$url = "http://" . $_SERVER["HTTP_HOST"] . xss_check_3($_SERVER["REQUEST_URI"]);
break;
default :
// $url = "http://" . $_SERVER["HTTP_HOST"] . urldecode($_SERVER["REQUEST_URI"]);
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"];
break;
}
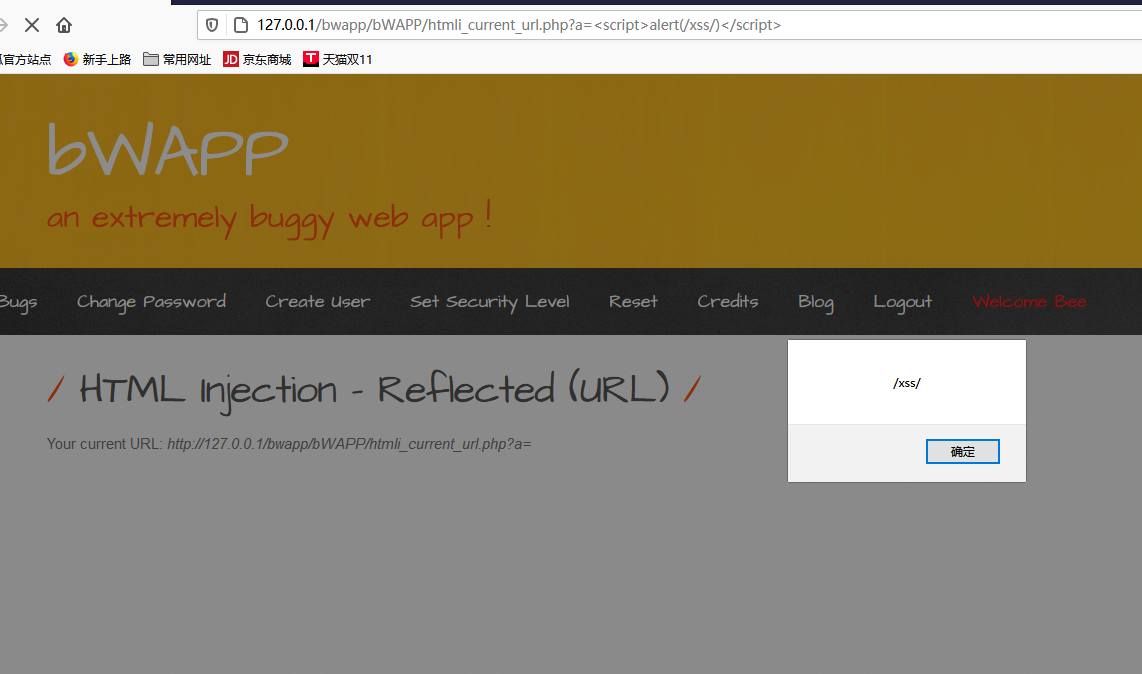
根据要求是要构造url:/bwapp/bWAPP/htmli_current_url.php?a=
中级
$url = "";
这里document对象 -- 代表整个HTML 文档,可用来访问页面中的所有元素;
document.URL是 设置URL属性从而在同一窗口打开另一网页;
document.write() 是动态向页面写入内容。
此时再通过前面的方式抓包改包,已经不起作用了。
在low和medium等级下,是没有做任何防护的,都是直接获取url然后将其直接输出,可以在连接中添加代码实现弹框,这里是ie禁用了部分js脚本,导致了弹框失败。
高级
在high等级下,执行
$url = "http://" . $_SERVER["HTTP_HOST"] . xss_check_3($_SERVER["REQUEST_URI"]);
其中调用了xss_check_3函数对host后面的部分进行了过滤处理,使得无法进行注入。
function xss_check_3($data, $encoding = "UTF-8")
{
// htmlspecialchars - converts special characters to HTML entities
// '&' (ampersand) becomes '&'
// '"' (double quote) becomes '"' when ENT_NOQUOTES is not set
// "'" (single quote) becomes ''' (or ') only when ENT_QUOTES is set
// '<' (less than) becomes '<'
// '>' (greater than) becomes '>'
return htmlspecialchars($data, ENT_QUOTES, $encoding);
}
iFrame Injection
低级
这里给到一个留言板功能,插入xss语句尝试弹窗
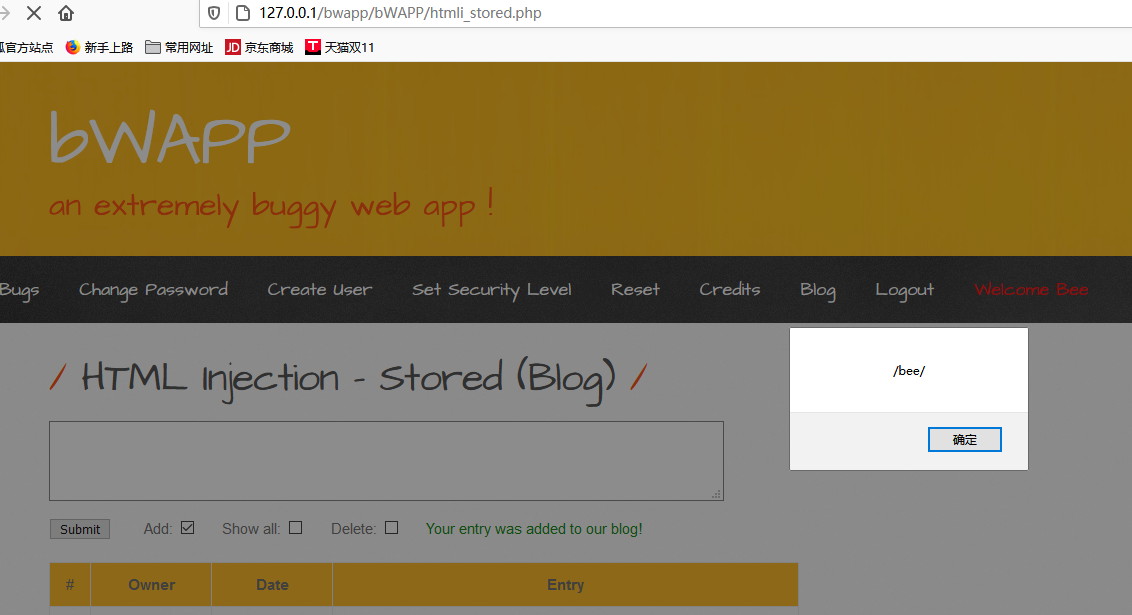
也可以尝试读取用户cookie
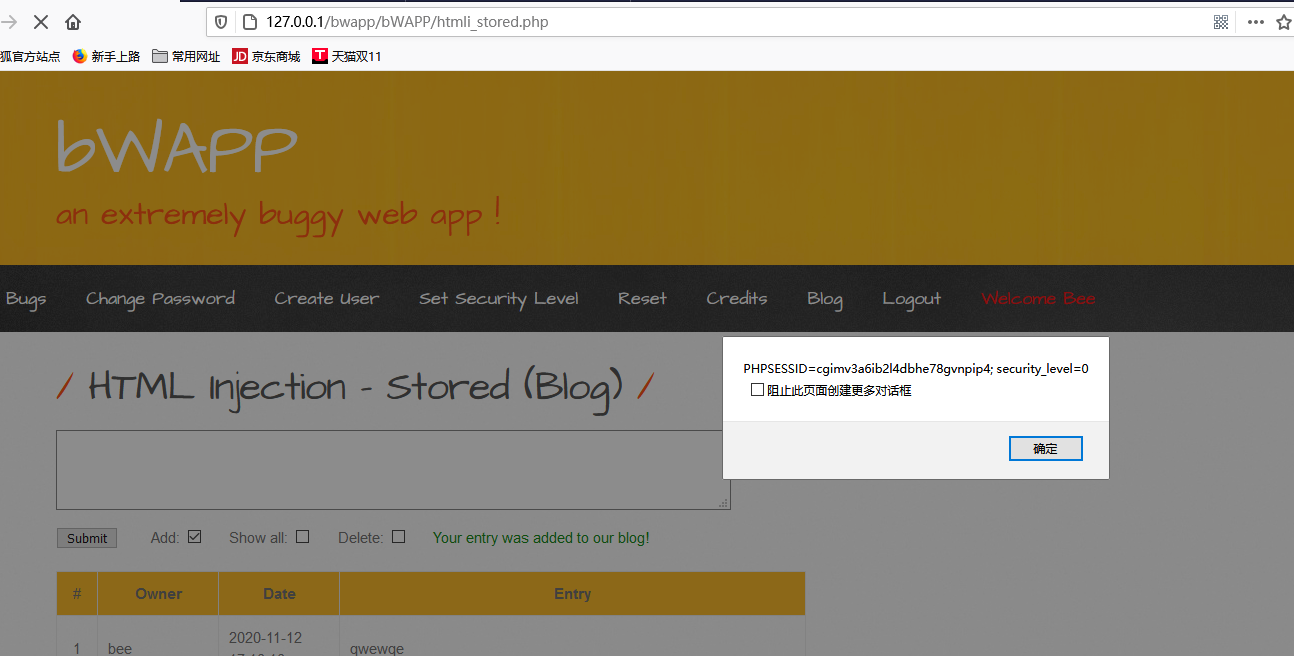
根据源码找到数据存储的地方
else
{
$sql = "INSERT INTO blog (date, entry, owner) VALUES (now(),'" . $entry . "','" . $owner . "')";
$recordset = $link->query($sql);
存在html注入漏洞
在查看源码后,三个级别都使用了sqli_check_3函数进行语句转义
switch($_COOKIE["security_level"])
{
case "0" :
$data = sqli_check_3($link, $data);
break;
case "1" :
$data = sqli_check_3($link, $data);
// $data = xss_check_4($data);
break;
case "2" :
$data = sqli_check_3($link, $data);
// $data = xss_check_3($data);
break;
default :
$data = sqli_check_3($link, $data);
break;
}
function sqli_check_3($link, $data)
{
return mysqli_real_escape_string($link, $data);
}
下列字符受影响:
\x00
\n
\r
'
"
\x1a
如果成功,则该函数返回被转义的字符串。如果失败,则返回 false。
中级
当设置等级为medium时,调用xss_check_4进行防xss保护
function xss_check_4($data)
{
// addslashes - returns a string with backslashes before characters that need to be quoted in database queries etc.
// These characters are single quote ('), double quote ("), backslash (\) and NUL (the NULL byte).
// Do NOT use this for XSS or HTML validations!!!
return addslashes($data);
}
高级
当设置等级为high时,调用xss_check_3进行防xss保护
function xss_check_3($data, $encoding = "UTF-8")
{
// htmlspecialchars - converts special characters to HTML entities
// '&' (ampersand) becomes '&'
// '"' (double quote) becomes '"' when ENT_NOQUOTES is not set
// "'" (single quote) becomes ''' (or ') only when ENT_QUOTES is set
// '<' (less than) becomes '<'
// '>' (greater than) becomes '>'
return htmlspecialchars($data, ENT_QUOTES, $encoding);
}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号