NewStar2024 re wp
week3
011vm
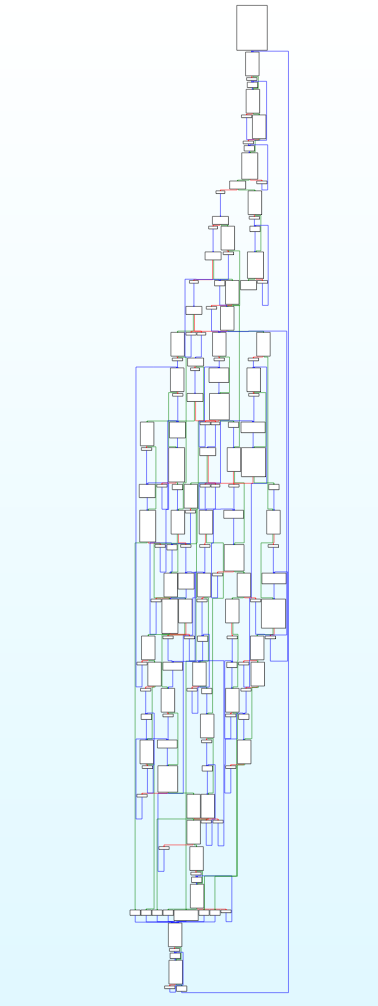
main函数有控制流平坦化的特征
可以用D-810去
但是ida9.0自动去了
8.3打开长这个样子
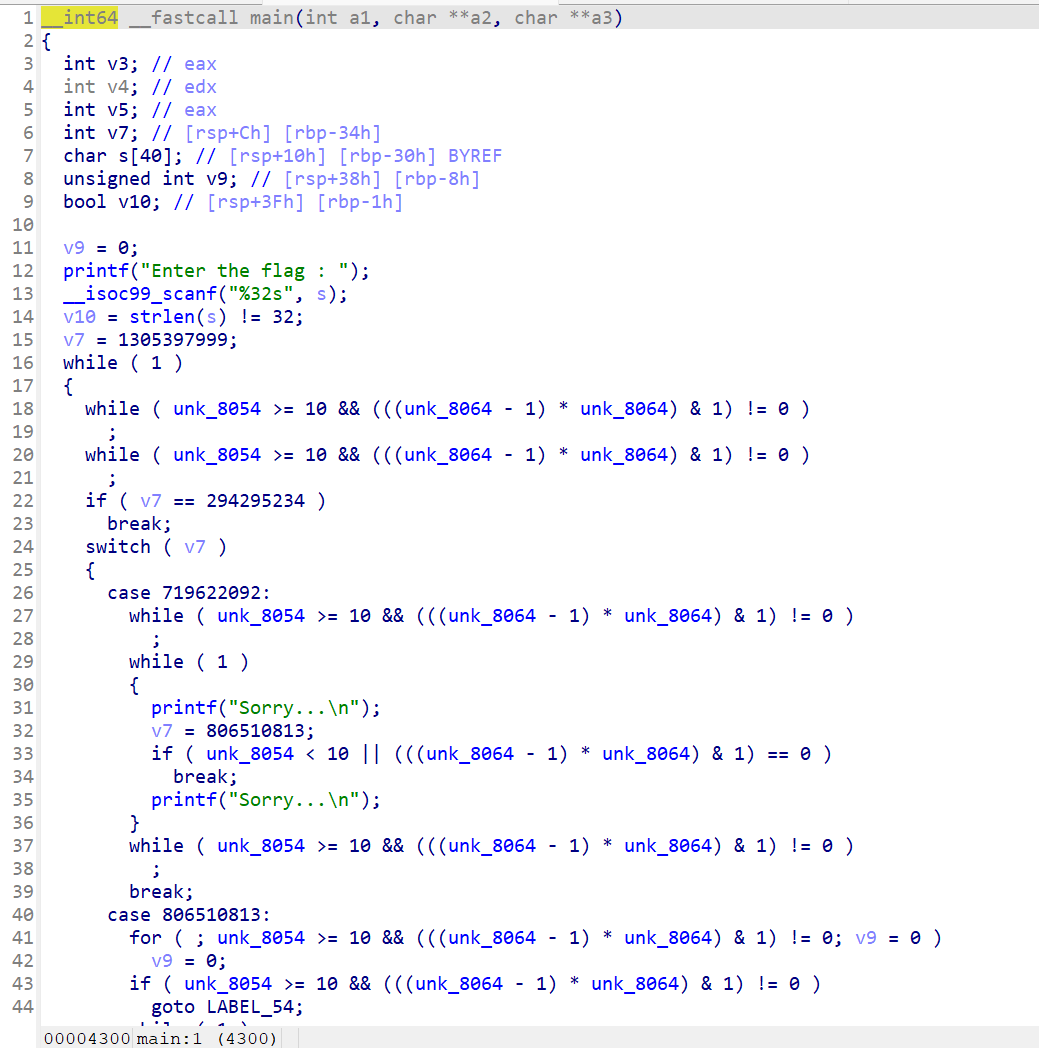
但是9.0打开就是

进判断处的函数

sub_1170是tea加密
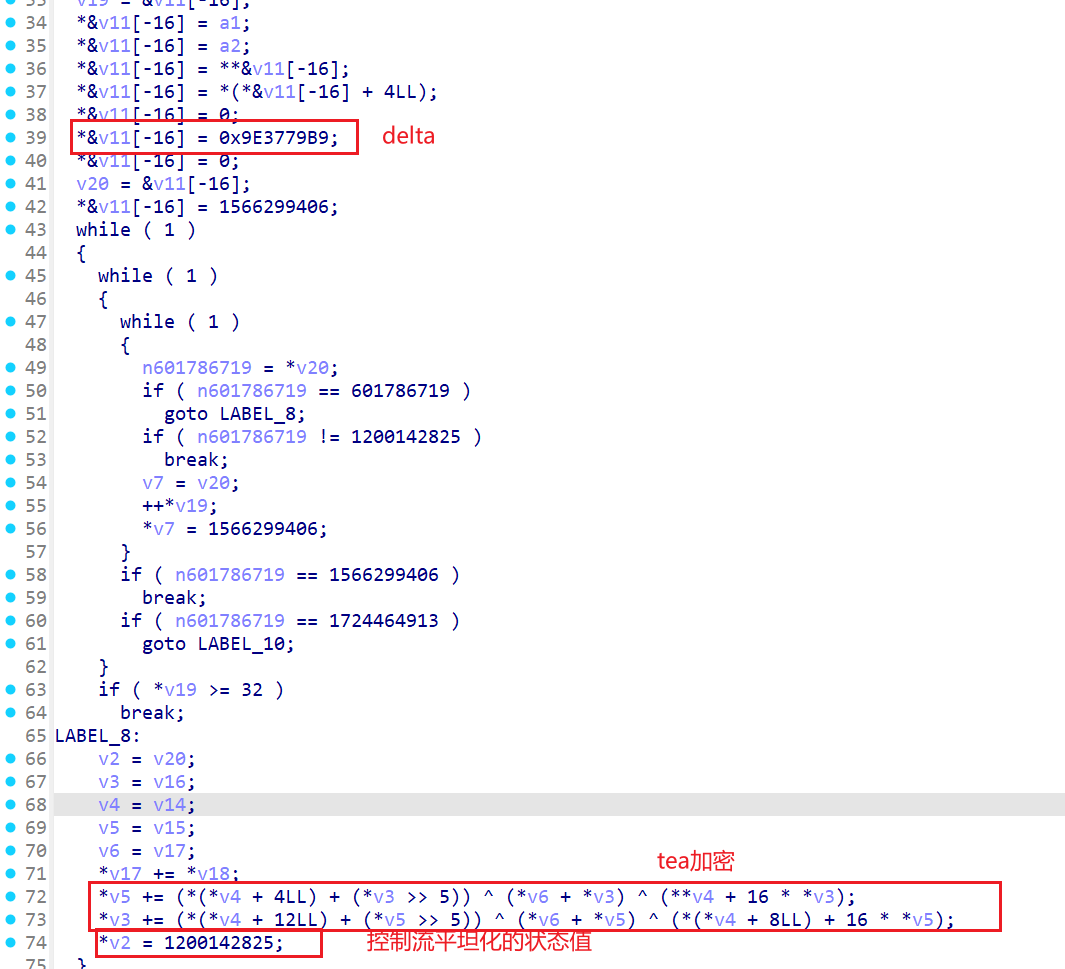
标准的
#include <stdio.h>
#include <stdint.h>
void decrypt (uint32_t *v,uint32_t *k){
uint32_t delta=0x9e3779b9;
uint32_t v0=v[0],v1=v[1],sum=delta * 32,i;
uint32_t k0=k[0],k1=k[1],k2=k[2],k3=k[3];
for (i=0;i<32;i++){
v1-=((v0<<4)+k2)^(v0+sum)^((v0>>5)+k3);
v0-=((v1<<4)+k0)^(v1+sum)^((v1>>5)+k1);
sum-=delta;
}
v[0]=v0;v[1]=v1;
}
int main()
{
uint32_t v[8]={0x38B97E28,0xB7E510C1,0xB4B29FAE,0x5593BBD7,0x3C2E9B9E,0x1671C637,0x8F3A8CB5,0x5116E515};
uint32_t k[4]={0x11121314,0x22232425,0x33343536,0x41424344};
for(int i=0;i<4;i++){
uint32_t temp[2] = {v[i*2],v[i*2+1]};
decrypt(temp,k);
printf("%.8s", (char*)temp);
}
return 0;
}
flag:flag{011vm_1s_eZ_But_C0MP1EX_!!}
PangBai 过家家(3)
python逆向,强烈推荐pyinstxtractor-ng.exe解包(可以忽略环境问题)
https://pylingual.io/ 在线网站,pyc反编译
import sys
print('Welcome to NewStar~')
print('Please input the flag:')
enc = [40, 9, 22, 52, 15, 56, 66, 71, 111, 121, 90, 33, 18, 40, 3, 13, 80, 28, 65, 68, 83, 88, 34, 86, 5, 12, 35, 82, 67, 3, 17, 79]
key = 'NewStar2024'
input = input('> ')
if len(input) != len(enc):
print('Wrong flag, try again!')
sys.exit(0)
for i in range(len(input)):
if enc[i] != ord(input[i]) ^ ord(key[i % len(key)]):
print('Wrong flag, try again!')
sys.exit(0)
print('Correct flag!')
异或
enc = [40, 9, 22, 52, 15, 56, 66, 71, 111, 121, 90, 33, 18, 40, 3, 13, 80, 28, 65, 68, 83, 88, 34, 86, 5, 12, 35, 82, 67, 3, 17, 79]
key = 'NewStar2024'
for i in range(len(enc)):
print(chr(enc[i] ^ ord(key[i % len(key)])), end='')
flag:flag{Y0u_Know_Py1nstall3r_W311!}
SMc_math
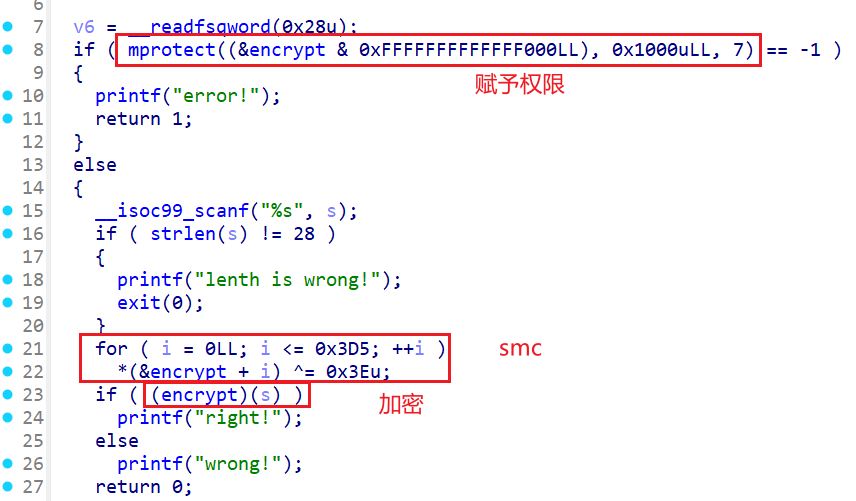
函数原型int mprotect(void *addr, size_t len, int prot);
自修改代码,用idc脚本跑一下
auto addr = 0x11E9;
auto i = 0;
for(i;i <= 0x3d5; i++){
PatchByte(addr+i,Byte(addr+i) ^ 0x3e);
}

z3解密
from z3 import *
# 创建求解器
s = Solver()
# 定义变量(假设有30个变量)
a = [Int(f'a_{i}') for i in range(7)]
# 添加约束
s.add(5 * (a[1] + a[0]) + 4 * a[2] + 6 * a[3] + a[4] + 9 * a[6] + 2 * a[5] == 0xD5CC7D4FF)
s.add(4 * a[6] + 3 * a[3] + 6 * a[2] + 10 * a[1] + 9 * a[0] + 9 * a[5] + 3 * a[4] == 0x102335844B)
s.add(9 * a[4] + 4 * (a[3] + a[2]) + 5 * a[1] + 4 * a[0] + 3 * a[6] + 10 * a[5] == 0xD55AEABB9)
s.add(9 * a[1] + 5 * a[0] + 9 * a[6] + 2 * (a[2] + 2 * a[3] + 5 * a[4] + a[5]) == 0xF89F6B7FA)
s.add(5 * a[4] + 9 * a[3] + 7 * a[0] + 2 * a[1] + a[2] + 3 * a[6] + 9 * a[5] == 0xD5230B80B)
s.add(8 * a[6] + 6 * a[3] + 10 * a[2] + 5 * a[1] + 6 * a[0] + 3 * a[5] + 9 * a[4] == 0x11E28ED873)
s.add(a[0] + 4 * (a[2] + a[1] + 2 * a[3]) + 9 * a[4] + a[5] + 3 * a[6] == 0xB353C03E1)
# 检查是否有解
if s.check() == sat:
m = s.model()
# 获取解
solution = [m.evaluate(a[i]) for i in range(7)]
print("Solution:", solution)
else:
print("No solution found.")
#Solution: [1734437990, 1596998779, 1601515609, 1999662667, 1129149279, 1148073055, 2100517471]
输出为char型
#include <stdio.h>
#include <stdint.h>
int main(){
uint64_t a[]={1734437990, 1596998779, 1601515609, 1999662667, 1129149279, 1148073055, 2100517471};
for(int i=0;i<7;i++){
printf("%c",a[i] & 0xff);
printf("%c",(a[i] >> 8) & 0xff);
printf("%c",(a[i] >> 16) & 0xff);
printf("%c",(a[i] >> 24) & 0xff);
}
return 0;
}
flag:flag{D0_Y0u_Kn0w_sMC_4nD_Z3}
SecertsOfKawaii
java层有混淆,用jeb看就好,是rc4和base64加密

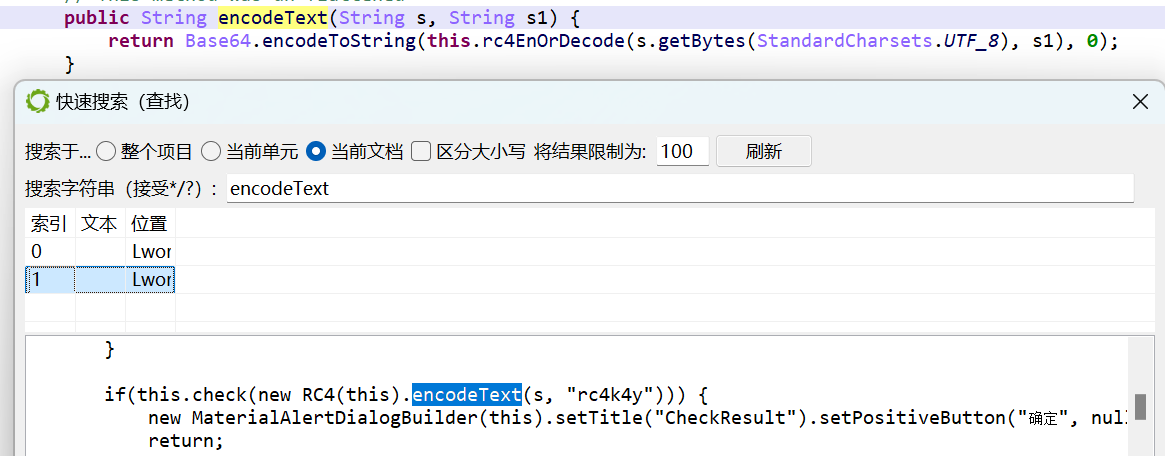
key是rc4k4y
so文件有upx壳

xxtea:https://www.cnblogs.com/zpchcbd/p/15974293.html
#include <stdio.h>
#include <stdint.h>
#define DELTA 0xDEADBEEF
#define MX (((z ^ key[e ^ p & 3]) + (y ^ sum)) ^ (((4 * z) ^ (y >> 3)) + ((8 * y) ^ (z >> 5))))
void btea(uint32_t *v, int n, const uint32_t key[4])
{
uint32_t y, z, sum;
unsigned p, rounds, e;
if (n < -1) /* Decoding Part */
{
n = -n;
rounds = 6 + 52/n;
sum = rounds*DELTA;
y = v[0];
do
{
e = (sum >> 2) & 3;
for (p=n-1; p>0; p--)
{
z = v[p-1];
y = v[p] -= MX;
}
z = v[n-1];
y = v[0] -= MX;
sum -= DELTA;
}
while (--rounds);
}
}
int main() {
uint32_t v[12] = {
0x8C12D3DF, 0x5F4C4137, 0x1A9D3D02, 0x2D1294B7,
0xFB622B37, 0xD18D84E3, 0x064C4592, 0x16985CAB,
0xFDB06D69, 0xFB30B1E3, 0x925C2FD3, 0x2E1BB40C
};
const uint32_t *k = (const uint32_t *)"meow~meow~tea~~~";
btea(v, -12, k);
printf("%s\n", (char *)v);
return 0;
}
//qGioT8ksbvHifioMYdq/hBspRL4CRzFVO/YbgNYdCg==
厨子解

flowering_shrubs
(跟着wp做的)
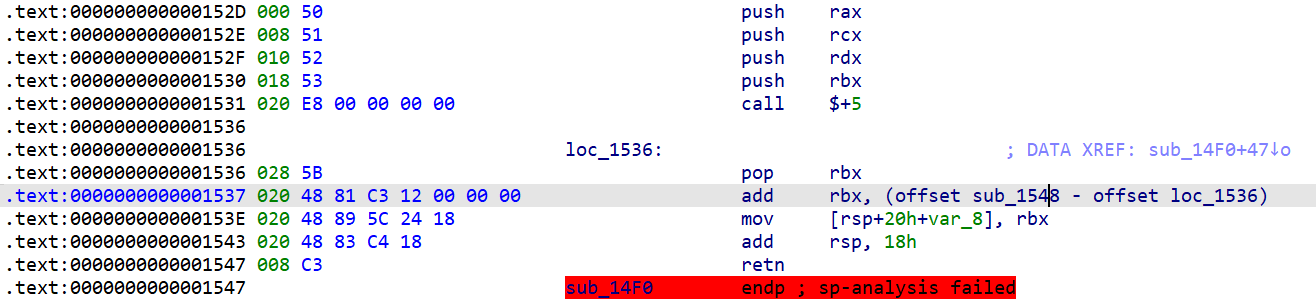
这一段是花指令
大量同样的花指令,用脚本去除
# remove_flower.py
import idc
import idaapi
startaddr=0x1100
endaddr=0x15FF
lis=[0x50, 0x51, 0x52, 0x53, 0xE8, 0x00, 0x00, 0x00, 0x00, 0x5B, 0x48, 0x81, 0xC3, 0x12, 0x00, 0x00, 0x00, 0x48, 0x89, 0x5C, 0x24, 0x18, 0x48, 0x83, 0xC4, 0x18,0xC3]
#这个for循环是关键点,检测以当前地址开始的27个字节是否符合lis列表的内容。
for i in range(startaddr,endaddr):
flag=True
for j in range(i,i+27):
if idc.get_wide_byte(j)!=lis[j-i]:
flag=False
if flag==True:
for addr in range(i,i+27):
idc.patch_byte(addr,0x90) # 将这部分内容全部nop掉
for i in range(startaddr,endaddr):# 取消函数定义
idc.del_items(i)
for i in range(startaddr,endaddr): # 添加函数定义
if idc.get_wide_dword(i)==0xFA1E0FF3: #endbr64
idaapi.add_func(i)


四个字符一组的加密逻辑
可以将这个加密逻辑提出来
a,b,c,d,str
a = a ^ str
b = b ^a
b=b+str mb=(b^a^str) + str
c=c^b c=c^mb
c=c-str mc=(c^mb) - str
d=d^c md=d^mc
a=a^d ma=a^str^md
a=ma^str^md
d=md^mc
c=(mc+str)^mb
b=(mb-str)^a^str
a,b,c,d为flag的4个字节,ma,mb,mc,md是4个加密后的,也就是能够提取出来的数据,str就是uarefirst.
现在我动态调试Linux文件好麻烦〒▽〒
尝试了两天,没有调上,放弃了
所以直接用0,4,32,12,8,24,16,20,28,36
#include<stdio.h>
#include<string.h>
int main() {
int m[] = {0x54,0xF4,0x20,0x47,0xFC,0xC4,0x93,0xE6,0x39,0xE0,0x6E,0x0,0xA5,0x6E,0xAA,0x9F,0x7A,0xA1,0x66,0x39,0x76,0xB7,0x67,0x57,0x3D,0x95,0x61,0x22,0x55,0xC9,0x3B,0x4E,0x4F,0xE8,0x66,0x8,0x3D,0x50,0x43,0x3E};
char flag[40];
char str[] = "uarefirst.";
int buf[] = {0,4,32,12,8,24,16,20,28,36};
for(int i = 0; i < 10; i++) {
int pos = buf[i];
flag[pos] = m[pos] ^ str[i] ^ m[pos + 3];
flag[pos + 3] = m[pos + 3] ^ m[pos + 2];
flag[pos + 2] = ((m[pos + 2] + str[i]) & 0xff) ^ m[pos + 1];
flag[pos + 1] = ((m[pos + 1] - str[i]) & 0xff) ^ flag[pos] ^ str[i];
}
for(int i=0;i<=36;i+=4){
printf("%c%c%c%c",flag[i],flag[i+1],flag[i+2],flag[i+3]);
}
return 0;
}
注意:脚本里面的m和flag数组用pos索引,buf数组用i索引
flag{y0u_C4n_3a51ly_Rem0v3_CoNfu510n-!!}
simpleAndroid
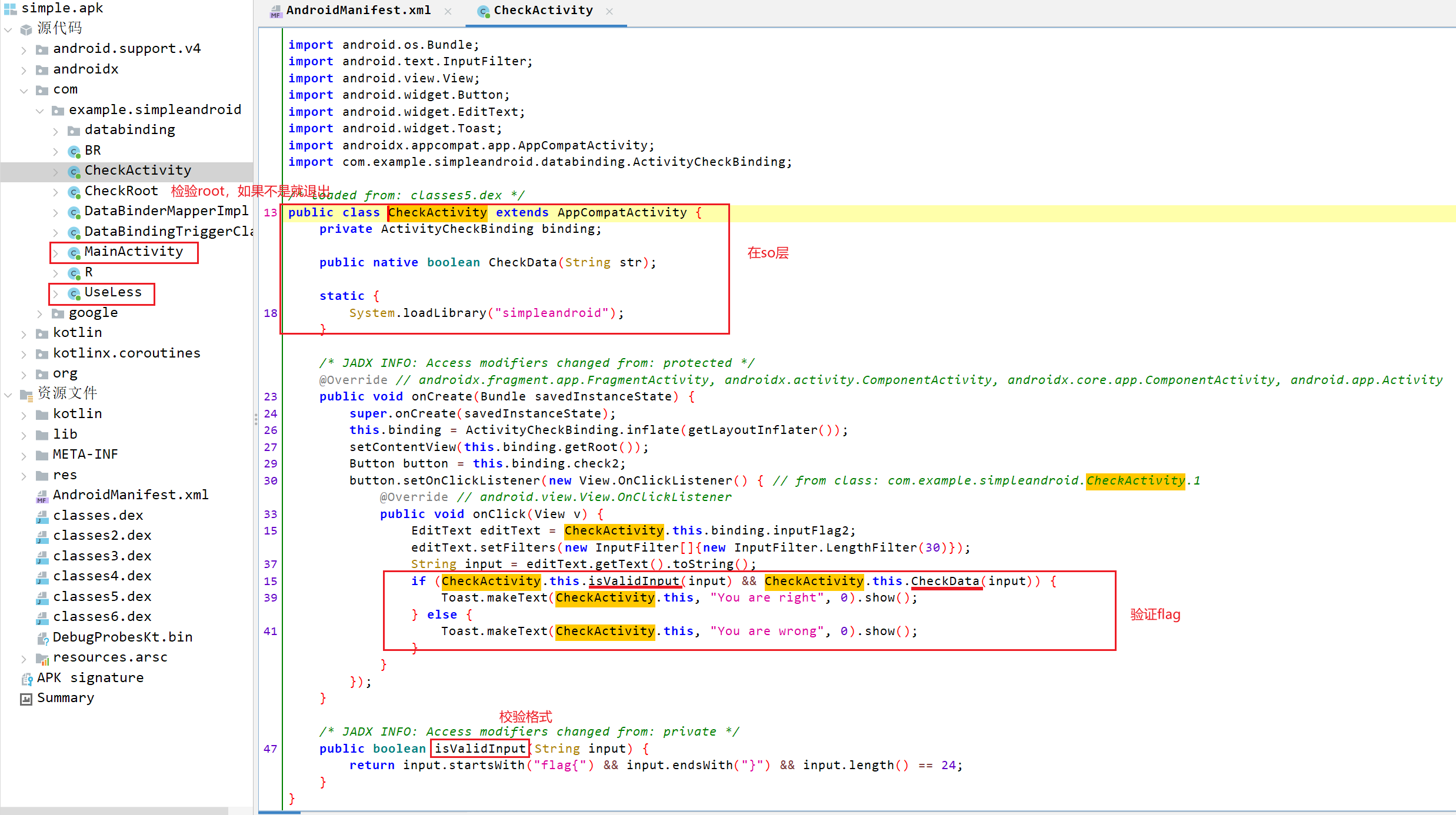
如果打开app点击check的话会退出,能用frida hook掉,但是当我再次尝试的时候失败了,我也没有找到问题(当然也不影响做题)
脚本如下:
Java.perform(function () {
// 获取 CheckRoot 类
var CheckRoot = Java.use("com.example.simpleandroid.CheckRoot");
// Hook checkExistSu() 方法,强制返回 false
CheckRoot.checkExistSu.implementation = function () {
console.log("[*] Bypassing root check...");
return false; // 直接返回 false,绕过检测
};
// 也可以直接 Hook check() 方法,让它返回 false
CheckRoot.check.implementation = function () {
console.log("[*] Bypassing root check...");
return false;
};
});
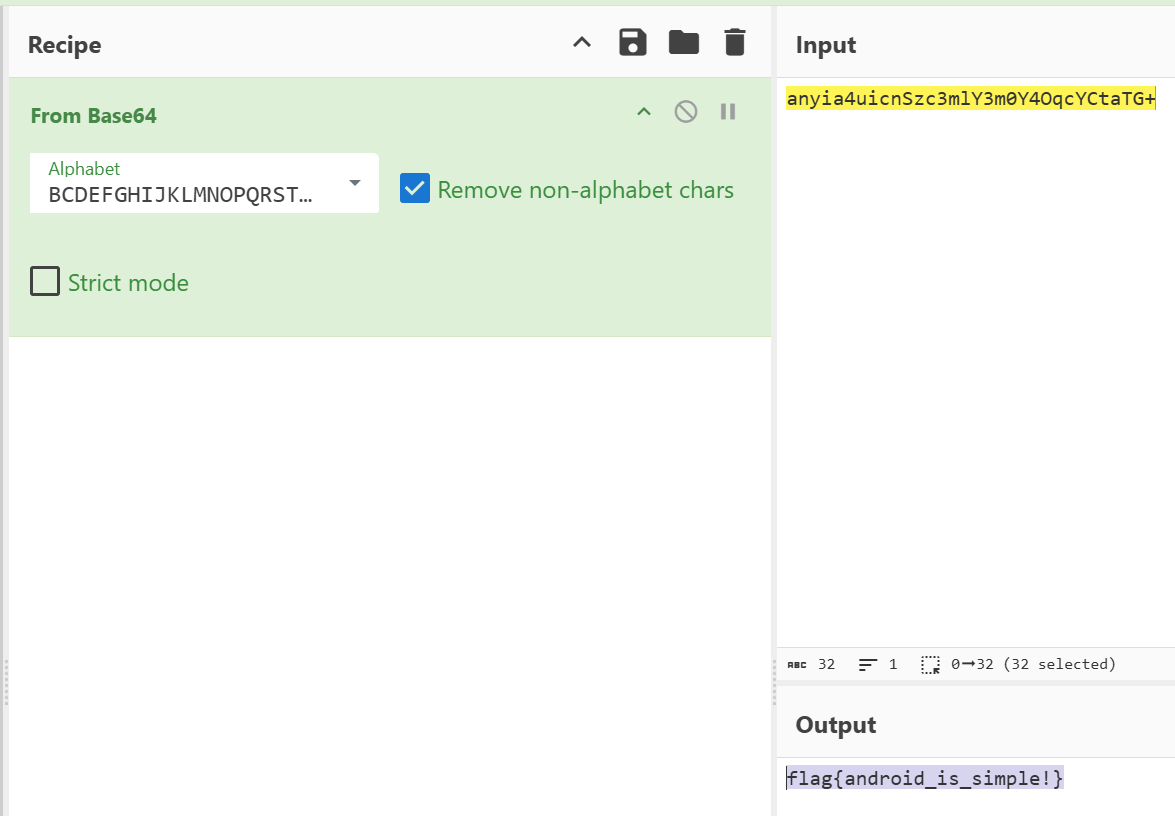
UseLess函数是标准base64加密
再去so层
直接找CheckData函数
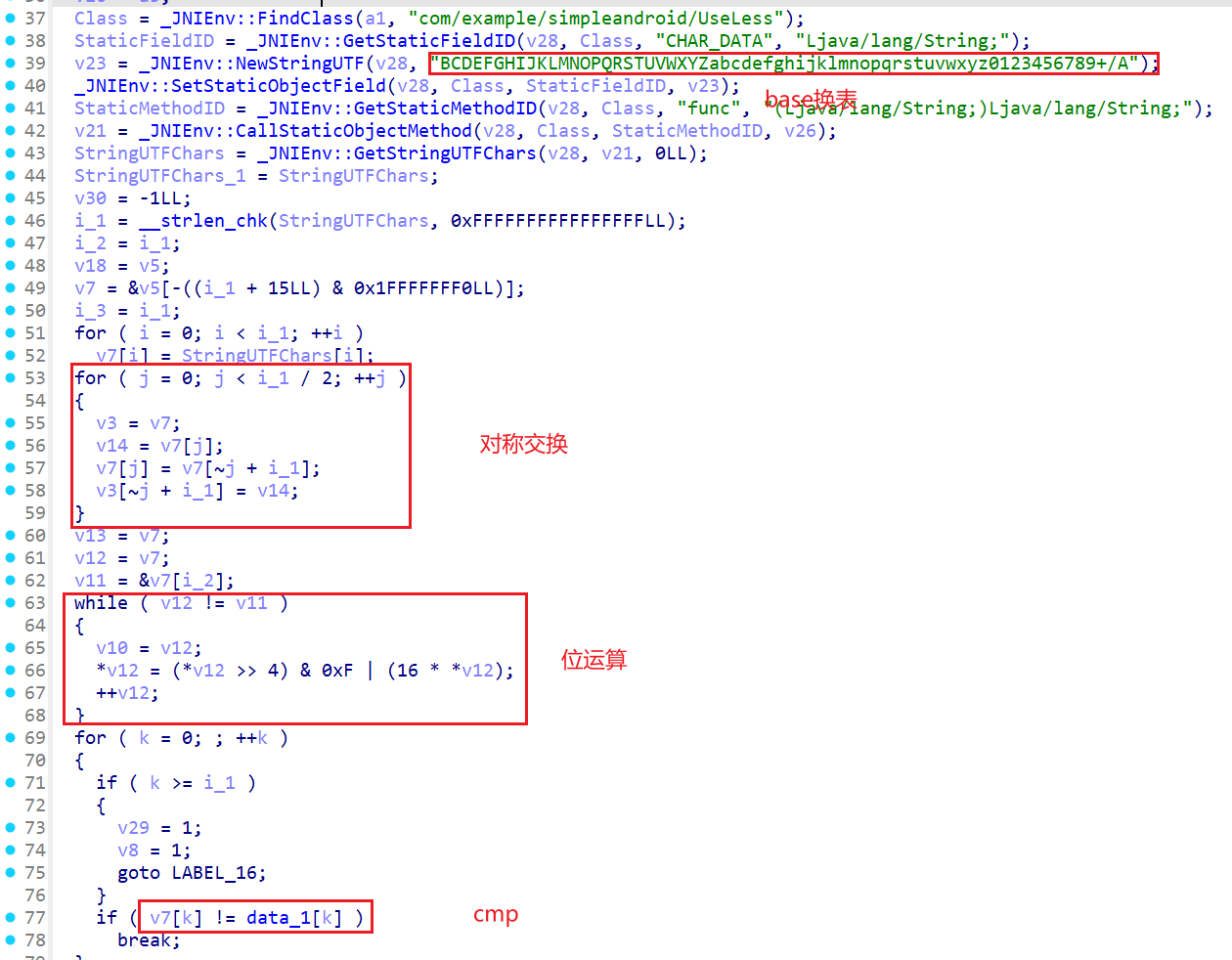
取反:~
~j 相当于-j-1
#include <stdio.h>
#include <string.h>
int main() {
char a[] = {0xB2,0x74,0x45,0x16,0x47,0x34,0x95,0x36,0x17,0xF4,0x43,0x95,0x3,0xD6,0x33,0x95,0xC6,0xD6,0x33,0x36,0xA7,0x35,0xE6,0x36,0x96,0x57,0x43,0x16,0x96,0x97,0xE6,0x16};
int len = sizeof(a);
for(int i=0;i<len;i++){
a[i] = (a[i] >> 4) & 0xf | (a[i] << 4);
}
for(int i=0;i<len/2;i++){
int temp = a[i];
a[i] = a[len - i - 1];
a[len - i - 1] = temp;
}
for(int i=0;i<len;i++){
printf("%c",a[i]);
}
return 0;
}
//anyia4uicnSzc3mlY3m0Y4OqcYCtaTG+


 浙公网安备 33010602011771号
浙公网安备 33010602011771号