nexus3部署及istio域名解析及istio acl
- 部署环境
aws eks环境 sc是gp2
- 部署文件
--- apiVersion: apps/v1 kind: Deployment metadata: namespace: saas name: nexus3 labels: app: nexus3 spec: replicas: 1 selector: matchLabels: app: nexus3 template: metadata: labels: app: nexus3 spec: containers: - name: nexus3 image: sonatype/nexus3:3.32.0 imagePullPolicy: IfNotPresent # command: ["/bin/bash", "-c","sleep 20000000000"] ports: - containerPort: 8081 name: web protocol: TCP livenessProbe: httpGet: path: / port: 8081 initialDelaySeconds: 100 periodSeconds: 30 failureThreshold: 6 readinessProbe: httpGet: path: / port: 8081 initialDelaySeconds: 100 periodSeconds: 30 failureThreshold: 6 resources: limits: cpu: 4000m memory: 2Gi requests: cpu: 500m memory: 512Mi volumeMounts: - name: nexus-data mountPath: /nexus-data securityContext: fsGroup: 0 volumes: - name: nexus-data persistentVolumeClaim: claimName: nexus-data-pvc --- apiVersion: v1 kind: PersistentVolumeClaim metadata: name: nexus-data-pvc namespace: saas spec: accessModes: # - ReadWriteMany - ReadWriteOnce # 指定 storageClass 的名字,这里使用aws默认的 gp2 storageClassName: "gp2" resources: requests: storage: 500Gi --- apiVersion: v1 kind: Service metadata: name: nexus3 namespace: saas labels: app: nexus3 spec: selector: app: nexus3 type: ClusterIP ports: - name: web protocol: TCP port: 8081 targetPort: 8081
- istio域名解析
apiVersion: networking.istio.io/v1alpha3 kind: Gateway metadata: name: nexus3-tenant namespace: saas spec: selector: istio: ingressgateway # use istio default controller servers: - port: number: 80 name: http protocol: HTTP hosts: - "nexus.xxxx.com" --- apiVersion: networking.istio.io/v1alpha3 kind: VirtualService metadata: name: nexus3-tenant namespace: saas spec: hosts: - "nexus.xxxx.com" gateways: - nexus3-tenant http: - match: - uri: prefix: / route: - destination: host: nexus3 port: number: 8081
- istio-acl
apiVersion: security.istio.io/v1beta1 kind: AuthorizationPolicy metadata: name: nexus-acl namespace: istio-system spec: selector: matchLabels: app: istio-ingressgateway action: DENY rules: - from: - source: notIpBlocks: ["ip地址", "ip地址", "ip地址"] to: - operation: hosts: ["nexus.xxxx.com"]
- 踩坑
执行部署nexus yaml文件部署时出现没有权限创建nexus-data目录
查看容器权限有问题,没有root权限
增加一下参数即可创建目录
securityContext: fsGroup: 0
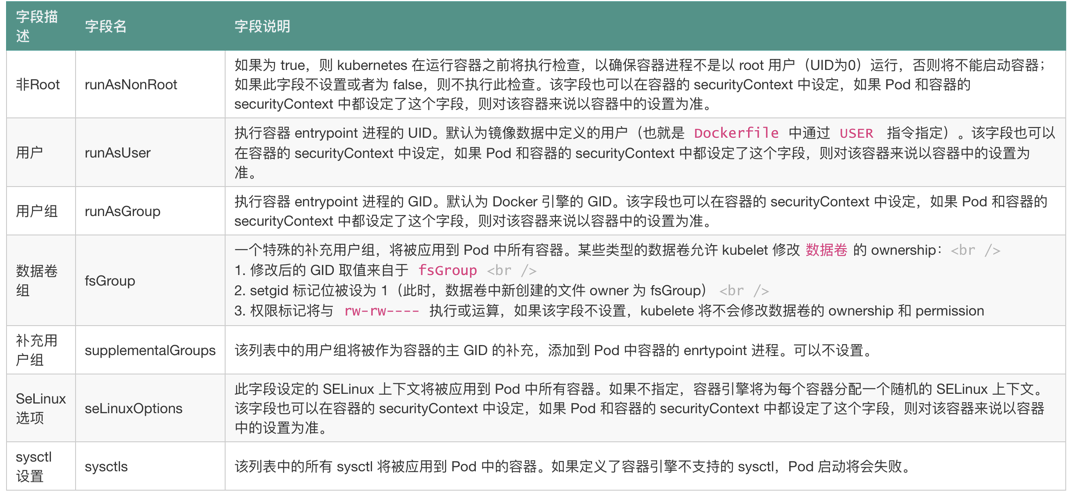
参数解析
我们只需要在 Pod 定义的资源清单文件中添加 securityContext 字段,就可以为 Pod 指定安全上下文相关的设定,通过该字段指定的内容将会对当前 Pod 中的所有容器生效。
在当前资源清单文件中我们在 Pod 下面添加了 securityContext 字段,其中:
runAsUser 字段指定了该 Pod 中所有容器的进程都以 UID 1000 的身份运行
runAsGroup 字段指定了该 Pod 中所有容器的进程都以 GID 3000 的身份运行
如果省略该字段,容器进程的 GID 为 root(0)
容器中创建的文件,其所有者为 userID 1000,groupID 3000
fsGroup 字段指定了该 Pod 的 fsGroup 为 2000
数据卷 (对应挂载点 /pod/demo 的数据卷为 sec-ctx-demo) 的所有者以及在该数据卷下创建的任何文件,其 GID 都为 2000
参考文献:https://blog.csdn.net/weixin_39246554/article/details/121734279

 浙公网安备 33010602011771号
浙公网安备 33010602011771号