K8S脉络整理(017)-kubernetes Dashboard
基于
使用Kubespray在ubuntu上自动部署K8s1.9.0集群
完成部署后,dashboard已部署,但对应service为cluster-ip,外部无法访问。
daweij@master:~$ kubectl get svc --namespace=kube-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE kube-dns ClusterIP 10.233.0.3 <none> 53/UDP,53/TCP 59d kubernetes-dashboard ClusterIP 10.233.44.80 <none> 443/TCP 59d tiller-deploy ClusterIP 10.233.60.111 <none> 44134/TCP 3d daweij@master:~$ kubectl get deployment --namespace=kube-system NAME DESIRED CURRENT UP-TO-DATE AVAILABLE AGE kube-dns 2 2 2 2 59d kubedns-autoscaler 1 1 1 1 59d kubernetes-dashboard 1 1 1 1 59d tiller-deploy 1 1 1 1 3d
为方便使用,可通过kubectl --namespace=kube-system edit service kubernetes-dashboard 修改为NodePort类型。
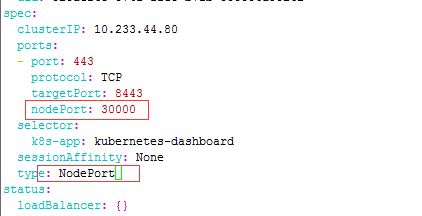
再次查看,已为service分配了端口30000,:
daweij@master:~$ kubectl get svc --namespace=kube-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE kube-dns ClusterIP 10.233.0.3 <none> 53/UDP,53/TCP 59d kubernetes-dashboard NodePort 10.233.44.80 <none> 443:30000/TCP 59d tiller-deploy ClusterIP 10.233.60.111 <none> 44134/TCP 3d
通过浏览器可访问Dashboar https://172.28.2.210:30000
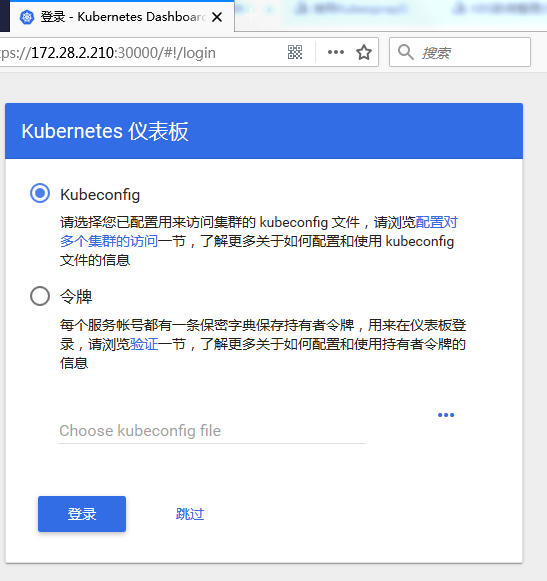
配置登陆权限 (参考配置user和role:https://blog.csdn.net/qq_34463875/article/details/78728041)
k8s里面有两种用户,一种是User,一种就是service account,User给人用的,service account给进程用的,让进程有相关的权限。
如dasboard就是一个进程,我们就可以创建一个service account给它,让它去访问k8s。
第一种方法:默认用户赋予admin权限
我们看一下是如何把admin权限赋给dashboard的:Dashboard支持kubeconfig和Token两种认证方式,为了简化配置,可通过配置文件dashboard-admin.yaml为Dashboard默认用户赋予admin权限。
daweij@master:~/config$ cat dashboard-admin.yaml apiVersion: rbac.authorization.k8s.io/v1beta1 kind: ClusterRoleBinding metadata: name: kubernetes-dashboard labels: k8s-app: kubernetes-dashboard roleRef: apiGroup: rbac.authorization.k8s.io kind: ClusterRole name: cluster-admin subjects: - kind: ServiceAcount name: kubernetes-dashboard namespace: kube-system
把 kubernetes-dashboard 这个ServiceAccount绑定到cluster-admin这个ClusterRole上,这个cluster role非常牛逼,啥权限都有
daweij@master:~/config$ kubectl describe clusterrole cluster-admin -n kube-system Name: cluster-admin Labels: kubernetes.io/bootstrapping=rbac-defaults Annotations: rbac.authorization.kubernetes.io/autoupdate=true PolicyRule: Resources Non-Resource URLs Resource Names Verbs --------- ----------------- -------------- ----- [*] [] [*] *.* [] [] [*]
而创建dashboard时创建了这个service account:
apiVersion: v1 kind: ServiceAccount metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-system
然后deployment里指定service account
daweij@master:~/config$ kubectl --namespace=kube-system edit deployment kubernetes-dashboard --- dnsPolicy: ClusterFirst restartPolicy: Always schedulerName: default-scheduler securityContext: {} serviceAccount: kubernetes-dashboard serviceAccountName: kubernetes-dashboard terminationGracePeriodSeconds: 30 tolerations: - effect: NoSchedule key: node-role.kubernetes.io/master volumes: - name: kubernetes-dashboard-certs secret: defaultMode: 420 secretName: kubernetes-dashboard-certs - emptyDir: {} name: tmp-volume
若通过配置文件dashboard-admin.yaml为Dashboard默认用户赋予admin权限,执行kubectl apply 使之生效,然后点击登录页面的SKIP就可以登录Dashboard了。
第二种方法:更安全的方法 token
daweij@master:~/config$ cat admin-token.yaml kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1beta1 metadata: name: admin annotations: rbac.authorization.kubernetes.io/autoupdate: "true" roleRef: kind: ClusterRole name: cluster-admin apiGroup: rbac.authorization.k8s.io subjects: - kind: ServiceAccount name: admin namespace: kube-system --- apiVersion: v1 kind: ServiceAccount metadata: name: admin namespace: kube-system labels: kubernetes.io/cluster-service: "true" addonmanager.kubernetes.io/mode: Reconcile
daweij@master:~/config$ kubectl apply -f admin-token.yaml clusterrolebinding "admin" created serviceaccount "admin" created daweij@master:~/config$ kubectl get secret -n kube-system|grep admin admin-token-lfmnj kubernetes.io/service-account-token 3 43s daweij@master:~/config$ kubectl describe secret admin-token-lfmnj -n kube-system Name: admin-token-lfmnj Namespace: kube-system Labels: <none> Annotations: kubernetes.io/service-account.name=admin kubernetes.io/service-account.uid=82979988-3628-11e8-bfaf-005056a90262 Type: kubernetes.io/service-account-token Data ==== ca.crt: 1090 bytes namespace: 11 bytes token: eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi10b2tlbi1sZm1uaiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjgyOTc5OTg4LTM2MjgtMTFlOC1iZmFmLTAwNTA1NmE5MDI2MiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTphZG1pbiJ9.ml-BptH9YLS2uBOJSaH9OcXKc3i2AgEMyxRlgICCXyYJWIyfu6uOQHxXYULl4uVn6EpDdtHtfGa6t3XclEJVyqO6dVyGV2auYQbvnjLLny_gM93yzhTsFgLwARTzUgfsqzoligxYcEL0vPAwOw1jBNg6pw5A5s4n0aF14K-EooEKaEcDSLlmS_k-ZWrv8gtEr9Bw40RfcaBqYuFUzTj0lUwMfcy3qFT6ch1J-J7YwdqbndZZ6cyTkuGnZvWzP4nCTBxd0YeicwtxNfhAzJklf0WAKTRLPVVDjwYCDLJA4z8lsIWeByJoQGYNvoYXnOgjHEIxRKQKvmJ_AjcCQP2bvw
查看令牌token:
kubectl -n kube-system describe secret $(kubectl get secret -n kube-system|grep admin | awk '{print $1}')
用此token在界面上登录即可(即令牌)
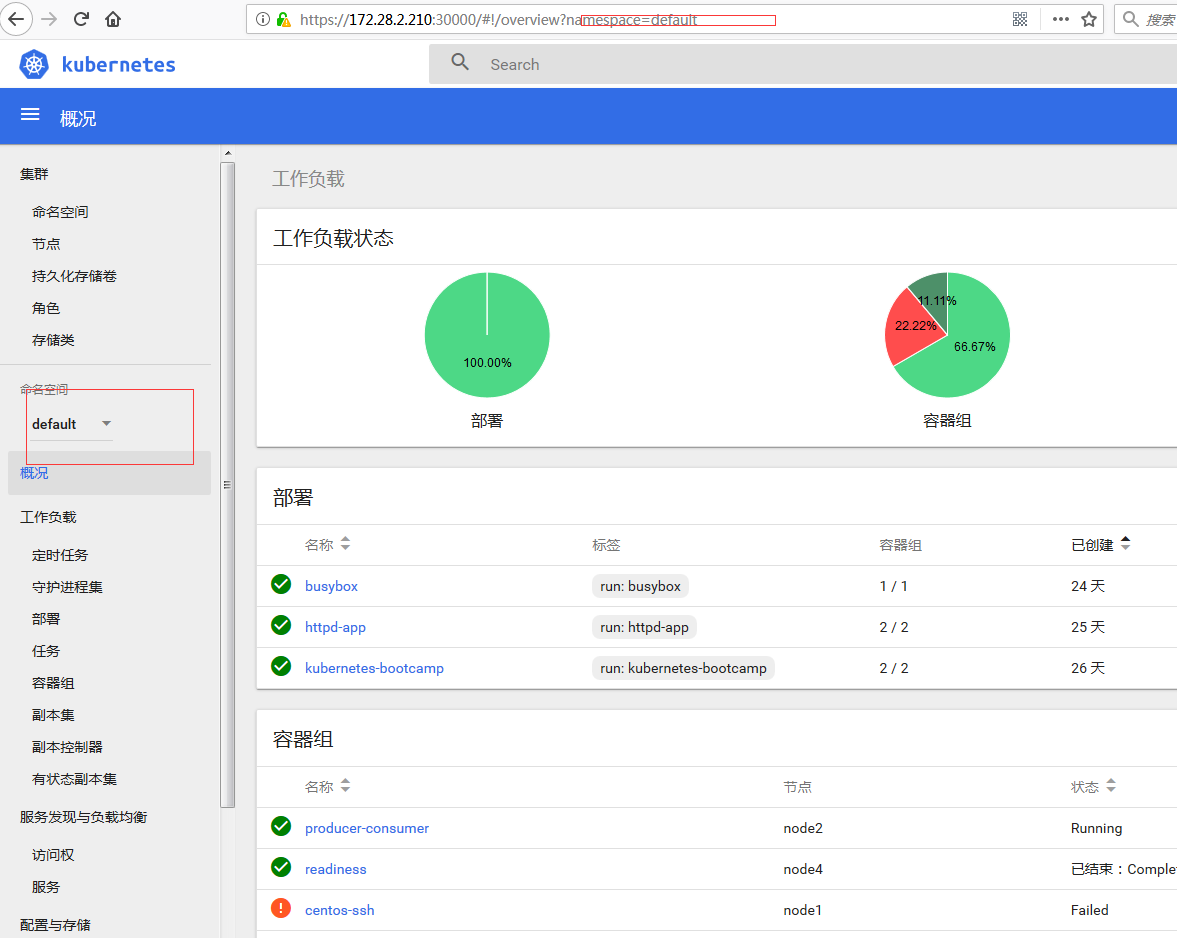
可根据需要创建(view 或 edit) service-account 并查看令牌。
Dashboard能完成日常管理的大部分工作,可以作为命令行工具kubectl的有益补充。
如:部署deployment、每种资源的在线操作(查看/编辑yaml)、查看资源详细信息、查看Pod日志等。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号