Metasploit的三种启动方式
不多说,直接上干货!
注意:博主我用的是Kali linux 2016.2(Rolling)。

msfcli 的启动

root@kali:~# msfcli -h
bash: msfcli: 未找到命令
root@kali:~#
msfcli 早就废弃了,现在只有 msfconsole。
msfconsile的启动
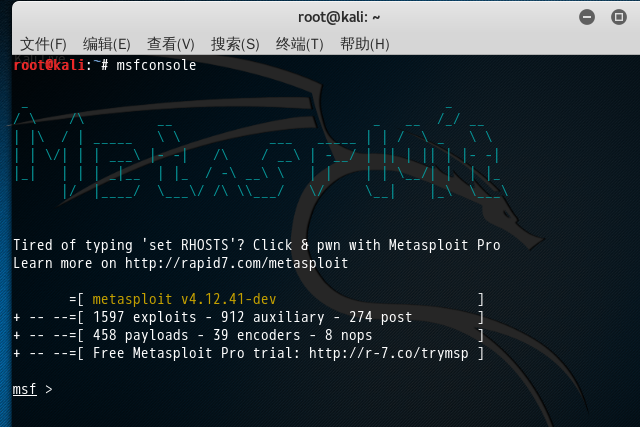
root@kali:~# msfconsole [-] Failed to connect to the database: FATAL: password authentication failed for user "msf" FATAL: password authentication failed for user "msf" _---------. .' ####### ;." .---,. ;@ @@`; .---,.. ." @@@@@'.,'@@ @@@@@',.'@@@@ ". '-.@@@@@@@@@@@@@ @@@@@@@@@@@@@ @; `.@@@@@@@@@@@@ @@@@@@@@@@@@@@ .' "--'.@@@ -.@ @ ,'- .'--" ".@' ; @ @ `. ;' |@@@@ @@@ @ . ' @@@ @@ @@ , `.@@@@ @@ . ',@@ @ ; _____________ ( 3 C ) /|___ / Metasploit! \ ;@'. __*__,." \|--- \_____________/ '(.,...."/ Frustrated with proxy pivoting? Upgrade to layer-2 VPN pivoting with Metasploit Pro -- learn more on http://rapid7.com/metasploit =[ metasploit v4.12.41-dev ] + -- --=[ 1597 exploits - 912 auxiliary - 274 post ] + -- --=[ 458 payloads - 39 encoders - 8 nops ] + -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ] msf > 或者(每次它的启动界面都不一样啦) root@kali:~# msfconsole [-] Failed to connect to the database: FATAL: password authentication failed for user "msf" FATAL: password authentication failed for user "msf" +-------------------------------------------------------+ | METASPLOIT by Rapid7 | +---------------------------+---------------------------+ | __________________ | | | ==c(______(o(______(_() | |""""""""""""|======[*** | | )=\ | | EXPLOIT \ | | // \\ | |_____________\_______ | | // \\ | |==[msf >]============\ | | // \\ | |______________________\ | | // RECON \\ | \(@)(@)(@)(@)(@)(@)(@)/ | | // \\ | ********************* | +---------------------------+---------------------------+ | o O o | \'\/\/\/'/ | | o O | )======( | | o | .' LOOT '. | | |^^^^^^^^^^^^^^|l___ | / _||__ \ | | | PAYLOAD |""\___, | / (_||_ \ | | |________________|__|)__| | | __||_) | | | |(@)(@)"""**|(@)(@)**|(@) | " || " | | = = = = = = = = = = = = | '--------------' | +---------------------------+---------------------------+ Love leveraging credentials? Check out bruteforcing in Metasploit Pro -- learn more on http://rapid7.com/metasploit =[ metasploit v4.12.41-dev ] + -- --=[ 1597 exploits - 912 auxiliary - 274 post ] + -- --=[ 458 payloads - 39 encoders - 8 nops ] + -- --=[ Free Metasploit Pro trial: http://r-7.co/trymsp ] msf >
或者如下,也是可以的。
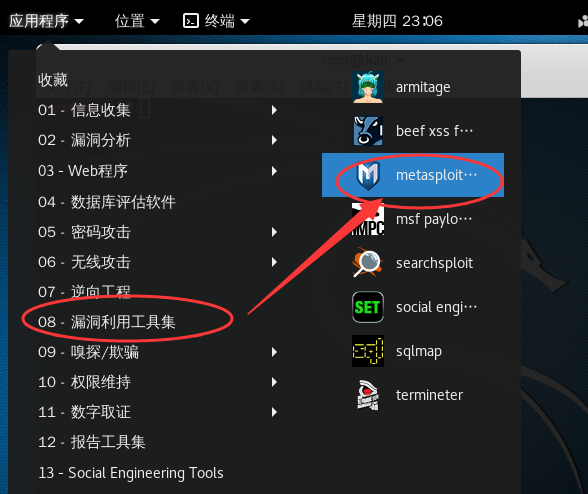
armitage的启动
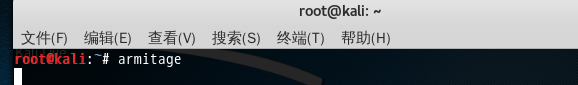
root@kali:~# armitage
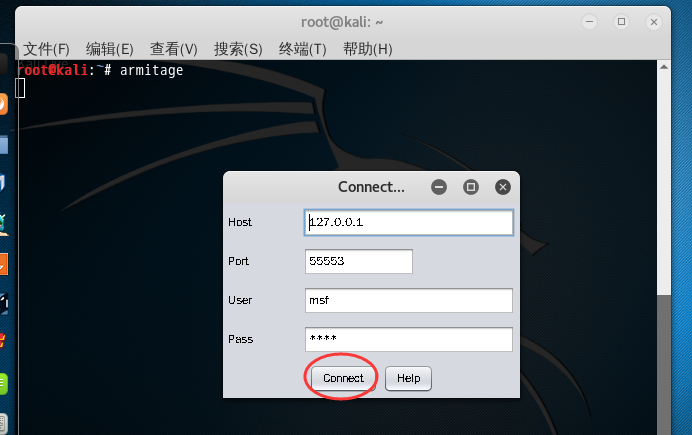
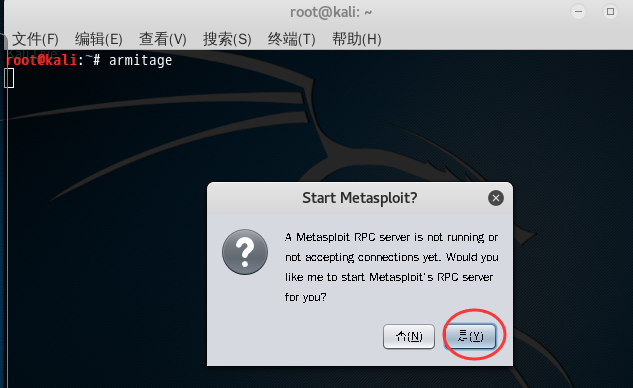
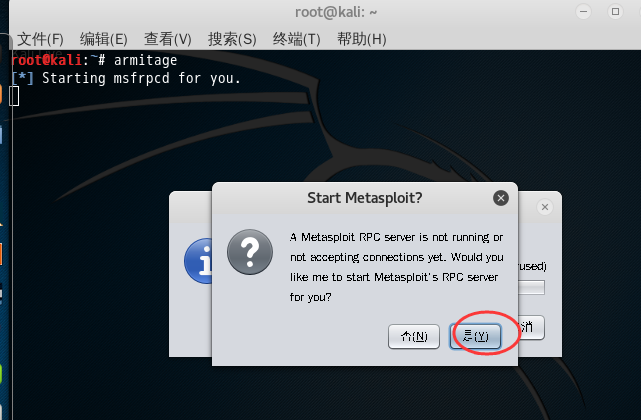
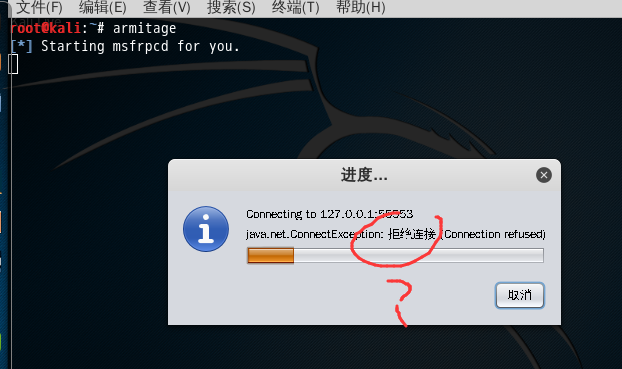
别急,过会儿就好了 。
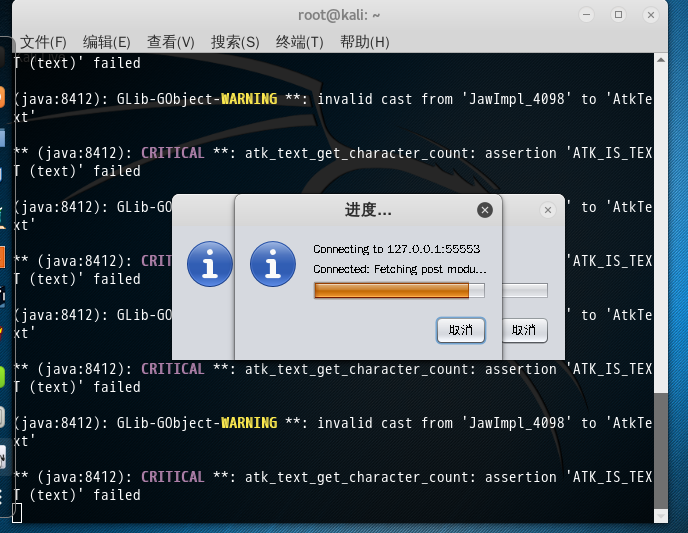
别急,过会儿就好了 。
别急,过会儿就好了 。
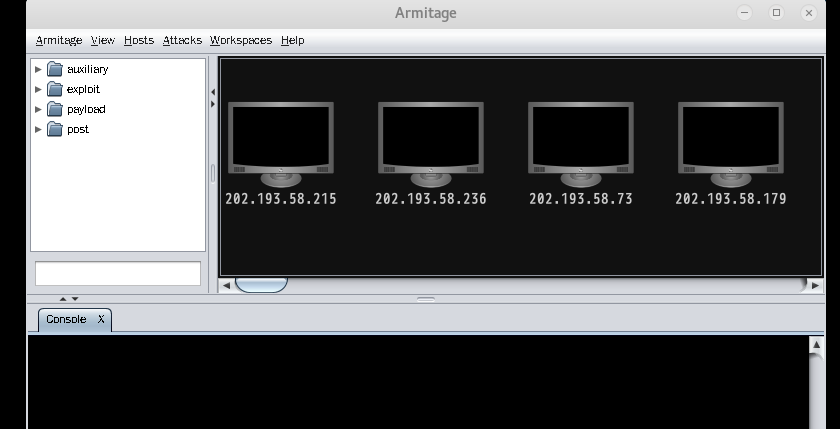
可以,干活了。
作者:大数据和人工智能躺过的坑
出处:http://www.cnblogs.com/zlslch/
本文版权归作者和博客园共有,欢迎转载,但未经作者同意必须保留此段声明,且在文章页面明显位置给出原文链接,否则保留追究法律责任的权利。
如果您认为这篇文章还不错或者有所收获,您可以通过右边的“打赏”功能 打赏我一杯咖啡【物质支持】,也可以点击右下角的【好文要顶】按钮【精神支持】,因为这两种支持都是我继续写作,分享的最大动力!




 浙公网安备 33010602011771号
浙公网安备 33010602011771号