Linux安全-通过修改/etc/hosts.deny拒绝远程ssh暴力破解
1.备份/etc/hosts.deny到/root/hosts.deny.tmp
\cp /etc/hosts.deny /root/hosts.deny.tmp
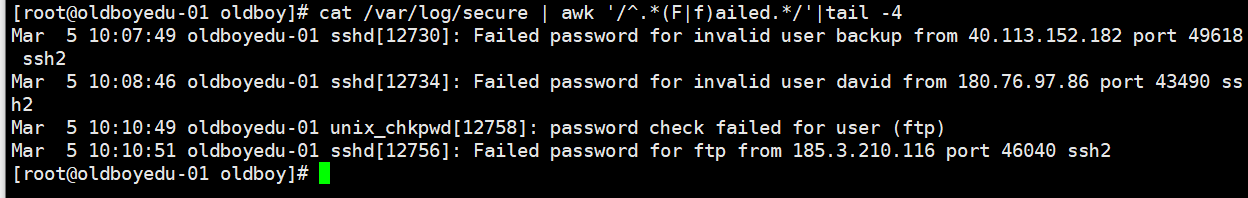
2.过滤出/ar/log/secure中的错误链接:
cat /var/log/secure | awk '/^.*(F|f)ailed.*/'|tail -4
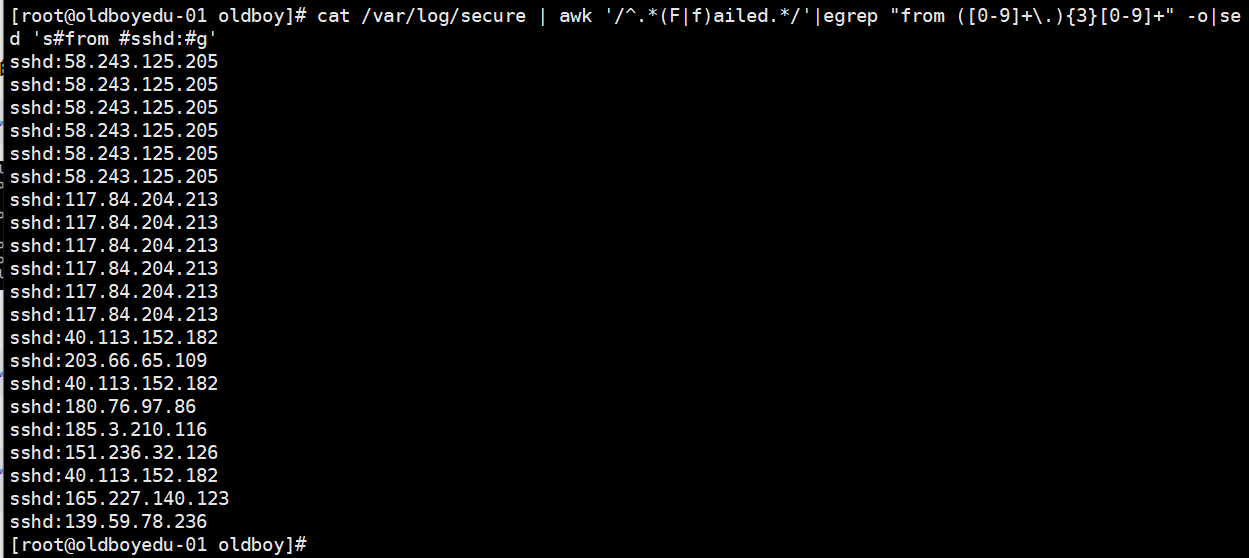
3.从1中过滤出来IP地址:
cat /var/log/secure | awk '/^.*(F|f)ailed.*/'|egrep "from ([0-9]+\.){3}[0-9]+" -o
4.留下from 好替换成sshd:
cat /var/log/secure | awk '/^.*(F|f)ailed.*/'|egrep "from ([0-9]+\.){3}[0-9]+" -o|sed 's#from #sshd:#g'
5.追加到临文件hosts.deny.tmp中:
cat /var/log/secure | awk '/^.*(F|f)ailed.*/'|egrep "from ([0-9]+\.){3}[0-9]+" -o|sed 's#from #sshd:#g' >> /root/hosts.deny.tmp
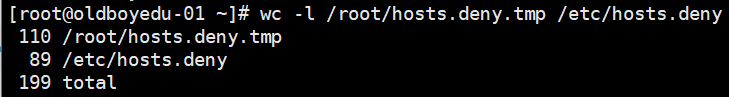
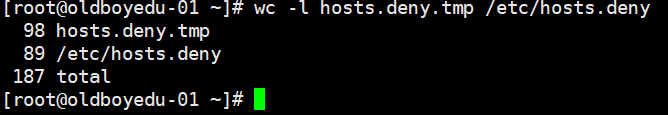
5.对比两个文件:
wc -l /root/hosts.deny.tmp /etc/hosts.deny
6.去除/root/hosts.deny.tmp重复项:
sort /root/hosts.deny.tmp|uniq -w 15 #或者sort -u /root/hosts.deny.tmp sort -u /root/hosts.deny.tmp -o hosts.deny.tmp #去除重复并写入
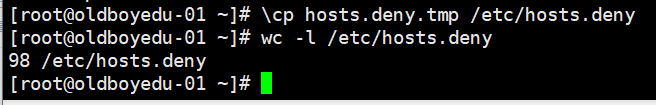
7.覆盖回/etc/hosts.deny
\cp hosts.deny.tmp /etc/hosts.deny