HCTF2016-杂项签到
题目下载了一个+_+.pcapng ,用Wireshark打开, Ctrl-F搜索flag 发现python代码 将Data导出
#!/usr/bin/env python # coding:utf-8 __author__ = 'Aklis' from Crypto import Random from Crypto.Cipher import AES import sys import base64 def decrypt(encrypted, passphrase): IV = encrypted[:16] aes = AES.new(passphrase, AES.MODE_CBC, IV) return aes.decrypt(encrypted[16:]) def encrypt(message, passphrase): IV = message[:16] length = 16 count = len(message) padding = length - (count % length) message = message + '\0' * padding aes = AES.new(passphrase, AES.MODE_CBC, IV) return aes.encrypt(message) IV = 'YUFHJKVWEASDGQDH' message = IV + 'flag is hctf{xxxxxxxxxxxxxxx}' print len(message) example = encrypt(message, 'Qq4wdrhhyEWe4qBF') print example example = decrypt(example, 'Qq4wdrhhyEWe4qBF') print example
是DES加密,知道VI 与 key
在pcap流量包继续搜索看到了
mbZoEMrhAO0WWeugNjqNw3U6Tt2C+rwpgpbdWRZgfQI3MAh0sZ9qjnziUKkV90XhAOkIs/OXoYVw5uQDjVvgNA=
猜测是直接加密,发现解不开。
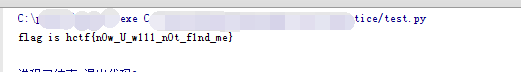
测试得出:
用base64解码,再用该decrypt()解密。
#!/usr/bin/env python # coding:utf-8 __author__ = 'Aklis' from Crypto import Random from Crypto.Cipher import AES import sys import base64 def decrypt(encrypted, passphrase): IV = encrypted[:16] aes = AES.new(passphrase, AES.MODE_CBC, IV) return aes.decrypt(encrypted[16:]) def encrypt(message, passphrase): IV = message[:16] length = 16 count = len(message) padding = length - (count % length) message = message + '\0' * padding aes = AES.new(passphrase, AES.MODE_CBC, IV) return aes.encrypt(message) # IV = 'YUFHJKVWEASDGQDH' # message = IV + 'flag is hctf{xxxxxxxxxxxxxxx}' # # # print len(message) # example = encrypt(message, 'Qq4wdrhhyEWe4qBF') # print example a='mbZoEMrhAO0WWeugNjqNw3U6Tt2C+rwpgpbdWRZgfQI3MAh0sZ9qjnziUKkV90XhAOkIs/OXoYVw5uQDjVvgNA==' b = base64.b64decode(a) example = decrypt(b, 'Qq4wdrhhyEWe4qBF') print example


 浙公网安备 33010602011771号
浙公网安备 33010602011771号