Kubernetes Dashboard 是 k8s集群的一个 WEB UI管理工具,代码托管在 github 上,地址:https://github.com/kubernetes/dashboard
#由于镜像无法直接下载需要通过docker 先将镜像拉下来
#拉取镜像
docker pull mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1
#重新打标签
docker tag mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1 k8s.gcr.io/kubernetes-dashboard-amd64:v1.10.1
#删除无用镜像
docker rmi mirrorgooglecontainers/kubernetes-dashboard-amd64:v1.10.1
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v1.10.1/src/deploy/recommended/kubernetes-dashboard.yaml // 直接安装
--- # ------------------- Dashboard Service ------------------- # kind: Service apiVersion: v1 metadata: labels: k8s-app: kubernetes-dashboard name: kubernetes-dashboard namespace: kube-system spec: ports: - port: 443 targetPort: 8443
type: NodePort //修改yaml 文件将接口暴露给外网
selector: k8s-app: kubernetes-dashboard
或者
root@kube rbac]# kubectl patch svc kubernetes-dashboard -p "{"spec":{"type":"NodePort"}}" -n kube-system //通过patch 修改配置信息 Error from server (BadRequest): invalid character 's' looking for beginning of object key string [root@kube rbac]# kubectl patch svc kubernetes-dashboard -p '{"spec":{"type":"NodePort"}}' -n kube-system service/kubernetes-dashboard patched [root@kube rbac]# kubectl get svc -n kube-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 55d kubernetes-dashboard NodePort 10.98.15.9 <none> 443:31358/TCP 23m [root@kube rbac]# [root@kube rbac]# [root@kube rbac]#
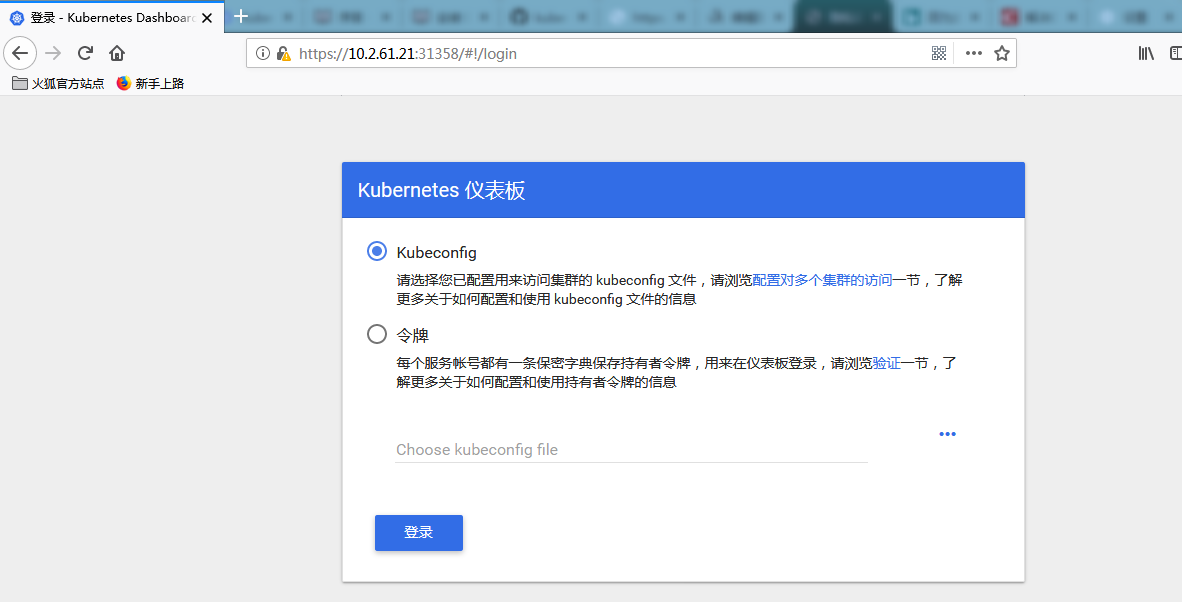
身份认证
登录 dashboard 的时候支持 Kubeconfig 和token 两种认证方式,Kubeconfig 中也依赖token 字段,所以生成token 这一步是必不可少的。
生成token
我们创建一个admin用户并授予admin 角色绑定,使用下面的yaml文件创建admin用户并赋予他管理员权限,然后就可以通过token 登陆dashbaord,这种认证方式本质实际上是通过Service Account 的身份认证加上Bearer token请求 API server 的方式实现,参考 Kubernetes 中的认证。
[root@kube dashboard]# cat admin_user.yaml kind: ClusterRoleBinding apiVersion: rbac.authorization.k8s.io/v1 metadata: name: admin roleRef: kind: ClusterRole name: cluster-admin apiGroup: "" subjects: - kind: ServiceAccount name: admin namespace: kube-system --- apiVersion: v1 kind: ServiceAccount metadata: name: admin namespace: kube-system [root@kube dashboard]#
上面的admin用户创建完成后我们就可以获取到该用户对应的token了,如下命令:
[root@kube dashboard]# kubectl get secret -n kube-system|grep admin-token admin-token-cl5sr [root@kube dashboard]# kubectl get secret admin-token-cl5sr -o jsonpath={.data.token} -n kube-system |base64 -d eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi10b2tlbi1jbDVzciIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjI1MDA3OGU2LTRlMWEtNDk2My04ZTFlLWE4YTA2YTFmZDI3NyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTphZG1pbiJ9.LeeblTJH2hI-fc5xSr_8r6puCVdPJOoj8lX4dnbZfOqFWj1DAWtoKYGJq6bVu9z5EMw--xuHqAQ47iTphBJbn0tddTwM4-gmpypaUvRh7qJxlGHlMrxdBzfhWW3vRK48B-oagqrho5mWX36BrL7rZjB3Jb93OD4EwOVx0OMTHUEAoNfNzmDvPWf2GUBxfSUlEuLTHYrx6gU6gjjyyNu5tyWMRb2lKM9IQeUbp5m87BHAIlAXNd_6UjhFMmdNP-_fyzaOBlrqtRiEEpPMhYTmKcLg_3mglhvRexUo4PnNadPUVU1Pld0PtGnX2QFs2FBJ1mjOnPxUticpGg6AYKEjyA[root@kube dashboard]#
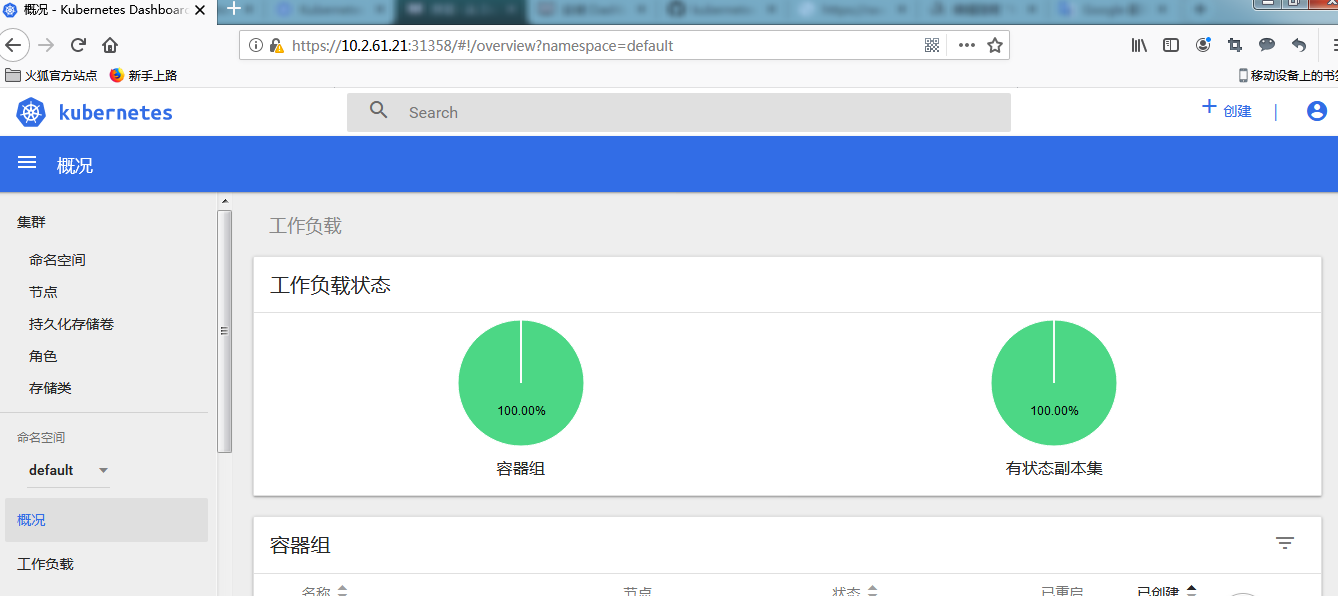
使用 token 成功登陆



 浙公网安备 33010602011771号
浙公网安备 33010602011771号